Mapping ISP provided Static IP to MAC addresses -behind Pfsense
-
Normally, IPv6 uses the DUID for that. Also, are they providing addresses for each host? Or just a prefix and letting you manage your hosts? I'm on Rogers and get a /56 prefix from them. With the DUID, my prefix is unlikely to change, but Rogers knows nothing about what's behind my firewall. Also, MAC addresses are irrelevant off the local network, as they don't pass through the firewall. So, even if they were using the MAC to assign an address, they'd never see it.
Are they providing a prefix? Or just a single address?
-
@JKnott Thanks for your reply.. Its a /24. But they are enabling 1 IP per Mac address provided.
So my question is will NAT work for Port forwarding from the WAN, if the ISP can't see the MAC Address.?
-
@ros81 to answer your question... they are providing addresses for each host. Anyway to map this in Pfsense?
-
Would NAT 1:1 on Pfsense help? Mind it the VoIP server is not on a DMZ.
-
Why did I think IPv6 was involved? Anyway, the router part still stands. If you have a router, such as pfSense, they'll never see the MAC. There are firewalls that act like a bridge, but I don't know if pfSense can do that.
BTW, Telus also provides IPv6, so you'll want to consider that too, when you set up the firewall.
Also, please, Please, PLEASE learn to forget about NAT. It's a curse on networks that came about due to the IPv4 address shortage. As I mentioned, the proper solution is a firewall that filters without routing. With NAT, they'll only see a single MAC, that of the firewall WAN NIC, for every device behind it.
-
Thanks @JKnott
But I guess I need to use NAT as I'm working with 2 public IPs . One for the Pfsense box that is connected to the ISP bridged modem/router , and the other is the non-DMZ Voice server.
I just want to find the best method to implement proper NAT to external IPs, on the pfsense. -
You're still down to 1 MAC, which means you'll only get one IP. What are the servers running on? If Linux, you've already got a good firewall there. Linux is used in most of the consumer grade firewalls out there and some form of Unix on just about everything else. Even some Cisco gear runs on Linux.
I really wish people would forget about NAT, as it causes them to come up with poor solutions, instead of doing it the proper way. What you need is a firewall that will filter without routing and passes packets intact, complete with original MAC.
BTW, before switching to pfSense, I used Linux for my firewall.
-
Can they use the same MAC for both IPs? That is a very common setup. In that case you could 1:1 NAT it from a virtual IP on WAN to the VoIP server on an internal subnet.
Otherwise to use the IP directly and get the MAC from the server you would have to bridge it's interface to the WAN. To do that you would need to have a NIC available to use.
Steve
-
@stephenw10 said in Mapping ISP provided Static IP to MAC addresses -behind Pfsense:
Can they use the same MAC for both IPs?
If he used a static config, he could use aliases. However, I thought he had to provide the MAC to Telus, which means they'd be using a DHCP server with static mapping. Try assigning 2 IPs to a MAC in pfSense and see what happens. Hint - It's not allowed.
-
Thanks @stephenw10 and @JKnott
-
You are right... ISP does not allow to use the same MAC for both IPs. I'm trying to get this escalated in TELUS.
-
WAN router is bridged to PFSense box.
-
I was reading about creating virtual IPs in Pfsense for the non-DMZ server public IP and then create NAT 1:1... I'll be testing in a few hours. Hopefully, it works. Let me know any suggestions.
-
-
If you need two MACs you will have to bridge the WAN with another NIC so the server pulls the IP from Telus directly.
Is that an option for you? You have a NIC you can use to connect the server?You can still filter traffic across the bridge.
There is also at least one truly horrendous hack you might deploy if all else fails.

Steve
-
Guess there are more people asking the same question, and they are on TELUS...
https://www.reddit.com/r/networking/comments/4u3sn3/isp_delivers_static_ips_via_dhcp_reservation/ -
@stephenw10 I want to keep the server behind the Pfsense. So I'm not sure how to achieve what you are suggesting.
WAN (Public IP1) --Bridged--> PFSense (with VLANs) -> switches and server(on vlan).
Public IP2 for the server.How do I associate Public IP2 to the server, since the public IP2 requires DHCP reservation for the server.
-
@ros81 said in Mapping ISP provided Static IP to MAC addresses -behind Pfsense:
I was reading about creating virtual IPs in Pfsense for the non-DMZ server public IP and then create NAT 1:1... I'll be testing in a few hours. Hopefully, it works. Let me know any suggestions.
Please forget NAT. It's a borked solution, as johnpos would say. Here's some info on setting up pfSense as a transparent firewall. This is the sort of solution you need, not NAT.
-
Do you have an additional interface on pfSense you can use for this?
Or is the server on a separate VLAN? Could it be?
The best solution for you here is to put the server in a a sort of DMZ bridged to the WAN. So:
WAN (Public IP1)--> PFSense (with VLANs) -> switches - LAN clients | |_ Voip server (Public IP2)The VoIP server is set as DHCP and pulls it's IP from Telus directly.
Steve
-
@stephenw10 Thanks... The server is on a separate VLAN.
Are you suggesting to do this?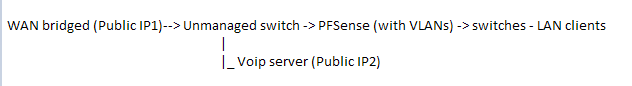
Or this diagram...

If diagram 2, can the ISP see the MAC address on the other NIC card in the PFsense box?
-
Either way, I don't feel comfortable to leave the Voice Server on DMZ. Thanks guys for your suggestions, but do you have any other suggestions?
-
@ros81 said in Mapping ISP provided Static IP to MAC addresses -behind Pfsense:
Thanks guys for your suggestions, but do you have any other suggestions?
Only the correct one, that is a transparent firewall, as I suggested. I provided a link to that pfSense article for doing that. With it, Telus will be able to assign IP addresses to the MAC addresses, as required.
-
It would be like the 2nd diagram. You would set the server VLAN interface as IPv4 type none then create a bridge with it and WAN in.
Now it's in the same layer 2 segment as the WAN so can pull an IP directly from Telus using it's own MAC.
I'm not sure why you would not want to do that. You can still filter all the incoming and outgoing traffic to it.
The other suggestions I have are last ditch style. Do you have a spare NIC you can use in that system?
Steve
-
@stephenw10 Thanks.. I like your idea about the diagram 2..(You said this can be achieved without an additional NIC card, but just with vlan.) Can you explain how to do it ?
I have another NIC too..