Masquerade two different local nets into IPSEC tunnel [solved]
-
Hi,
I have setup an IPSec tunnel successfully setup but the remote end insists of us masquerading our IPs. That's what I also did, but we have actually two local subnets that we need to connect throught the tunnel to the remote site. One of it is a Roadwarrior's VPN.
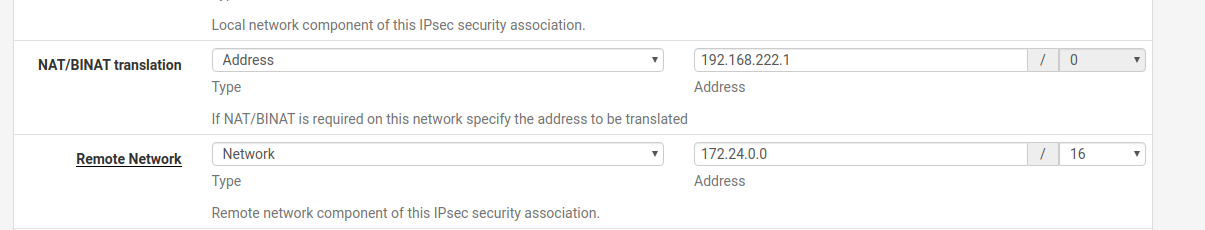
Do I have to add a second IPSec tunnel in order to achieve that?
I tried to add a second phase 2 element to the IPSec tunnel but only one local net is able to connect through the tunnel.Thank you
pfSense 2.4.4p3 -
Try using the split connection option, might be the other side needs that.
-
@wickeren
That worked, thank you very much. -
Hi, almost cross posting here
 . Because this need some visibility so other don't have to waste hours finding out that Cisco may needs this option with multiple phase 2 for a stable connection.
. Because this need some visibility so other don't have to waste hours finding out that Cisco may needs this option with multiple phase 2 for a stable connection.Ref: https://forum.netgate.com/topic/132546/ipsec-phase2-problem-pfsense-checkpoint
a slight hijack of this thread from me.Split Connection was the solution to my problems too. IKE2, multiple phase 2 and Cisco ASA don't play well together (single phase 2 had no problems). This particular connection has now bean stable, 14h and counting.
Brgs,