multi Phase 2 with vti IPsec and tunnel for Site-to-Site IPsec for Internet Traffic
-
Hello
I have the following setup:
pfSense site A
WAN 123.123.123.1
LAN 192.168.1.0/24
DMZ 192.168.2.0/24pfSense site B
WAN 123.123.123.10 (and virtual IP 123.123.123.11)
LAN 192.168.10.0/24I have a routed vti IPsec tunnel between site A and site B with static routes for 192.168.1.0/24 and 192.168.10.0/24 which is working fine.
Now i wanted to add a site-to-site tunnel for the DMZ on site A and the pfSense on Site B. The internet traffic should be routed thourgh the ipsec tunnel.
I followed the following tutorial:
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/routing-internet-traffic-through-a-site-to-site-ipsec-vpn.htmlFor this scenario i added a second phase 2 entry:
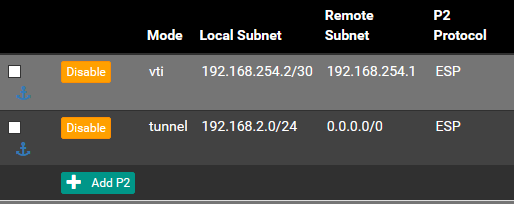
Everything is also configured on the other side.
The traffic from 192.168.2.0/24 to the internet always uses the gateway on site A, but i want it to be tunneld through the IPsec tunnel to site B. After some time everything breaks and nothing works anymore.It seems that 192.168.2.0/24 used the routed vti interface.
Is there something wrong in my configuration?
Thank you.