pfSense Freeradius as auth server for all pfSense firewalls
-
Can I use freeradius server of a pfsense firewall as an authentication server for users of another pfsense firewall?
-
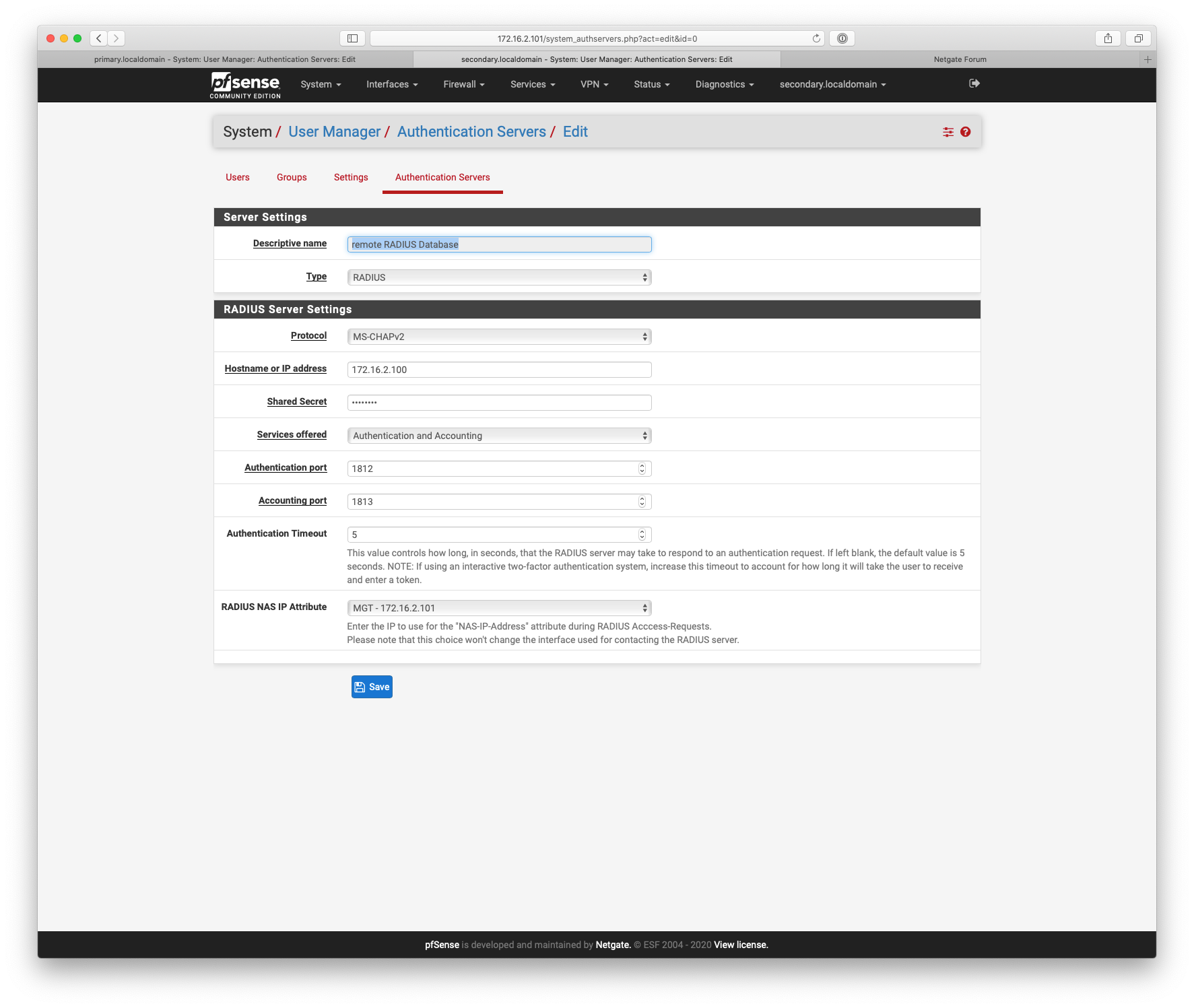
Yes the Freeradius server would be set as local (127.0.0.1) on the master and the masters IP address / FQDN would need setting in the others.
Looking at a previous diagram of yours:-
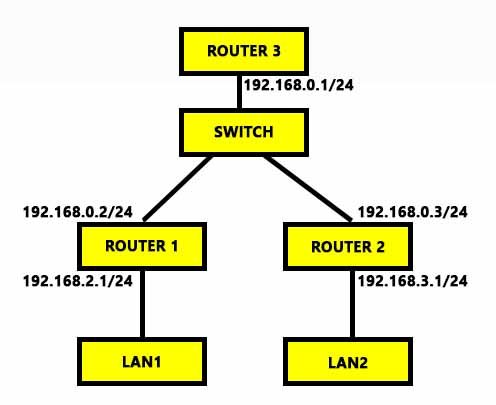
Say router3 is the master that would have 127.0.0.1 or 192.168.0.1 set as the Hostname or IP address and routers1 & 2 would have 192.168.0.1 set.
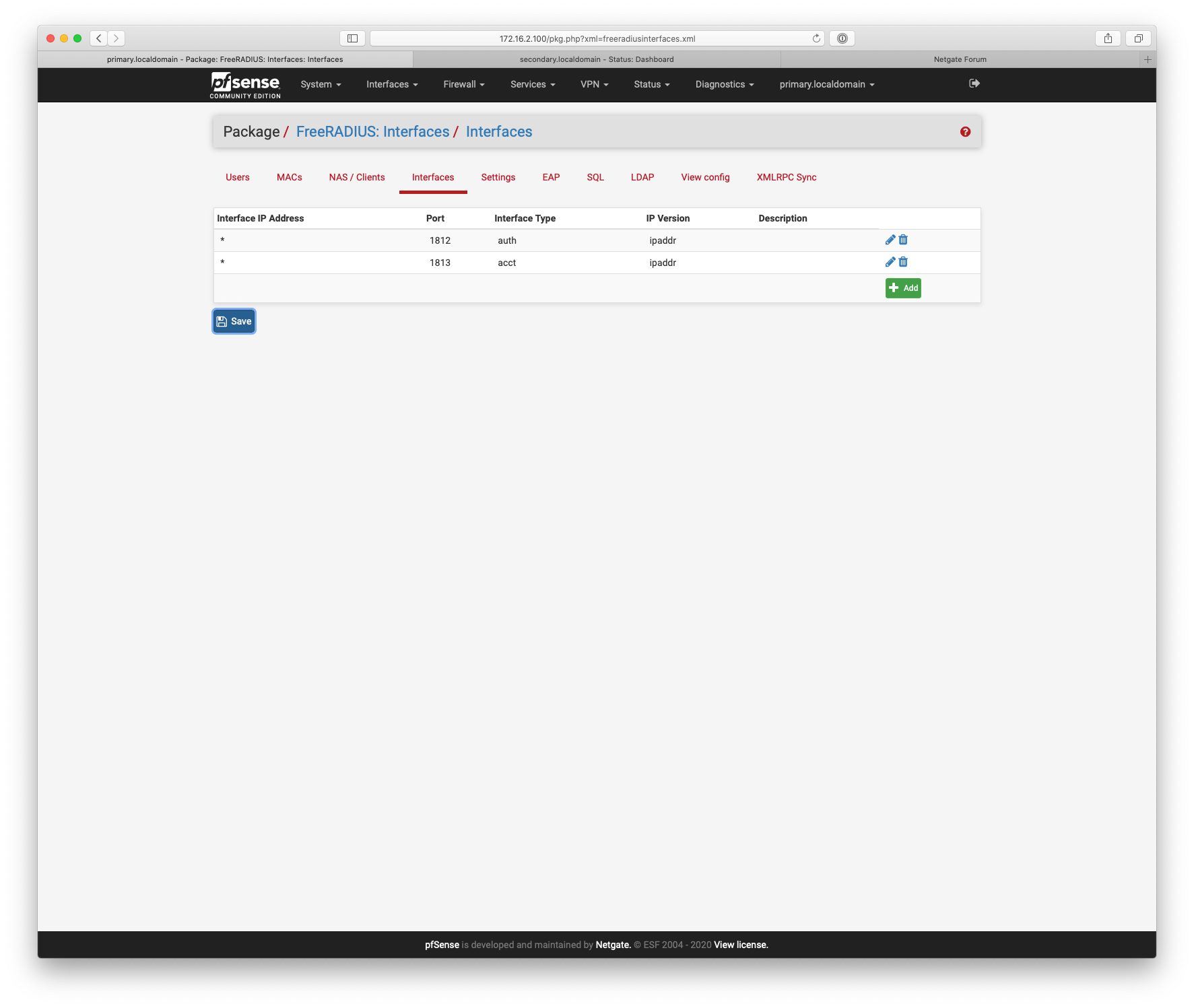
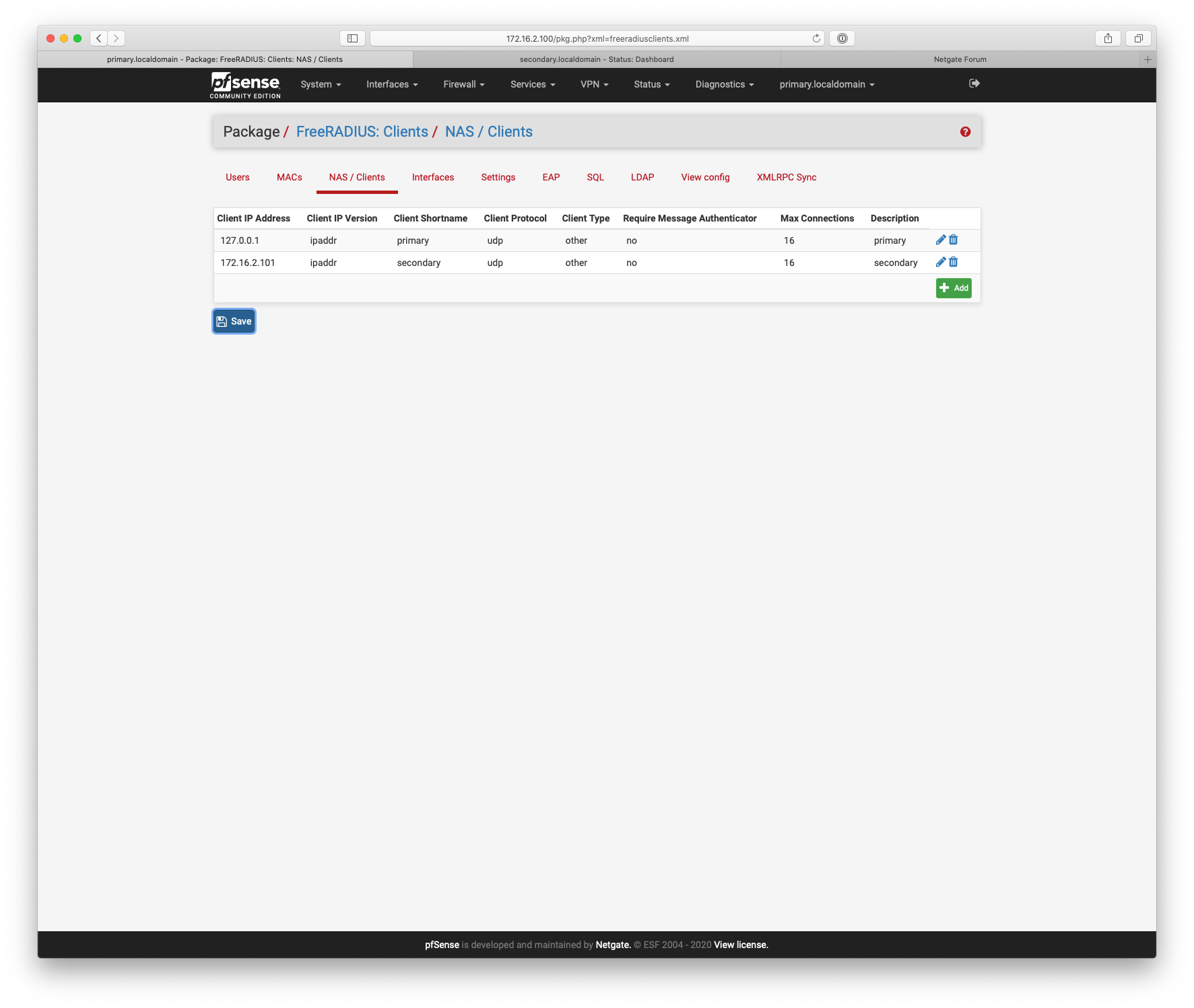
Also router1 would need router2 & 3 set up as nas clients in Freeradius.
-
@NogBadTheBad I have tried this but I get Authentication Failed. My current setup is I have two gateways in one subnet. I setup 192.168.8.2 as my freeradius, added 127.0.0.1 and 192.168.8.1 as clients. Then in my 192.168.8.1 pfsense, I added 192.168.8.2 as an authentication server. Should I also install freeradius in my 192.168.8.1 pfsense or does setting authentication server in user manager enought?
-
@azmodeuz said in pfSense Freeradius as auth server for all pfSense firewalls:
@NogBadTheBad I have tried this but I get Authentication Failed. My current setup is I have two gateways in one subnet. I setup 192.168.8.2 as my freeradius, added 127.0.0.1 and 192.168.8.1 as clients. Then in my 192.168.8.1 pfsense, I added 192.168.8.2 as an authentication server. Should I also install freeradius in my 192.168.8.1 pfsense or does setting authentication server in user manager enought?
Two gateways on one subnet doesn't matter, they are just Freeradius nas endpoints.
Do a radsniff -x from the pfsense main server CLI and post your results when trying to connect from one of other routers.
https://support.microfocus.com/kb/doc.php?id=7014552
You have allowed the Freeradius ports through the firewall rules haven't you ?
-
Still no luck. Do I need to do some firewall rules? The firewalls are in the same subnet.
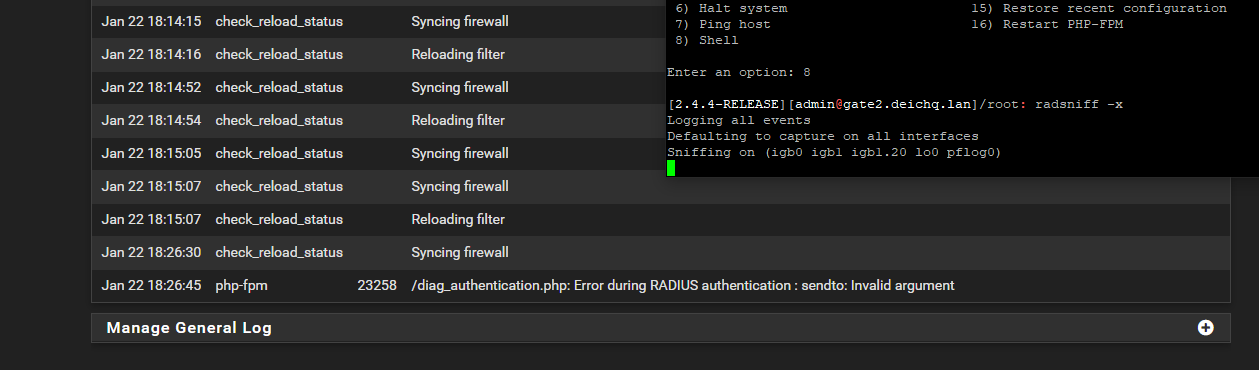
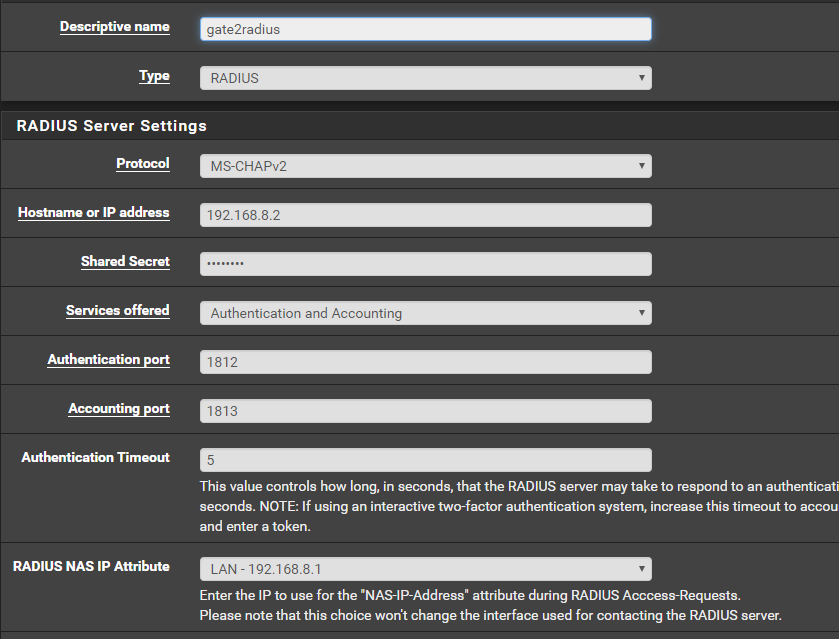
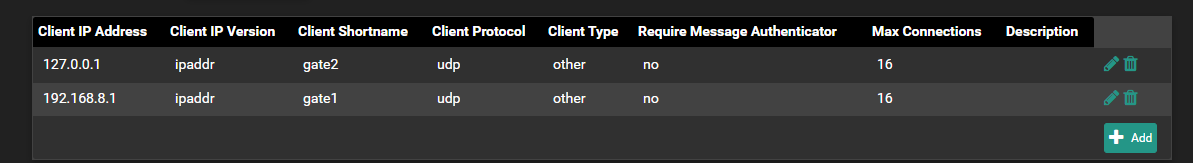
-
Client device being blocked by firewall rules or client System -> User Manager -> Authentication Servers not defined correctly ?
You should see something with radsniff.
Draw a diagram.
-
@NogBadTheBad . . . . . . . . . . . . . . . . . . . . . . . . . .freeRadius
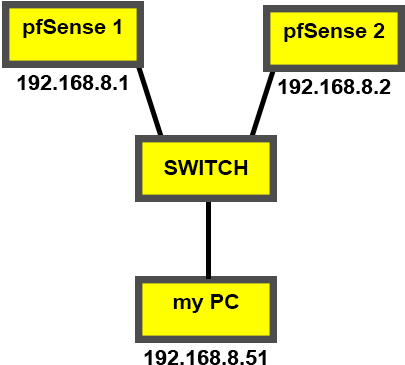
-
Do a radsniff on the server and a radtest on the client.
-
Its a setup issue your end.
Just set up 2 test vm pfsense instances:-
[2.4.4-RELEASE][admin@primary.localdomain]/root: radsniff -x
Logging all events
Defaulting to capture on all interfaces
Sniffing on (em0 em1 em2 lo0 pflog0)
2020-01-22 14:09:31.508870 (1) Access-Request Id 67 em2:172.16.2.101:59365 -> 172.16.2.100:1812 +0.000
User-Name = "pfsense-admin"
NAS-IP-Address = 172.16.2.101
Service-Type = Login-User
Called-Station-Id = "00:50:56:32:83:51:secondary.localdomain"
NAS-Identifier = "secondary.localdomain"
MS-CHAP-Challenge = 0xe856d8caf78d4633c7f65d7e613ae111
MS-CHAP2-Response = 0x010198ec245274b7f003ca538775786f0c880000000000000000b17d614e8c71e69e61775f835cd7fcc48f1be796c7b2f890
Authenticator-Field = 0x84ac06c27a828b8d5ebb5340b6ca7e55
2020-01-22 14:09:31.796700 (2) Access-Accept Id 67 em2:172.16.2.101:59365 <- 172.16.2.100:1812 +0.028 +0.028
Class = 0x61646d696e73
MS-MPPE-Encryption-Policy = Encryption-Allowed
MS-MPPE-Encryption-Types = RC4-40or128-bit-Allowed
MS-CHAP2-Success = 0x01533d42383831353644373030324532344345334136343246454231453433384138383733323443343834
Attr-26.311.17 = 0x950d89f8ee1df2bfeb52ca26c2d668c88be3e6371242e112a8613fab9647c6a0f353
Attr-26.311.16 = 0x9fb9c6fefbab7c6698140a6845f3c65299bb75c6ae639613216ad7e26195b6f98d45
Authenticator-Field = 0x4b63b17534283a9a46b164e752bc3634
2020-01-22 14:09:36.279670 (1) Cleaning up request packet ID 67 -
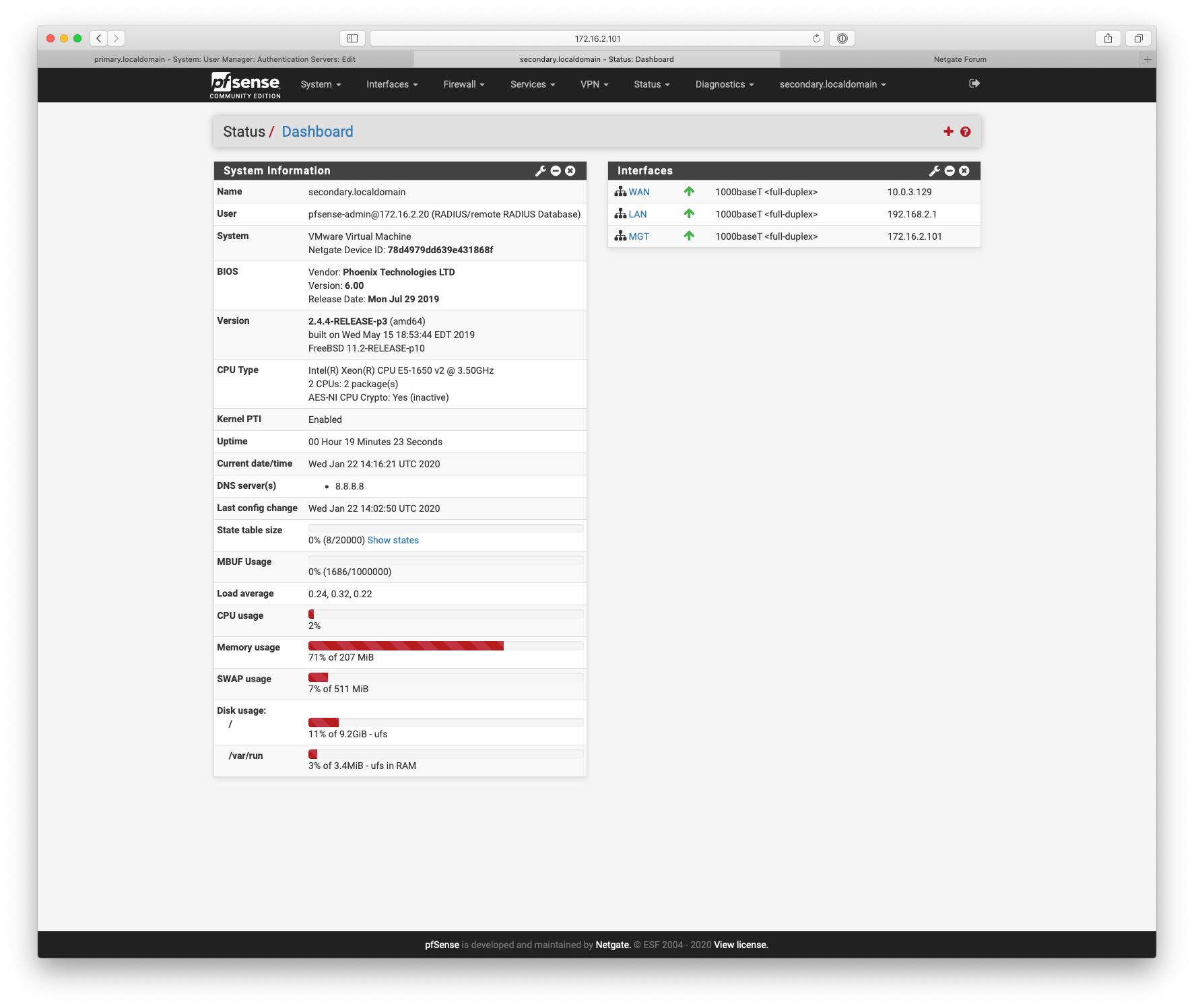
primary
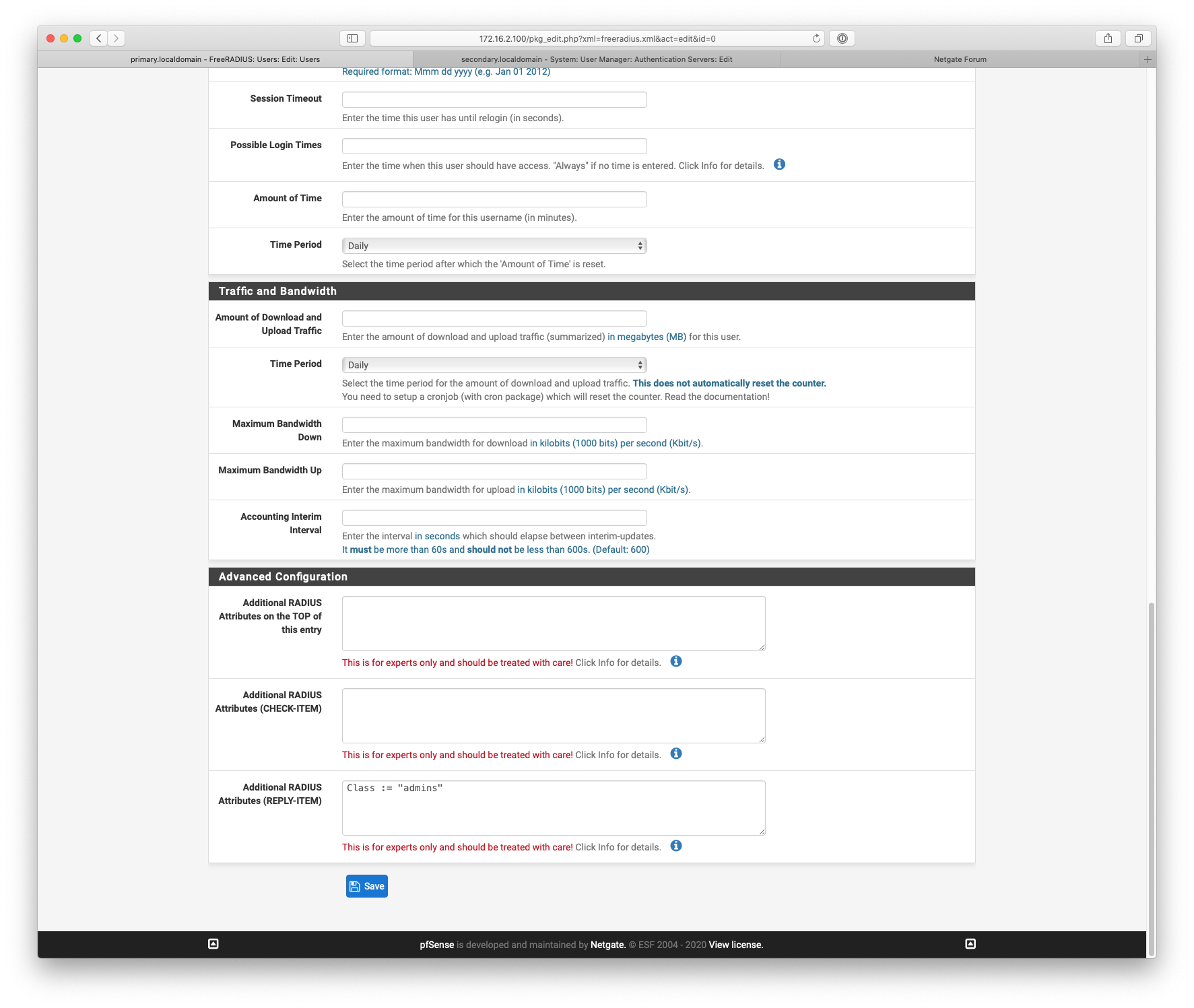
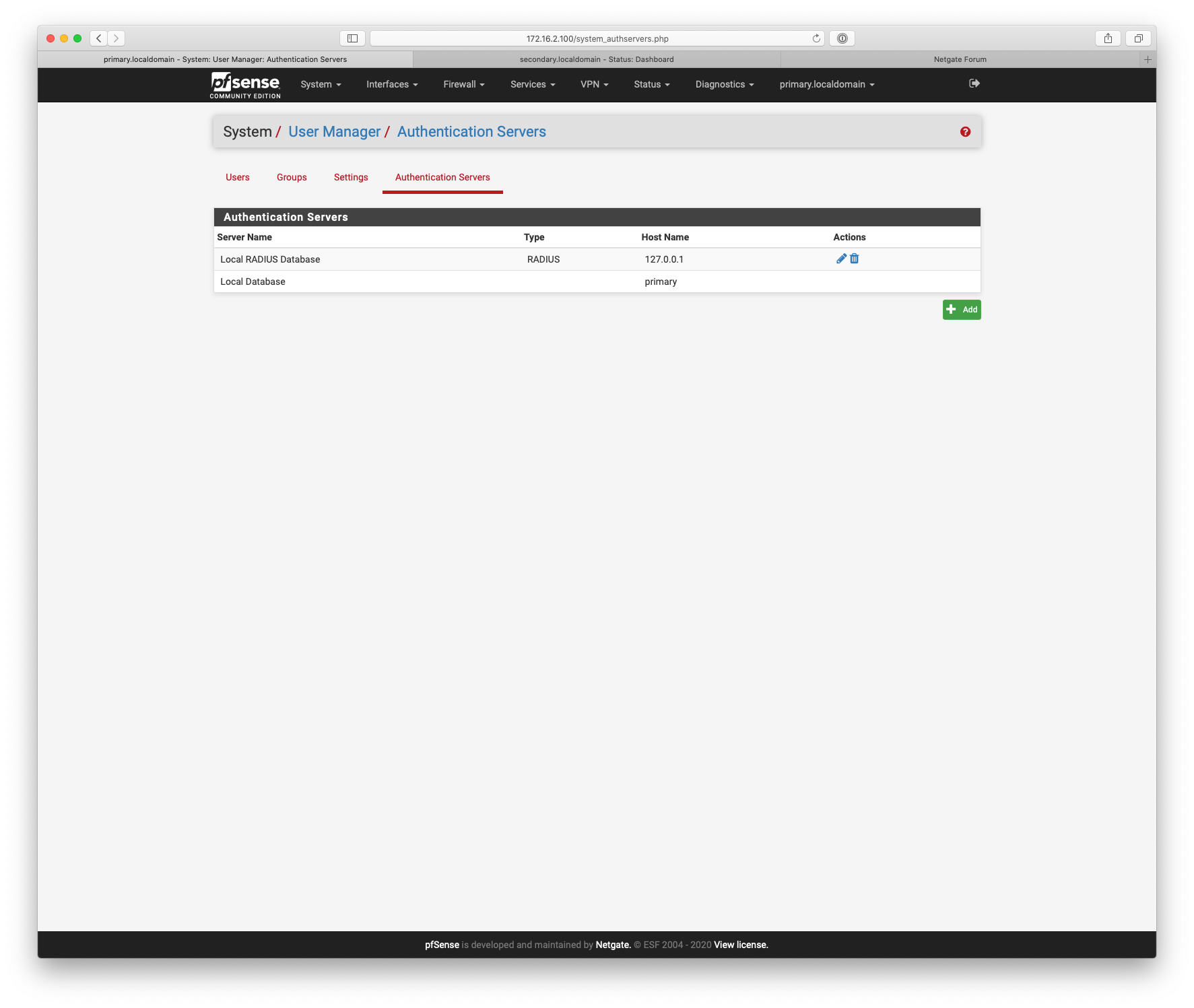
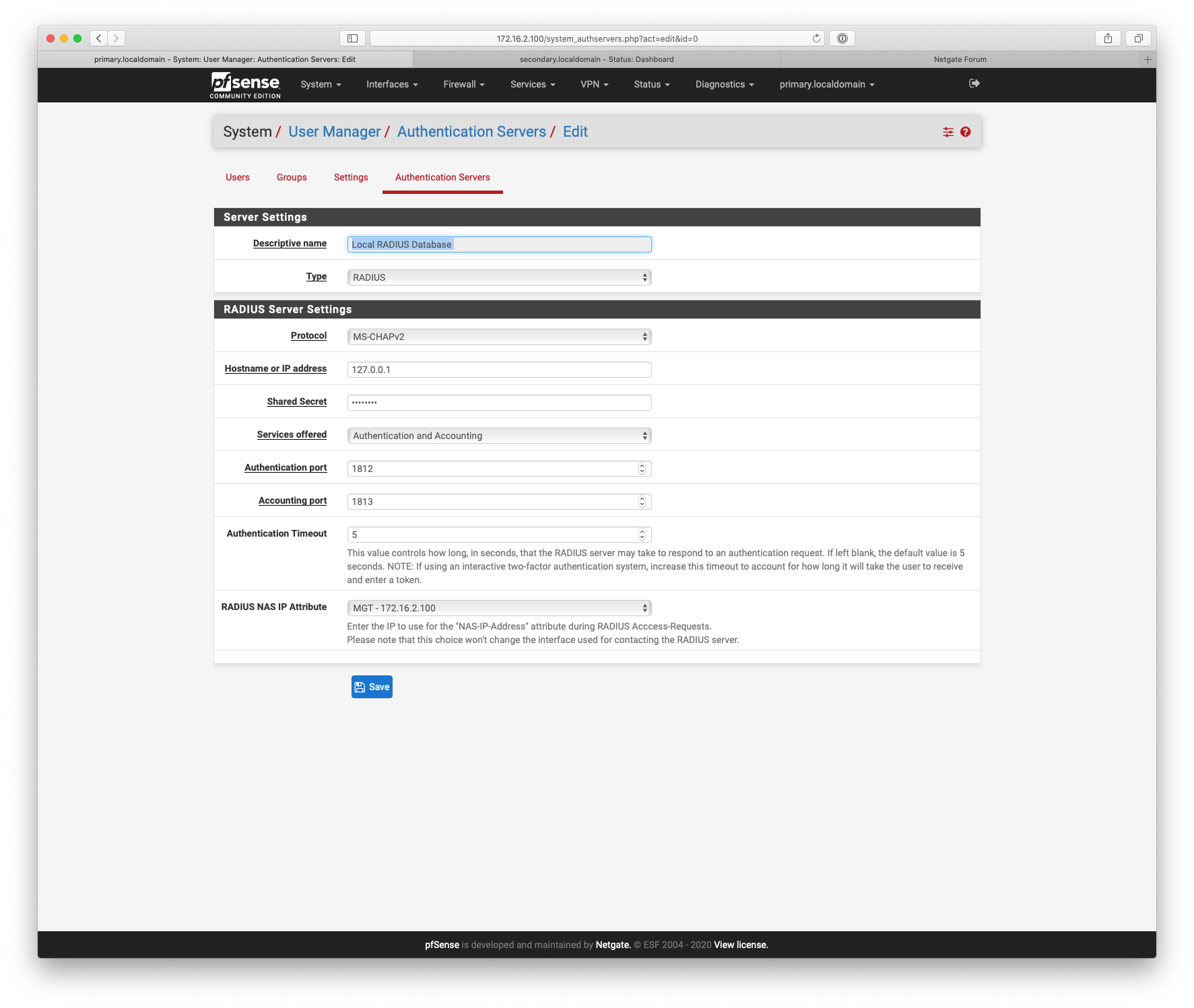
-
secondary