Redirect incoming data to from an external IP to another external IP address destination.
-
Thanks for the reply @johnpoz
I've included an image showing how the devices should send data.
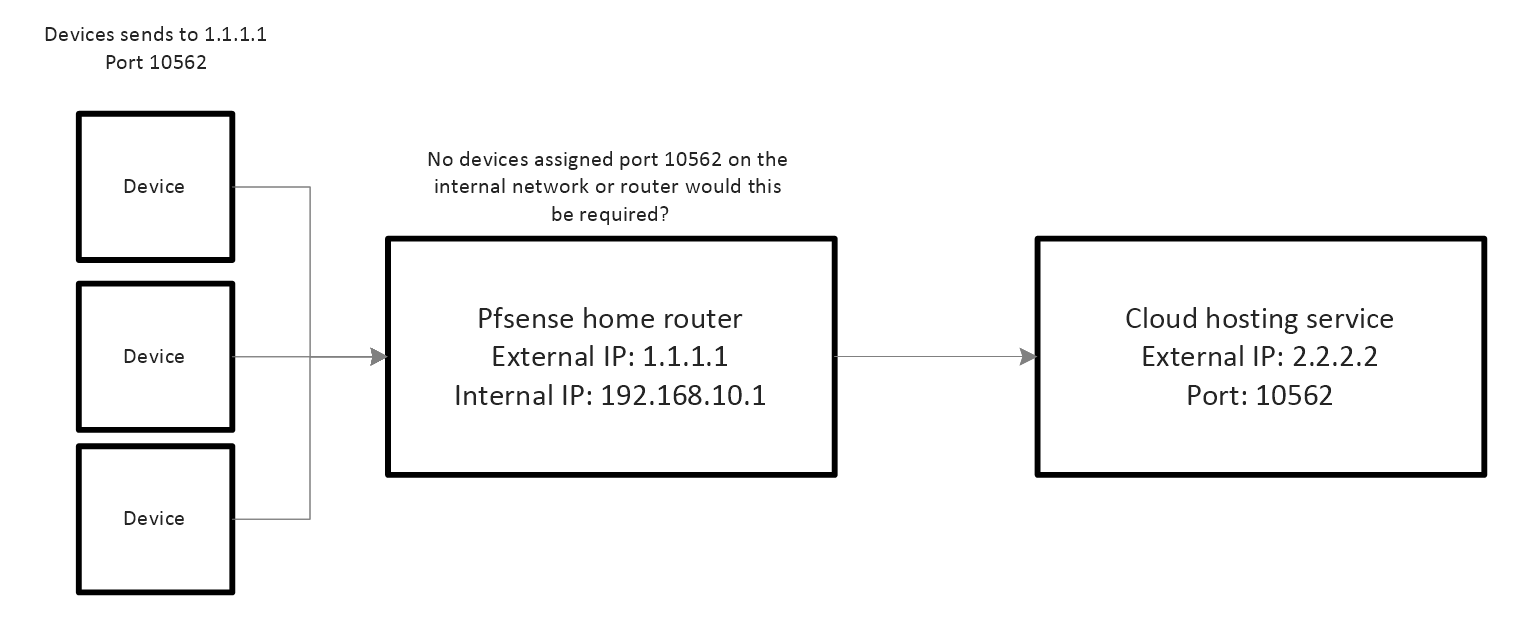
Disclaimer:
The devices get individual IP addresses every time they connect to the cellular network. So the source of the information is constantly changing for the Pfsense router. However, I have a static home IP address and a static cloud service address so these WAN addresses do NOT change.
The devices are programmed to just send to my 1.1.1.1:10562 through UDP and that's it. The main thing that I want is to get the router to forward ALL data coming to the home router on port 10562 directly to 2.2.2.2:10562.
It's probably obvious that I'm not a networking guy so I apologize if I have overlooked or misunderstood something completely here!
Thanks!
-
@anders-o said in Redirect incoming data to from an external IP to another external IP address destination.:
The devices get individual IP addresses every time they connect to the cellular network.
Huh?? So they don't use 192.168.10.1 as their gateway? They get an addresses that are not in the 192.168.10 network?
they are some public IP, that would send data to pfsense IP? 1.1.1.1
-
Yes, correct! Sorry, I should have explained that better.
All the devices connect to the telecom and get a WAN IP address every time they connect to the network and are not connected to my local network.
Like:
10.81.166.1
10.81.165.2
etc. -
Well they wouldn't be 10 address.. They would have to be natted at some point to talk to public.
But forwarding to some other external, if you hitting your wan IP.. Would be like this
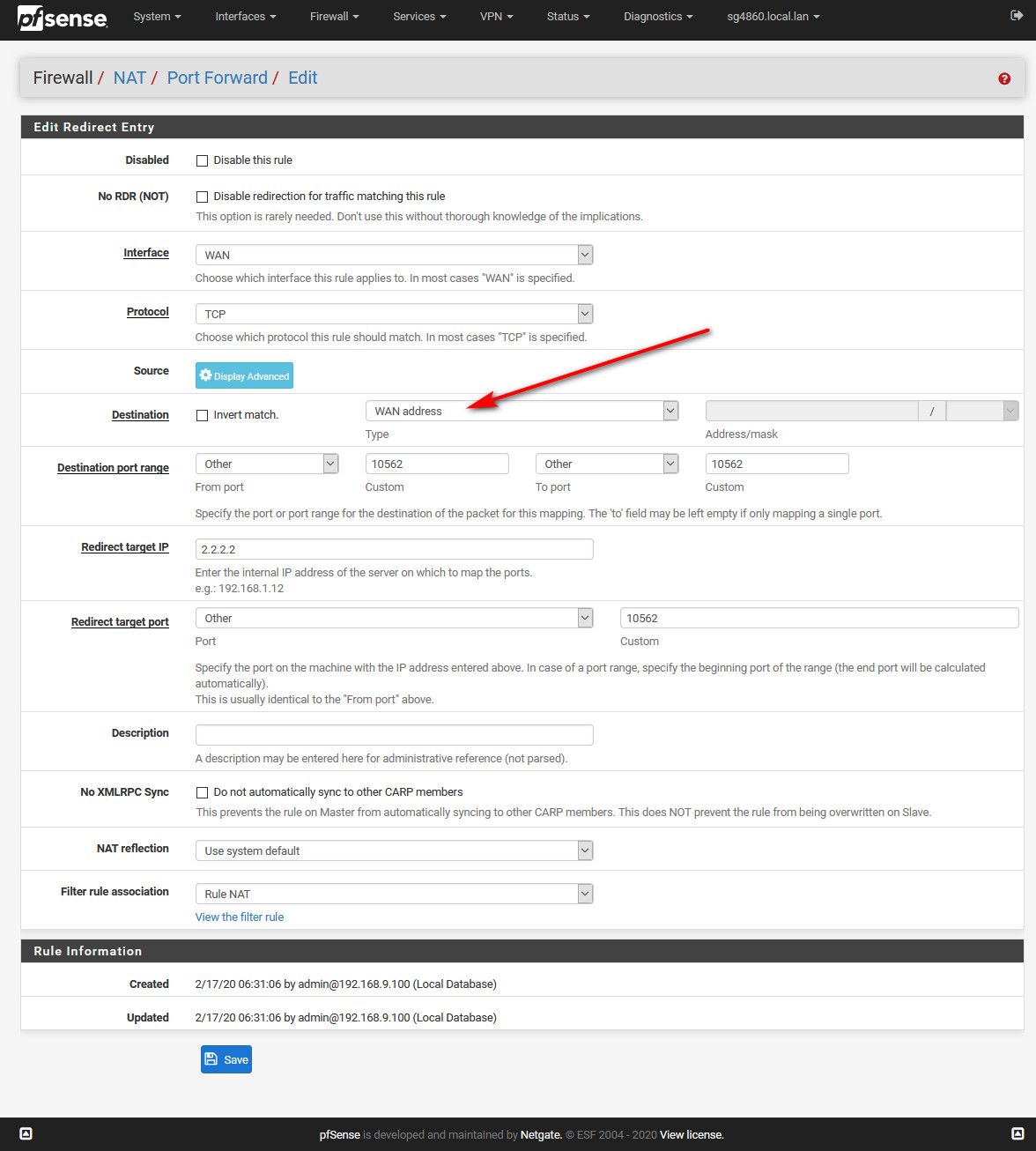
The traffic is going to my wan IP, 1.1.1.1 in your example.. Mine is 64.53.x.x dest would be your port 10562, and where your sending it 2.2.2.2 10562
So I went to can you see me, and sent traffic to my IP on 10562, and you can see from the sniff pfsense sends it out to 2.2.2.2 without changing the source IP.. If all you need is some UDP traffic this could work..
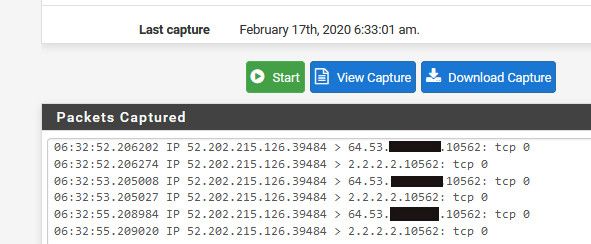
-
You're right they seem to have a different IP address than 10 addresses.
As shown here the device sends data to the 10564 however I can't see that the data gets forwarded. And looking on the cloud server, it doesn't receive any data.
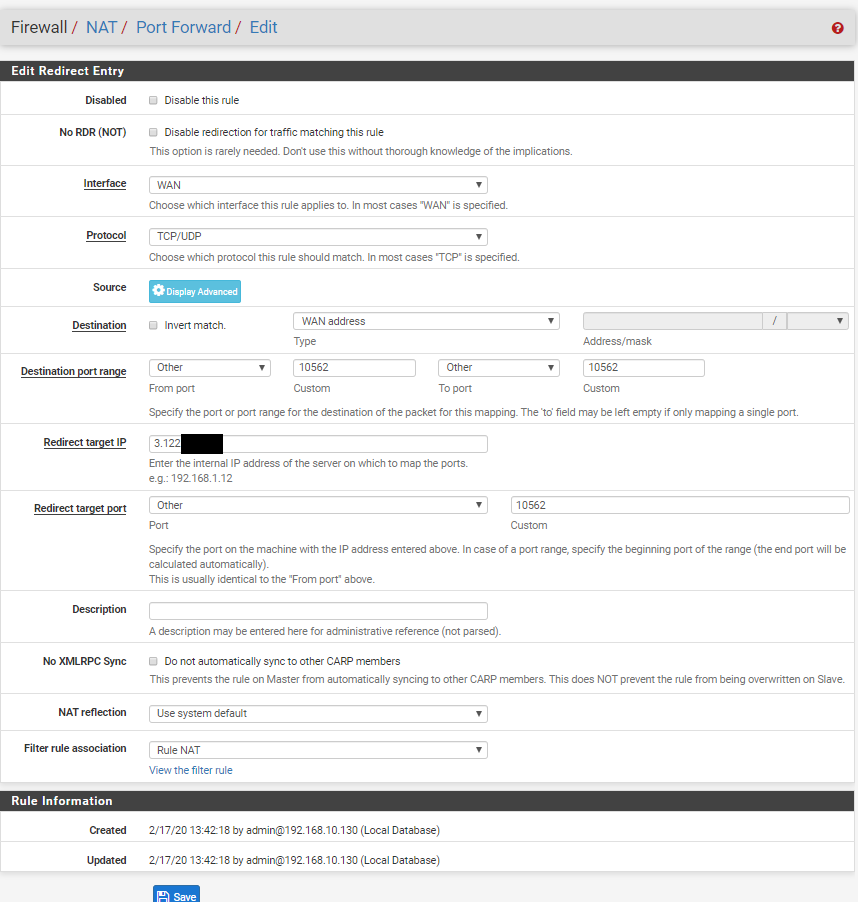
Here is the setup as you instructed. I changed it to affect TCP/UDP and not only TCP as shown in your example as this wouldn't work for my UDP packets.
Can you see that I'm doing something wrong?
Thank you so much for the time and help your providing!
-
Why do you have Rule NAT for association.. What are you firewall rules on your wan? Do you have something else forwarding say this traffic inbound currently?
Your forward is for 10562, but your traffic is hitting 10564 via your sniff.
Here I changed it to udp... I had to ssh to one of my vps to be able to send a udp packet on that odd port.. can you see me doesn't test udp.
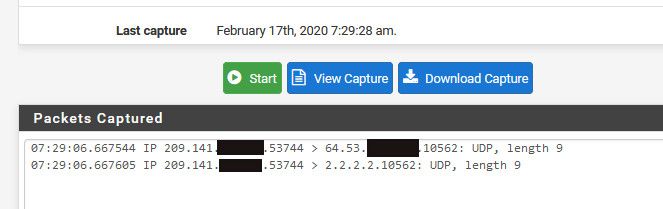
-
Now it seems to be working. And yes, I had the wrong port which I believe was the root of the problem here. I facepalmed rather hard after realizing I had written the wrong port number.
Now the log shows:
14:26:29.771406 IP 193.181.245.214.62668 > 51.174.x.x.10564: UDP, length 39
14:26:29.771426 IP 193.181.245.214.62668 > 3.122.x.x.10564: UDP, length 39
14:27:34.731419 IP 193.181.245.220.32867 > 51.174.x.x.10564: UDP, length 39
14:27:34.731441 IP 193.181.245.220.32867 > 3.122.x.x.10564: UDP, length 39So I think it should work fine now right? If I don't get any data now on my cloud server then it should be an issue with my firewall on my cloud server?
-
Well you can always sniff on your cloud server I would hope to validate the traffic got there, but as you can see pfsense sent it on, with the original IP as source, and even same source port.
-
Update:
I've attempted to figure out why the AWS instance doesn't receive any data and I'm a bit unsure if the firewall is the cause of the issue here.
I've included the settings of what the router has in the firewall to see if anything is wrong here.
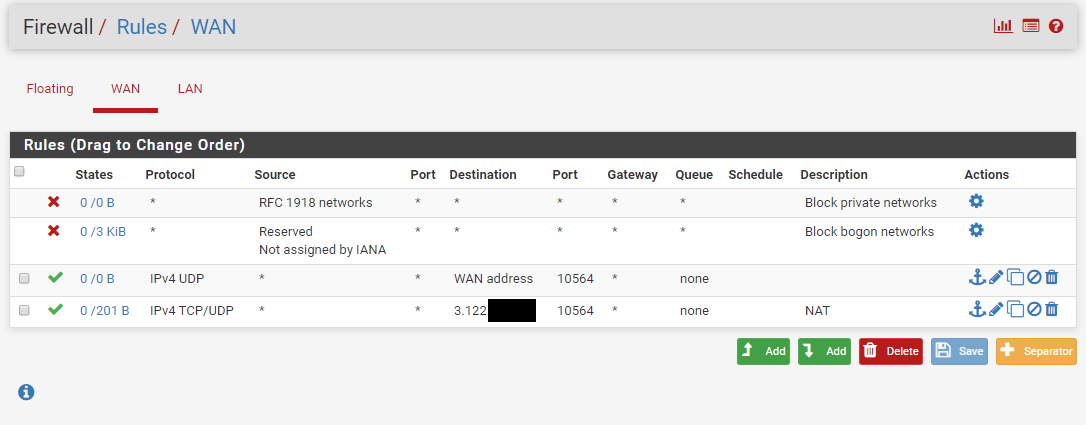
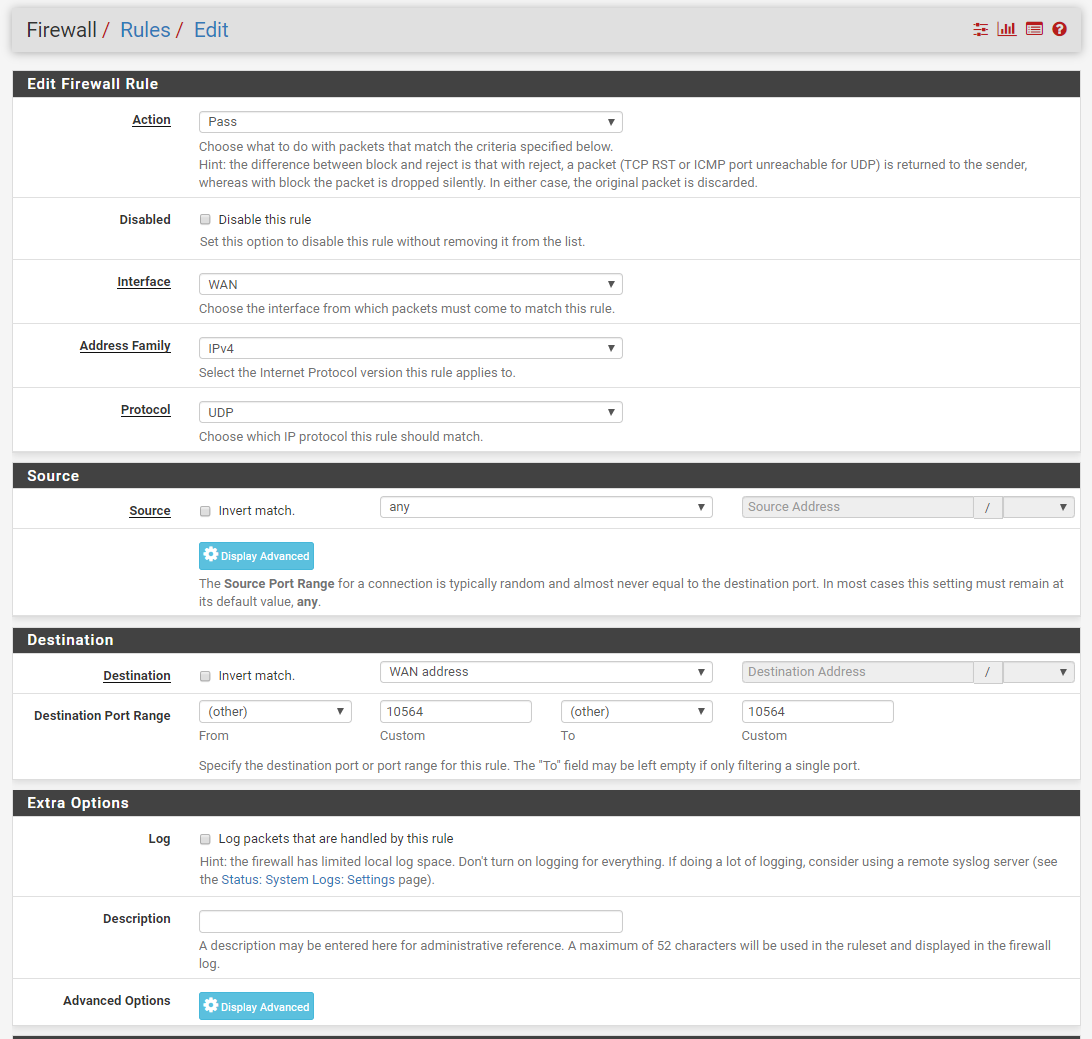
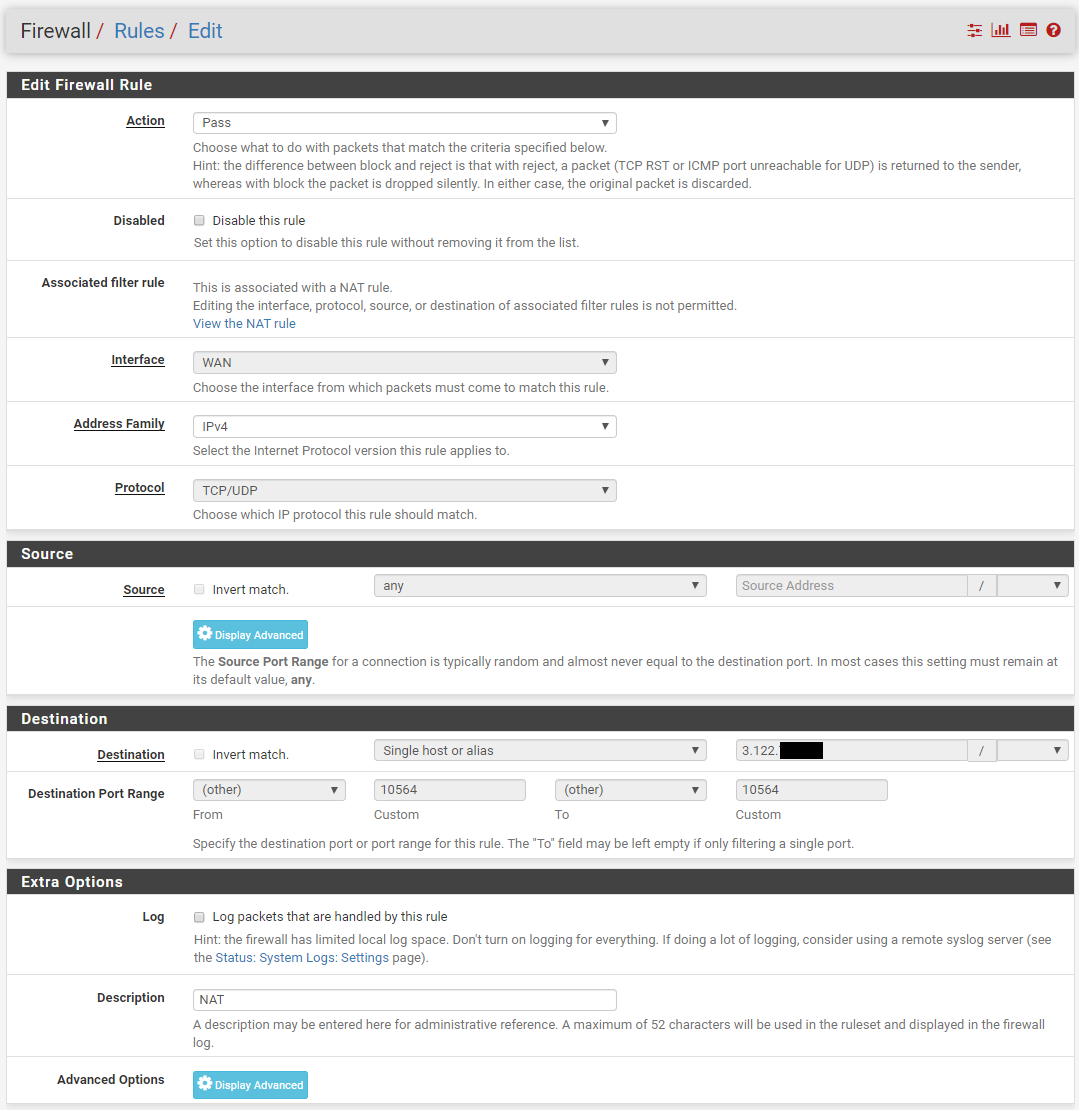
Can anyone see any issue here? PS. I've not done any other configuration than shown in this post and the previous. So if there are some crucial settings please let me know.
-
so you have another pfsense firewall in your aws.. And then your trying to forward to something behind that, which would be on a rfc1918??
If its public, you wouldn't be natting. So if its rfc1918 behind pfsense your forward to a 3.x address all wrong. Just follow the guide to find out what is wrong.
https://docs.netgate.com/pfsense/en/latest/nat/port-forward-troubleshooting.html
-
There isn't any blocking on the AWS in the firewall for this port. It just goes directly to the EC2.
The Devices are on a public IP 193.181.245.220:37072 that sends to my home address 1.1.1.1:10564 and then I want to send this out again to another external network 2.2.2.2:10564
So basically.
My telecom network -> My home network -> AWS cloud network so all of this is to my knowledge public networks.
-
Dude we already went over this.. And you showed it working. Are you trying to send different traffic somewhere else? You can not send traffic hitting your pfsense on IP port X to more than 1 place..
@anders-o said in Redirect incoming data to from an external IP to another external IP address destination.:
Now it seems to be working. And yes, I had the wrong port which I believe was the root of the problem here. I facepalmed rather hard after realizing I had written the wrong port number.
Now the log shows:
14:26:29.771406 IP 193.181.245.214.62668 > 51.174.x.x.10564: UDP, length 39
14:26:29.771426 IP 193.181.245.214.62668 > 3.122.x.x.10564: UDP, length 39
14:27:34.731419 IP 193.181.245.220.32867 > 51.174.x.x.10564: UDP, length 39
14:27:34.731441 IP 193.181.245.220.32867 > 3.122.x.x.10564: UDP, length 39
So I think it should work fine now right? If I don't get any data now on my cloud server then it should be an issue with my firewall on my cloud server?