ECDSA Curve Certificates on 2.5.0
-
@jimp this done by up to date openssl version on OS? If yes then it good to hear, specially for people who using HAproxy.
Little offtopic question about webgui: on 2.4 stable release webgui work only with RSA keys. Using ECDSA Keys broke nginx. How it going now? -
Yes, the updated OpenSSL enabled TLS v1.3. There may be something extra that HAProxy needs to activate it, I haven't checked into that yet, but you might bring it up in the Cache/Proxy board to see if the HAProxy package maintainer has worked on that yet.
The ECDSA question needs to go in its own thread, but I haven't tried it, there is probably some work needed for the nginx config to enable ECDSA ciphers.
-
@jimp ECDSA is available from ACME, people can fail by trie get them working, like I did half year ago :(. So add support for this can remove potential time-consuming issues :)
-
@dragoangel said in Please Enable TLSv1.3 On pfSense 2.5.0:
Using ECDSA Keys broke nginx. How it going now?
Not with 2.5
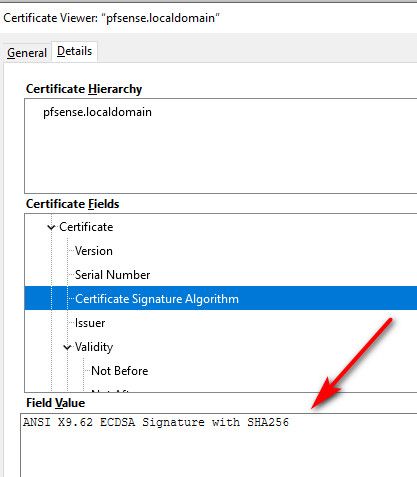
You prob want to make sure what your browser supports before you do you ca and certs in pfsense.
-
@johnpoz of course browser support that :), I use this type of certs for all sites hosted on HAproxy. Great to hear that now all work. Thanks for check. I think HAproxy will work too, it uses local os openssl. Unfortunately no matter how many I write about HAproxy updates or futures in forum, or even redmine - I was ignored so
 . When pfsense 2.5 will became stable release?
. When pfsense 2.5 will became stable release? -
@dragoangel said in Please Enable TLSv1.3 On pfSense 2.5.0:
@johnpoz of course browser support that
They support some curve types, but openssl can use some that are not.. Is brainpool supported by firefox for example?
As to haproxy updates, 2.5 is currently using 2.07 so pretty close to current, 2.08 just came out a few weeks ago.
-
I split this off into its own thread since it was a bit of a tangent from the other one.
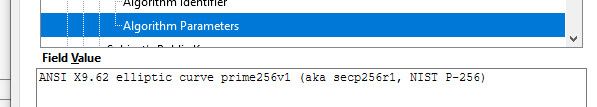
ECDSA certificates do work on 2.5.0 in the GUI, but as @johnpoz said it depends on the curve chosen. TLS 1.3 deprecated the use of brainpool curves due to lack of use, and it's not clear if any/most browsers supported them, but that's what our new ECDSA code in the certificate manager defaulted to.
I just changed that to
prime256v1which does indeed work. I made a new GUI certificate usingprime256v1and it worked fine with Firefox, where one using a brainpool curve did not. -
 . So did you know eta 2.5 will become stable?
. So did you know eta 2.5 will become stable?