Site-to-Site Authentication Fails
-
Good morning,
We recently setup a Site-to-Site IPSec between two pfSense routers but they do not seem to agree on authenticating per the logs. Site A currently uses CARP for HA behind my ISP's router (DMZ enabled on CARP IP) which is working with failover when setup with OpenVPN. Site B is connects to the ISP directly.
We have ensured that Site B's Remote ID is set to the internal address of Site A (192.168.2.5) to ensure that it matches up with the Local ID on Site A. Despite this, we are still encountering issues but are unsure if the issue is NAT related or somewhere else below are the configs of site as well as their logs.
Any assistance would be much appreciated. Thanks!
Site A config:
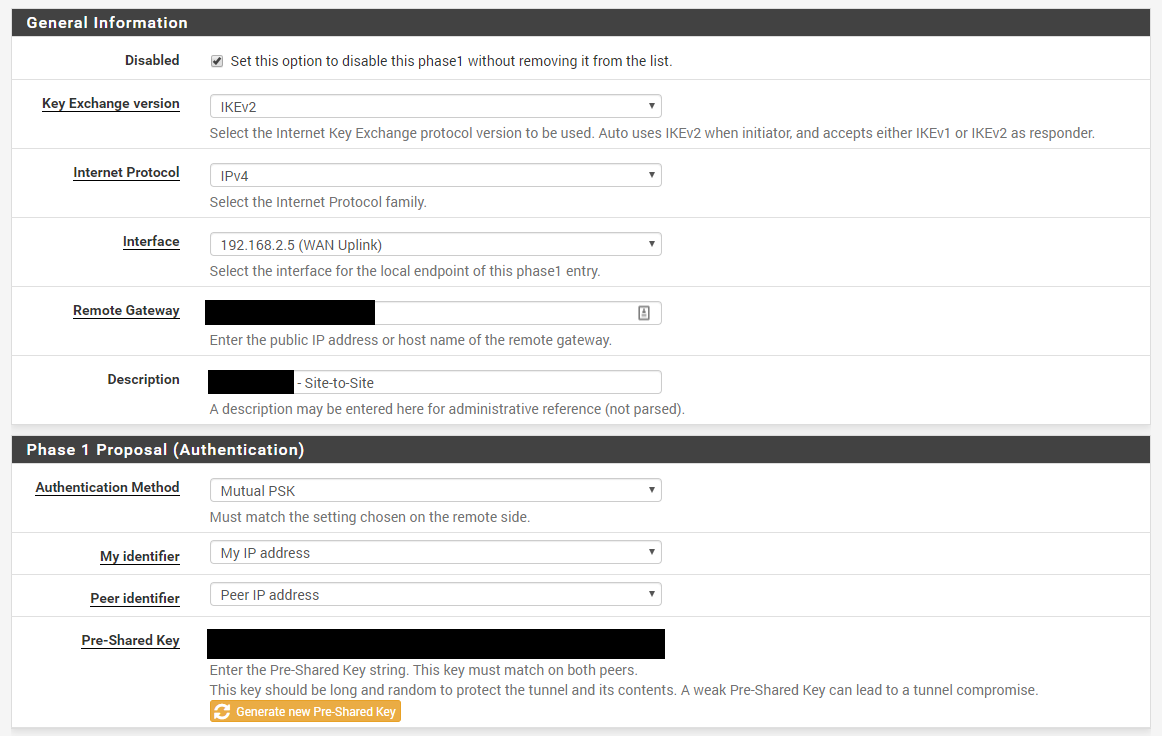
Site B config:

Site A logs:
05[IKE] initiating IKE_SA con1000[138] to 62.*.*.* 05[IKE] <con1000|138> IKE_SA con1000[138] state change: CREATED => CONNECTING 05[CFG] <con1000|138> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 05[CFG] <con1000|138> sending supported signature hash algorithms: sha256 sha384 sha512 identity 05[ENC] <con1000|138> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] 05[NET] sending packet: from 192.168.2.5[500] to 62.*.*.*[500] (464 bytes) 14[NET] received packet: from 62.*.*.*[500] to 192.168.2.5[500] (464 bytes) 14[ENC] <con1000|138> parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] 14[IKE] <con1000|138> received FRAGMENTATION_SUPPORTED notify 14[IKE] <con1000|138> received SIGNATURE_HASH_ALGORITHMS notify 14[CFG] <con1000|138> selecting proposal: 14[CFG] <con1000|138> proposal matches 14[CFG] <con1000|138> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 14[CFG] <con1000|138> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 14[CFG] <con1000|138> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 14[CFG] <con1000|138> received supported signature hash algorithms: sha256 sha384 sha512 identity 14[IKE] <con1000|138> local host is behind NAT, sending keep alives 14[IKE] <con1000|138> reinitiating already active tasks 14[IKE] <con1000|138> IKE_CERT_PRE task 14[IKE] <con1000|138> IKE_AUTH task 14[IKE] authentication of '192.168.2.5' (myself) with pre-shared key 14[IKE] <con1000|138> successfully created shared key MAC 14[CFG] <con1000|138> proposing traffic selectors for us: 14[CFG] 10.0.0.0/15|/0 14[CFG] <con1000|138> proposing traffic selectors for other: 14[CFG] 10.2.0.0/16|/0 14[CFG] <con1000|138> configured proposals: ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ 14[IKE] <con1000|138> establishing CHILD_SA con1000{41} reqid 7 14[ENC] <con1000|138> generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH N(ESP_TFC_PAD_N) SA TSi TSr N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] 14[NET] sending packet: from 192.168.2.5[4500] to 62.*.*.*[4500] (304 bytes) 14[NET] received packet: from 62.*.*.*[4500] to 192.168.2.5[4500] (80 bytes) 14[ENC] <con1000|138> parsed IKE_AUTH response 1 [ N(AUTH_FAILED) ] 14[IKE] <con1000|138> received AUTHENTICATION_FAILED notify error 14[CHD] <con1000|138> CHILD_SA con1000{41} state change: CREATED => DESTROYING 14[IKE] <con1000|138> IKE_SA con1000[138] state change: CONNECTING => DESTROYING Jan 12 07:03:36 charon 00[DMN] signal of type SIGINT received. Shutting down Jan 12 07:03:36 charon 00[CHD] CHILD_SA con1000{40} state change: ROUTED => DESTROYINGSite B logs:
06[CFG] <134> sending supported signature hash algorithms: sha256 sha384 sha512 identity 06[ENC] <134> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] 06[NET] <134> sending packet: from 62.*.*.*[500] to 94.*.*.*[500] (464 bytes) 06[NET] <135> received packet: from 94.*.*.*[500] to 62.*.*.*[500] (464 bytes) 06[ENC] <135> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] 06[CFG] <135> looking for an IKEv2 config for 62.*.*.*...94.*.*.* 06[CFG] <135> candidate: %any...%any, prio 24 06[CFG] <135> candidate: 62.*.*.*...test-project.com, prio 3100 06[CFG] <135> found matching ike config: 62.*.*.*...test-project.com with prio 3100 06[IKE] <135> 94.*.*.* is initiating an IKE_SA 06[IKE] <135> IKE_SA (unnamed)[135] state change: CREATED => CONNECTING 06[CFG] <135> selecting proposal: 06[CFG] <135> no acceptable ENCRYPTION_ALGORITHM found 06[CFG] <135> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 06[CFG] <135> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 06[CFG] <135> looking for IKEv2 configs for 62.*.*.*...94.*.*.* 06[CFG] <135> candidate: %any...%any, prio 24 06[CFG] <135> candidate: 62.*.*.*...test-project.com, prio 3100 06[IKE] <135> no matching proposal found, trying alternative config 06[CFG] <135> selecting proposal: 06[CFG] <135> proposal matches 06[CFG] <135> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 06[CFG] <135> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 06[CFG] <135> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 06[CFG] <135> received supported signature hash algorithms: sha256 sha384 sha512 identity 06[IKE] <135> remote host is behind NAT 06[CFG] <135> sending supported signature hash algorithms: sha256 sha384 sha512 identity 06[ENC] <135> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] 06[NET] <135> sending packet: from 62.*.*.*[500] to 94.*.*.*[500] (464 bytes) 06[NET] <135> received packet: from 94.*.*.*[4500] to 62.*.*.*[4500] (304 bytes) 06[ENC] <135> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH N(ESP_TFC_PAD_N) SA TSi TSr N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] 06[CFG] <135> looking for peer configs matching 62.*.*.*[62.*.*.*]...94.*.*.*[192.168.2.5] 06[CFG] <135> candidate "bypasslan", match: 1/1/24 (me/other/ike) 06[CFG] <135> candidate "con1000", match: 20/20/3100 (me/other/ike) 06[CFG] <135> ignore candidate 'con1000' without matching IKE proposal 06[CFG] <bypasslan|135> selected peer config 'bypasslan' 06[IKE] authentication of '192.168.2.5' with pre-shared key successful 06[CFG] <bypasslan|135> constraint requires public key authentication, but pre-shared key was used 06[CFG] <bypasslan|135> selected peer config 'bypasslan' unacceptable: non-matching authentication done 06[CFG] <bypasslan|135> no alternative config found 06[IKE] <bypasslan|135> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding 06[ENC] <bypasslan|135> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] 06[NET] sending packet: from 62.*.*.*[4500] to 94.*.*.*[4500] (80 bytes) 06[IKE] <bypasslan|135> IKE_SA bypasslan[135] state change: CONNECTING => DESTROYING 06[JOB] <134> deleting half open IKE_SA with 94.*.*.* after timeout 06[IKE] <134> IKE_SA (unnamed)[134] state change: CONNECTING => DESTROYING 00[DMN] signal of type SIGINT received. Shutting down 00[CHD] CHILD_SA con1000{99} state change: ROUTED => DESTROYING -
The logs are telling you that what is incoming does not match any configured tunnel.
In the site B logs:
06[CFG] <135> candidate: 62.*.*.*...test-project.com, prio 3100 06[IKE] <135> no matching proposal found, trying alternative config06[CFG] <135> looking for peer configs matching 62.*.*.*[62.*.*.*]...94.*.*.*[192.168.2.5]06[CFG] <135> ignore candidate 'con1000' without matching IKE proposalHard to say for sure with so much redacted, but it's at least not matching the local<->remote peer addresses even before it checks the IDs.
-
Site A:
Remote Gateway: remote.test-project.com
Local Identifier: 192.168.2.5 (CARP address of interface)
Remote Identifier: My peer address (remote.test-project.com)Site A updates the dynamic DNS of test-project.com with that of its external IP (since WAN IP is internal).
Site B:
Remote Gateway: test-project.com
Local Identifier: WAN IP
Remote Identifier: 192.168.2.5 (set manually)Site B updates the dynamic DNS of remote.test-project.com with that of its WAN IP.
Identifiers aside, the local address of Site A would not match the peer address of Site B outright due to Site A's IP being internal and Site B using a dynamic DNS to an external. Would this cause the issue?
-
NAT will make that trickier but usually you can get around that by setting appropriate identifiers. I wouldn't use hostnames in those fields for identifiers, though. It isn't handled there like it is in the remote gateway field. Try setting the identifiers explicitly to a value on both sides and see what happens.