(SOLVED) IPSec with VPN clients
-
I have successfully connected two offices with pfSense and IPSec:
Office A:
LAN: 10.0.0.1/16
VPN: 172.16.123.1/24IPSec P2 configuration 1:
Local Subnet: LAN (which is 10.0.0.0/16)
Remote Subnet: 10.1.0.0/16IPSec P2 configuration 2:
Local Subnet: 172.16.123.0/24
Remote Subnet: 10.1.0.0/16Office B:
LAN: 10.1.0.1/16
VPN: 172.16.122.1/24IPSec P2 configuration 1:
Local Subnet: LAN (which is 10.1.0.0/16)
Remote Subnet: 10.0.0.0/16IPSec P2 configuration 2:
Local Subnet: 172.16.122.0/24
Remote Subnet: 10.0.0.0/16In both OpenVPN servers I have:
IPv4 Local networks: 10.0.0.0/16, 10.1.0.0/16
I am successfully pushing both routes to the VPN clients.Computers from LAN A can ping computers from LAN B over the IPSec tunnel. The opposite is also true.
VPN clients connected to Office A can ping computers in LAN A
VPN clients connected to Office B can ping computers in LAN BThe problem: VPN clients connected to Office A cannot ping computers in LAN B.
VPN clients connected to Office B cannot ping computers in LAN A.The firewall is wide open.
Any ideas?
-
@pvn Are you allowing (protecting in ipsec terminology) the openvpn ip's at the p2 level of ipsec?
A second thing would be, unless pf is also the default gateway for both sites, if hosts have necessary routes for other sites openvpn addresses. -
Yes, in both sites in IPSec configuration I have two P2: One for LAN to LAN and the second one for VPN subnet to LAN.
Local LAN to Remote LAN works. VPN to Local LAN also works. VPN to Remote LAN does not work.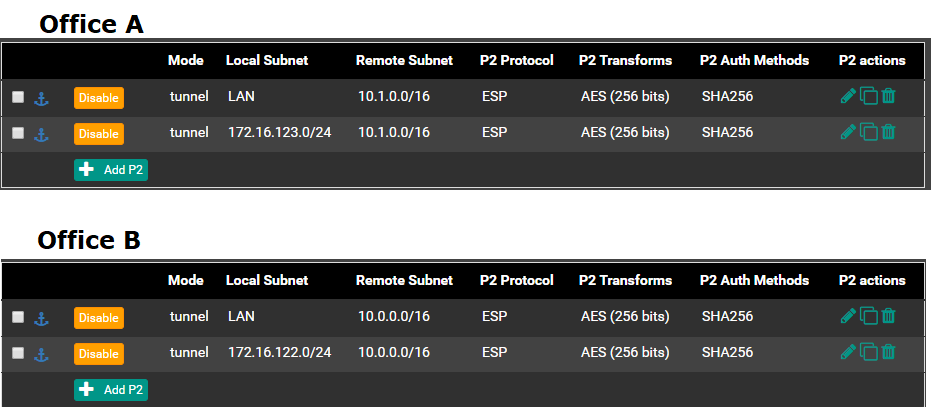
pfSense is default gateway in both sites.
-
@pvn I haven't tried it but it seems that 172.16.xx.xx is remote traffic for ipsec Try changing the mask on all p2 negotiations to 172.16.0.0/16 and or check ip sec logs...
If its not firewalling and not routing, it has to be ipsec.... -
172.16.123.0/24 is the IPv4 Tunnel Network for Office A
172.16.122.0/24 is the IPv4 Tunnel Network for Office BI am seeing the following in the IPSec logs:
Jan 5 09:44:11 charon 10[CFG] <con1000|4> config: 10.1.0.0/16|/0, received: 10.1.0.0/16|/0 => match: 10.1.0.0/16|/0 Jan 5 09:44:11 charon 10[CFG] <con1000|4> config: 172.16.122.0/24|/0, received: 10.1.0.0/16|/0 => no match Jan 5 09:44:11 charon 10[CFG] <con1000|4> config: 10.0.0.0/16|/0, received: 10.0.0.0/16|/0 => match: 10.0.0.0/16|/0 Jan 5 09:44:11 charon 10[CFG] <con1000|4> config: 10.0.0.0/16|/0, received: 172.16.123.0/24|/0 => no matchI am pretty sure my second P2 for the VPN subnet is incorrect. Could someone help me with that?
-
I solved it!
As suspected the problem was in the second P2 that is dealing with the VPN subnet. Each P2 should have a match on the other site but mirrored. And since I needed:
VPN clients connected to Office A to be able to access machines in Office B LAN
and
VPN clients connected to Office B to be able to access machines in Office A LANThis required a third pair of P2 on both sides.
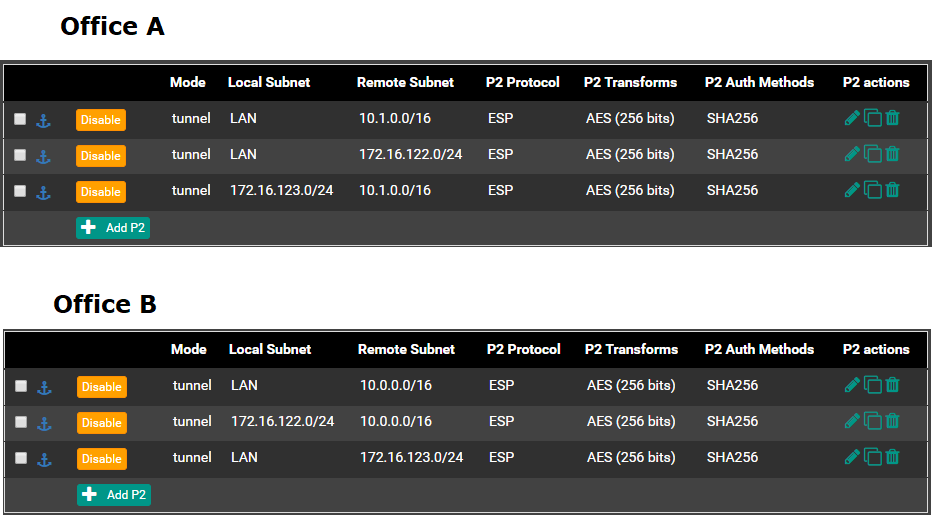
Thanks @netblues for the ideas!