IPv6 and VLAN sanity check
-
Hello, I am new to IPv6 so trying to get my head around how it gets configured with all the interfaces etc. I would like to know best practices how I should configure IPv6 across all my vlans. I have got IPv6 working on all my interfaces through trial and error, so seek a review just to make sure.
I get a /56 prefix from my ISP. I have set DHCPv6 on WAN. These are the WAN settings:
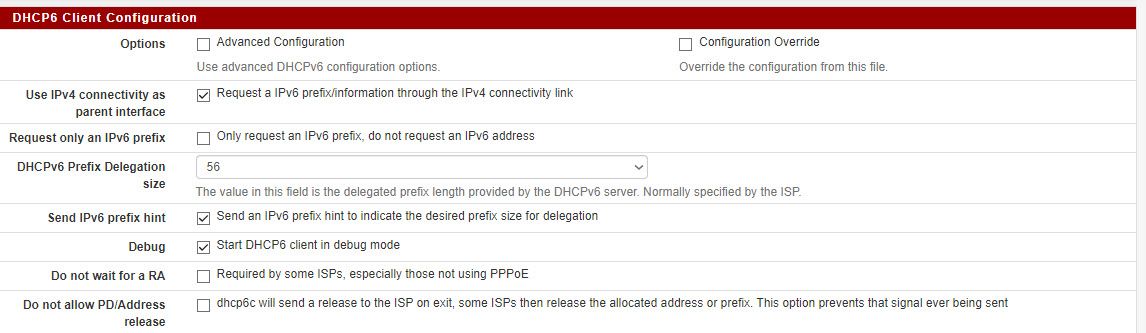
These are my LAN settings:
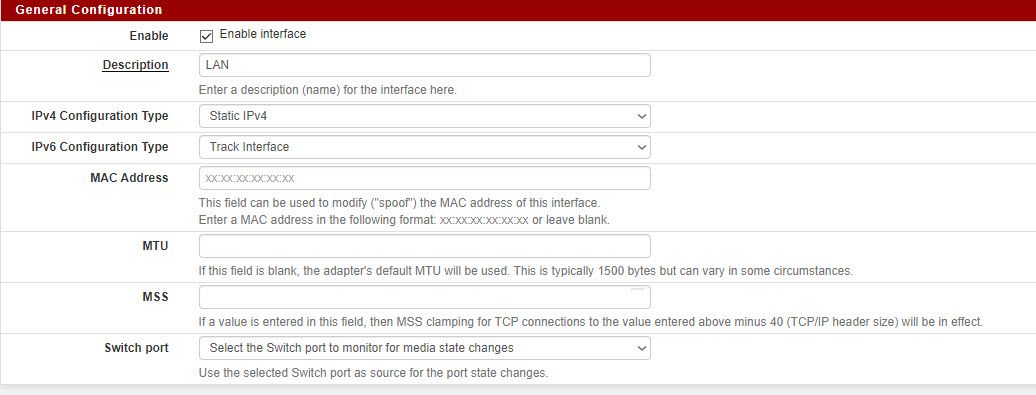
This is one of my VLANs (CAMERA) settings

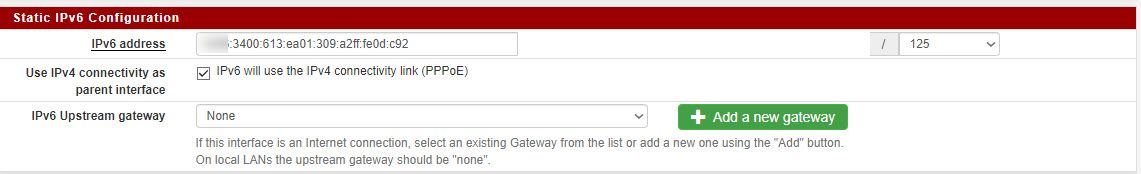
and the corresponding DHCP6 settings:
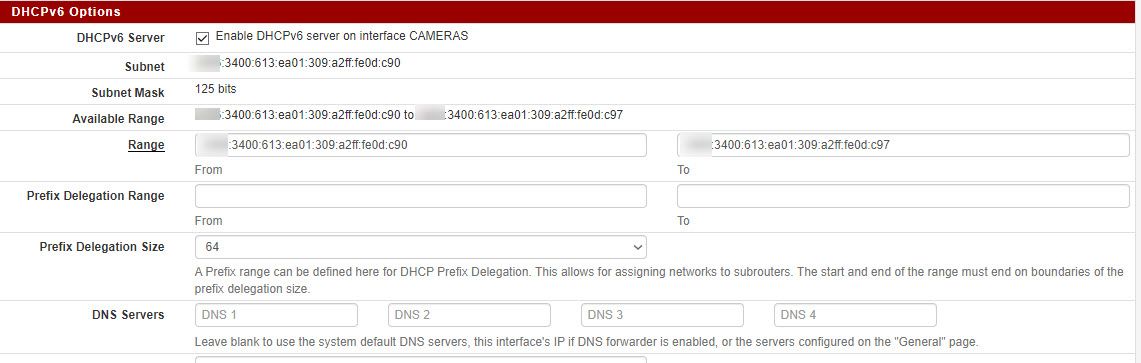
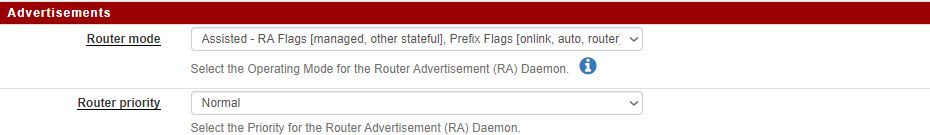
and Router advertisements
These are the firewall rules (CAMERA VLAN shown), but I have it for WAN too:

I have blurred the first quartet for privacy. Let's assume they start with 2001 for this example.
Questions:
-
Are the settings on WAN and LAN supposed to be as they are?
-
Are the firewall rules correct?
-
I read somewhere that for IPv6, each LAN segment should be a /64 subnet. By using /125, does that break best practices.
-
I have used Track Interface for LAN, should I be using DHCP6 instead?
-
Should I divvy up the /56 into blocks of /64?
eg LAN interface start: 2001:3406:0613:0601::1 (Cant change this at present)
CAMERA interface start: 2001:3406:0613:0602::1
VLAN3 interface start: 2001:3406:0613:0603::1 -
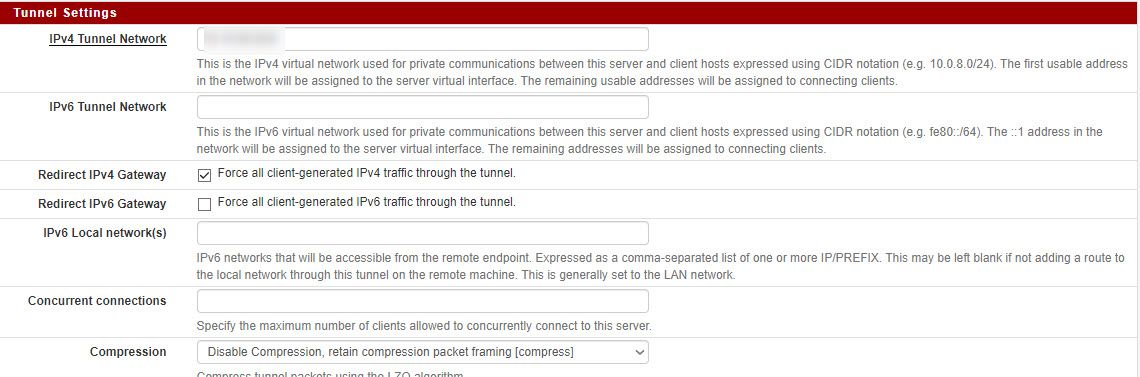
I have an OpenVPN interface running, I would like to configure that with IPv6. Am I guessing correctly, I can use VPN interface start: 2001:3406:0613:0605::1
but what address do I use for the setting: IPv6 Local network to set it on LAN?
Thanks very much.
-
-
Why are you configuring a static LAN? With SLAAC, you get static addresses automagically. For each LAN or VLAN, configure for SLAAC and select which prefix ID you want to use. You can use any between 0 & ff, with the main LAN typically 0. Also, you use each ID only once. You may have to configure the firewall according to your needs.
Start by getting the main LAN working and then add the VLANs, following the config you used for the LAN as an example.
-
@alnico said in IPv6 and VLAN sanity check:
I read somewhere that for IPv6, each LAN segment should be a /64 subnet. By using /125, does that break best practices.
While it is technically functional, it is not best practice to use anything smaller than /64. One of the biggest challenges when going to IPv6 is unlearning the practices of IPv4;
a) there is no shortage of IP addresses, so while it seems wasteful to have 4 devices on a /64, your /56 assignment works out to 256 /64s, is it realistic to think you will use all 256 subnets is a short time period, if so, ask your upstream for a /52.
b) There is no more security offered by NAT of private IP space; all Global Unicast IPv6 addresses are publicly reachable, make sure your firewall rules are configured accordingly. While there is some discussion about using Unique Local addressing to parallel the operation of IPv4; the protocol architects tend to frown on that.
Certainly there is a use case that has come up on the forum here about using ULA as an overly with ISP assigned prefixes when the prefix might not be constant, this seems to be counter to the concept of IPv6.Should I divvy up the /56 into blocks of /64?
eg LAN interface start: 2001:3406:0613:0601::1 (Cant change this at present)
CAMERA interface start: 2001:3406:0613:0602::1
VLAN3 interface start: 2001:3406:0613:0603::1
That is entirely up to you, as @JKnott points out, you can use between 00 and ff. If you like it neat and tidy, you can map VLAN numbers directly to the network assignments, so VLAN 1 becomes 2001:3406:0613:0601::/64, VLAN 2 2001:3406:0613:0602::/64... VLAN 255 2001:3406:0613:06ff::/64
I have an OpenVPN interface running, I would like to configure that with IPv6. Am I guessing correctly, I can use VPN interface start: 2001:3406:0613:0605::1
Yes, that will work.
-
@alnico said in IPv6 and VLAN sanity check:
each LAN segment should be a /64 subnet. By using /125, does that break best practices.
YES!! There is ZERO reason not to use /64!!
-
@awebster said in IPv6 and VLAN sanity check:
I read somewhere that for IPv6, each LAN segment should be a /64 subnet. By using /125, does that break best practices.
While it is technically functional, it is not best practice to use anything smaller than /64. One of the biggest challenges when going to IPv6 is unlearning the practices of IPv4;
Yep, always use /64. The exception would be on point to point links, where a /127 is used, as it provides a bit more security than a /64.
There is no more security offered by NAT of private IP space; all Global Unicast IPv6 addresses are publicly reachable, make sure your firewall rules are configured
NAT provides no better security than a properly configured firewall. Since pfSense starts with deny all, it's OK.
as @JKnott points out, you can use between 00 and ff. If you like it neat and tidy, you can map VLAN numbers directly to the network assignments, so VLAN 1 becomes 2001:3406:0613:0601::/64, VLAN 2 2001:3406:0613:0602::/64... VLAN 255 2001:3406:0613:06ff::/64
What I do is have my prefix match up with my IPv4 address blocks. For example, my main LAN is 172.16.0.0 /24 and prefix 0. Then I have a test LAN on 172.16.4.0 and prefix 4 and OpenVPN is 172.16.255.0 and ff.
-
-
Don't forget, you can configure OpenVPN to carry both IPv4 and IPv6.