Isolate a network with a second TpLink router on OPT1
-
Hi,
I want to isolate a network. For that, I'm trying to connectthe WAN port of a TP-Link router to the OPT1 port on my pfsense. I've create my interface on pfsense with a DHCP server. My TP-Link receive hi IP address correctly. Internet is on the pfSense WAN port. PC on the LAN TpLink network can ping TPLink WAN IP address but not the pfSense OPT1 interface IP.
Here's a quick network schema : https://drive.google.com/open?id=1xPN3cK5lqrnzYdoyW6lKW14k_uQp3YaF
I've done a test. Ping the OPT1 interface from a PC on the LAN side of the TPLink router. Packetracer on the pfsense see the packet but a route is missing to return :
15:39:37.129052 IP 10.10.10.5 > 10.10.10.1: ICMP echo request, id 1, seq 4071, length 40I know one route is missing on my pfsense, but I don't understand the logic to create it. Do I have to create a new gateway?!
If someone can help me, I'd really appreciate!
Thanks in advance!
-
If your IP addresses are in fact setup like your "schema" drawing, everything looks good.
On any additional networks/interfaces you add/create on pfsense, you need to add a pass rule to get traffic moving.
So... in pfsense, in the Firewall -> Rules section, add a new rule on the OPT1 interface. Set it up like this:
Action = Pass
Interface = OPT1
Address Family = IPv4+IPv6
Protocol = Any
Source = OPT1 net
Destination = anyGive it a good name in the description field, then click save.
You might need to reboot your pfsense box, and you might need to reboot your TP-Link router box.
Jeff
-
@akuma1x Thanks! You rules! :)
With that rules that works! With rules, I blocked access to network directly connected to the LAN port of the pfSense. For a security reason, I only want my backup VEEAM machine on the LAN network to have acces to a NAS on the network 10.10.20.0. I'm currently testing some rules and I know there is different way to do it, but I'd like to know the best way to do it with pfsense ... the more "conventionnal" way to avoid any problem!
Is there a way to simply add a route? When I'm trying to add a route, I need to create a gateway absolutely?!?!?
Thanks again!
-
@M0L50N You say "for a security reason" but not much more detail.
I'm assuming you mean that you want to secure your LAN network from your OPT1 network, correct? If so, you need to make a couple of settings.
- Create an alias on your pfsense box under Firewall -> Aliases. Make it look like the screenshot below.
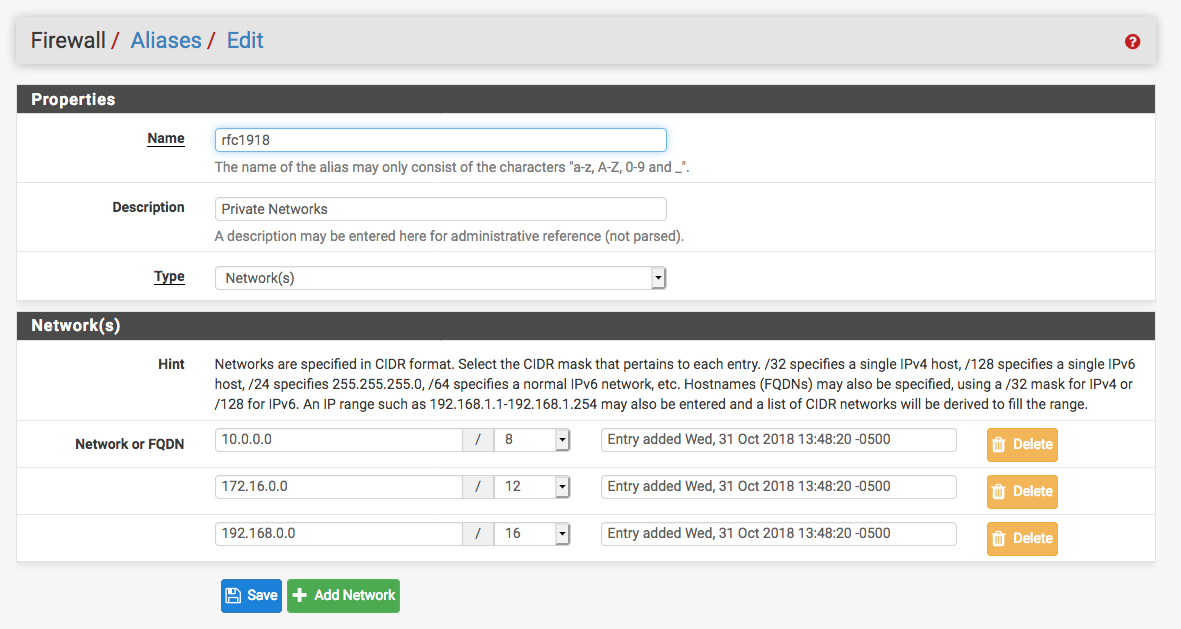
- Then, on the OPT1 network/interface, create a block rule that blocks the OPT1 network from talking to any private networks, basically anything else you've got setup on your pfsense box as a LAN network. See screenshot below. I use a network called CAMS, but you need to use your OPT1 network in that box.
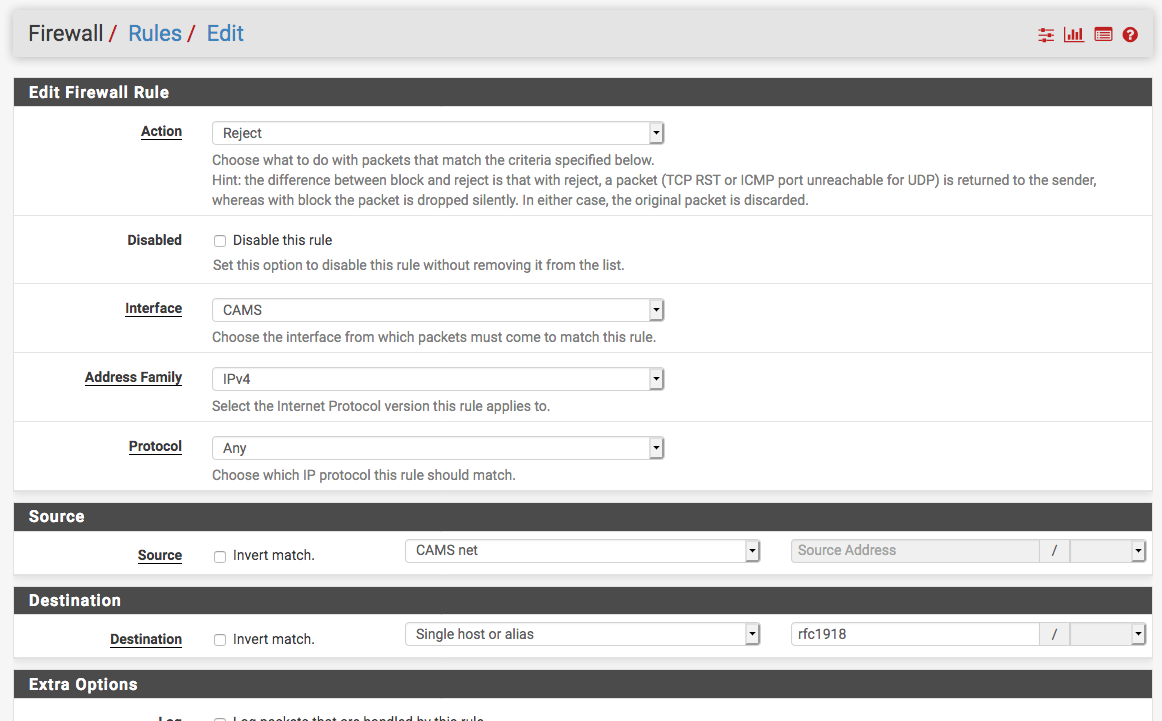
- Put this new block/reject rule above your OPT1 "pass any" rule we talked about earlier, and you should be good to go.
Jeff
-
Thanks again for your answer. Finally, I modify my "Pass any" rules to only let the network on OPT1 and WAN to talk between us. I used the option "not" to invert the sense of the match for the destination "LAN net". For now, PC on OPT1 network (unsafe area) cannot ping any PC on the LAN (safe area), but OPT1 network can access WAN for the internet.
My next challenge is to permit my VEEAM server on the LAN net to have access to a NAS on the OPT1 network! Do you have a good idea to do it properly? NAT forwarding from my TP-Link router connected to the OPT1?**
Thanks!
-
Should be as simple as putting in a pass rule on your LAN network for that VEEAM server machine to the OPT1 network address for the NAS machine. What will trip you up is if the NAS box is running a firewall of it's own that blocks communications from hosts NOT on the same subnet as itself.
Also, if you have enough physical ports on your pfsense box, or have a smart managed switch that can do VLANs, you should remove that TP-Link router from your network. It's unnecessary. You can program pfsense to do everything it's already doing, plus whatever the TP-Link box is doing.
Jeff
-
@akuma1x for now, I only testing it with a PC (not a NAS). I've create a rule on interface LAN with the source IP addresse = My VEEAM server, and Destination my PC test on the other side isolate network on TPLink LAN side. this doesnt work. Can it be related to the rules order on the LAN interface? I've put this rules at the end, if this rule is after a Default allow LAN to any rule, is it OK? By the way, if I have a Default allow LAN to any rule, I don't need to add a rule for specific host?!?!
I've create a rule host to host on LAN interface and on the OPT1 interface with ANY protocols and it dont work!?!?!?
-
Post up screenshots of your firewall rules. And, like I said earlier, that extra router behind pfsense is probably causing the problems.
Jeff