Blocking Acces to Another VLAN but Allow Internet Acces
-
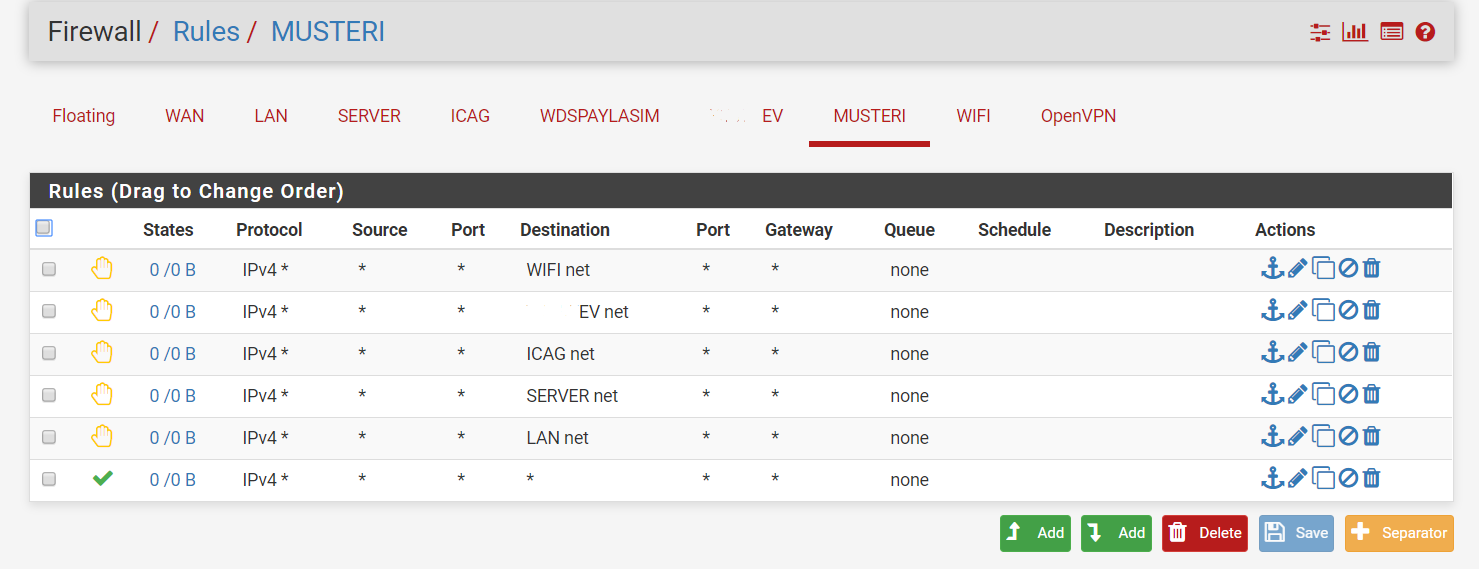
I wanna block musteri vlan to acces any another vlan except wdspaylasim vlan. I did this rules but musteri vlan still can acces to etc. Wifi network.
-
Have you deleted the states?
BTW: It's more reliable to reject any and allow only the destinations you want to allow.
For allowing internet access add an alias including all RFC 1918 networks and use this in a pass rule as destination with "invert" checked. (Presuming you use only RFC 1918 networks behind pfSense.)
So you will be still save if you change a subnet or add a network. -
I Just restarted my machine.
Actually i wanna do same thing for my other VLANs too. But its different. Like icag can acces to Server, wdspaylasim and internet but cant acces to other VLANs. Also i cant allow Just dns, http and https. My clients using different smtp ports, cctv port etc.
Also no, i have out of RFC1918 network
-
If you have those rules and client can still access the wifi subnet from the musteri subnet after rebooting then something else is passing that traffic. You might have a floating rule or an interface group rule passing that traffic.
Steve
-
Where are you testing from? Because I'm not seeing hits on any of those rules. The first thing I would do is re-verify that your access ports are in the correct VLAN.
Then, If you only want MUSTERI to access WDSPAYLASIM and nothing else, then remove everything you have and configure an explicit pass rule for:
Source = MUSTERI net
Destination = WDSPAYLASIM netand be done. Everything else will get blocked by the implicit deny.