I can't understand any of the Virtual IP/Proxy ARP/CARP documentation
-
Why is this so complicated to use multiple public IP addresses from your ISP?
Can I just put a switch between the ISP's router and use 2 public IP's directly on my 2 routers without having all this convoluted mess?If not, what I'm trying to to is put a 2nd public IP address on the WAN interface of another router and send anything destined for that public IP address to the WAN of that router. Any detailed examples of how to accomplish this?
-
@dlogan said in I can't understand any of the Virtual IP/Proxy ARP/CARP documentation:
Why is this so complicated to use multiple public IP addresses from your ISP?
Can I just put a switch between the ISP's router and use 2 public IP's directly on my 2 routers without having all this convoluted mess?
If not, what I'm trying to to is put a 2nd public IP address on the WAN interface of another router and send anything destined for that public IP address to the WAN of that router. Any detailed examples of how to accomplish this?@dlogan , I don't get your full request, but let me try to help you.
I assume you have a subnet assigned to your connection from your ISP. One address you are using on your PFSENSE. From your message, I derive that you wish to use a second IP address on a second PFSENSE. If so, just set up the second PFSENSE and assign the IP address to that installation.
If you wish to add a second address to a PFSENSE, just go to Firewall-Virtual IPs and add an IP alias.
If you wish to run your firewalls redundant, first configure HA (system-high availability) see: https://docs.netgate.com/pfsense/en/latest/highavailability/configuring-high-availability.html
and configure an IP shared address under Firewall-Virtual IPs.It shouldn't be so hard to set up at all if you have both firewalls connected to the ISP equipment.
Niels
-
"If so, just set up the second PFSENSE and assign the IP address to that installation."
And plug it into what? My ISP's router (AT&T fiber) only provides one functioning port for me to plug into.
"If you wish to add a second address to a PFSENSE, just go to Firewall-Virtual IPs and add an IP alias."
And then do what? This is exactly what I'm talking about. The documentation tells you how to assign the IP....then I do what with it? I need to actually use the IP address...
I put a virtual IP, assigned it to a port bridged to my WAN port, do a 1:1 NAT from the virtual IP to an IP like 172.16.0.1, assign the 172.160.0.1 on my laptop's NIC, plugged into the bridged port on the pfSense, assign the NAT'd public OR the ISP router's gateway as my gateway, and I can't communicate with anything.It is not as simple as "simply assign it to an interface." I need to be able to use this new IP address just as I'm using the main public IP on my WAN.
I'm not doing redundant/HA.
I can't plug both into the ISP equipment. That's why I was asking if I could put a switch between the two.
-
@dlogan said in I can't understand any of the Virtual IP/Proxy ARP/CARP documentation:
The documentation tells you how to assign the IP....then I do what with it?
Whatever you want.. Not sure why users think documentation of a firewall, should go into every possible scenario on how to do X with it..
Once you create a vip on your wan for your second public IP you could use it in port forwarding, you could setup a 1:1 nat with it to something behind pfsense. You could use it for outbound connections, so some clients get natted to the normal IP on the wan interface, and some get natted to the VIP address.
What exactly are you wanting to do with it?
, assigned it to a port bridged to my WAN port,
WTF?? That makes ZERO sense and BORKED for sure..
If you want say box 172.16.0.x to use this VIP for its public IP, then create 1:1 nat using the vip, or port forwards - and adjust your outbound nat so this client uses this VIP.
-
Well, you said it, it makes no sense.
https://docs.netgate.com/pfsense/en/latest/book/firewall/methods-of-using-additional-public-ip-addresses.html
"To assign public IP addresses directly to hosts behind the firewall, a dedicated interface for those hosts must be bridged to WAN. When used with bridging, the hosts with the public IP addresses directly assigned must use the same default gateway as the WAN of the firewall: the upstream ISP router. This will create difficulties if the hosts with public IP addresses need to initiate connections to hosts behind other interfaces of the firewall, since the ISP gateway will not route traffic for internal subnets back to the firewall."
-
That would be an actual PUBLIC IP, not a VIP or rfc1918 address... you wouldn't be using 172.16 for example..
This drawing is pretty clear - you are talking about this correct.
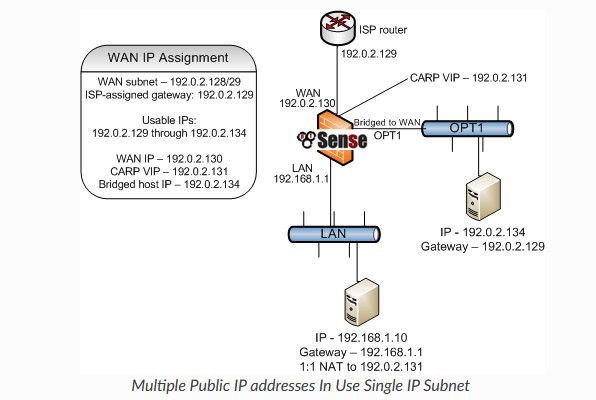
In that scenario you passing through via a bridge to a client a public IP, and the VIP is being used for a different client on a natted rfc1918 network.
-
@dlogan What you are trying to do is difficult because you have an interface network and not a subnet routed to your interface address. You want to do something that is normally accomplished by routing but you cannot route an interface address into another inside network because it is not routed to you.
You have four choices:
- Put a switch between your ISP and your WAN ports and just assign two different addresses to both pfSense and the other router's WAN. Your ISP might or might not support this. (Some ISPs put weird/nonsense limits on the number of MAC addresses, etc.) The pfSense firewall would not be involved in the traffic flow to/from that router at all.
- Bridge an inside interface with the WAN and put the router WAN on the inside bridge port. Your ISP might or might not support this as above. The pfSense firewall could be involved in the traffic flow using firewall rules on the bridge member interfaces if properly-configured.
- Use 1:1 NAT to NAT one of the interface addresses (an IP alias VIP on your pfSense WAN) to the inside address of the router WAN (A private RFC1918 address, usually). This is what people commonly do when they absolutely have to use an ISP router on the outside for various reasons but want to use a pfSense firewall behind that.
- Tell your ISP you need another subnet routed to your WAN address. You can then route that subnet properly to an inside network and use it directly on inside devices.