Mobile IPsec clients cannot see traffic from LAN
-
LAN: 10.10.10.0/24
IPsec: 10.10.12.0/24pfSense: 10.10.10.1
IPsec Host: 10.10.12.1
LAN Host: 10.10.10.20Packets from the IPsec host reach the LAN host, but packets from the LAN host never reach the IPsec host.
For example, during a ping from the IPsec host 10.10.12.1 to the LAN host 10.10.10.20, the ICMP echo request reaches 10.10.10.20, which sends a reply. The ICMP echo reply reaches pfSense and be seen on the LAN interface (see below):
[2.4.4-RELEASE][root@pfSense.localdomain]/root: tcpdump -ni ue0 icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on ue0, link-type EN10MB (Ethernet), capture size 262144 bytes 13:53:43.579030 IP 10.10.12.1 > 10.10.10.20: ICMP echo request, id 108, seq 1, length 64 13:53:43.579443 IP 10.10.10.20 > 10.10.12.1: ICMP echo reply, id 108, seq 1, length 64 13:53:44.595713 IP 10.10.12.1 > 10.10.10.20: ICMP echo request, id 108, seq 2, length 64 13:53:44.596197 IP 10.10.10.20 > 10.10.12.1: ICMP echo reply, id 108, seq 2, length 64 13:53:45.603382 IP 10.10.12.1 > 10.10.10.20: ICMP echo request, id 108, seq 3, length 64 13:53:45.603821 IP 10.10.10.20 > 10.10.12.1: ICMP echo reply, id 108, seq 3, length 64But if we watch the IPsec interface, we only see the requests going out. The ICMP echo replies never show up on the IPsec interface (the last place we see them is on the LAN interface).
Requests only, no replies on IPsec interface (?)
[2.4.4-RELEASE][root@pfSense.localdomain]/root: tcpdump -ni enc0 icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on enc0, link-type ENC (OpenBSD encapsulated IP), capture size 262144 bytes 13:53:43.578991 (authentic,confidential): SPI 0xcb9f807f: IP 10.10.12.1 > 10.10.10.20: ICMP echo request, id 108, seq 1, length 64 13:53:44.595679 (authentic,confidential): SPI 0xcb9f807f: IP 10.10.12.1 > 10.10.10.20: ICMP echo request, id 108, seq 2, length 64 13:53:45.603340 (authentic,confidential): SPI 0xcb9f807f: IP 10.10.12.1 > 10.10.10.20: ICMP echo request, id 108, seq 3, length 64I have rules to pass any/any/any on IPsec and LAN:
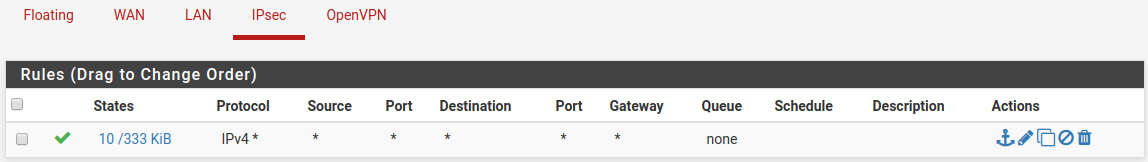
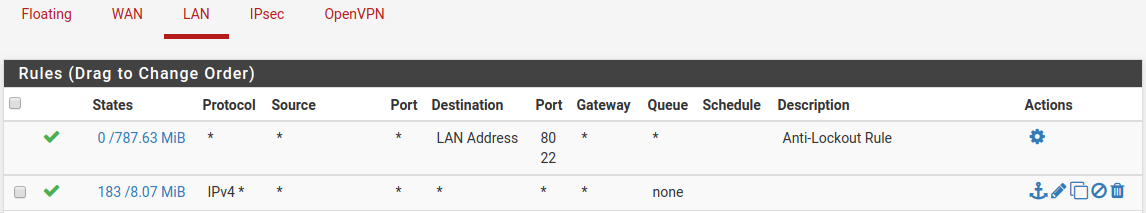
So I believe maybe this is a routing issue. Here's my routing table:
[2.4.4-RELEASE][root@pfSense.localdomain]/root: netstat -rn Routing tables Internet: Destination Gateway Flags Netif Expire default 192.181.160.1 UGS em0 10.10.10.0/24 link#6 U ue0 10.10.10.1 link#6 UHS lo0 10.10.11.0/24 10.10.11.2 UGS ovpns1 10.10.11.1 link#7 UHS lo0 10.10.11.2 link#7 UH ovpns1 127.0.0.1 link#3 UH lo0 192.168.10.0/24 link#6 U ue0 192.168.10.50 link#6 UHS lo0 192.181.160.0/19 link#1 U em0 192.181.169.71 link#1 UHS lo0 209.18.47.61 1c:b0:44:fe:0f:13 UHS em0 209.18.47.63 1c:b0:44:fe:0f:13 UHS em0But I have been unable to direct pfSense to send the traffic to the IPsec interface.
(As an aside, one interesting fact is that I also have an OpenVPN set up and the OpenVPN hosts, 10.10.11.0/24, CAN communicate with the IPsec hosts. It is only the LAN hosts which cannot)
-
My first thought is your USB ethernet is misbehaving.
How is your IPsec tunnel configured?