IPv6 with two or more LAN-side interfaces
-
The allowed indices on tracking interfaces are controlled by the DHCPv6 Prefix Delegation Size on the WAN and what is received from the ISP. For /64 that means only one is allowed (0). For a /60 that would allow 16 networks, so the ID can be from 0-F (it's in hex).
If you do not know what your maximum prefix delegation size is, contact your ISP. You might be able to just try larger values and see what happens, or check in the DHCP logs, but the best way to know is to ask the ISP.
-
@jimp said in IPv6 with two or more LAN-side interfaces:
You might be able to just try larger values and see what happens, or check in the DHCP logs, but the best way to know is to ask the ISP.
Or, if you're handy with Packet Capture and Wireshark, you can see what is provided. The prefix size and address are provided in both the Advertise XID and Reply XID lines.
-
@JKnott I am not. So I tried 63 and 60 and none of my LAN-sided interfaces got an IPv6. So I am out of luck with my ISP.
Is there another solution to provide IPv6 to those Interfaces or is it just not possible, without using Hurricane Electric IPv6 Tunnel or something different?
-
@Bob-Dig
First, find out what your ISP provides. Did you check /var/log/dhcpd.log as @jimp suggested? In it, you will see something like:
Feb 12 09:19:18 firewall dhcp6c[18217]: <3>[prefix] (6)
Feb 12 09:19:18 firewall dhcp6c[18217]: <3>[::] (2)
Feb 12 09:19:18 firewall dhcp6c[18217]: <3>[/] (1)
Feb 12 09:19:18 firewall dhcp6c[18217]: <3>[56] (2)
Feb 12 09:19:18 firewall dhcp6c[18217]: <3>[infinity] (8)
Feb 12 09:19:18 firewall dhcp6c[18217]: <3>end of sentence [;] (1)The 56 above is my prefix length.
You might also mention your ISP, so that someone else here might offer advice.
-
@JKnott Nothing like this in the logs.
-
@Bob-Dig
You have Start DHCP6 client in debug mode enbled on the WAN interface ?
-
@NogBadTheBad Not till now, will give it a try.
-
@Bob-Dig said in IPv6 with two or more LAN-side interfaces:
@NogBadTheBad Not till now, will give it a try.
Just a thought, not sure if it will give you the answer you need.
-
@NogBadTheBad Looks like it:
Feb 14 17:01:41 pfSense dhcp6c[73783]: get DHCP option IA_PD, len 41 Feb 14 17:01:41 pfSense dhcp6c[73783]: IA_PD: ID=0, T1=302400, T2=483840 Feb 14 17:01:41 pfSense dhcp6c[73783]: get DHCP option IA_PD prefix, len 25 Feb 14 17:01:41 pfSense dhcp6c[73783]: IA_PD prefix: 2a02:xxxx:xxxx:xxxx::/64 pltime=604800 vltime=1209600 Feb 14 17:01:41 pfSense dhcp6c[73783]: get DHCP option preference, len 1 -
@Bob-Dig
Might want to hide part of the IPv6 address.
-
So is there any option left with that ISP-IPv6 or no?
-
What lengths did you try? Only 64, 63, and 60? You should at least try some other common ones: 56, 48, etc. before ruling them out.
-
@jimp Ok, tried them now, not working.
-
@Bob-Dig said in IPv6 with two or more LAN-side interfaces:
So is there any option left with that ISP-IPv6 or no?
You could try mentioning what ISP that is. There might be someone here who has experience with them.
-
-
@Bob-Dig
Well, it's hard to know what to believe, when you won't mention who the ISP is. If all you get is a single /64, then you can't do much, as both SLAAC and DHCPv6 require a full /64 to work properly. One option would be to use he.net for a 6in4 tunnel.
They provide a /48. -
Interesting, never thought something like that with all the IPv6-addresses we got, little that I know.
The ISP is
https://www.pyur.com/Thanks @ all
-
@JKnott said in IPv6 with two or more LAN-side interfaces:
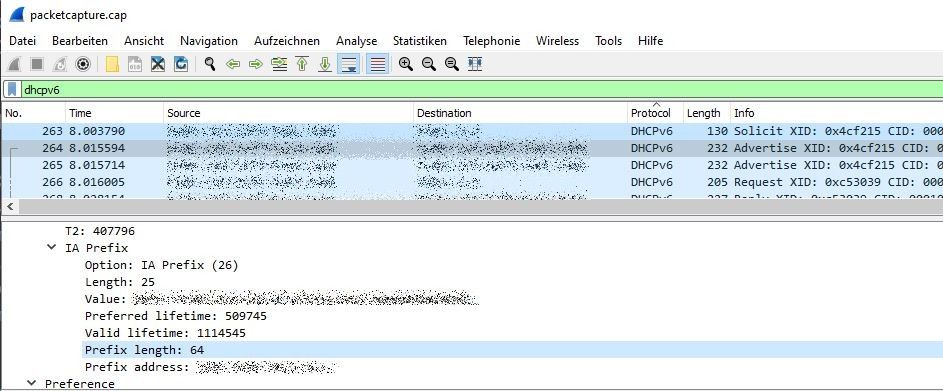
Or, if you're handy with Packet Capture and Wireshark, you can see what is provided. The prefix size and address are provided in both the Advertise XID and Reply XID lines.
Could you help me with that? I have downloaded Wireshark and also captured something and then loaded it in Wireshark.
But what should I capture in the first place and how to look for it in Wireshark would be much appreciated.
-
@Bob-Dig
To capture with Wireshark, you need some way to insert a computer running it between the modem and the pfSense computer. This is can be done with a managed switch, configured for port mirroring. Failing that, you can use the Packet Capture that's built in to pfSense. You can then capture the packets when you disconnect/reconnect the WAN port. You can then download the capture to view in Wireshark. If you use a managed switch, you can capture everything from power up, instead of just disconnecting the WAN port. You want to filter on DHCPv6, which is port 546 or 547. You can use either. That should leave you with the XID packets, which you can then open and find the info.
-
@JKnott So is that it? Or is it not?