Remote Access VPN Setup
-
Hi All, I'm tryin to get something other than OpenVPN & PPTP VPN's working on our Pfsense box.
I've followed the instructions on setting up a remote access VPN - found here .... https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html
However I get literally no connection with the client stating... "the network connection between your computer and the VPN server could not be established because the remote server is not responding...." blah blah blah....
Not really sure where to start with this....
I've also tried to setup Windows remote access and hooked that into the NPS server.
This works internally but I'm not able to get a remote connection through the PFSense…. any ideas what rules I need to put in place on which interfaces?kind regards,
Paul.
-
Are you allowing port 500 & 4500 on your wan interface?
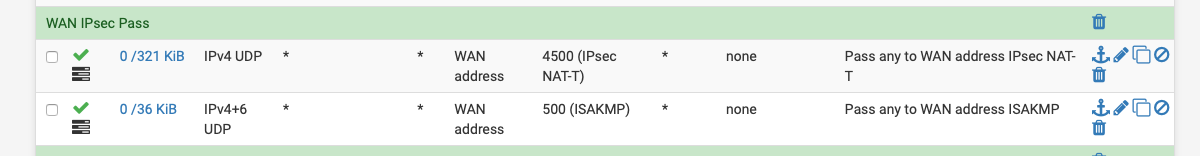
Also anything in the logs?
Status -> System Logs -> IPsec
-
Hi, NBTB - that's a bit better... I'm now getting a Policy Match error... Log is showing "received proposals inacceptable" and "remote host is behind NAT"... which could be because I'm trying to push the authentication to the NPS server....
-
The location of the auth server should not matter but mobile ipsec alost always uses NAT-T anyway. You are not passing ESP so it must use NAT-T here.
If the policy doesn't match it will not connect. Do you see what the client is proposing in the pfSense logs?
You setup the server exactly as shown in that doc?Steve
-
Hi, NBTB - that's a bit better... I'm now getting a Policy Match error... Log is showing "received proposals inacceptable" and "remote host is behind NAT"... which could be because I'm trying to push the authentication to the NPS server....
Update: Right well progress of sorts... I've resolved to use PfSense to make the VPN connection and then authenticate via Radius with our Windows box. Having added the relevant registry key to allow SHA256 to work (on a windows machine) and imported the cert I created on the Pfsense, I'm now getting an IKE authentication credentials are unacceptable error.
Any ideas how I resolve that?
-
I use the following Freeradius on pfSense.
-
Right so I finally have a connection... I had to export the root CA cert and import that so that the generated cert was trusted... (I'm not sure it mentioned that in the documents!).
Next up is to A. make RADIUS work and b. be able to do something once I'm connected (which I'm not able to at the moment)…
-
It's the first part of the Windows client section

https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html#import-the-ca-to-the-client-pcBut Windows often updates stuff etc. Please let us know if that needs updating to match whatever the current Windows requirements are.
Steve
-
@stephenw10 Aha, yes... I must have misread that... so I didn't need to download the certificate I created only the CA one?
-
You don't need the server cert on the client, no. It needs the CA so it can verify the identity of the server when it connects.
Steve
-
So next up then … I have a connection and an IP address of 192.168.205.1 subnet mask of 255.255.255.255 and no gateway address. As a result I'm connected but I can't get to any resources (typically found on my network at 192.168.10.0 and 192.168.200.0)….
I added the 192.168.205.0 network to my static routes pointing it at the LAN interface on 192.168.254.254 which seems to be where the other internal LAN's point.... but obviously without the client getting a gateway address that could prove tricky... Should I add a gateway of 192.168.205.254 ? -
Hmm, no it should not be necessary to add anything. Windows is assigning the vpn adapter as /32?
Do all clients behave like that?
We're probably going to need to see some screenshots of your setup to verify it.
Steve
-
-
Nope, that seems good. It's been a while since I configured that. Windows might have changed something I guess....
-
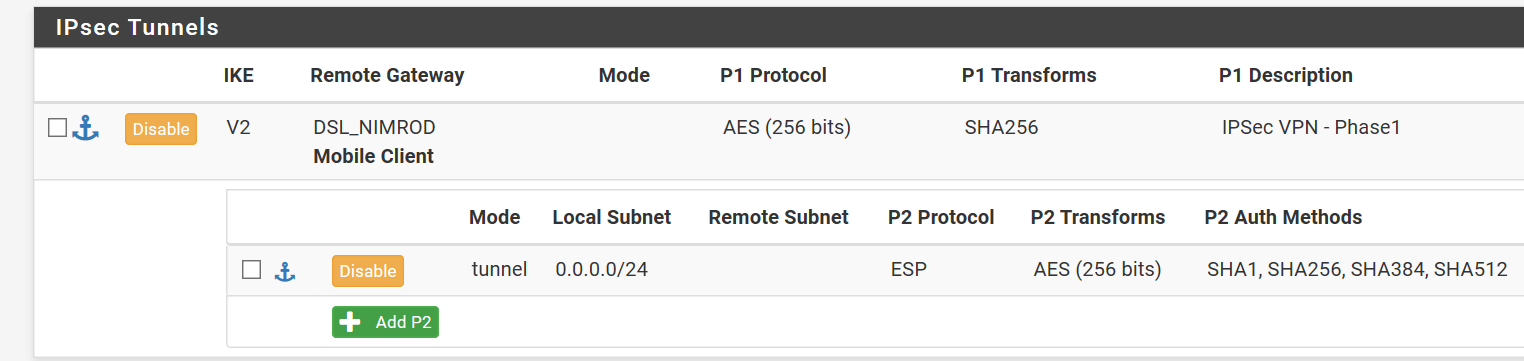
Right think I've got this bit solved now.... The problem was in Phase 2 where I had the local network settings set to 0.0.0.0 /24 as opposed to 0.0.0.0 /0 - I changed it to 192.168.10.0 /24 (our server network) and I can connect and ping … you guessed it, the servers... I've changed it now to 0.0.0.0 /0 and it still seems to hang together.... Next up getting it to use RADIUS authentication on our NPS ! :-) - Thanks to everyone for their assistance.
-
RTFM

https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html
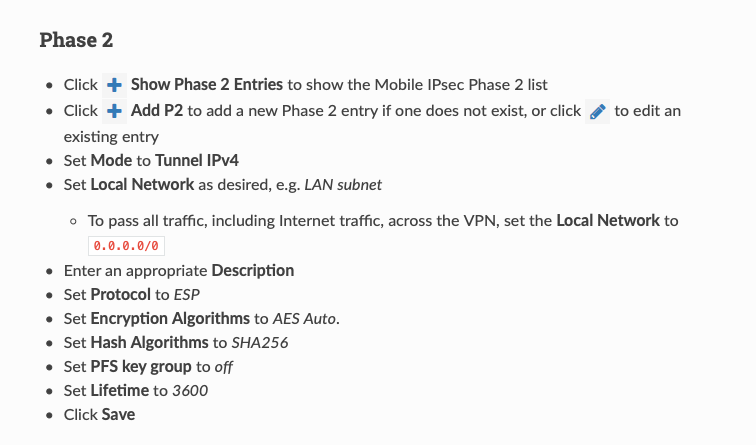
When you have 0.0.0.0/0 everything will go over the VPN tunnel from the local client, if you have 192.168.10.0 /24 only 192.168.10.0 /24 will pass over the VPN tunnel.
-
@NogBadTheBad Yes sounds about right... the penny finally dropped ! ;-)
-
Nice. Not sure how I missed that /24. Must have been low on coffee!