IPSEC not routing to LAN
-
I have setup an IPSEC VPN server. Connection is successful but can only access WAN and not LAN.
-
Virtual Address Pool is 172.16.0.0 - successfully getting an IP on my iphone
-
DHCP server range is 192.168.7.0
-
I can ping the iphone from the LAN successfully, but not the other way around
-
Firewall IPSEC rule is set to ip4 any to any
-
All WAN traffic goes through VPN successfully, no LAN traffic
-
Local Network set to 0.0.0.0/0 (under mobile clients)
The only interesting thing i found on the IPSEC log was the following: (-.-.-.- are my public IPs)
Jan 18 11:32:00 charon 12[CHD] <con-mobile|3> SPI 0x0ac300f6, src -.-.-.- dst -.-.-.- Jan 18 11:32:00 charon 12[CHD] <con-mobile|3> adding outbound ESP SA Jan 18 11:32:00 charon 12[CHD] <con-mobile|3> SPI 0xc46c79fb, src -.-.-.- dst -.-.-.- Jan 18 11:32:00 charon 12[CHD] <con-mobile|3> adding inbound ESP SA Jan 18 11:32:00 charon 12[CHD] <con-mobile|3> using HMAC_SHA2_256_128 for integrity Jan 18 11:32:00 charon 12[CHD] <con-mobile|3> using AES_CBC for encryption Jan 18 11:32:00 charon 12[CHD] <con-mobile|3> CHILD_SA con-mobile{3} state change: CREATED => INSTALLING Jan 18 11:32:00 charon 12[CFG] <con-mobile|3> config: 172.16.0.1/32|/0, received: ::/0|/0 => no match Jan 18 11:32:00 charon 12[CFG] <con-mobile|3> config: 172.16.0.1/32|/0, received: 0.0.0.0/0|/0 => match: 172.16.0.1/32|/0 Jan 18 11:32:00 charon 12[CFG] <con-mobile|3> selecting traffic selectors for other: Jan 18 11:32:00 charon 12[CFG] <con-mobile|3> config: 0.0.0.0/0|/0, received: ::/0|/0 => no match Jan 18 11:32:00 charon 12[CFG] <con-mobile|3> config: 0.0.0.0/0|/0, received: 0.0.0.0/0|/0 => match: 0.0.0.0/0|/0 Jan 18 11:32:00 charon 12[CFG] <con-mobile|3> selecting traffic selectors for us: Jan 18 11:32:00 charon 12[CFG] <con-mobile|3> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQDon't know what else to check, any ideas?
-
-
ping...any help?
-
I never managed to get 0.0.0.0 to work in classic IPSec via pfSense.
Once this P2 has been declared, pfSense passes ALL traffic through the interface and can no longer route its own LAN networks.
The solution for me was to use IPSec VTI tunnels which allow to manually manage the routing (no more implicit rules)
Using IPSec VTI, pfSense create a virtual interface, which greatly simplifies operations (static routing, dynamic / conditional routing, NAT, etc.)
You can find more informations at https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ipsec-routed.html ;)
coom
-
to route all the traffic though IPsec tunnel please follow the below configuration.
-
you need firewall Aliases.
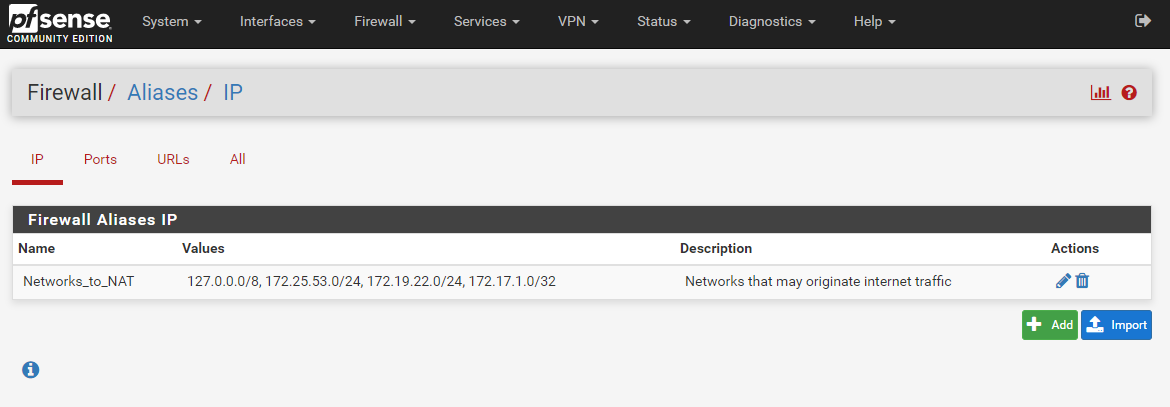
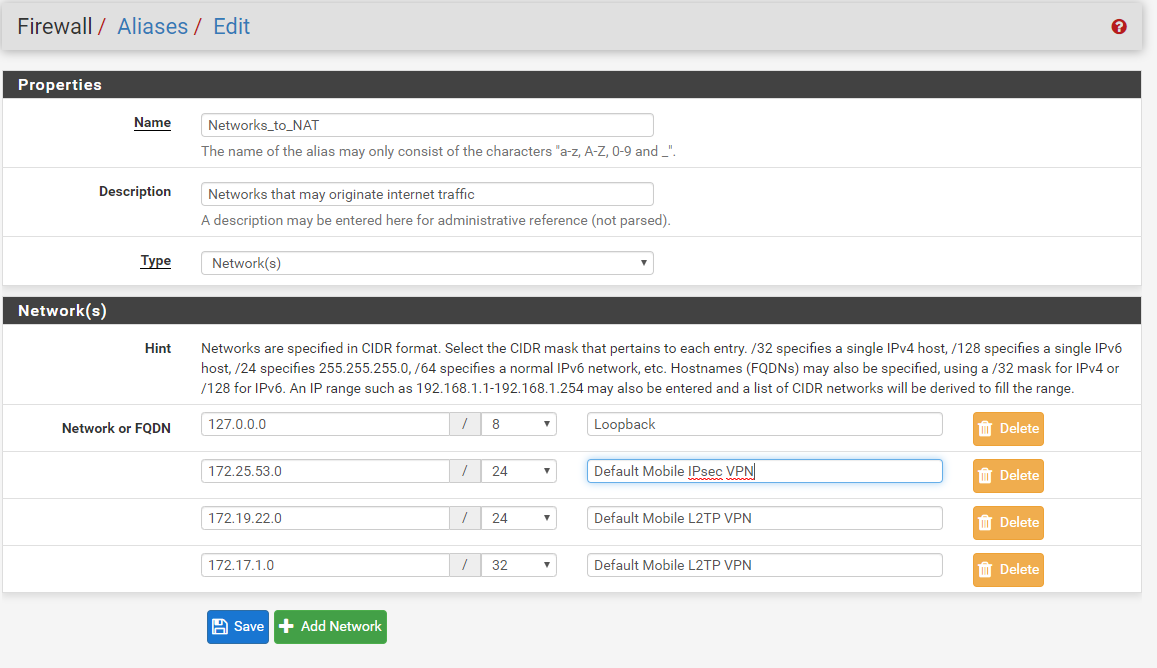
-
you need virtual IP for DNS routing could be any
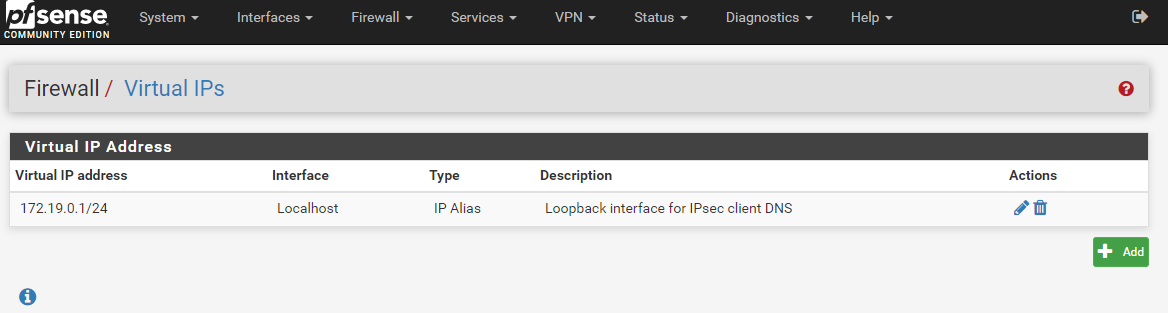
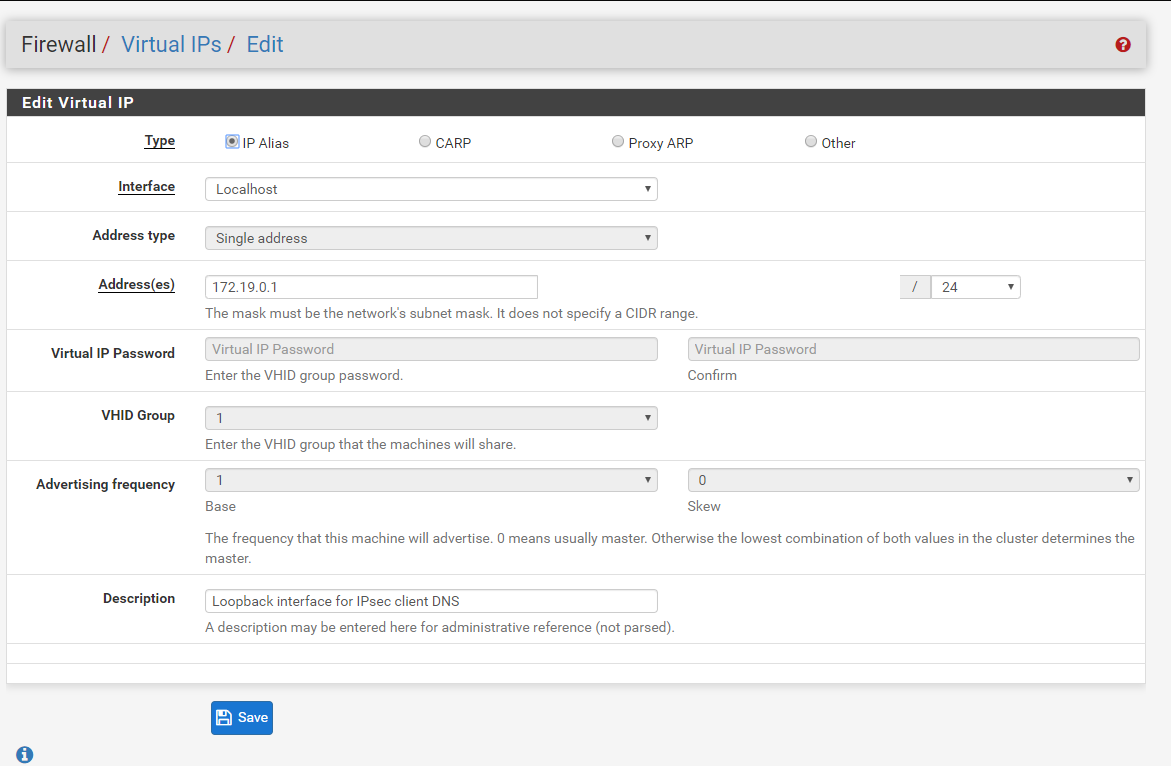
- Set the above virtual ip as DNS for vpn clients.
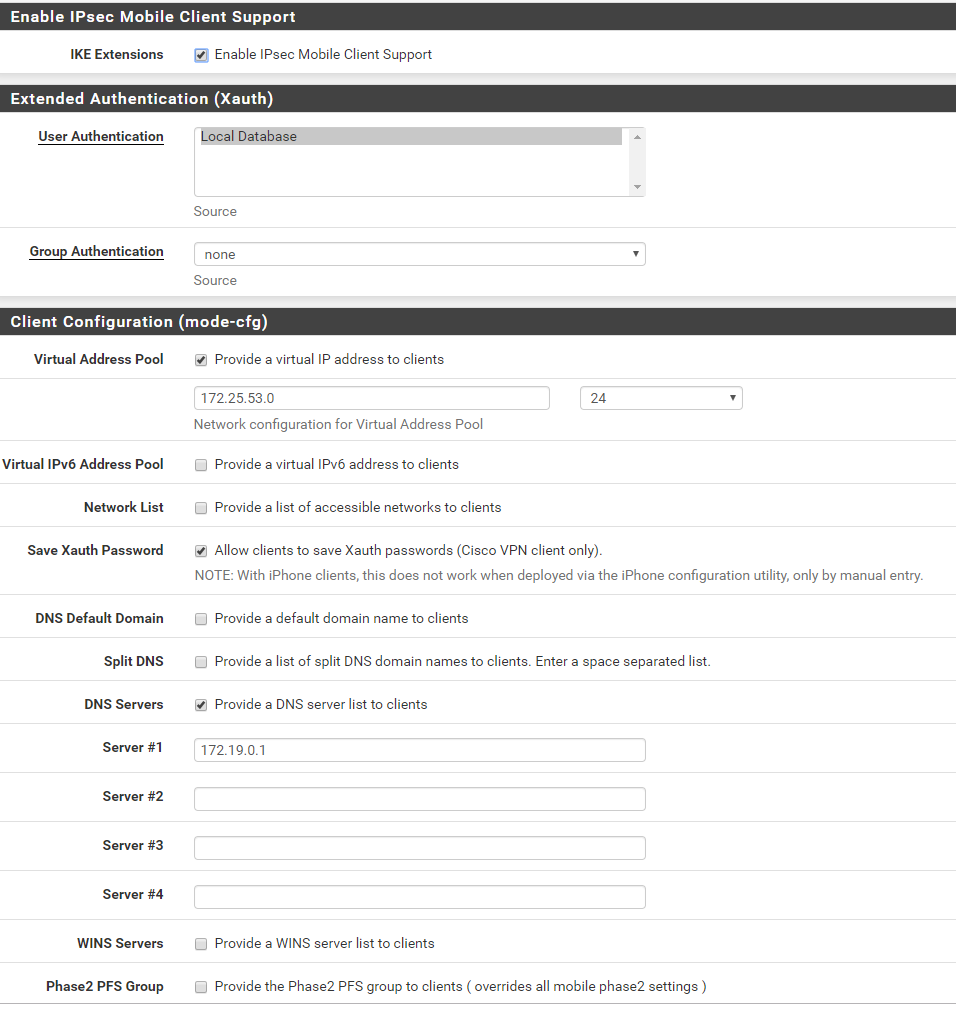
hope this should work for you.
Thanks
Daman -