Network Setup Suggestions For XG-7100
-
This post is deleted! -
Your "server" in this context is some sort of VM host? With the three subnets shown used internally?
If so then sending all three subnets using one VLAN per port makes no sense there.
It makes no sense anyway to use three ports unless you have a requirement for >1Gbps between subnets. 3 ports used an 8 port switch at each end is also a waste of resources IMO.I would definitely use multiple VLANs on one port if that's how you are going to arrange the devices. I assume the 8 port switch is managed?
If you have the option I would put the 'server' on on the ix ports and send the VLANs to it there.
Steve
-
@stephenw10 said in Network Setup Suggestions For XG-7100:
Your "server" in this context is some sort of VM host? With the three subnets shown used internally?
If so then sending all three subnets using one VLAN per port makes no sense there.
It makes no sense anyway to use three ports unless you have a requirement for >1Gbps between subnets. 3 ports used an 8 port switch at each end is also a waste of resources IMO.I would definitely use multiple VLANs on one port if that's how you are going to arrange the devices. I assume the 8 port switch is managed?
If you have the option I would put the 'server' on on the ix ports and send the VLANs to it there.
Steve
Hi Steve. Yes the server is a ESXi VM host with many VM's. There are two of these "servers" for redundancy actually (I updated the diagram too). The pfSense box has the gateway (interfaces) setup on it and the physical servers connect to the LAN network, while the VM's have static IPs set for their respective subnets they belong too. The switch is currently a Netgear GS108 Unmanaged switch, looking for a 24 - 48 port managed switch upgrade in the future.
I like the idea of one port per server being used which will send all the traffic for all of the subnets and this is the approach I would like to take. However, I'm not sure how to setup the XG-7100 in this manner. It seems you would have to edit the Interface->Switch->Ports setting and have multiple Port VID's listed for a single interface, no?
ETH 1 is WAN
ETH 3 is Server 1The error is shown because I tried to enter "4091,4092" into the Port VID box for ETH 3.
-
Any suggestions here? Is there a way to setup ETH3 to allow multiple or all VLANs?
-
You only can put a VLAN in a NIC, not in a switched port.
7100 series have 10 ports, switched.
2 SPF+ ports
2 Giba ports
6 switched ports.
So you only have 4 macaddress.
When you us Giga ports, its only can be used as switched and just can create interfaces into pfSense.
I recomend to put VLANs to work (exept the VLANs for the Giga ports) with the SFP+ ports -
You can setup the switch to pass any number of VLANs tagged on port 3.
Since they are tagged the PVID doesn't matter there. Just set port 3 tagged as a member of all the VLAN groups you wanted trunked from it.
You would then need to Configure ESXi to accept that tagged traffic and send it to the correct VMs of course.
Steve
-
I am having trouble getting the pfsense firewall to hand out a IP address to the UniFi switch.
Setup
The XG-7100 pfSense firewall is connected to the switch on Ix1 SFP port to the UniFi switch's SFP port 49.
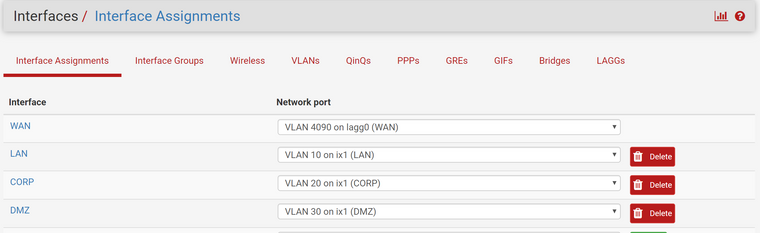
All Ports are set to "ALL" for the port profile. The management interface is using the UniFi network which is the default network (just changed the name to UniFi since I have a network named LAN).
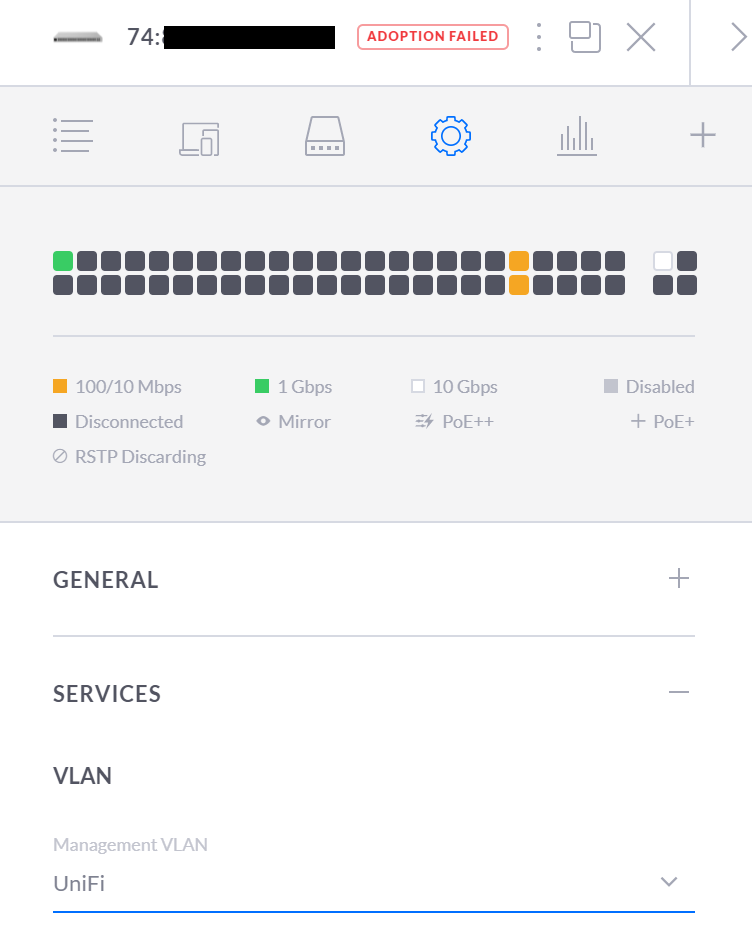
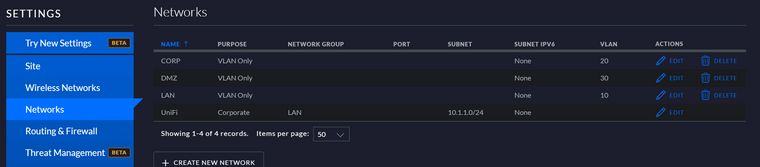
-
ix1 doesn't connect through the on-board switch. You don't need an y switch config present to have that connect.
You would need to be using one of those VLANs as the management subnet in UniFi to be able to 'see' it from anywhere else unless you have ix1 also assigned directly, whcih you don't appear to.
Steve
-
@stephenw10 said in Network Setup Suggestions For XG-7100:
ix1 doesn't connect through the on-board switch. You don't need an y switch config present to have that connect.
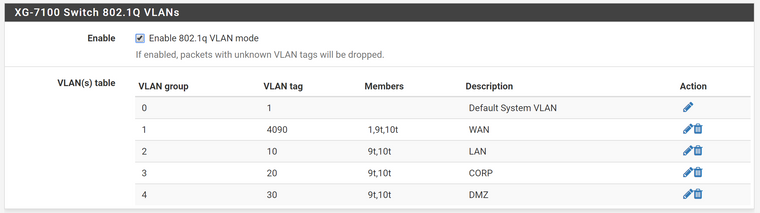
Are you saying that I can delete the VLAN groups 2,3, & 4 in the following screenshot?
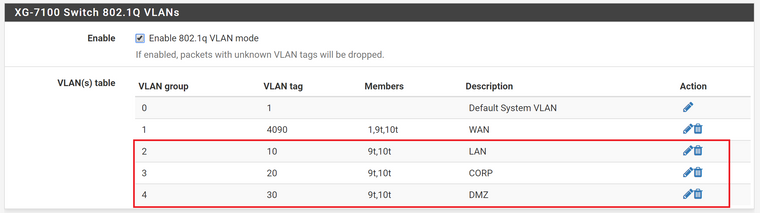
You would need to be using one of those VLANs as the management subnet in UniFi to be able to 'see' it from anywhere else unless you have ix1 also assigned directly, whcih you don't appear to.
So I did change the Management VLAN to the LAN Network I created which got the switch to get a IP address from the firewall that was reserved for it. So that part worked out.
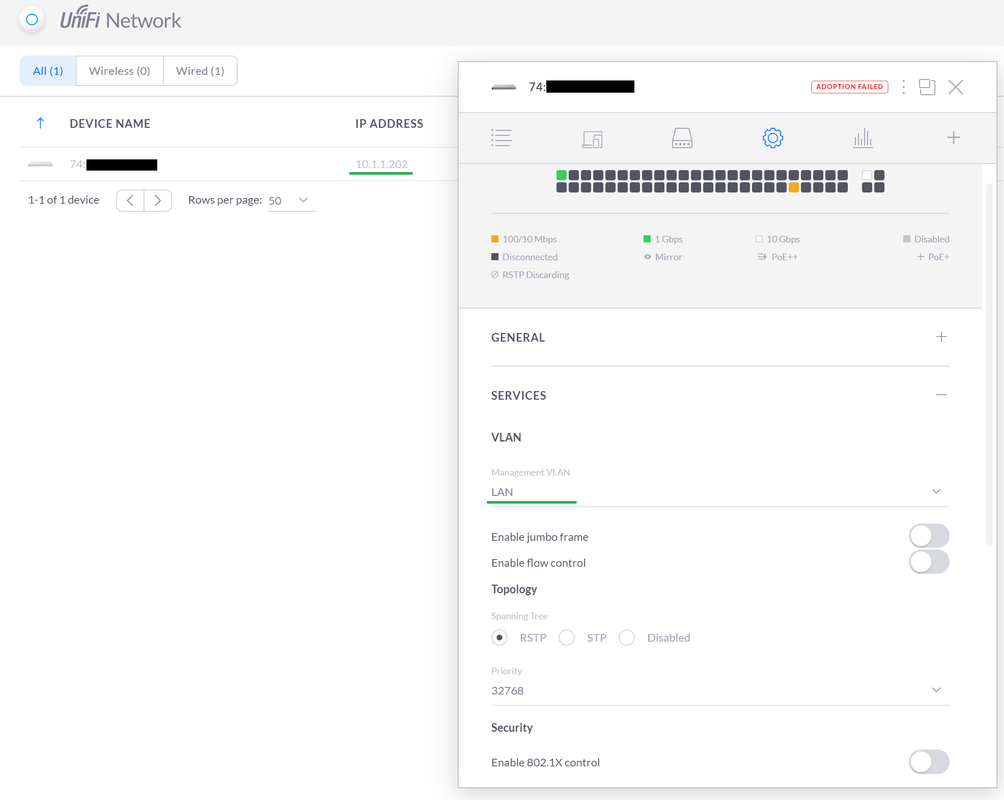
However after doing that I can not get the Controller to adopt the switch anymore. The PC that is running the controller software is on IP 10.1.1.250. It is plugged in directly to Port 1 on the switch just like it was before changing the management interface.
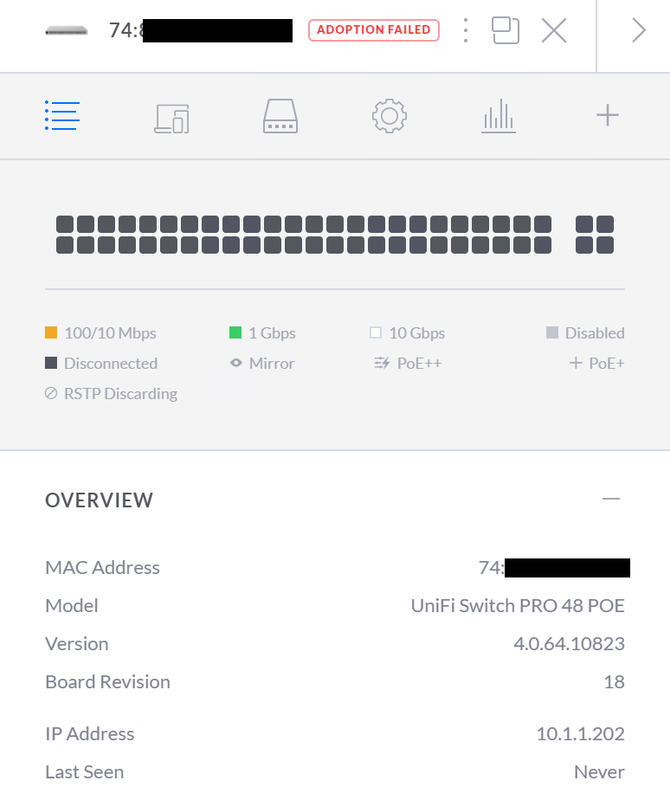
-
@ThePieMonster said in Network Setup Suggestions For XG-7100:
Are you saying that I can delete the VLAN groups 2,3, & 4 in the following screenshot?
Yes, you only need those defined there at all if you want to truck VLAN through the on-board switch. If you're using ix0/1 directly for VLANs the switch plays no part in that.
Steve