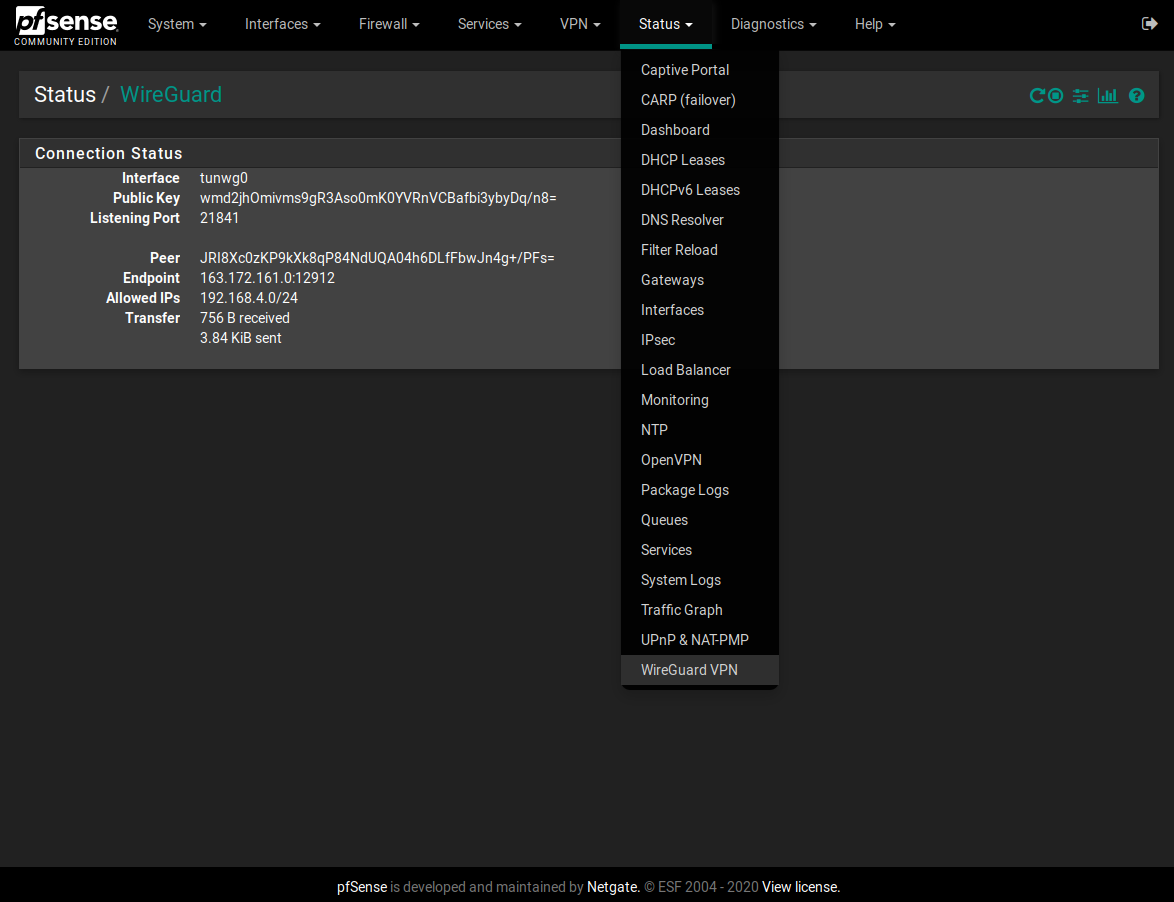
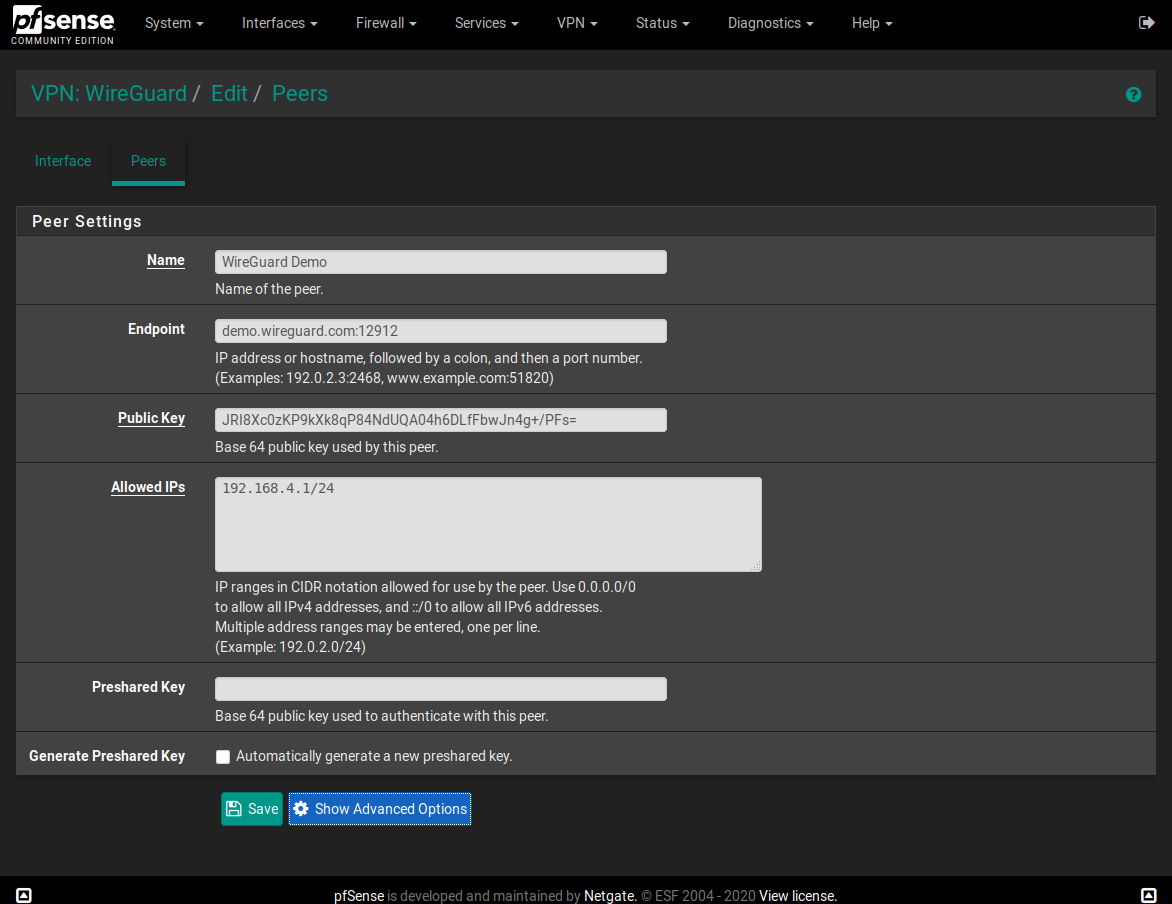
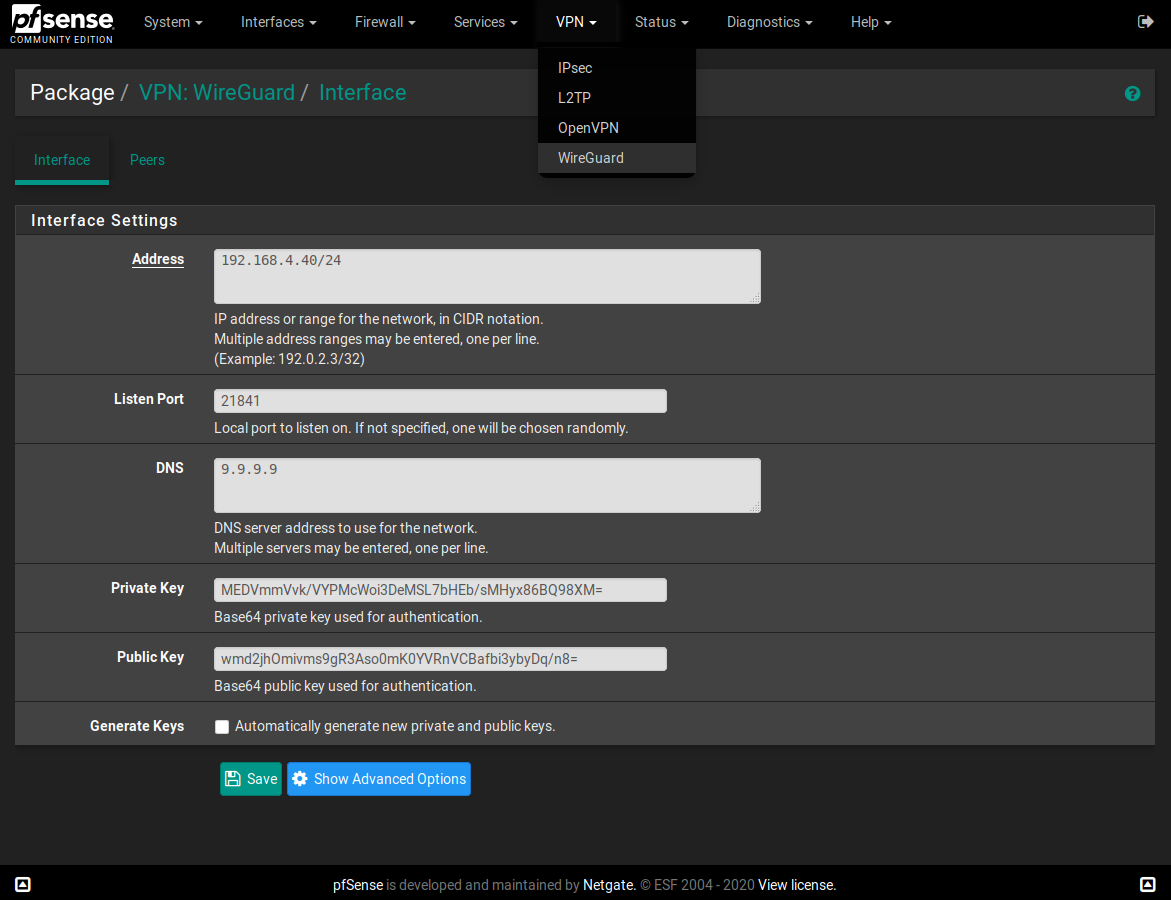
I made a WireGuard package for pfSense
-
@lucas_nz Thanks for your effort, I have a question, currently I have already installed version 1.0.0, how can I upgrade the package to your version (1.0.1) ? is it ok to just install it over the original one or ? Thanks.
-
@a-katib91 I did pkg remove and then pkg add on the new package.
Use "pkg info | grep wireguard" to determine what package to remove and then just add the one you want. You might need to reboot, but I am not sure. -
@ubernupe Fantastic!!!
I set up a server on VMware ESXi and managed to build the package. I downloaded your version and thats the one I am using, but I just wanted to be able to build packages for the 2.5 in case someone makes improvements.@dubatech the weird thing is that in the gateway section, Gateway is set to dynamic and greyed out.
If I manually edit the file I could put in the 1.2.3.4 (as in your example), but I cannot change the IP lates on. Then I get an error message The gateway address 1.2.3.4 does not lie within one of the chosen interface's subnets, which seams strange since 0.0.0.0/0 should be pretty much the whole internet. I thought adding 1.2.3.4/32 as allowed IPs would solve this, but now I found the "Use non-local gateway through interface specific route."
It is working great with 2.4.5, so I am happy with it.2.5 is another story. It starts working when I make adjustments and then dies after a while. From 5 minutes to 30 hours in my case. I have this monitoring where I monitor both OpenVPN and Wireguard from both firewalls. It is always 2.5 with wireguard that stops working and the other three works all the time...
-
@Talisker thanks, that worked.
-
I am having huge problems with the 2.5 version. The tunnel goes up and traffic flows. After a while it just stops. The only solution I have found is to reboot the firewall. Slightly annoying.
However. The 2.4.5 version is working perfectly. No downtime the last two weeks with Lucasnz package.
Btw, I discovered "Tag" and "Tagged" with floating rules in order to prevent traffic to leave the wrong way (directly to internet). PFSense is really weird considering rules and routing.
-
Don't know if happened to someone else, but I've problems with the 4th tunwg interface created.
I've removed tunwg3, then reinstalled @lucas_nz pkg, but nothing: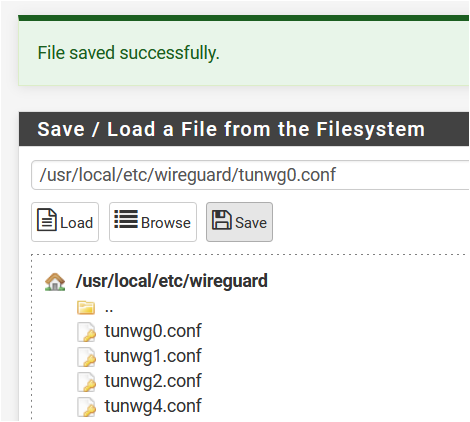
Here is the output of ifconfig:
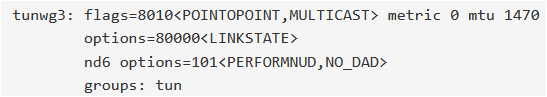
Is there a way to delete it?
I've created a new interface tunwg4 and it works but tunwg3 still visible.I'm on pfSense 2.4.5-RELEASE-p1 and using lucasnz pkg v1.0.1.
Thank you so much
Update: OK, just a reboot fixed the problem!
-
-
@abidkhanhk I followed the how to earlier in this thread.
-
For you and any and all seeking a setup guide - see below :
https://forums.torguard.net/index.php?/topic/1975-ascrod-ashus-pfsense-pkg-wireguard-tutorial-guide/
Also if you read through this thread see here ( my post ) - you can see the attached text for how to build / compile packages - and much more :
https://forum.netgate.com/topic/150943/i-made-a-wireguard-package-for-pfsense/125
Peace -
-
Many thanks!!! exactly what i was looking for.
-
Hi Guys,
I'm just curious. How long do you all think it will take to get wireguard as an offical package for pfsense? I'm pretty egar to start using it.
I would ideally like to have it running on a pfsense box that way I can have suricata and other things running to protect it. But who knows, maybe I can just run wireguard as a linux server behind a pfsense box.
Anyways, I just did a test on performance. I have a 1 gig office network and a 1 gig home network. Bother are 1000/1000Mbps. So I did iperf on openvpn and got 50Mbps, when I ran an SMB file transfer over the tunnel I got 350Mbps.
Then I did iperf on wireguard tunnel and got 300Mbps, and the SMB file transfer of 688Mbps which might be line speed considering overhead and travel time over the WAN?
This is a pretty powerful technology and I'm seriously considering putting it out in some of my production environments. I also like how simple it is to setup compared to OpenVpn. The only negative is that the Mac version of wireguard only works with Mojave or later.
Best,
Tidal -
@ubernupe said in I made a WireGuard package for pfSense:
Hello and I hope that you are safe and well. I compiled and built Lucasnz pfSense-pkg-wireguard-1.0.1 For 2.5.0. With all due respect to Ascrod and Ashus, I found Lucasnz to work perfectly on pfSense 2.5.0. For you to get a basic idea as to how to setup a FreeBSD 12 Build Server - see my old tutorial here :
I have pfSense 2.5.0 running on a SG-3100.
I did a system update tonight, and noticed there's a new wireguard-tools package:
https://forum.netgate.com/topic/155751/2-5-just-installed-a-new-wireguard-tools-package
Does anybody know what this is? Will it help to get Wireguard going?
-
@victorhooi that’s cool. So wireguard is under the package manager now?
Also curious for the developers. Does the wireguard package have the ability to use the local authentication server as a multi factor Authenticator?
I want to start using wireguard to stream PCoIP media streams over the WAN, but some of the big clients require two factor authentication.
Currently we are using OpenVPN (SSL+user authentication) so the certificate key is stored on the Remote Desktop. Then the user has to also authenticate with the username and password which is stored on the pfsense local database.
With wireguard I see a noticeable improvement in Single threaded WAN speeds from 50-100Mbps with OpenVPN tunnels to 200+Mbps with Wireguard connections - default settings on both protocols.
The PCoIP protocol might work with openVPN but it states it needs 100Mbps per client. Sometimes my OpenVPN clients only get 60Mbps for some reason. So I really want to upgrade my VPN architecture to wireguard.
However I won’t be able to use wireguard with our current security policy unless we can somehow integrate a user based authentication on top of the key string. I’ve read that it is possible to integrate a TOTP Authenticator which if we have to, we could install on the end users phones, but would rather use the local database for ease of deployment.
So anyways, I really appreciate all the work you guys do for the open source community. I support netgate. We have many SG-3100s in service.
Thanks for reading!
-
Ascord, Fantastic job with this thank you !!!
But I have a few issues though.. i can get my device to handshake with the 'Netgate Wireguard'. but i'm unable to access any of my servers on the lan .. am i missing really obvious something ?
-
Hi all,
Good Job , thank you.
I have a question about the package if it's only works as client or can work as a server too? -
@moelharrak There is not much difference in server vs client configuration, so in general, yes, it works. Server just has the listen directive to know on that UDP port it can receive communication through firewall. Client has to know ip and port, where to connect in endpoint directive. The connection is then managed by wireguard automatically.
https://www.wireguard.com/quickstart/#nat-and-firewall-traversal-persistence
https://docs.sweeting.me/s/wireguard#How-WireGuard-Routes-Packets -
Anyone know if this wireguard setup keeps working after updating pfsence to 2.4.5_1?
Im currently on 2.4.5 and have no issues with wireguard. Just debating if i should update or not. Thanks. -
@alirz Hi, I'm using it without any kind of problem, since the release of 2.4.5-RELEASE-p1.
-
@dubatech thanks, do you think if I upgrade from 2.4.5 to 2.4.5-1, I will have to reinstall and re-configure the wireguard?
-
Greetings to all! And immediately I apologize for my English. Dear Ascrod, the wireguard service does not start if I specify several Allowed IPs in the peer settings. If one is Allowed IPs, then the service starts.
I'm using 2.4.5-RELEASE-p1 (amd64)
FreeBSD 11.3-STABLE