How to find spambot? Got network abuse report from my ISP
-
I have the ports blocked since 3 days and Snort runs now on LAN.
Nothing shows up. All phones, PCs, tablets, the print server, satellite receiver, DECT station are connected as ever.
Nobody was here with a another device.
As i said: could be something temporary from playing around and it's no longer present.
But it's hard to believe there was something in Raspbian, Armbian or DietPi.
Maybe something i did but on the new Fire TV stick that i already did uninstall...The funny thing is that the day before someone from my ISP was here because bridge mode did not work and there box sometimes did crash/reboot.
He was the only one with other devices.
He told me the router did not receive the last firmware automatically and made a reset to factory defaults. After that the router did pull the newest firmware. -
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
Nothing shows up
You mean : even you didn't send a mail ?
Show us the LAN firewall ?@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
He was the only one with other devices.
These devices are not passing through pfSense ...
-
Does anybody know what this means, in his screenshot above?
source_port: 33431
Jeff
-
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
source_port: 33431 source-port: 33431 original-rcpt-to: www.tiaanxxxxxxxx.09@gmail.com source-ip: 176.199.xxx.xxxWhen the mail was send, it cam from the IP 176.199.xxx.xxx using port 33431.
The device that send the mail the mail was behind pfSense (but was it - see my question just above) and so it was NATted.
The original source LAN IP and source port can't be known to the ISP.
The only thing they and we know is the destination, a gmail mail server and one of the mail destination ports : 465 or 25 if gmail still accepts mail on port '25'. -
@Gertjan said in How to find spambot? Got network abuse report from my ISP:
You mean : even you didn't send a mail
What i mean is that nothing shows up that is trying to send mails.
Sure, if I try to send one (what of course is not working) it shows up. -
It happened again.
Nothing in Snort and mail ports are blocked:
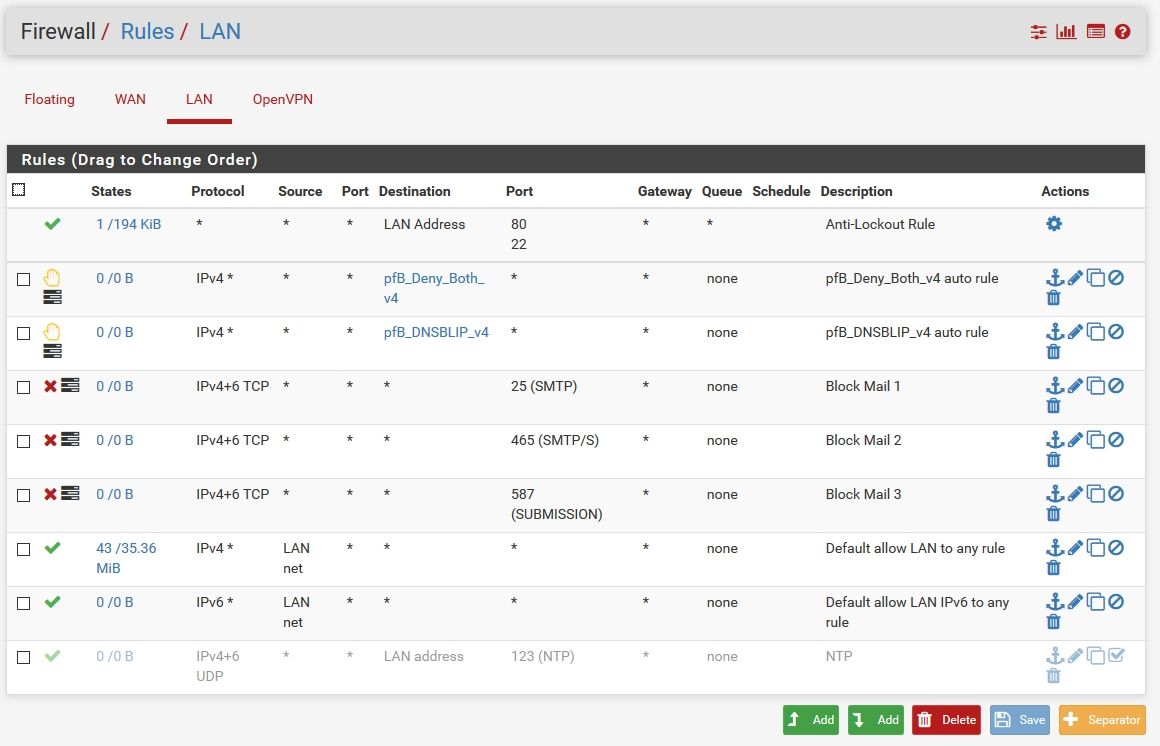
I have a lot of blocked UDP but i don't know what device it is with that IPv6:
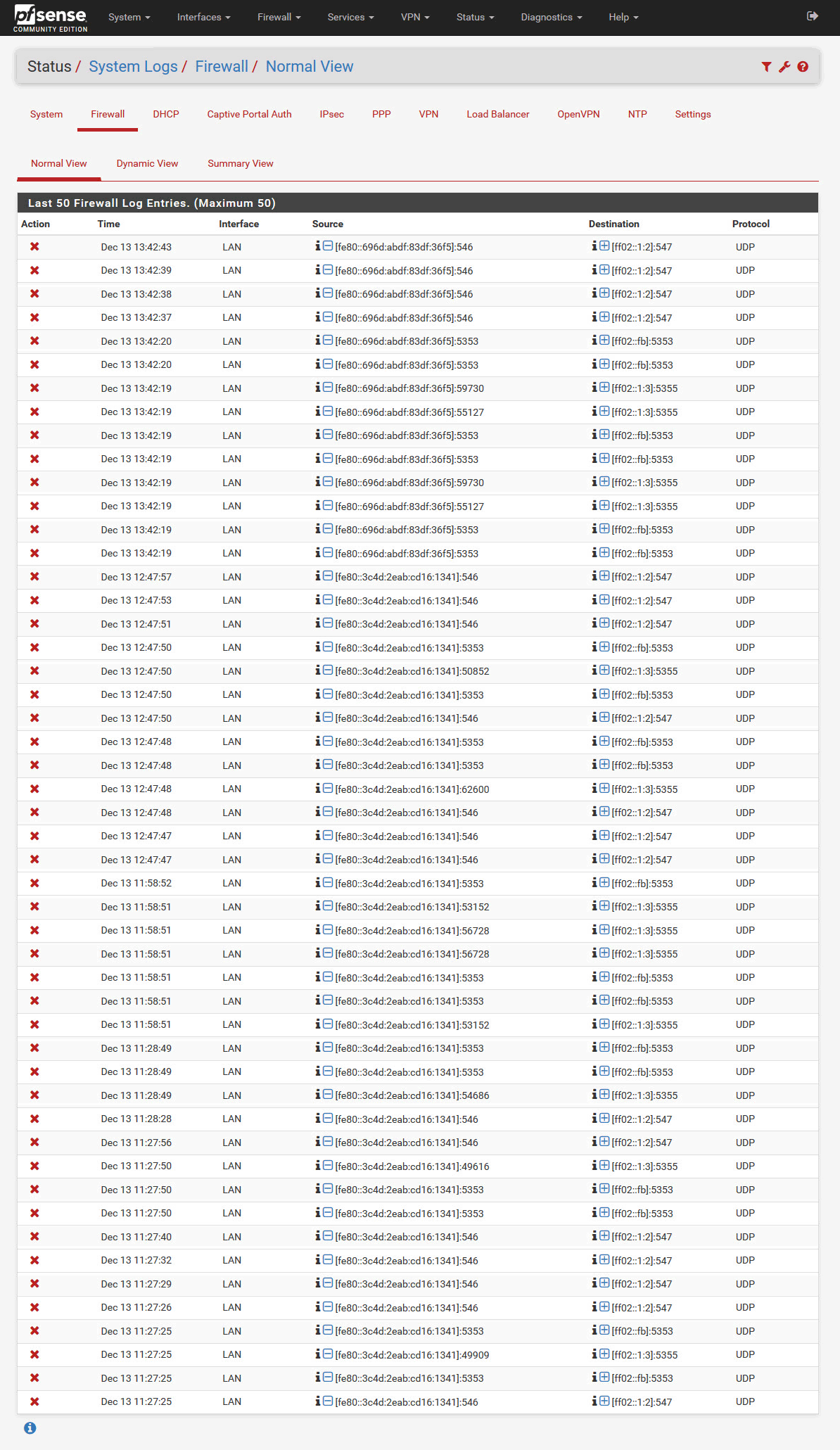
And this and 10.1.254.10 is my Nvidia Shield:
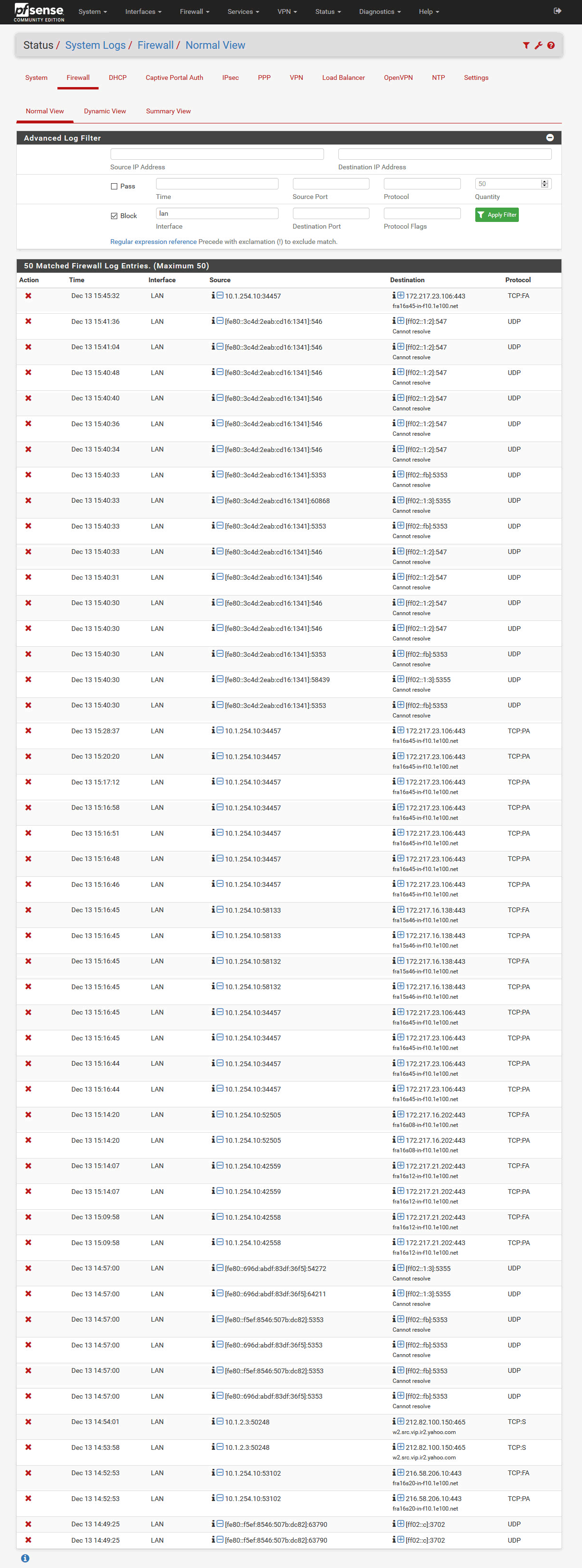
-
@akuma1x said in How to find spambot? Got network abuse report from my ISP:
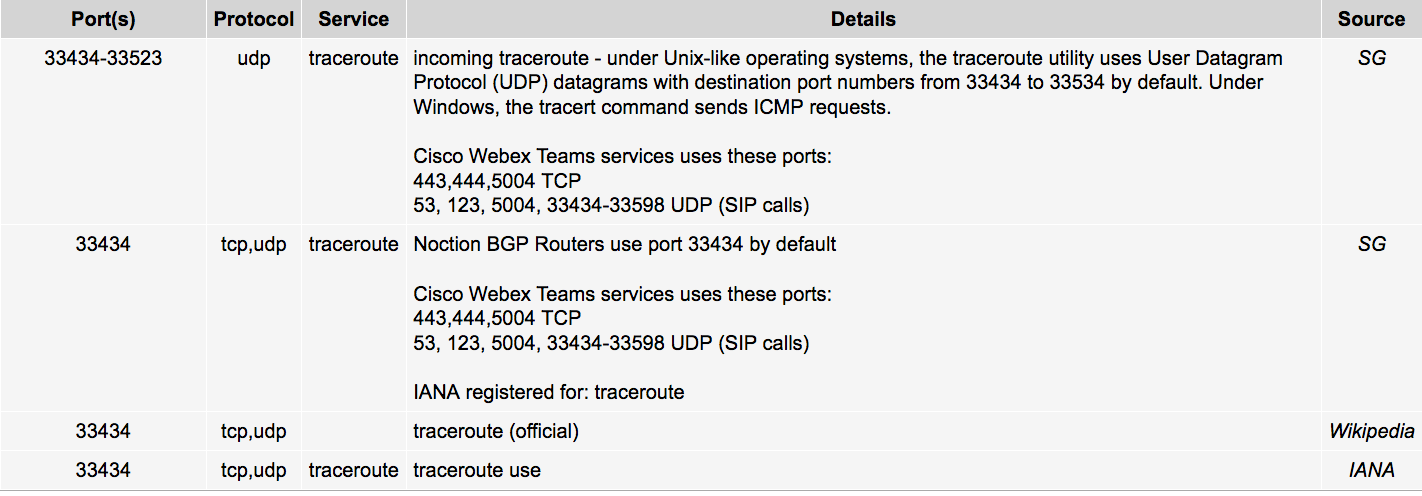
Does anybody know what this means, in his screenshot above?
source_port: 33431
Jeff
A quick search revealed this...could it be his router in front of pfSense doing the spamming?
-
Humm.
No need to list firewall logs - or the rules. As the link (from your ISP ?) shows, the last 2 days there were no spam mails. It stopped 11 December, that was two days ago.
Your firewall rules look ok to me.
I played with an identical rule :
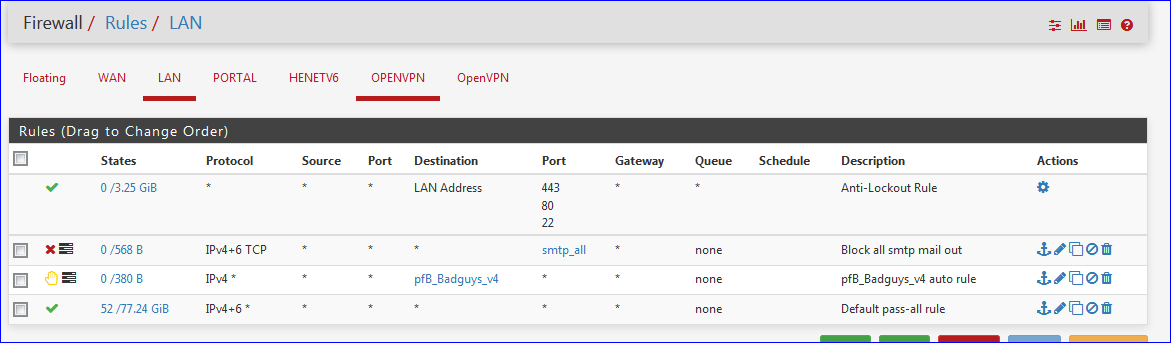
My second rules, with the port-alias including 25,465,587 works just fine : Outlook, the mail client is now hurling it can't mail out any mails ....
That the rules is capturing traffic can be seen by :
What this all means : if mail reaches the Internet by your WAN IP, it isn't injected via your LAN (?) interface.
By OpenVPN (is this a VPN server interface ?) ?
If not, that it's pretty save to say : this spam mail does flow through pfSense. What this means : you can disconnect the LAN interface and spam will still be send. Because it's not originating from a device 'behind' pfSense - on it's LAN.
pfSense is connected to what upstream device ? A router with wifi or other devices connected to it ? -
@Gertjan Wondered whether his ISP serviceman loaded a corrupted firmware on the router!
-
There is only the ISP router/modem in front of pfSense.
Until last week i had double NAT but it is now switched to bridged mode.
So the routers WLAN and everything is off.OpenVPN is the OpenVPN Server in pfSense.
What also changed is that i moved from Proxmox to Hyper-V (in Windows 10) that is giving me trouble and not working reliable. Had pfSense running in Proxmox for a long time and also in Hyper-V 2016 Core without problems.
https://forum.netgate.com/topic/148638/can-t-get-puplic-ip-in-pfsense-with-hyper-v-in-windows-10-pro -
That only happens in fake Youtube movies and other SF films.
It can be done, though .... but who wins what where and when ?
If only the tech service can update such a router, the scandal would be huge : ISP out of business .... that's mega $$$$$$.
If one can't trust his ISP router any more .....
Said that : my ISP router is just a router : no TV - phone - Wifi facilities are enabled. It's a pure VDSL to LAN-port device, having pfSense as it's only client-device. No one connects to the other 3 available LAN ports - never.
-
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
OpenVPN is the OpenVPN Server in pfSense.
So, this could be another vector ?!
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
Hyper-V (in Windows 10)
Yet another vector : if the hosting W10 machine has access to the pfSense WAN interface (ir shouldn't) any software in the host (W10) could output mail, completely bypassing pfSense.
Again : these spam mails are not passing through pfSense. Up to you to test the rest.
Btw :
https://docs.netgate.com/pfsense/en/latest/virtualization/virtualizing-pfsense-with-hyper-v.htmlWhen they talk about the WAN :
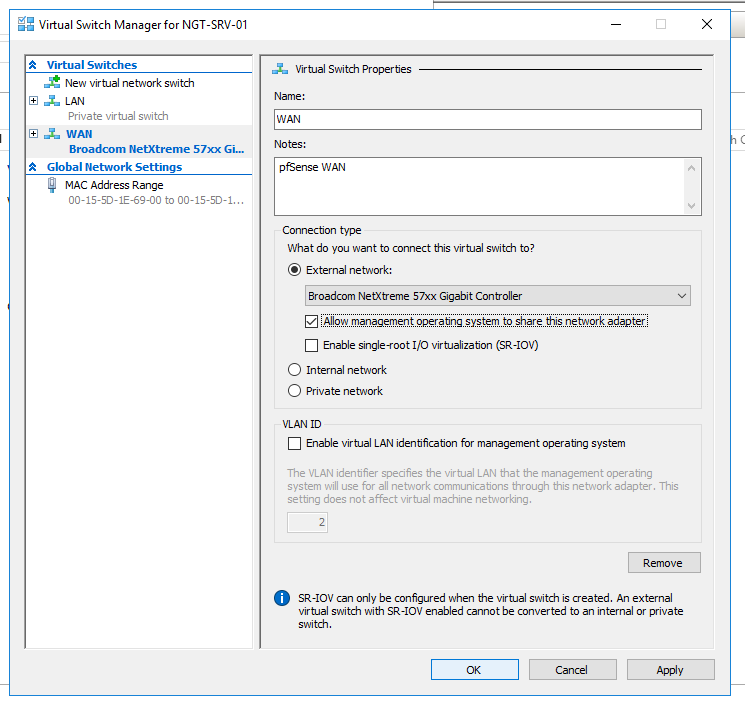
the option : "Allow management operating system to share this network adapter" should be unchecked !!
If not, the host could use it, bypassing pfSense. -
Sure "Allow management operating system to share this network adapter" is disabled.
That is how i had it for 3 years in Hyper-V 2016.I did disabled OpenVPN for now.
I also made a AdwCleaner and Malwarebytes Anti-Malware scan on the host (Win 10).
For now i switched to my pfSense standalone box.
If it's the Hyper-V box then it should show up in pfSense!?Is there something (Virus, Trojan or whatever) that could bypass the blocked mail ports?
Sending mails over something else? -
@MrGlasspoole You're never going to catch anything on PFsense's log viewer unless you switch to dynamic view and watch it live. And even then, because the log buffer is so short, you still may miss it. In order for the firewall logs to be useful, you need to export them to a syslog server. However, up until now, it's been moot cause your block rules show no hits anyway.
After looking around, it looks like there may be some additional ports that need to be blocked. Apparently, 2525 and 2526 are non-standard ports that are used as alternates on some mail servers. Which makes the list now:
25, 465, 587, 2525, 2526
I would start exporting your firewall logs to a syslog server at a minimum. Some other things to look at:
- Start sending netflow data to a collector. The data would be captured either at the switch, which would be ideal if you have capable gear or on PFsense via the softflowd package. The idea being you would have historical top talker/top connection data that can be cross-referenced with the timestamps in your ISP's abuse reports which will aid in tracking down the offending device.
- Do you have any full tunnel road warrior setups or site-to-site tunnels configured where the remote end is routing its traffic through your connection? If so, it's possible that the offending device may not even be on your network.
- You could install Untangle in bridge mode behind PFsense and leverage the SPAM filter app
-
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
Is there something (Virus, Trojan or whatever) that could bypass the blocked mail ports?
Sending mails over something else?Sure !
That's like running a web server on port ....81 (for http) and, example, port 512 (https).
No one will be able to connect to it, except if the user knows about it, and uses on his side - the client - the special port override.Now for mails : Take a look at this setting :
System > Advanced > Notifications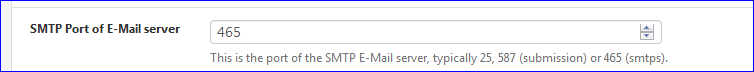
I could set up any port here. Why not.
But .... when I want to send a notification mail to gmail, it has to be port 587 or 465 because gmail hasn't set up any other ports for receiving mail.You could be running your own mail server for your own domains( I actually do that) and thus mails leaving my local network could use any port, if I set up my mail server to use these ports to receive mails, so it can relay them afterwards. My mail server would have to use the standard ports 25 (clear text mail) or 465 (smtps mail) to hand it over to the destination MX.
No exception possible. -
@marvosa said in How to find spambot? Got network abuse report from my ISP:
Some other things to look at:- Start sending netflow data to a collector. The data would be captured either at the switch, which would be ideal if you have capable gear or on PFsense via the softflowd package. The idea being you would have historical top talker/top connection data that can be cross-referenced with the timestamps in your ISP's abuse reports which will aid in tracking down the offending device.
- Do you have any full tunnel road warrior setups or site-to-site tunnels configured where the remote end is routing its traffic through your connection? If so, it's possible that the offending device may not even be on your network.
- You could install Untangle in bridge mode behind PFsense and leverage the SPAM filter app
That all sounds really complicated. This is a home network and not the FBI headquarters :-)
I have a Netgear WNDR4300 with DD-WRT as AP and a ZyXEL GS1900-24E switch.I wonder what the Nvidia Shield is doing there all the time what gets blocked.
And how can i found out that other device that only shows a IPv6 (the one with 5353 UDP)?I did google if other people get mails from my ISP but there mails are about Open-DNS Resolver and open mDNS Service.
Most people get mails because of Amazon Fire TV/Fire HD or PlayStation 4 and port 5353. -
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
port 5353.
has zero to do with email - its mdns... No you shouldn't have those ports open to the internet.
-
@johnpoz said in How to find spambot? Got network abuse report from my ISP:
port 5353.
has zero to do with email - its mdns... No you shouldn't have those ports open to the internet.
I know it has nothing to do with email. I just wonder that my ISP is sending abuse mails to a lot of people about it and most of the time the PS4 was the problem.
I did install PRTG Network Monitor. Now i need to find out how that works.
Looks like flying a Boeing 747.I need to monitor the WAN port? I do that with softflowd?
-
Ok there are 18 new events on that abuse site this morning 2:52am (Dec 14).
pfSense is running on a standalone machine (no HyperV) and all the mail ports are blocked.I have now PRTG running but I'm not sure with some settings.
Should i leave the "Source Address" default or should i set it to LAN since I'm only looking for mails going out?
For "Syslog Contents" i only selected "Firewall Events".
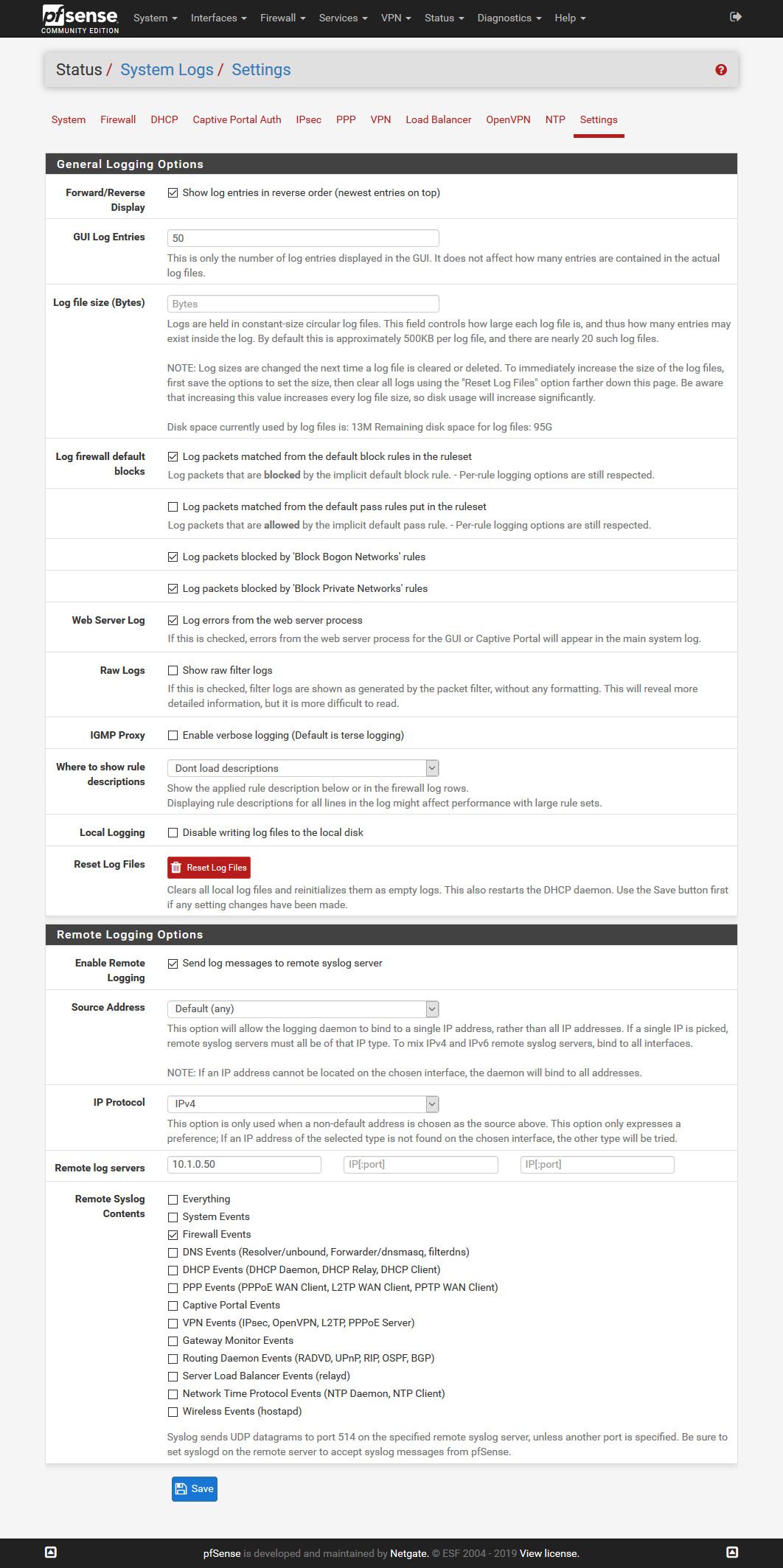
I did set the "Include Filter" in PRTG to "message[igb1]" because I'm only looking for what is blocked on the LAN interface.
This is what i have then:
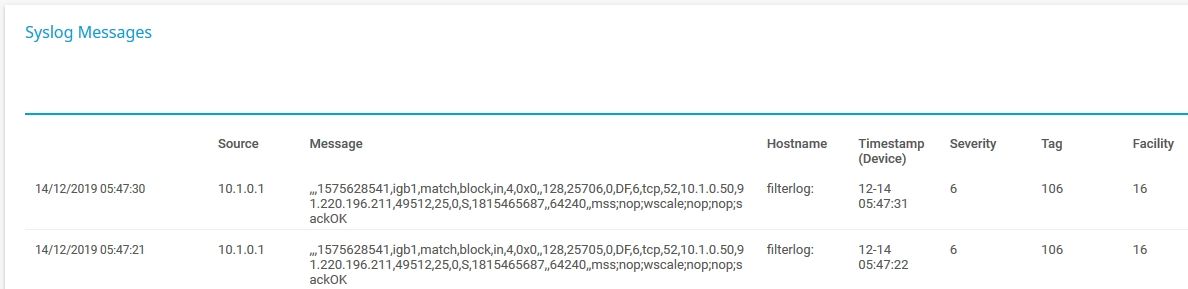
I cant figure out how to filter that by port or how to make it more readable.
This two messages is PRTG trying to send some mails.Now that NetFlow thing. I have no idea what values to use on Max Flows, Hop Limit and on all this timeout settings.
Is it enough to select "IP" in "Flow Tracking Level"?
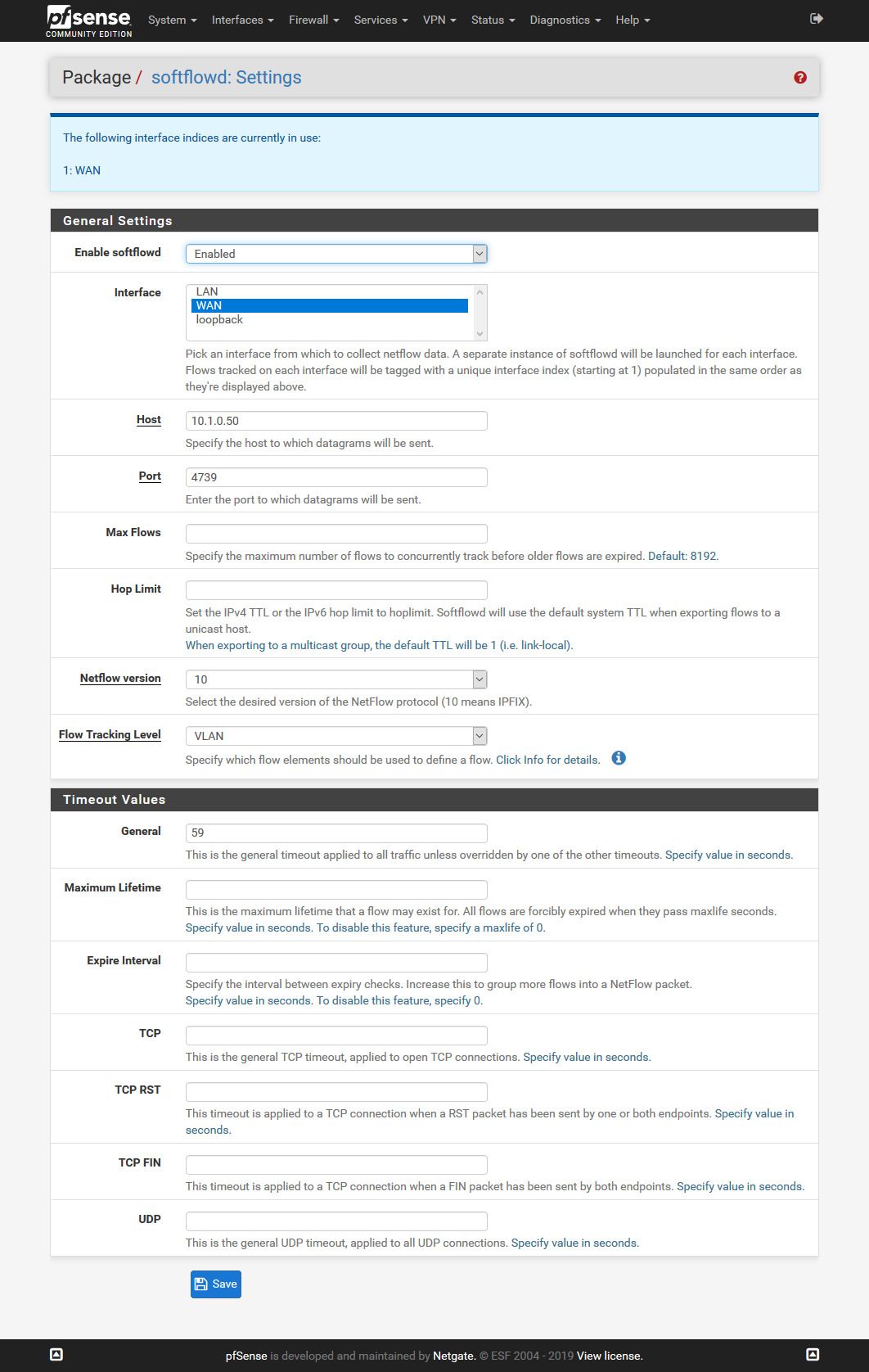
This this from PRTG but is over my head:
Make sure that you set an Active Flow Timeout in the sensor settings that is one minute greater than the flow timeout value that you set in the target device.
For more information, see https://kb.paessler.com/en/topic/66485.I did set the filter to Port[25] or Port[465] or Port[587] or Port[2525] or Port[2526]
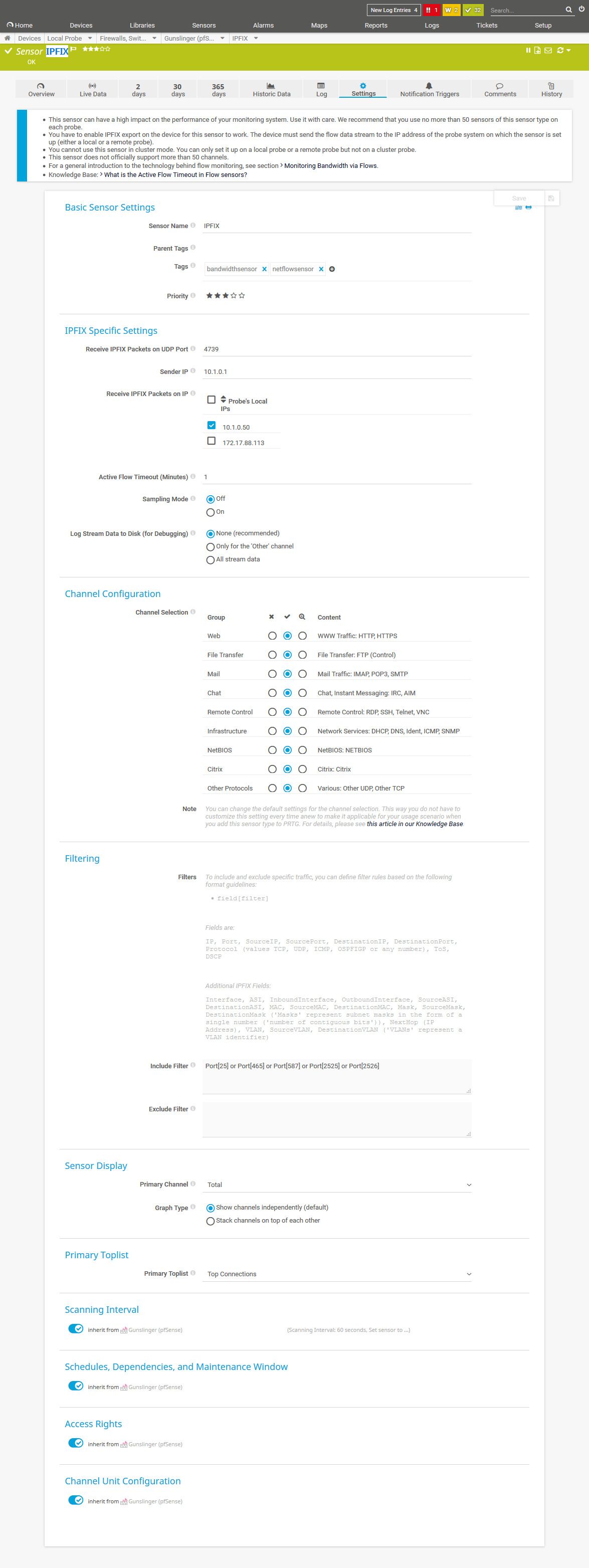
Here i did retrieve and send a mail with Thunderbird. Is it normal that i don't see the IP from my workstation?
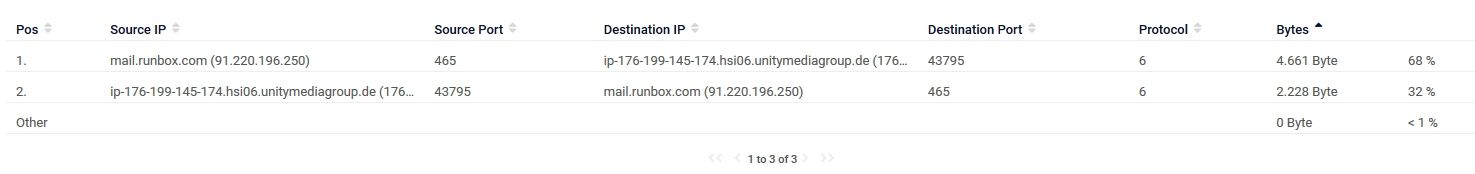
This is some other stuff i see. Stuff i don't know what it is:
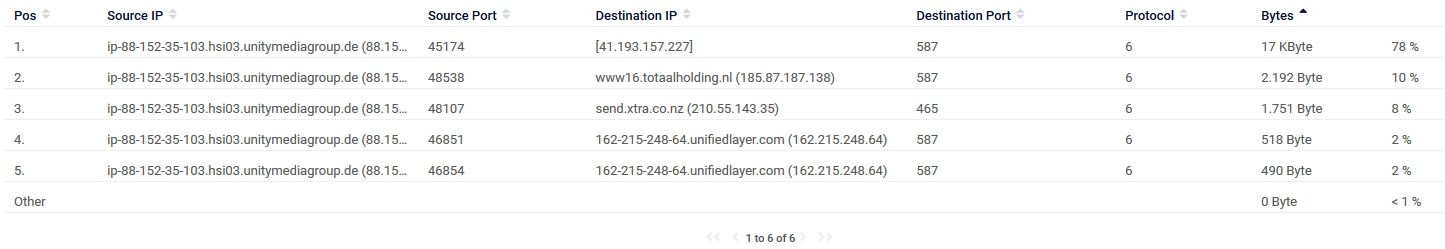
-
After my last posting i see this:
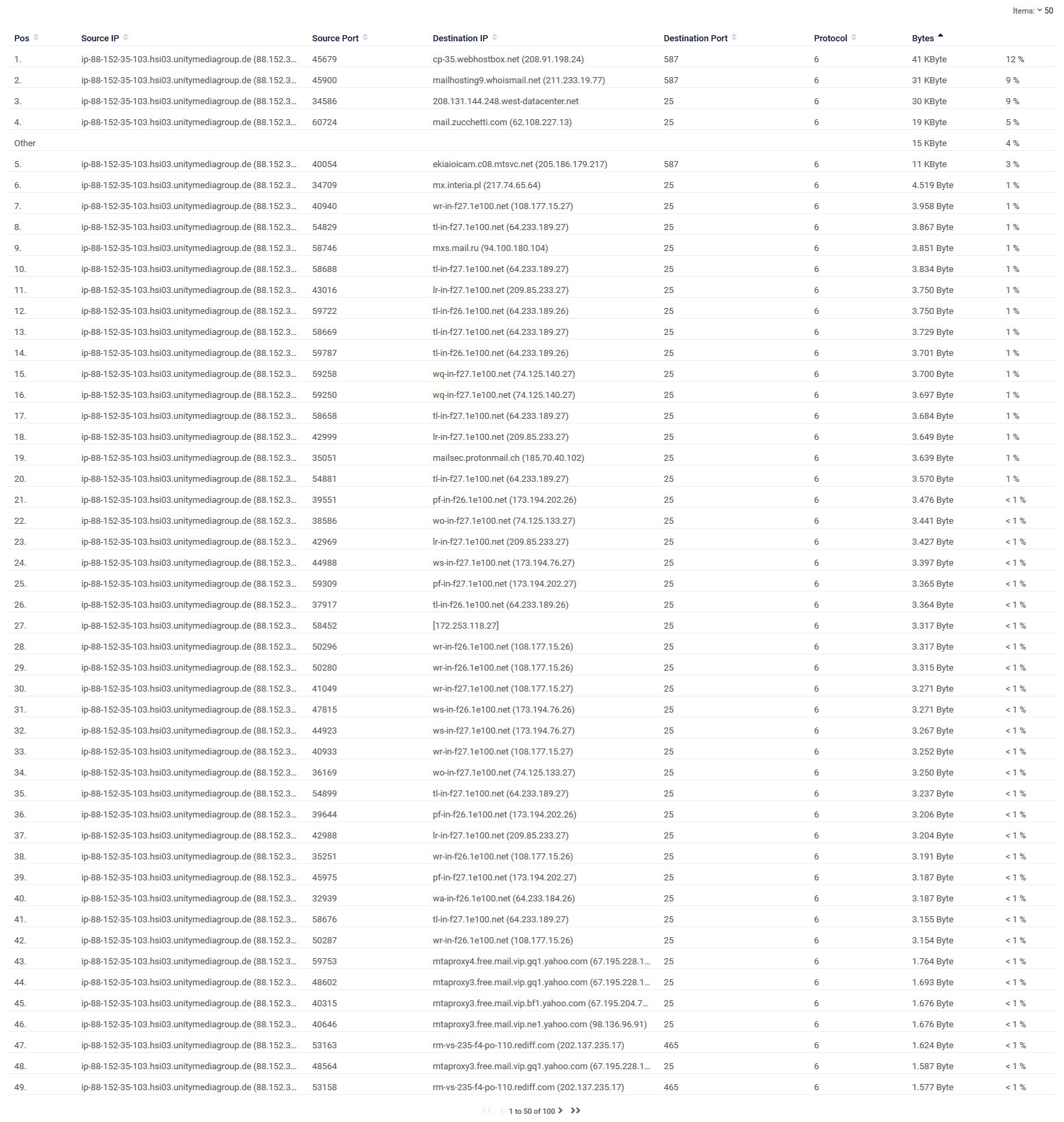
And ~50 new entries on the abuse website.
