LAN, use opt as lan interface
-
@netgater said in LAN, use opt as lan interface:
My pc can get .56.1/24 via the Dhcp but i cannot even ping igb2 interface. I cannot get to anywhere.
And what rules did you put on this new interface you created? Out of the box lan gets any any rule... But when you create new interfaces there will be no rules..
Where did you read here that you create a bridge.. NO!!! that is really never going to be the correct answer.. And no you wouldn't do that for what your wanting with different network your .56/24 vs .55/24
Your a CCIE??? and you thought bridging was solution for bringing up another network??? Yeah a statement makes zero sense!!! Sorry but going to call BS on you being a CCIE.. Or even somewhat ready to even take your first ccna test..
Tried putting igb1 and igb2 to separate vlans to no avail.
Sorry dude but there is NO Fing way your a CCIE... More than happy to help people, but when you clearly mis represent your skill set it is not possible to help you in any sort of useful manner..
-
@johnpoz woah, why so aggressive? Sorry for the typo 56.10 i assigned .56.10 to 56.100 as dhcp range..I'll hang around a bit hoping for some matured level headed person in this forum to help me.
I have no idea what works in pfsense mo idea how it behaves never configure Gui based router in my life so forgive me. I'm tried bridge because someone else in this forum said it worked for them.
Im pretty sure you're smarter than me. So let's get that out of the way. -
Your a CCIE and you have no idea how to setup an interface with an IP and connect it to a switch? And not clue to basic firewall rules?? Really?? Yeah sorry not buying it in the least....
Nor how to do basic troubleshooting? On why you can not ping the new interface you setup?
As to being aggressive - I work in the field, and don't like users just claiming creds they clearly do not have!!
Maybe I should stop into a doctor forum and claim to be a surgeon ;) Then ask how to open the bandaid package..
So your client got an IP from the dhcp setup... So clearly your L2 is working, any ccie would understand that... So lets see these rules you put on your new interface... Can you figure out how to post a screenshot?
-
@johnpoz ok Sir, you have my utmost respect and admiration. Can you please forgive whatever I said? Definitely don't want to open ticket with you if your the support engineer as your probably the king of your tiny bubble in whatever fortune 500 company your working at.
I admit, I'm the dumbest In the field. Can anybody else help me now please? -
Not without some basic info... Lets see your settings, lets see your firewall rules. If your client actually got a IP from your dhcp server you enabled on pfsense... Then clearly you have L2 connectivity.. So its a simple firewall rule setting most likely.
-
ahh the CCIE set you off right? deaden your ability to listen well. As I mentioned I lost my touch long ago so , I'm pretty sure your smarter than me.
If you read carefully and din't focus on CCIE and typos. I said I tried replicating all FW rules applied to LAN, it means i copied all default fw rules in the LAN and applied to my new interface except the anti-lockout rule. I didn't see any packet hitting the FW rules, no icmp, no nothing , zero packets) on the new interface as they do with the default LAN interface. "Then clearly you have L2 connectivity" god spare me the OSI layer bottom up troubleshooting. You sound like a network expert from Dlink supporting elderly who cannot access the internet.
Please god help me, still hoping there are anyone older than an 8th grader in this forum. Really need help. -
Again post up your rules you created... Can not tell you what is wrong without you actually showing it..
Here is what happens users says they did X, when they really did Y! If you do not post up what you actually have set there is no way for me to help you find what you did wrong..
Because it really is this simple.
Create IP on interface optX, lets call it 192.168.42.1/24
Enable dhcp server on this interface - lets call the scope 192.168.42.100-200Client gets 192.168.42.200 via dhcp, with gateway and dns pointing to 192.168.42.1
But without any rules on optX to allow, nothing going to happen.. Your not going to ping anything, your not going to get to the internet, etc..
Unless you dicked with the outbound nat, when you created your new interface pfsense would of automatically added this to your outbound nat.. But again without rules on optX to allow what you want - nothing going to work.
Common problem is user put TCP vs any for the rule - so no ping (icmp) or dns (udp) doesn't work...
-
@johnpoz you're the expert you know there are 3 default rules applied to lan on a new setup pfsense,
allow any any ipv4,
allow any any ipv6, and anti lockout rule.
I copied and applied the any any ipv4 and any any ipv6 (not that I need it) to the new lan (opt). No packet is hitting the rules. The fact that i got ip from the scope it means i should at least some udp packets there. But there is none. -
Dude I can not help you without you actually showing what you did!!!
Did you copy the rules and leave them set to lan net vs your new opt net??
Do you not know how to post a screenshot???
If you got an IP from your dhcp scope on pfsense... Then you should see traffic sent to pfsense IP... When you sniff...
Post up your settings!!! Did you put some rules in floating? Those are evaluated before your interface rules.
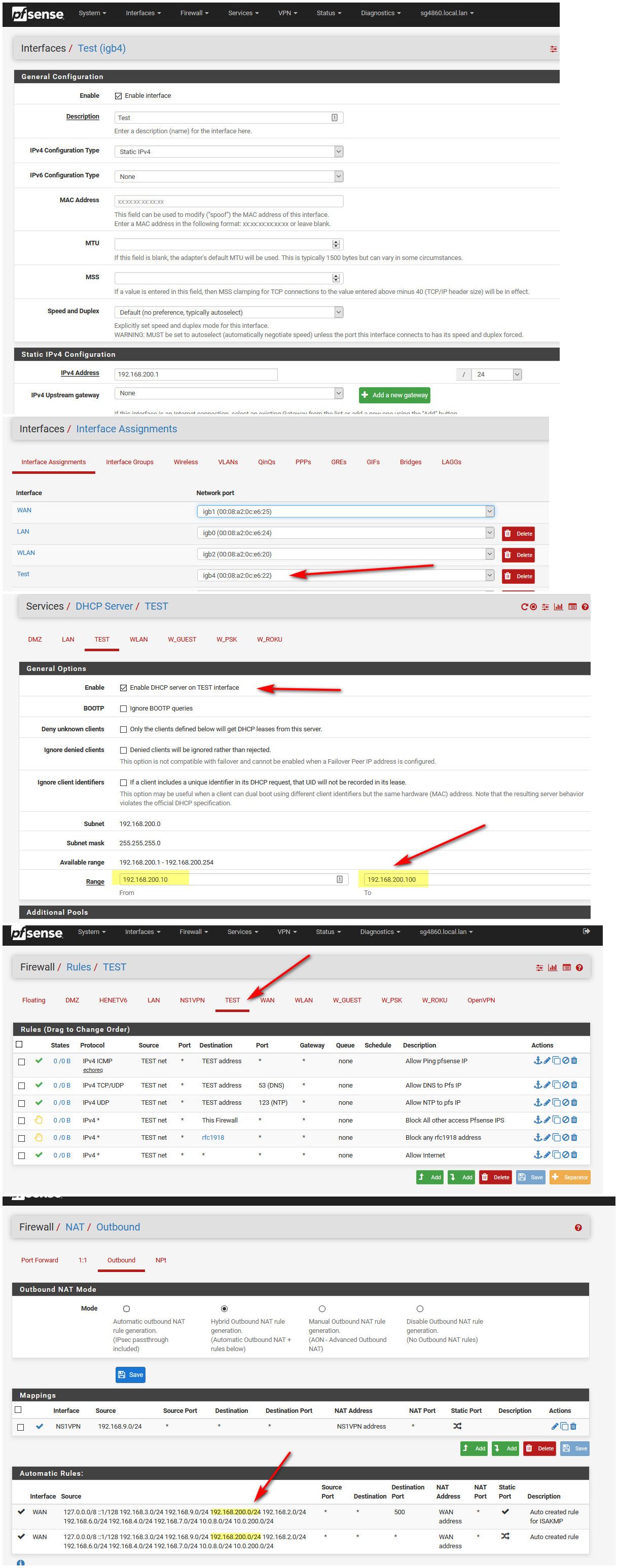
-
@johnpoz effing hell, nope, I'm out of here. Can't do this anymore. We're not going anywhere with this, clearly you and I are on a different frequencies.
Don't have time troubleshooting with an amateur network expert working as a tier 1 tech support in small market consumer-grade network vendor. Or a network engineer supporting 2 spoke sites or someone lower in the food chain, I'll give 10 yrs to get high 6 figure salary. You have the drive you'll get there.I give up. I honestly thank you for being helpful.
P. S.
If anyone can read this and have answer. I'm not here to troubleshoot with children. Im here for guidance how pfsense behave and how am i able to achieve what I'm trying to do. Not here te hear recommendations about best practice and topology suggestions. -
It behaves just like any other firewall. Layer 1, Layer 2, Layer 3. You remember the OSI model from your CCNA studies right?
How do i make my opt interfaces like a 2nd LAN interface. I just want to have a 2nd or 3rd lan interface that behave exactly like the LAN interface.
Do you want the new ports to be on the same broadcast domain or different broadcast domains than LAN?
@johnpoz just showed everything necessary to get a new interface working as a separate router/firewall interface (a different broadcast domain):
- Create the interface, enable it, and number it
- Enable the DHCP server on the interface (optional if you want to statically configure hosts)
- Add firewall rules to pass connections established by hosts on that interface into the firewall
- Be sure the interface source addresses match the rules for Outbound NAT
That is all that is required to get basic connectivity for those hosts. Of course, you have to do everything you need to do to get Layer 2 connectivity between the hosts and the router interface port.
-
We're not going anywhere with this
Nope not going to get anywhere when mister ccie can not figure out how to show is work for validation..
Lets see your sniff you did.. Clearly the dhcp discover got there if your client actually got dhcp from pfsense interface you setup... But you can not show us this?
What your saying is not actually possible - if you got dhcp from pfsense, then you would see traffic via a sniff.. It wouldn't of been able to hand you dhcp if not, etc..
If you can not be bothered to show us what you actually did, vs what your saying your doing - since clearly that is not working.. Then no we are never going to get anywhere.
But you know what happens all the time - even non ccie does this...Is they set the firewall rule to be tcp vs any... And then can not figure out why its not working... Or they put the wrong source net on the rule, etc.. But guess you know the 2 second screenshot showing what you did is too much trouble..
-
if you think that you have already done as @johnpoz and derelic suggested but it's still not working there must be something wrong on what you did, it's a realy simple implementation and there are no bug or malfunction on pfsense that can prevent that from working, only layer 8. that's why we always ask for screenshot, most of the time -> ppl says they did X, when they really did Y unintentionally, 4 or more eyes are better than 2.
-
It worked guys thank you very much to @johnpoz for your patience it works for me. Sorry, I didn't have access to my router yesterday hence couldn't provide any screenshots.
You acting like a dick from the get go, kind of overshadowed your awesomeness. Thanks anyways. -
Dick? Really? Calling you out on calling yourself a ccie when clearly everyone knows that is not even close to true is not being a dick... That is just calling someone out on their BS!
So what was the problem, only tcp for the rule? Wrong source?
Maybe you had policy route on the rule? But that wouldn't of stopped ping to pfsense IP? Only ping to other lan.. That is another common mistake.