DNS Resolver high ping
-
Hi everyone, since I finished configuring pfsense I noticed that the status of the dns resolver I always have a high ping, pinging the dns 8.8.8.8 from a pc on the lan I get a ping from 10 to 13 ms while on the status the ping is 495.
I don't think it's normal, did I miss something in the configuration?
Here are the screenshots.
Thanks for your help.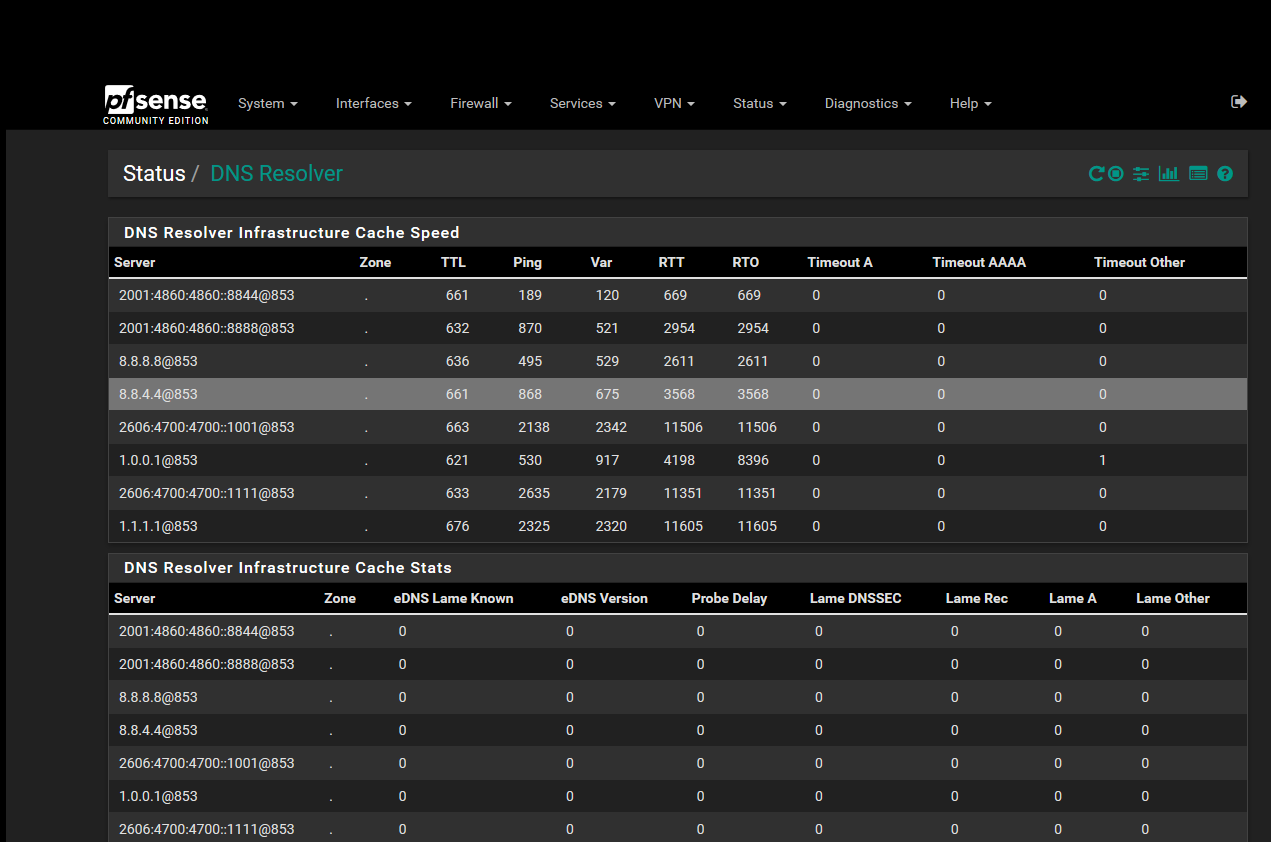
-
IIRC that's more of a "how long did it take to respond to this query" time than literally a ping. That will naturally be much higher than an ICMP echo since it is more complicated.
-
@jimp said in DNS Resolver high ping:
IIRC that's more of a "how long did it take to respond to this query" time than literally a ping. That will naturally be much higher than an ICMP echo since it is more complicated.
Thanks for the immediate response, do you say mine are acceptable times?
Because I saw some photos where people had much lower numbers.I forgot to ask you if you think the settings in the screenshots are okay?
Thank you. -
They seem a bit high but that could just be the speed/load/latency of your connection. There aren't any settings which would make that happen, except maybe very badly configured traffic shaping.
-
Now, for example, they have come down.
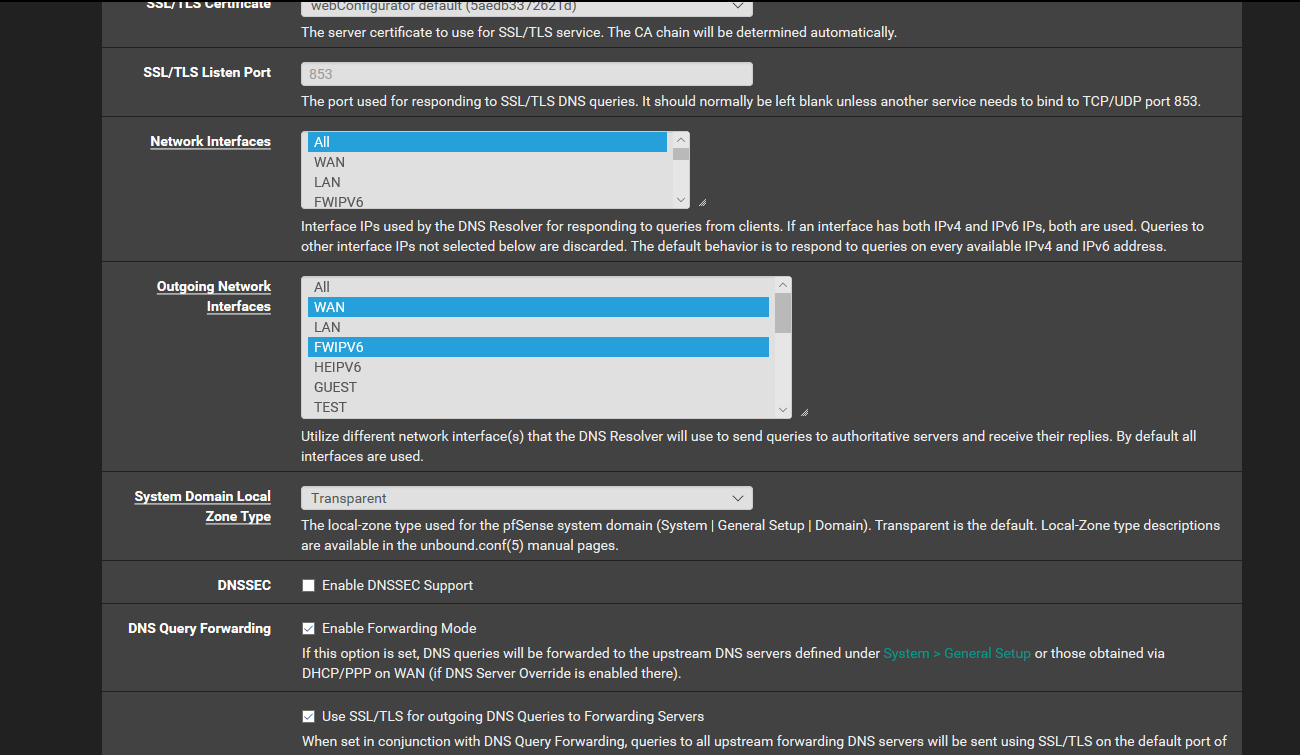
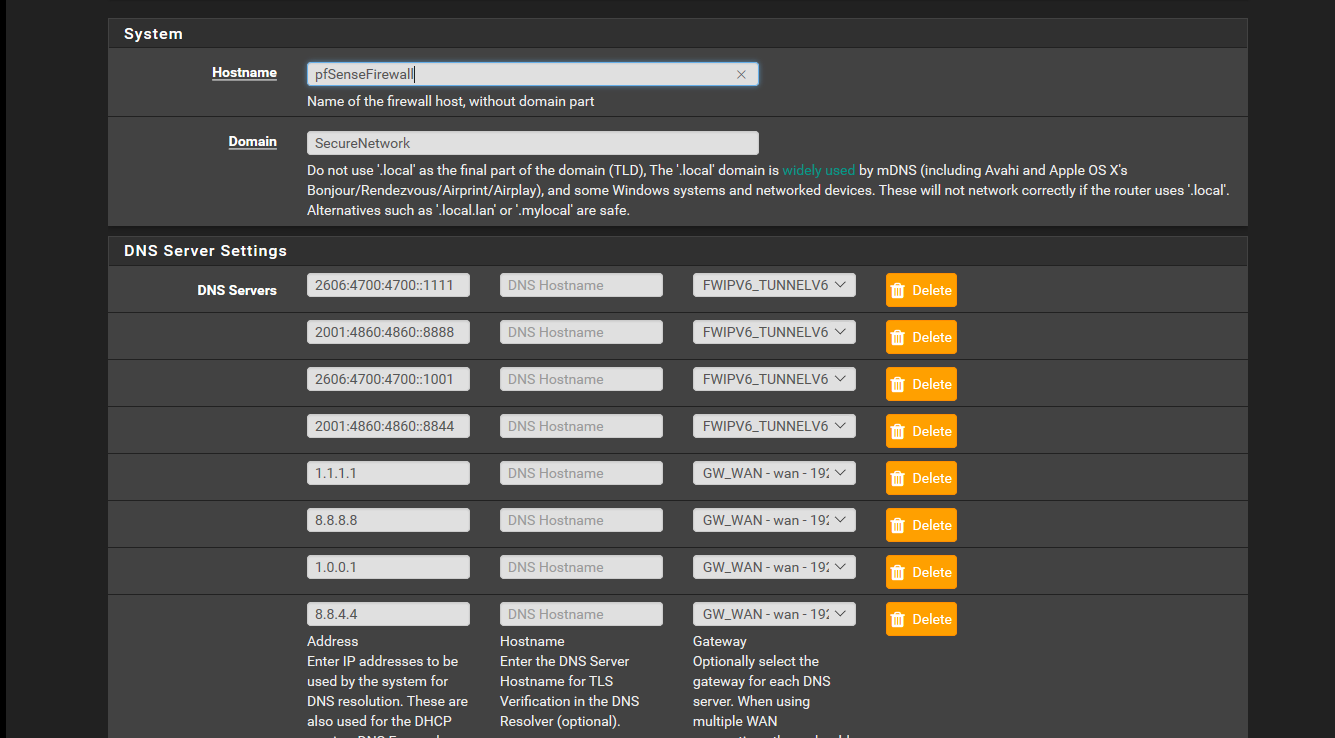
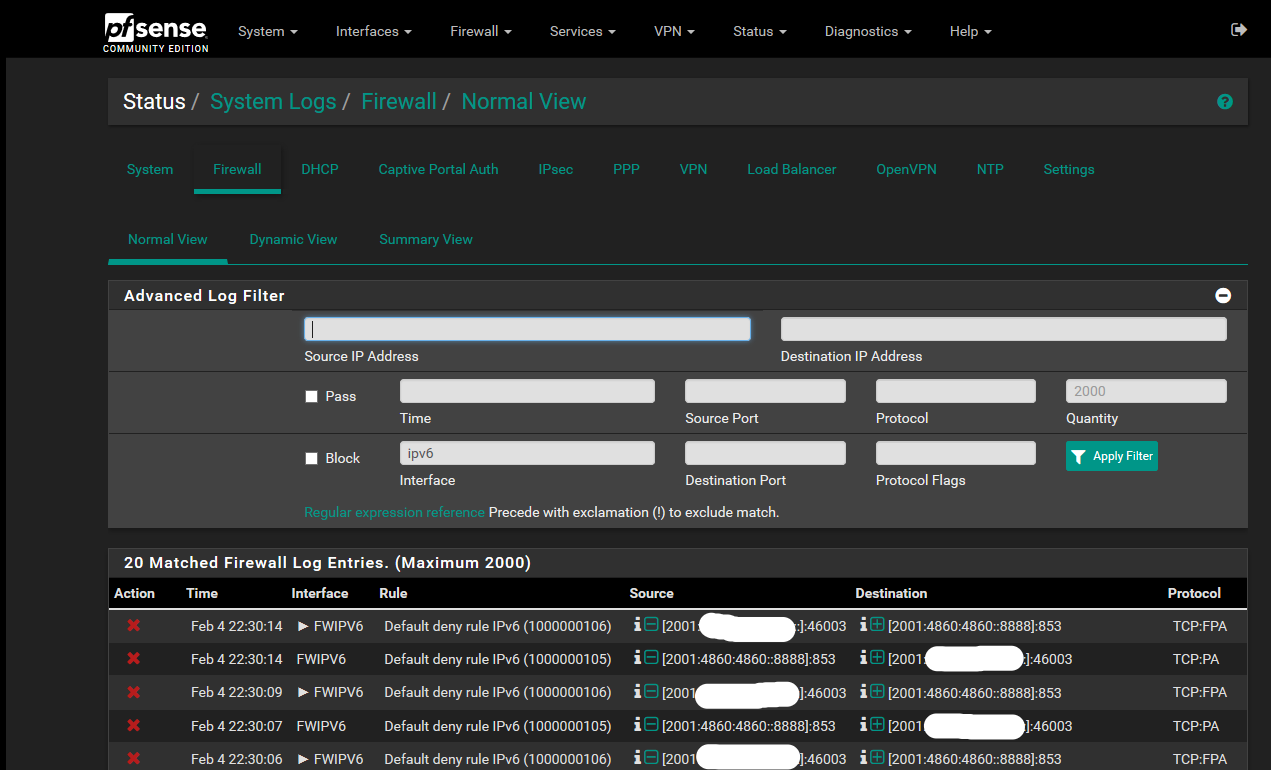
I take this opportunity to ask you one more thing, I noticed that some requests of the dns on the ipv6 tunnel instead of being on port 853 are on 53, but if I killthem in the log I see the connections as if they were on port 853.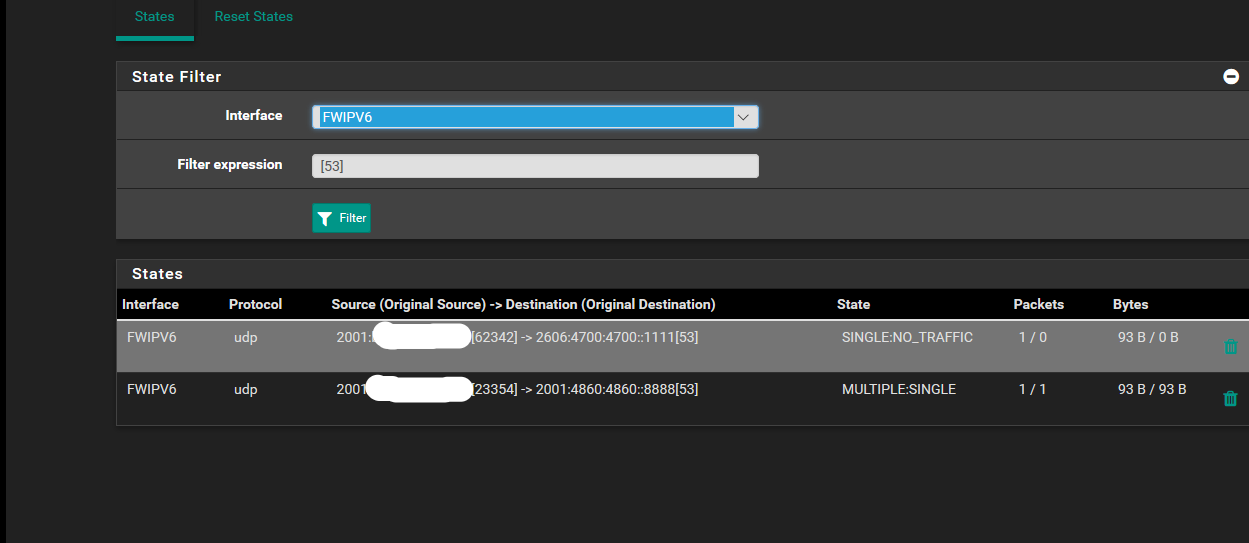
-
The DNS over TLS option is only for queries made through the DNS resolver. It wouldn't affect clients behind the firewall contacting the DNS servers directly, and also may not affect other services on the firewall itself if they make an outbound query directly (not to 127.0.0.1). That depends on your other settings for DNS under System > General, which you cut off in the images above.
-
@jimp said in DNS Resolver high ping:
The DNS over TLS option is only for queries made through the DNS resolver. It wouldn't affect clients behind the firewall contacting the DNS servers directly, and also may not affect other services on the firewall itself if they make an outbound query directly (not to 127.0.0.1). That depends on your other settings for DNS under System > General, which you cut off in the images above.
The two settings in general setup under the configured dns are deselected.
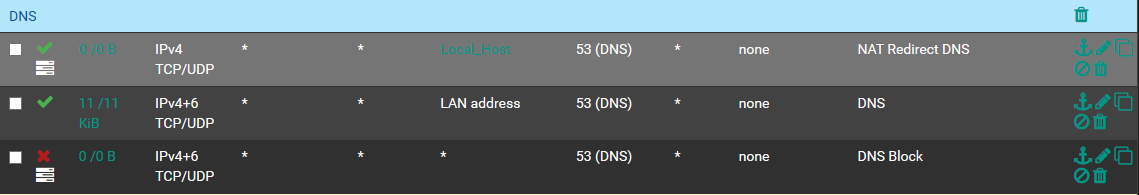
EDIT: On the lan the rules for the dns is configured them as per screenshot.
-
What is in
/etc/resolv.confon there? -
@jimp said in DNS Resolver high ping:
What is in
/etc/resolv.confon there?There are the DNS I have configured:
nameserver 127.0.0.1
nameserver 2606:4700:4700::1111
nameserver 2001:4860:4860::8888
nameserver 2606:4700:4700::1001
nameserver 2001:4860:4860::8844
nameserver 1.1.1.1
nameserver 8.8.8.8
nameserver 1.0.0.1
nameserver 8.8.4.4
search SecureNetwork -
Did you mask your search network... That search is going to slow down any queries because you would add that suffix. Which sure isn't a valid one.
Are you using that as single label domain?
-
@johnpoz
It's not very clear to me but I think you're referring to the domain configured in general setup, right?
Should I configure it with localdomain?EDIT: I understand what you mean and I use it in host overrides
@jimp
Even if you disable unbound, there are always requests on port 53 of 2606:4700:4700::1111 and 2001:4860:4860::8888 exiting the ip of the ipv6 tunnel. The two ip used are the first two set in general setup which have the ipv6 tunnel as gateway.
I think it is some service on the firewall that makes the requests, even if it is strange, because terminating the connections that have as destination the port 53 inside the register they appear communicating on the port 853. Is there any explanation for this?
How can I find out which firewall service is communicating without using unbound?
Thank you. -
Anyone have any ideas that can help me?
-
@mikekoke said in DNS Resolver high ping:
Should I configure it with localdomain?
You could configure it with something like name.localdomain, use of single label names is never a good idea.. If you want to use .securenetwork as tld for you domain sure that is fine... I would use something a bit shorter ;) I use local.lan for my domain as example.
Why do you have all those NS in there if your using the "resolver" did you change it to forwarder mode? Resolver needs nothing in there at all.. And to be honest if your resolving all you should have is loopback.
[2.4.4-RELEASE][admin@sg4860.local.lan]/root: cat /etc/resolv.conf nameserver 127.0.0.1 search local.lan [2.4.4-RELEASE][admin@sg4860.local.lan]/root:How can I find out which firewall service is communicating without using unbound?
There isn't one - not unless you installed some 3rd party package? Your clients could be asking dns, are you blocking all dns from your clients on your lan side rules to dns.
As to others showing faster times... Well yeah - if they are closer to the NS, they could have faster responses..
out of curiosity why do you forward vs just letting unbound resolve, which is the default config? But yeah if your going to use TLS for your forwarding the response time is going to be much longer!!! Much!!!
But pfsense dns client if set to use dns, how is it going to use tls, only unbound can use TLS... So if you want the firewall itself to use TLS, then you need to have it only ask itself, loopback... Yo would need to setup what to forward to in the custom options of unbound vs in the general settings.
-
@johnpoz said in DNS Resolver high ping:
@mikekoke said in DNS Resolver high ping:
Should I configure it with localdomain?
You could configure it with something like name.localdomain, use of single label names is never a good idea.. If you want to use .securenetwork as tld for you domain sure that is fine... I would use something a bit shorter ;) I use local.lan for my domain as example.
Why do you have all those NS in there if your using the "resolver" did you change it to forwarder mode? Resolver needs nothing in there at all.. And to be honest if your resolving all you should have is loopback.
[2.4.4-RELEASE][admin@sg4860.local.lan]/root: cat /etc/resolv.conf nameserver 127.0.0.1 search local.lan [2.4.4-RELEASE][admin@sg4860.local.lan]/root:How can I find out which firewall service is communicating without using unbound?
There isn't one - not unless you installed some 3rd party package? Your clients could be asking dns, are you blocking all dns from your clients on your lan side rules to dns.
As to others showing faster times... Well yeah - if they are closer to the NS, they could have faster responses..
out of curiosity why do you forward vs just letting unbound resolve, which is the default config? But yeah if your going to use TLS for your forwarding the response time is going to be much longer!!! Much!!!
But pfsense dns client if set to use dns, how is it going to use tls, only unbound can use TLS... So if you want the firewall itself to use TLS, then you need to have it only ask itself, loopback... Yo would need to setup what to forward to in the custom options of unbound vs in the general settings.
Hi, thanks for the help, I will change configuration and maybe set it similar to yours.
Yes I have installed some packages such as suricata, ntopng, openvpn, pfblockerng, telegraf and the services already available such as dhcp and radvd. I tried to disable one at a time but it didn't work.
My idea would be that the dns query of all clients on the lan and vlan point to the pfsense address, which would be the same as the gataway and pfsense forward them via tls to 2001: 4860: 4860 :: 8888, 1.1.1.1, ...
I would also like the firewall itself to do dns query via tls.
Clients will only use pfsense as dns, so they can use pfblockerng to filter, via a rule that allows it and one that denies the rest.
The rules for the dns on the lan that I published before, should redirect the dns queries to pfsense which forwards them if they have another dns, if I'm not mistaken.
The one below allows the dns on pfsense and the other blocks everything else, correct?
I tried to follow the guide on the forum but maybe I did something wrong, if you can explain to me how to do everything right so that it is fast, maybe I will remove tls, I would be grateful for it.
I hope I have explained myself, English is not my language. -
Anyone who can help me for a correct configuration?
-
Correct configuration for what? You want to tls foward to XYZ, and you don't want pfsense to be able to directly go to XYZ? Is that the configuration?
If multiple ns are listed in general, then pfsense could use any of those. And it would not use tls. So if you don't want pfsense to only ask any of those, and only unbound or dnsmasq va loopback, then that is the only thing that should be in general. Loopback.
And you have to tell unbound directly in its options to forward that traffic.
TLS fowarding via the gui of unbound would only be for clients asking unbound for something, not pfsense itself. Pfsense when it comes to looking up something it wants, ie checking for updates, package list, you asking to resolve an IP in the firewall logs, etc. Is just like any dns client, its going to be able to check all the ns listed, and you really never know which one that is. It should always check loopback first you would hope, but if you disable unbound so loopback didn't work - then it could and would check the others listed for it to talk to in the general setup.
-
Hi thanks, the correct configuration, which I would like to have, would be that all clients make requests to pfsense and then pfsense forwards them to be resolved.
Are you telling me that to do a forwarding with tls for the firewall I should remove ns in general setup? -
If what your concerned about is your clients, then the setup is not an issue.
What you brought up is you saw traffic that was not tls.. Pfsense as a client can and will talk to any IPs you put in general for NS... its a dns client as well.
If you put 192.168.0.1 and 1.1.1.1 on your machine in your network, can you be sure which one of those it will talk to? No.. So if you tell pfsense, hey you can talk to x y or z.. Then it can do that..
If you don't want pfsense to have the possibility to directly talk to some NS, then you can not put them in the general setting.. And only list loopback, which would be unbound.. Which in its config you have it only use tls to whatever upstreams you want.
The only thing pfsense is going to lookup, is updates, and package lists.. And if you say resolve some IP in your firewall logs... If you have some issue with that using the any of the NS you list in general via just 53 udp/tcp - then you can not put them there.
What is in your resolv.conf - that is who pfsense can talk to for dns. That is different than what unbound uses..
You stated your resolv.conf is this
nameserver 127.0.0.1 nameserver 2606:4700:4700::1111 nameserver 2001:4860:4860::8888 nameserver 2606:4700:4700::1001 nameserver 2001:4860:4860::8844 nameserver 1.1.1.1 nameserver 8.8.8.8 nameserver 1.0.0.1 nameserver 8.8.4.4So yes pfsense as a dns client can and would talk to any of those.. And it wouldn't do it via tls.
-
Okay I understand the speech, if pfsense does only that I don't worry. I did as you said and changed the domain. Instead my configuration, which you can see in the screenshots, is correct? I have removed tls, and it would seem faster.