HA proxy on pfsense cannot working
-
i configed ha proxy on pfsense ver 2.4.4-RELEASE-p3 (amd64) but not working.
two pfsense synced config, PC ping virtual ip of pfsense success but cannot access internet.
i cannot telnet proxy port (3128) to virtual ip
now, pfsense error: A communications error occurred while attempting to call XMLRPC method host_firmware_version: Unable to connect to tcp://192.168.20.101:80. Error: Operation timed out @ 2019-11-29 13:58:14
anyone help me. thank all.
below this is my diagram config HA: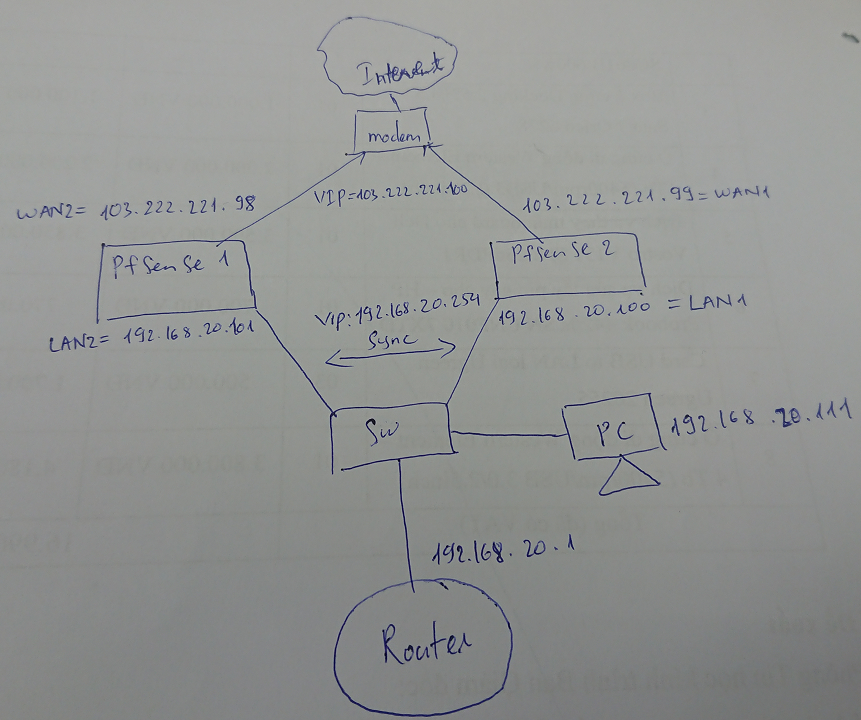
-
Hi, I'm new to pfSense but your problem seems to be related to connections. Missing gateway configuration or rule to let the connection pass.
Anyhow, one thing which makes me wonder a bit is the direction... Unable to connect to tcp://192.168.20.101:80. This means pfSense2 tries to sync to pfSense1. Why XMLRPC from secondary to primary? The secondary should not sync his config changes to master I guess. -
@mse Thank for commnet.
i have one pfsense primary only. The pfsense backup, i only checked "Synchronize states" ---> this is true or false.
thank you. -
I'm facing the same problem in my HA setup using version 2.4.4-RELEASE-p3 (amd64). Even if I put back the “Default LAN > any” rule right on the top of my rules internet still doesn't work. I tried pining 8.8.8.8 from a host on the LAN and never go through. My LAN host is using the LAN VIP as its gateway and DNS as I have DNS forwarder enable as well. HA setup is working fine and I use direct cable connection between the appliance
Probably something to be enabled as well for these rules to work ? Was your issue resolved ?
-
@usaiat How about nat configuration?
-
@netblues Which interface do I have to/address do I have to NAT
-
Outbound nat, on the interface traffic is leaving pf. In a ha environment, the vip with manual outbound.
In general, traffic must first reach the interface and then nat rules take effect.
So eg. you have to allow outbound at the lan level and nat it at the wan level. -
@usaiat I resolved this issue. You must nat forward traffic from LAN to internet redirect to members pfsense.
e.g: from pc (192.168.20.111) to internet with proxy(20.254) ====> you nat forwarding redirect through pfsense1(20.101) and nat forwarding redirect through pfsense2(20.100) ===> successs -
@Mr-Trieu Sorry I'm confused here. I thought with HA you just do NAT configuration on the primary ? Also is it Outbound NAT or Port Forward NAT as @netblues is suggesting Outbound NAT
-
Here is my IP schema for my HA
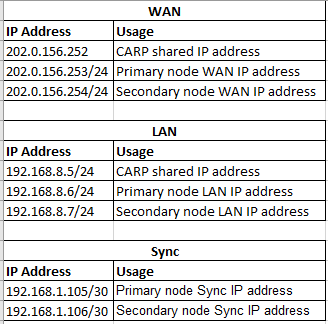
-
And I've got a host configured as 192.168.8.252/24 to use 192.168.8.5 as its gateway and DNS.
-
@usaiat said in HA proxy on pfsense cannot working:
@Mr-Trieu Sorry I'm confused here. I thought with HA you just do NAT configuration on the primary ? Also is it Outbound NAT or Port Forward NAT as @netblues is suggesting Outbound NAT
Nat rules are propagated, so yes, you do them on primary (unless for special purposes you don't want to replicate settings)
Outbound nat is for connections leaving pf sense .
port forward is for incoming connections typically from the InternetWhat is your issue?
-
Thanks @netblues . My issue is I just couldn't access internet from a client using the pfsense LAN VIP as its gateway and DNS (with DNS forwarder enabled). From pfsense itself I can ping internet and name lookup as well. Even if I put back the “Default LAN > any” rule right on the top of my rules internet still doesn't work.
I've also followed this step on the pfSense book
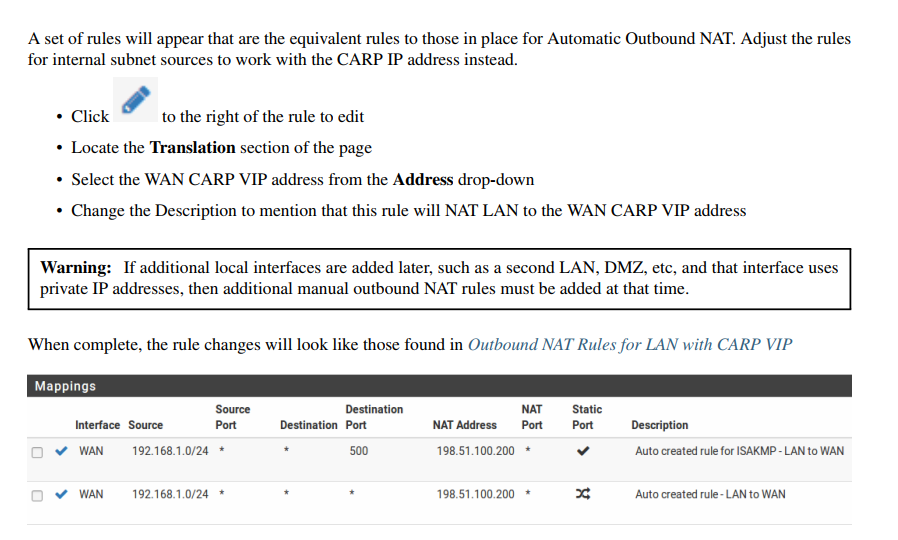
Probably something else I'm missing ?
-
@usaiat Probably there is a misconfiguration somewhere.
Please post your nat and firewall rules, not the ones from the book.
And a network diagram, if there is anything special apart from two nodes a carp wan, a carp vip and a sync interface... -
This is my setup
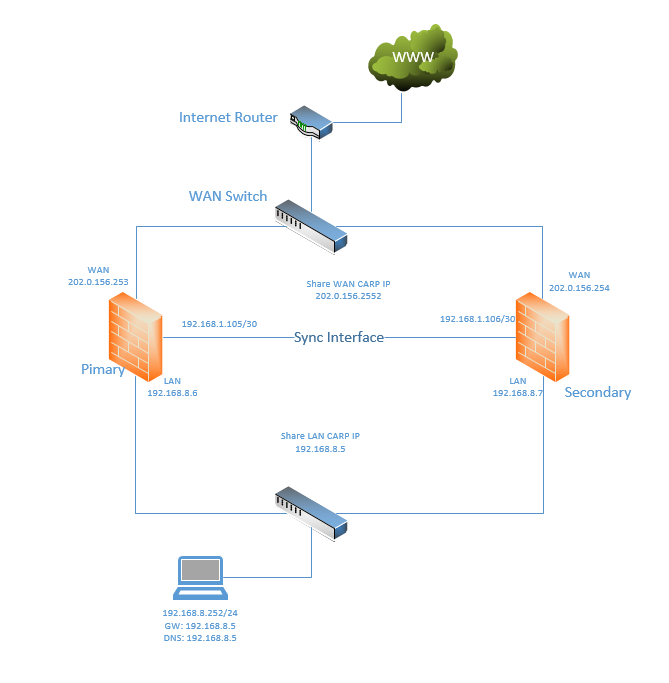
LAN rule below. WAN has only the default Block private networks and loopback addresses and Block bogon networks rule
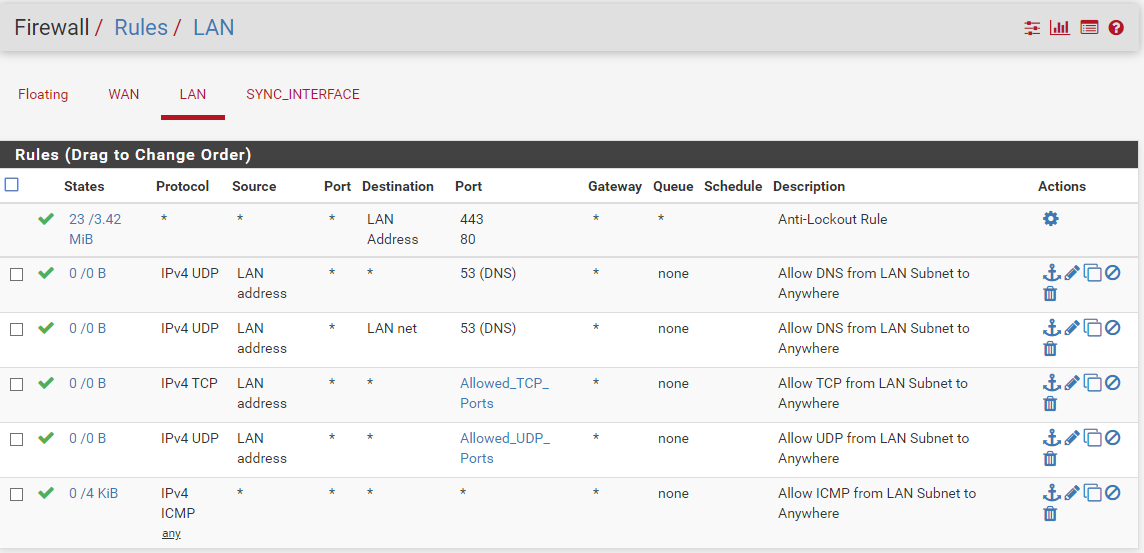
Manual Outbound NAT below
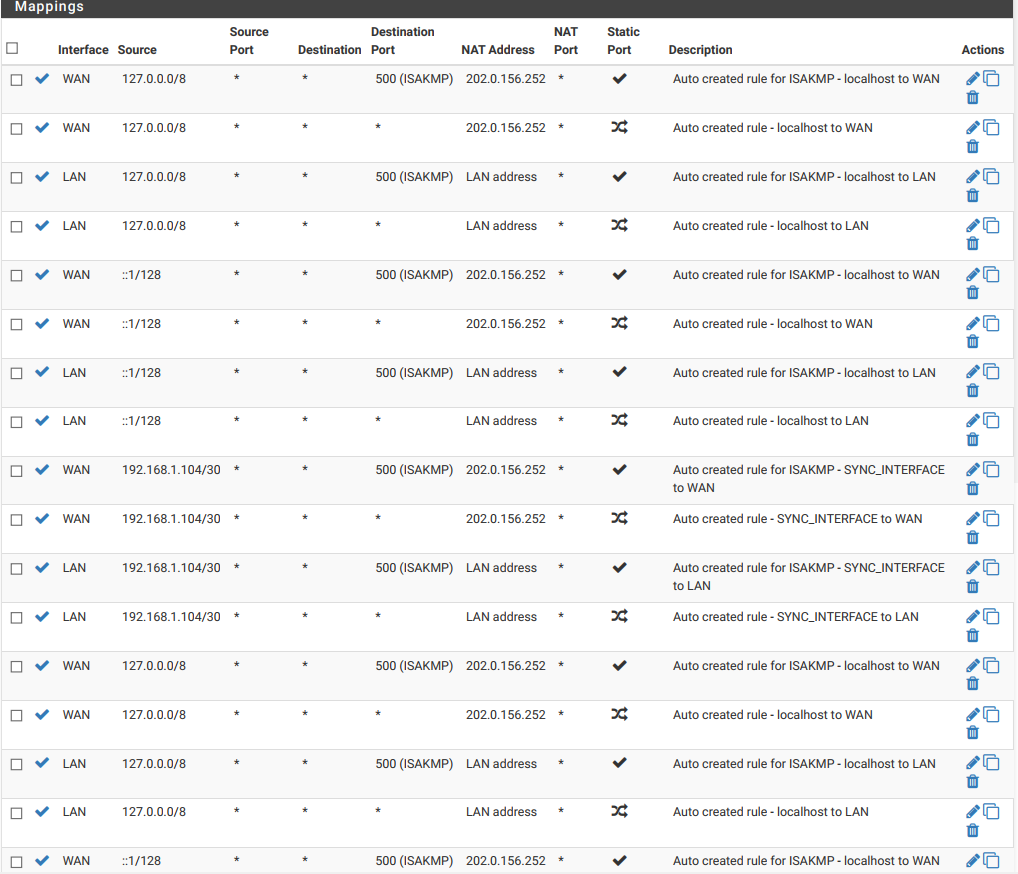
-
You are not allowing your lan to pass.
Only ping is allowed (and has some traffic matched too)
Lan address is the ip of pf. What you need is lan net
And I do hope Allowed_tcp ports says something meaningful
And your nat rules is a mess..
192.168.0.0/16 with nat address 202.0.155.252 is the only thing you need
(for lan.) also localhost to wan is needed for pfsense internet access
if not using ipsec you can eliminate all isakmp entries
This is a ha setup, don't rely too much on autocreated rules :)
As a rule of thumb, first establish basic connectivity and then start doing smarter things. -
@netblues That fix it for me. LAN rule - change from LAN address to LAN net. By the way, those NAT rules are the automatically created rules. So I just change all those on WAN interface to use my WAN VIP
Thank you so much
-
@usaiat Well, the automatic nat rules are there to ease first steps, however they do create clutter. e.g if there is no ipsec vpn, there is no need for port 500 and isakmp.
Also complete rfc1918 ranges are allowed, and even though this doesn't do much harm, makes the rules more difficult to read.
In practice you need nat rules for your lan pc's and for pfsense to reach the internet itself.
Nothing else. -
@netblues Sure, thanks
