IPsec VPN StS - no traffic
-
Hello everyone,
I got a problem on a IPsec tunnel between 2 branchs. What happen is: tunnel is up, I can ping devices on both sides but can't connect to them. For example I can't make RDP connections between the sides. I tried everything, changed encryption algorithm, auth methods, etc.
What makes it stranger is that I got others tunnels working on both sides with no problem.
IPsec rule is set * to * in both Firewalls, outbound NAT is automatic created (even tried with hybrid and still no luck).P1 config:
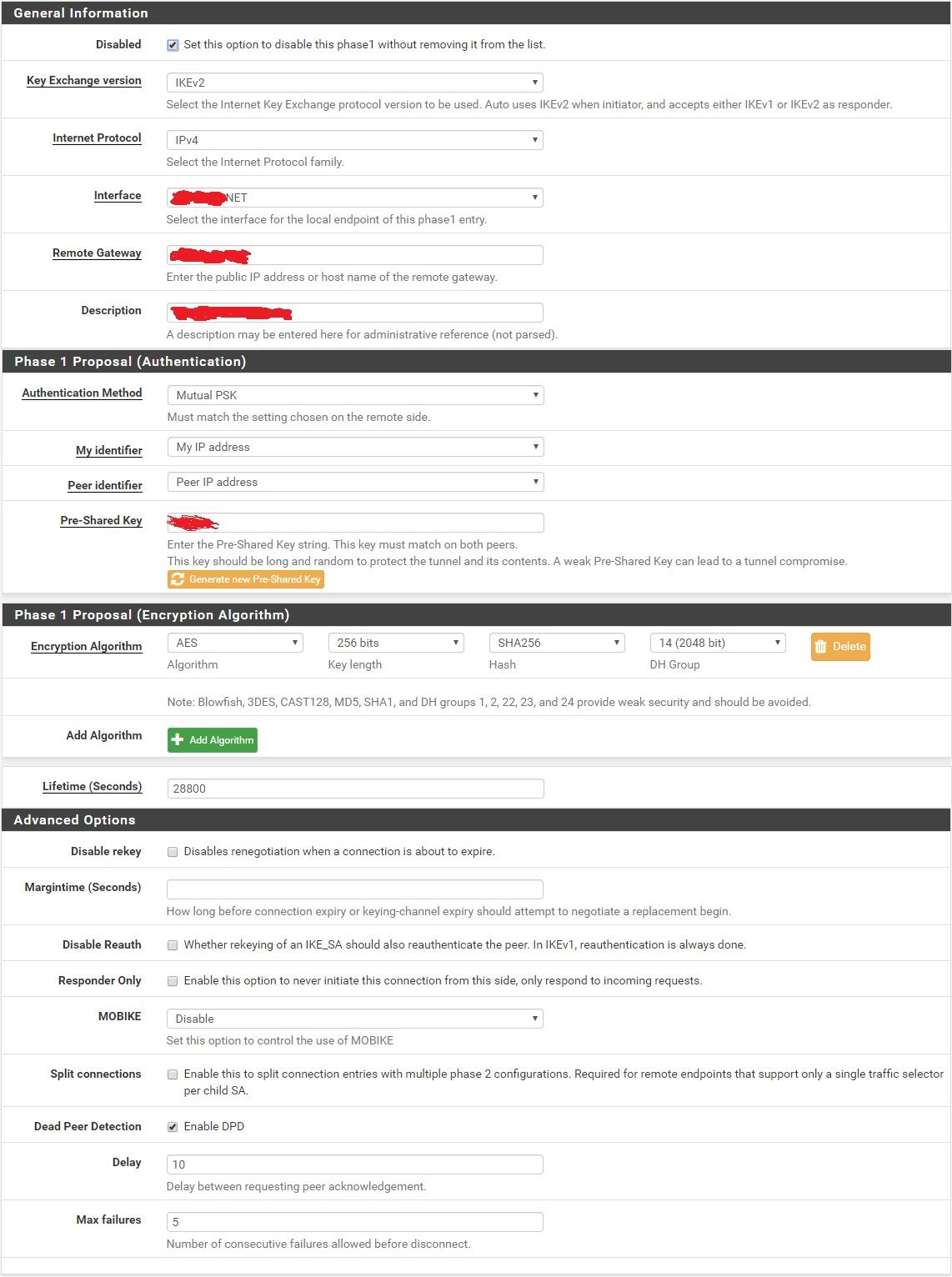
P2 config:
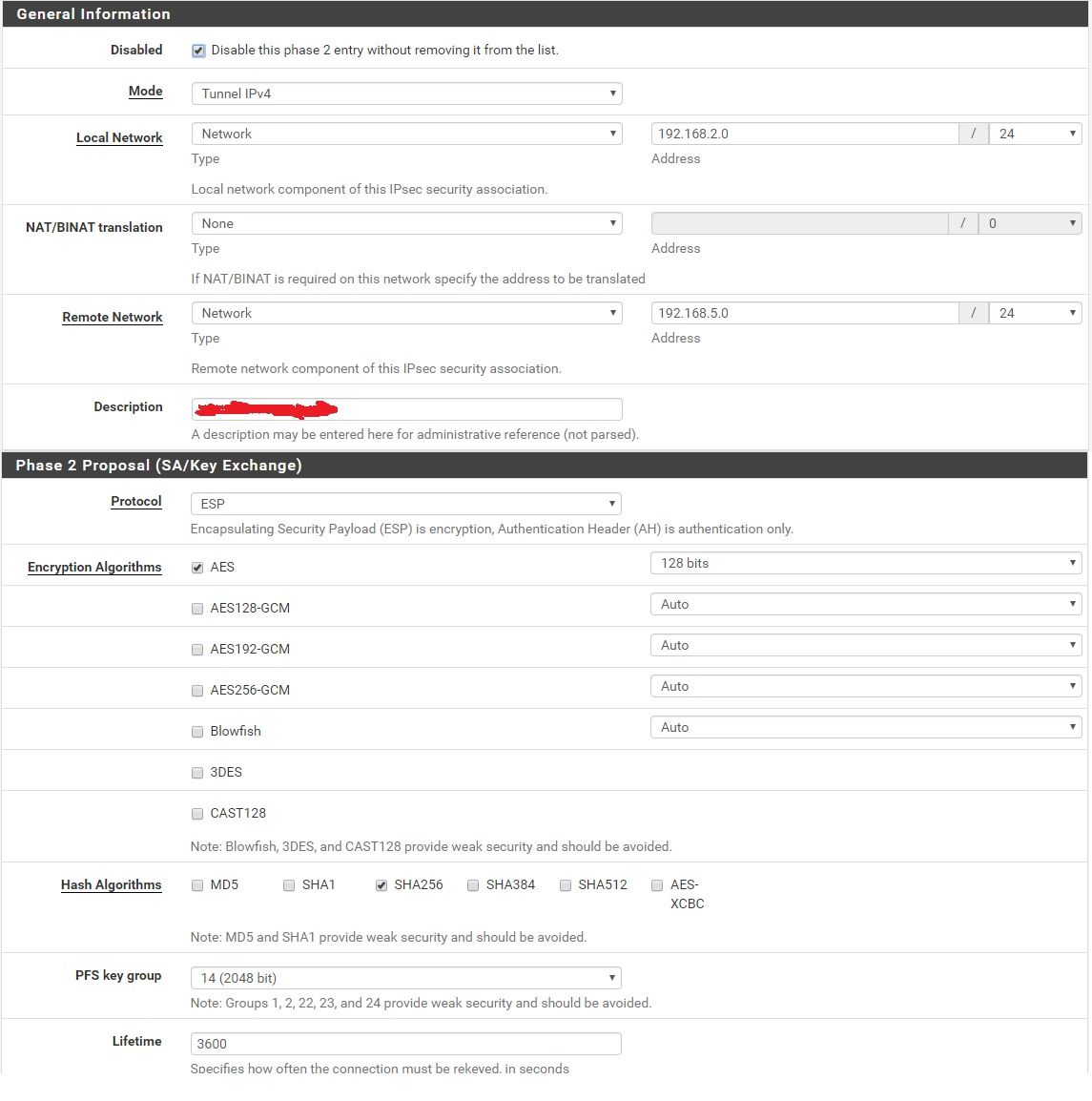
Same config on the other endpoint (obviously source/destination are inverse).
I even capture packets while testing and tried to analyse it on Wireshark, but I dont know exactly how to.
No. Time Source Destination Protocol Length Info 1 0.000000 192.168.5.5 192.168.2.5 ICMP 72 Echo (ping) request id=0x0002, seq=31022/11897, ttl=127 (reply in 2) 2 0.000378 192.168.2.5 192.168.5.5 ICMP 72 Echo (ping) reply id=0x0002, seq=31022/11897, ttl=127 (request in 1) 3 1.014671 192.168.5.5 192.168.2.5 ICMP 72 Echo (ping) request id=0x0002, seq=31023/12153, ttl=127 (reply in 4) 4 1.014990 192.168.2.5 192.168.5.5 ICMP 72 Echo (ping) reply id=0x0002, seq=31023/12153, ttl=127 (request in 3) 5 2.028549 192.168.5.5 192.168.2.5 ICMP 72 Echo (ping) request id=0x0002, seq=31024/12409, ttl=127 (reply in 6) 6 2.028857 192.168.2.5 192.168.5.5 ICMP 72 Echo (ping) reply id=0x0002, seq=31024/12409, ttl=127 (request in 5) 7 3.042263 192.168.5.5 192.168.2.5 ICMP 72 Echo (ping) request id=0x0002, seq=31025/12665, ttl=127 (reply in 8) 8 3.042583 192.168.2.5 192.168.5.5 ICMP 72 Echo (ping) reply id=0x0002, seq=31025/12665, ttl=127 (request in 7) 9 14.066480 192.168.5.5 192.168.2.5 TCP 64 60132 → 3389 [SYN, ECN, CWR] Seq=0 Win=8192 Len=0 MSS=1460 WS=256 SACK_PERM=1 10 14.066812 192.168.2.5 192.168.5.5 TCP 64 3389 → 60132 [SYN, ACK, ECN] Seq=0 Ack=1 Win=64000 Len=0 MSS=1460 WS=1 SACK_PERM=1 11 14.069804 192.168.5.5 192.168.2.5 TCP 52 60132 → 3389 [ACK] Seq=1 Ack=1 Win=1051136 Len=0 12 14.070182 192.168.5.5 192.168.2.5 TLSv1.2 99 Ignored Unknown Record 13 14.075407 192.168.2.5 192.168.5.5 TLSv1.2 71 Ignored Unknown Record 14 14.086762 192.168.5.5 192.168.2.5 TCP 52 60132 → 3389 [ACK] Seq=48 Ack=20 Win=1051136 Len=0 15 16.824950 192.168.5.5 192.168.2.5 TLSv1.2 236 Client Hello 16 16.829089 192.168.2.5 192.168.5.5 TCP 52 3389 → 60132 [ACK] Seq=20 Ack=232 Win=63769 Len=0 17 16.831388 192.168.2.5 192.168.5.5 TLSv1.2 1249 Server Hello, Certificate, Server Key Exchange, Server Hello Done 18 16.847789 192.168.5.5 192.168.2.5 TCP 52 60132 → 3389 [ACK] Seq=232 Ack=1217 Win=1049856 Len=0 19 16.848289 192.168.5.5 192.168.2.5 TLSv1.2 234 Client Key Exchange, Change Cipher Spec, Encrypted Handshake Message 20 16.852019 192.168.2.5 192.168.5.5 TLSv1.2 159 Change Cipher Spec, Encrypted Handshake Message 21 16.855845 192.168.5.5 192.168.2.5 TLSv1.2 185 Application Data 22 16.856661 192.168.2.5 192.168.5.5 TLSv1.2 393 Application Data 23 16.861601 192.168.5.5 192.168.2.5 TLSv1.2 777 Application Data 24 16.864061 192.168.2.5 192.168.5.5 TLSv1.2 185 Application Data 25 16.867408 192.168.5.5 192.168.2.5 TCP 52 60132 → 3389 [FIN, ACK] Seq=1272 Ack=1798 Win=1050880 Len=0 26 16.867652 192.168.2.5 192.168.5.5 TCP 52 3389 → 60132 [ACK] Seq=1798 Ack=1273 Win=64240 Len=0 27 16.867725 192.168.2.5 192.168.5.5 TCP 52 3389 → 60132 [RST, ACK] Seq=1798 Ack=1273 Win=0 Len=0 28 16.880864 192.168.5.5 192.168.2.5 TCP 64 60135 → 3389 [SYN, ECN, CWR] Seq=0 Win=8192 Len=0 MSS=1460 WS=256 SACK_PERM=1 29 16.881185 192.168.2.5 192.168.5.5 TCP 64 3389 → 60135 [SYN, ACK, ECN] Seq=0 Ack=1 Win=64000 Len=0 MSS=1460 WS=1 SACK_PERM=1 30 16.883322 192.168.5.5 192.168.2.5 TCP 52 60135 → 3389 [ACK] Seq=1 Ack=1 Win=1051136 Len=0 31 16.883713 192.168.5.5 192.168.2.5 TLSv1.2 99 Ignored Unknown Record 32 16.887822 192.168.2.5 192.168.5.5 TLSv1.2 71 Ignored Unknown Record 33 16.891909 192.168.5.5 192.168.2.5 TLSv1.2 236 Client Hello 34 16.898138 192.168.2.5 192.168.5.5 TLSv1.2 1249 Server Hello, Certificate, Server Key Exchange, Server Hello Done 35 16.916226 192.168.5.5 192.168.2.5 TLSv1.2 234 Client Key Exchange, Change Cipher Spec, Encrypted Handshake Message 36 16.919961 192.168.2.5 192.168.5.5 TLSv1.2 159 Change Cipher Spec, Encrypted Handshake Message 37 16.923422 192.168.5.5 192.168.2.5 TLSv1.2 185 Application Data 38 16.924200 192.168.2.5 192.168.5.5 TLSv1.2 393 Application Data 39 16.929901 192.168.5.5 192.168.2.5 TLSv1.2 777 Application Data 40 16.932183 192.168.2.5 192.168.5.5 TLSv1.2 185 Application Data 41 16.935580 192.168.5.5 192.168.2.5 TLSv1.2 249 Application Data 42 16.936476 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 43 16.939726 192.168.5.5 192.168.2.5 TLSv1.2 585 Application Data 44 16.941487 192.168.2.5 192.168.5.5 TLSv1.2 249 Application Data 45 16.943882 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 46 16.944126 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 47 16.944382 192.168.2.5 192.168.5.5 TCP 52 3389 → 60135 [ACK] Seq=2080 Ack=2172 Win=63340 Len=0 48 16.944554 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 49 16.947219 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 50 16.947641 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 51 16.950432 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 52 16.950855 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 53 16.954016 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 54 16.954427 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 55 16.957187 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 56 16.957614 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 57 16.960235 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 58 16.960641 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 59 16.963642 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 60 16.964067 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 61 16.967184 192.168.5.5 192.168.2.5 TLSv1.2 137 Application Data 62 16.967611 192.168.2.5 192.168.5.5 TLSv1.2 137 Application Data 63 16.972713 192.168.5.5 192.168.2.5 TCP 52 60135 → 3389 [ACK] Seq=2767 Ack=2760 Win=1049856 Len=0 64 16.974487 192.168.5.5 192.168.2.5 TLSv1.2 777 Application Data 65 16.977958 192.168.2.5 192.168.5.5 TLSv1.2 153 Application Data 66 16.978010 192.168.2.5 192.168.5.5 TLSv1.2 153 Application Data 67 16.978343 192.168.2.5 192.168.5.5 TCP 1512 3389 → 60135 [ACK] Seq=2962 Ack=3492 Win=63515 Len=1460 [TCP segment of a reassembled PDU] 68 16.978467 192.168.2.5 192.168.5.5 TCP 1512 3389 → 60135 [ACK] Seq=4422 Ack=3492 Win=63515 Len=1460 [TCP segment of a reassembled PDU] 69 16.978580 192.168.2.5 192.168.5.5 TLSv1.2 1233 Application Data 70 16.980656 192.168.5.5 192.168.2.5 TCP 52 60135 → 3389 [ACK] Seq=3492 Ack=2962 Win=1049856 Len=0 71 16.980820 192.168.5.5 192.168.2.5 TLSv1.2 153 Application Data 72 16.980958 192.168.5.5 192.168.2.5 TCP 64 [TCP Dup ACK 70#1] 60135 → 3389 [ACK] Seq=3593 Ack=2962 Win=1049856 Len=0 SLE=5882 SRE=7063 73 17.000701 192.168.2.5 192.168.5.5 TCP 52 3389 → 60135 [ACK] Seq=7063 Ack=3593 Win=63414 Len=0 74 17.032165 192.168.2.5 192.168.5.5 TCP 1512 [TCP Retransmission] 3389 → 60135 [ACK] Seq=2962 Ack=3593 Win=63414 Len=1460 75 17.078965 192.168.2.5 192.168.5.5 TCP 1512 [TCP Retransmission] 3389 → 60135 [ACK] Seq=2962 Ack=3593 Win=63414 Len=1460 76 17.172551 192.168.2.5 192.168.5.5 TCP 1512 [TCP Retransmission] 3389 → 60135 [ACK] Seq=2962 Ack=3593 Win=63414 Len=1460 77 17.344165 192.168.2.5 192.168.5.5 TCP 1512 [TCP Retransmission] 3389 → 60135 [ACK] Seq=2962 Ack=3593 Win=63414 Len=1460 78 17.671773 192.168.2.5 192.168.5.5 TCP 1512 [TCP Retransmission] 3389 → 60135 [ACK] Seq=2962 Ack=3593 Win=63414 Len=1460 79 18.326986 192.168.2.5 192.168.5.5 TCP 1512 [TCP Retransmission] 3389 → 60135 [ACK] Seq=2962 Ack=3593 Win=63414 Len=1460 80 19.621829 192.168.2.5 192.168.5.5 TCP 1512 [TCP Retransmission] 3389 → 60135 [ACK] Seq=2962 Ack=3593 Win=63414 Len=1460 81 22.180181 192.168.2.5 192.168.5.5 TCP 1512 [TCP Retransmission] 3389 → 60135 [ACK] Seq=2962 Ack=3593 Win=63414 Len=1460 82 27.319493 192.168.2.5 192.168.5.5 TCP 52 3389 → 60135 [RST, ACK, CWR] Seq=4422 Ack=3593 Win=0 Len=0 83 27.321508 192.168.5.5 192.168.2.5 TCP 64 [TCP Dup ACK 70#2] 60135 → 3389 [ACK] Seq=3593 Ack=2962 Win=1049856 Len=0 SLE=5882 SRE=7063 84 27.321668 192.168.2.5 192.168.5.5 TCP 52 3389 → 60135 [RST] Seq=2962 Win=0 Len=0Can someone help me out?
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.