How to tell if traffic if passing through VPN?
-
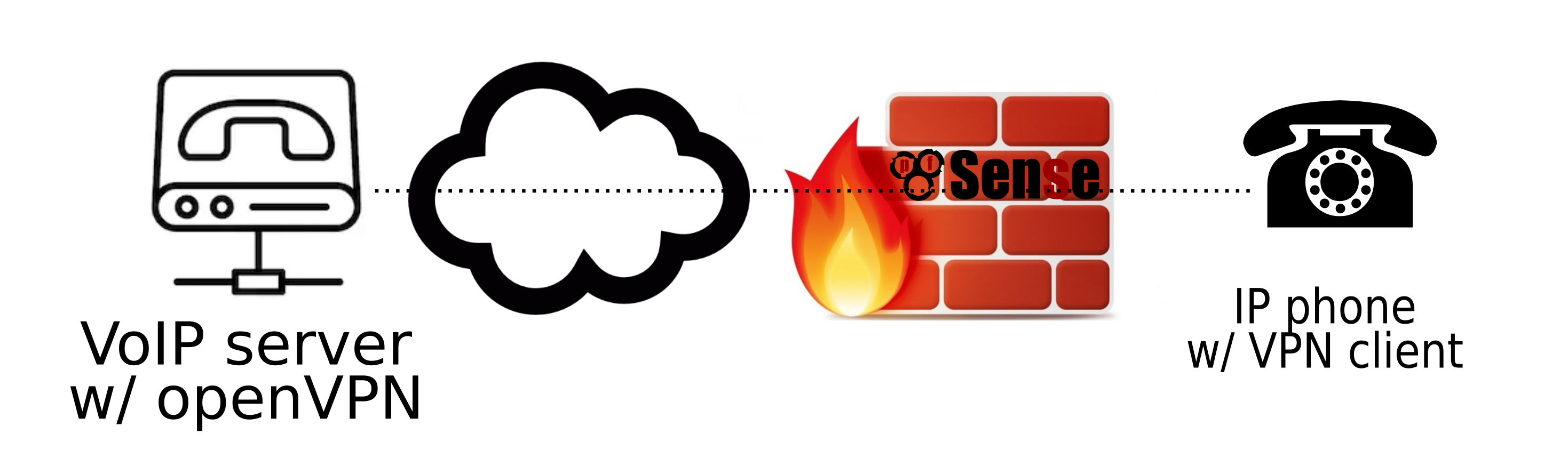
I have IP phone behind pfsense firewall / router onsite and a remote PBX server with openvpn server. The IP phone has VPN client and is set to connect to VoIP server through VPN. Both the VoIP and IP phone showing that the VPN is up and running.
- How can I verify that the traffic is actually going through the VPN and not just the regular internet traffic?
N.B. I tried packet capture and it does show "traffic" between the VoIP server and the IP phone.
-
I would check the open states for the phone IP in Diag > States.
I would expect to see only the OpenVPN state open to the server. By default that runs on UDP 1194 but could be running on any port though so might be hard to see.
You should specifically not see any SIP states though, UDP 5060-5062.
Steve
-
Thank you @stephenw10 , this was helpful. I did see some
1194traffic to the VoIP server on both state and Packet Capture (during active call) which is a good sign. I did also see some5060traffic as well on state and Packet Capture not sure if this is an issue.Of note, the server is set to direct the VPN IP range only through the OpenVPN server but not all client traffic.
LAN udp 192.168.30.21:5060 -> VoIP-server_IP:5060 MULTIPLE:MULTIPLE 33 / 25 15 KiB / 14 KiB WAN udp office_IP:5830 (192.168.30.21:5060) -> VoIP-server_IP:5060 MULTIPLE:MULTIPLE 32 / 25 15 KiB / 14 KiB LAN udp 192.168.30.21:45536 -> VoIP-server_IP:1194 MULTIPLE:MULTIPLE 26 / 24 4 KiB / 5 KiB WAN udp office_IP:64659 (192.168.30.21:45536) -> VoIP-server_IP:1194 MULTIPLE:MULTIPLE 26 / 24 4 KiB / 5 KiB -
Ok so I assume 192.168.30.21 is the phone here?
And just to be clear the OpenVPN client is running on the phone itself?
That's certainly how I understand it and what it looks like in that 1194 state.There is clearly some unencrypted SIP traffic from the phone there. You could try making a call and refreshing the states to see where the rtp traffic is, it might open more unencrypted states.
You could put in a block rule on LAN for the port 5060 traffic so it cannot open those states outside of the tunnel and see if you still have connectivity.
Steve