Web gui access limitation
-
Hi all,
Trying to block access to the admin Web GUI interface properly here so followed this guide: https://docs.netgate.com/pfsense/en/latest/firewall/restrict-access-to-management-interface.html
Since I have about 15-20 interfaces I actually added a floating rule to block this instead which works on this firewall, however this firewall is in a cluster of two and I'm still able to access the secondary firewalls admin interfaces.Any ideas?
Thank you!
-
Hmm, you mean the 'This Firewall' system alias doesn't block access to the Secondary?
I expect it to apply equally to the Secondary once the ruleset is pushed across. Can we see the actual rule(s) you used?
Steve
-
Hi Stephen,
I'm very sure it's just some misconfiguration on my part here.
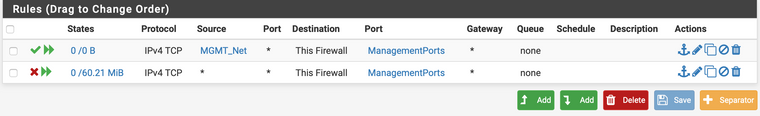 Like I mentioned before it's a floating rule due to us having quite a lot of interfaces.
Like I mentioned before it's a floating rule due to us having quite a lot of interfaces.
So a test scenario is as follows, we might have a client machine on the 172.16.10.0/24 network and a dmz on 172.16.128.0/24 network. In our specific case as well the client is also allowed to connect to anything outside of our internal networks on port 80 and 443 accordingly to a rule on it's specific interface;
Two firewalls in a cluster configuration, firewall-1's interfaces are 172.16.10.2 and 172.16.128.2 and firewall-2 is at 172.16.10.3 and 172.16.128.3 (CARP addresses are on .1 for both networks).
From the point of view of the client at IP 172.16.10.100 he cant reach 172.16.10.1+2, 172.16.128.1+2 but he can reach the firewall web gui at 172.16.128.3.The same rules are on the second firewall as well due to the sync between them.
Let me know if you need any more information, any ideas or input would be appreciated.
Thank you! -
What about 172.16.10.3?
Was the 172.12.128.0 subnet originally LAN? Check that the anti-lockout rule is not still enabled on the Secondary, that is not a setting that is sync'd between the nodes.
Testing it here it works as expected once I had removed the anti-lockout from both nodes.
Steve
-
Hi again Stephen,
That's a good point I actually hadn't done any test towards 172.16.10.3 but to answer your question I actually can't reach that one.
The 172.16.128.0 subnet has never (afaik) been on the LAN interface.
I think you actually found the problem and it looks like it's the anti lockout rule that's causing the issue, just tried real fast to remove it and it looks like I can't connect to the .3 address anymore.
Will run some more test just to make sure but I think that was the issue.Thanks again!
-
Nice. Let us know if you are able to connect, that would definitely need looking at if so.
The generated ruleset on the secondary looks good here though.
Steve