Routing Specific Device via VPN
-
Hi
I've got a PIA VPN configured which is used as the default gateway for all devices on OPT1, which has my mesh WiFi connected to it. These devices all present with the VPN providers IP Address and that works fine.Devices in my LAN (OPT0 ?) all route via the default gateway and present my static public IP Address, again that is working fine.
I want to send a device on the LAN out via the VPN. So I added a rule to LAN as follows:
Protocol: IPv4* Source: 192.168.1.191 (the device I want to go via the VPN) Port: * Destination: * Gateway: OPT3PIA_VPNV4Now the laptop can't get out at all. As soon as I disable this rule it works via the normal gateway.
How do I send one or more LAN devices out via the PIA VPN ?Thanks
-
Do you have a NAT rule to allow LAN devices (192.168.1.191) to be translated through VPN?
-
Thank for the reply.
Can you advise why a rule is needed on NAT for this to work on the LAN ?I have OPT1 configured and all traffic via that interface routes via the VPN, I've also setup a rule for some devices to route via the default gateway and that works.. Neither of these required any NAT rules.
Thanks
-
You need a nat rule to go out the vpn, just like you need a nat rule to go out any other interface from rfc1918 to public.
While your IP on your vpn interface would be the tunnel IP and not normally public, the vpn service isn't going to allow some other rfc1918 address - its only going to allow the IP it handed pfsense as the client.
So if you want other devices behind pfsense to go out that tunnel - you need to make it look to the vpn service like its pfsense client IP.. ie outbound nat.
Out of the box pfsense will create nat to your wan.. when set to automatic, so anything be it optX your normal lan - they would be natted to your wan IP when going out that connection.
when you create a new wan interface (which is what your vpn client connection becomes) you have to tell pfsense to traffic going out that interface to that IP..
Can be done with hybrid - example
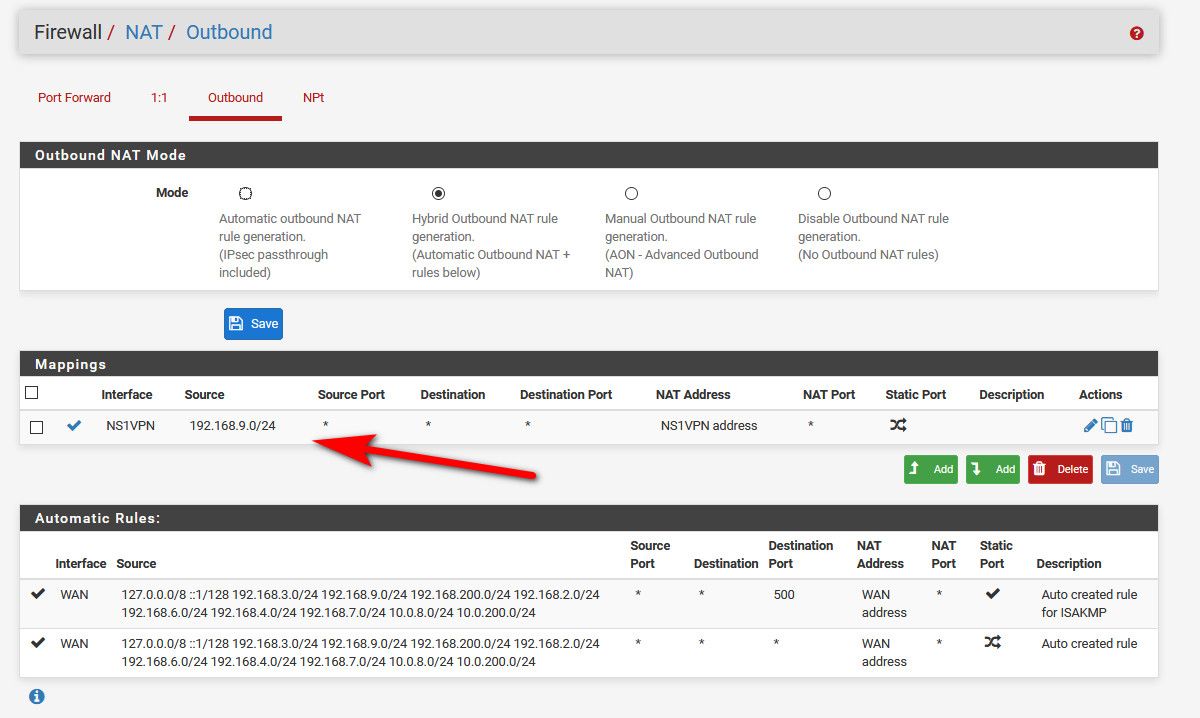
This allows devices on my lan (192.168.9/24) to be natted to the vpn interface IP. When I policy route traffic out that connection.
So post up your outbound nat - and we can take a look see if that looks correct.
Also post up your policy routing rule - rules are evaluated in order top to bottom, first rule to trigger wins - so if you have for example your policy route below some other rule that would allow the traffic out your normal wan - it wouldn't go out your vpn. -
Thanks that make sense.
I'd forgot I'd added the Outbound rule for OPT1 devices using OPT3PIA.I'll set this up and see how I get on.
Cheers