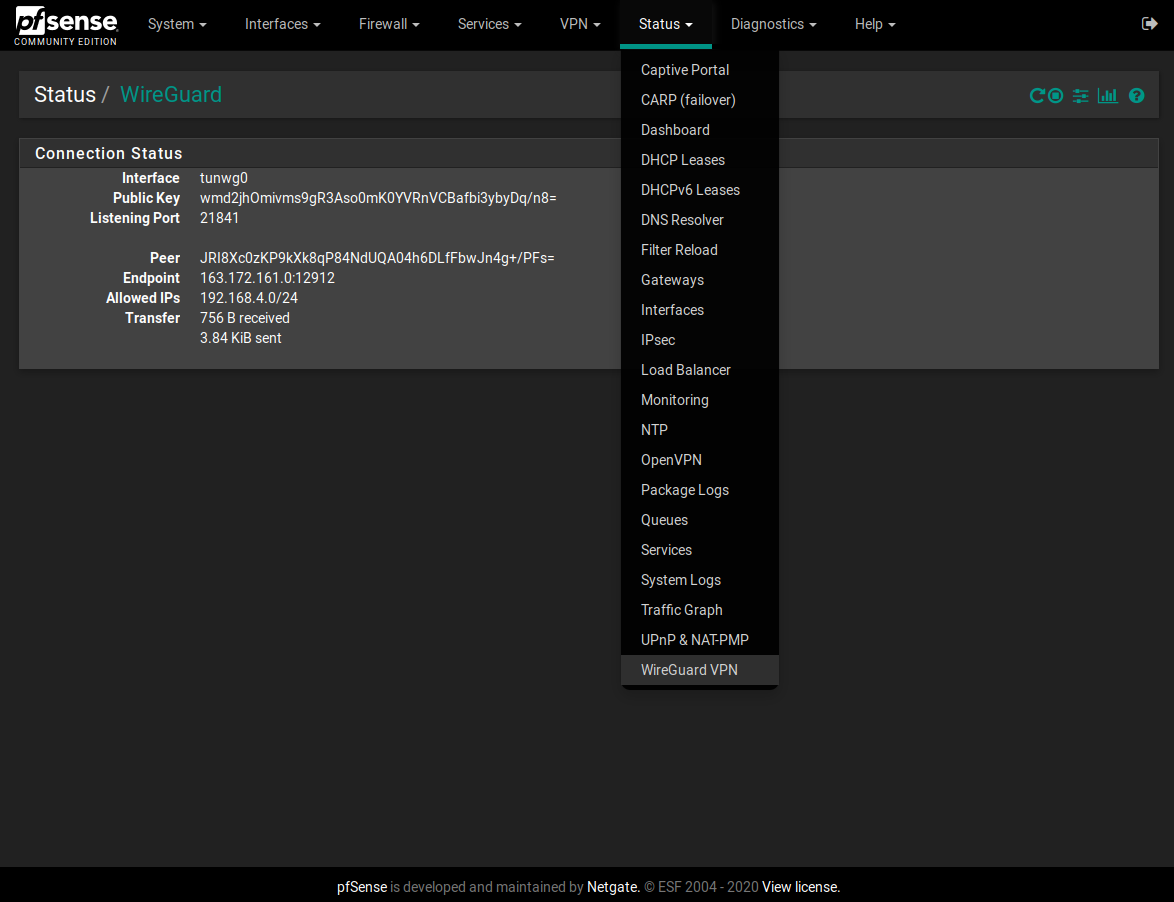
I made a WireGuard package for pfSense
-
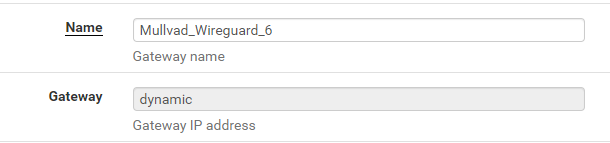
@dubatech But... Gateway IP is fixed as "dynamic" in the configuration?
I have tried using that IP in the NAT section, and I have set it as "static" IP on the actuall interface declaration. I just won't get it to work:(I tried a new public key upload now and are setting it up again...
-
@Talisker Create a new WG gateway and place that /32 ip on the gateway ip.
My config:
-
@dubatech I cant change "dynamic" as gateway. Do I have an old package, or do I have to go into the configuration file and do the change in text mode?
-
Ok, you have "Mullvad_Wireguard_6" gateway but create a new one with the same interface and then give a new name and place the ip.
I've pfSense 2.4.5 and I can do it without problem. -
@dubatech After manually setting the IP in the XML-file it started working. :)
Now It is no longer grayed out, so I can change it from the GUI as well.
Thanx!
-
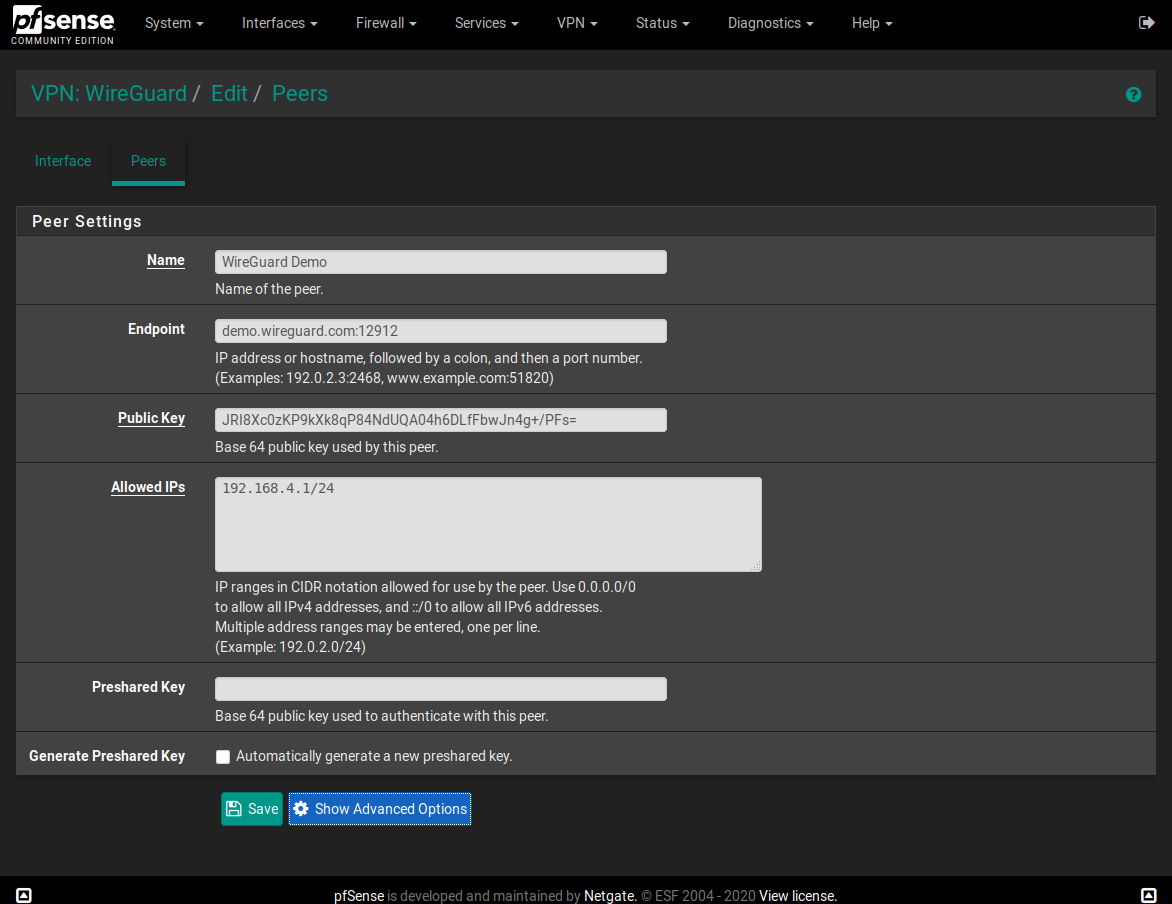
@Talisker Glad to hear that! On the Wireguard peer what "Allowed IP" did you set?
-
ok I have installed this package on a new pfSense 2.4.5-Release. With WG server setup on google cloud. So I made the connection and mostly things working fine, but I have weird problem, Youtube & Google don't work !!! I can't figure out why, most other websites / services working fine except few, but mainly youtube and google services. If anyone can help or share experience, I would really appreciate it. Thanks
-
I added support for more WireGuard tunnel interfaces to the package. Although they cannot be edited via GUI, they will persist across reboots and reload all at once if needed. In case anyone questioned why, there are some cases you need it, for example when used with multiple WANs to increase connectivity or reliability.
https://github.com/Ashus/pfSense-pkg-wireguard
-
@a-katib91 This problem is probably the same as I had.
You need to tune MTU and MSS on wireguard interface. My maximum values when big packets come through are: MTU 1420, MSS 1380.
Your DSL line might have different parameters. MSS is a bit of a hack modifying outgoing packets, but responded packets are then split at source speeding things up without the need to renegotiate. Both large IPv4 and IPv6 pinged packets come through OK. -
@Ashus Oh thank you very much. This definitely seems to be the problem. can you elaborate on how to adjust MSS ? I can adjust the MTU from the GUI of wireguard.
Edit: for information, I'm connected via PPPOE on vlan given by ISP. but I tired multiple MTU, and no results so far, can't get youtube to work. :/ is there any like tutorial or some kind of logic behind this ? Thanks
-
@Ashus also one more question, do I need to change anything on the WireGuard Server ? or just the Client (i.e. only MTU / MSS in the pfSense) ? Thanks and sorry for the many questions.
-
@Ashus
Dear Ashus,
Hello and I hope that you are well. I installed the package on pfsense 2.5.0 which you were kind enough to make available for us all. The error reads " wrong architecture " - and asks tells me that the package ( pfSense-pkg-wireguard-1.0.1.txz ) is for pfsense 2.4.5 which is based on FreeBsd 11 as you well know. My simple request is - can you and / or Ascrod make a package that will install for pfsense 2.5.0 which is as you know based on FreeBsd 12.
I tried to build my own package however there were bugs which caused the webgui to keeprepeatedly crashing. So, I hope that this is not too much of an ask.Peace and Stay Safe and Well
-
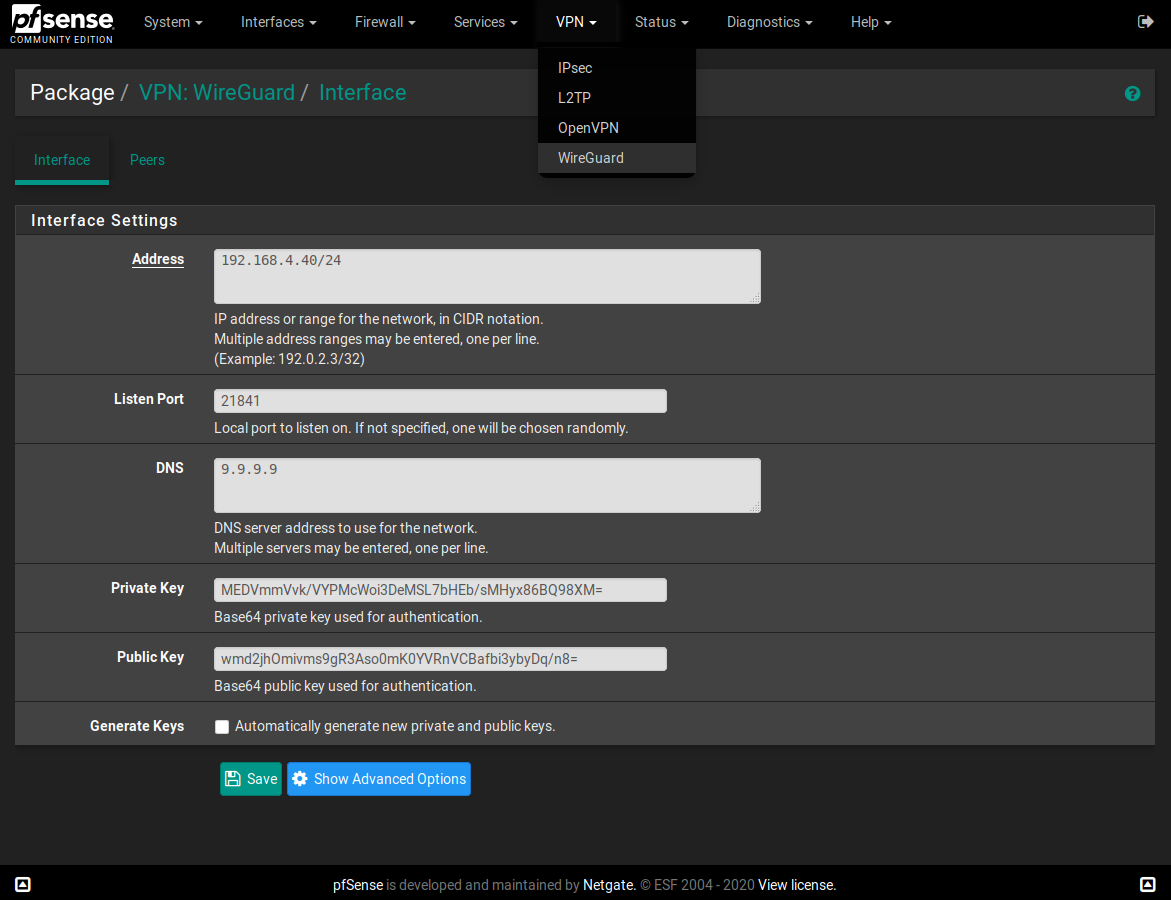
@a-katib91 You need to edit MTU and MSS values in interface config (pfSense menu - interfaces - wireguard), also the MTU should be defined in wireguard configuration (with the same value), this adjusts the interface setting when VPN is set up.
Also the MTU value should be equal to the remote server's MTU - just adjust it in the wireguard config there and reload configuration.
To find the maximum usable MTU, I recommend setting MTU high (1500) and pinging over the VPN with a large packet - see the syntax here: https://access.redhat.com/solutions/2440411 and go lower or higher until you find maximum, that works. Bear in mind, that the value you use in the command is actually ping's payload, the packet also needs its headers, so the ping's response might tell you the correct MTU value. Try both IPv4 and IPv6 as they have headers of different size.
MSS is then calculated just as MTU - 40. -
@ubernupe I will try to compile it for FreeBSD 12, so it's compatible with pfSense 2.5.0, but only for amd64 architecture. If you have another one, you will have to make it on your own, set up FreeBSD 12 in virtual machine and install and compile until you get a package. It's rather lengthy process.
Watch the assets in releases on github, i'll try to get it done today. Unfortunately I have no way of testing it easily, so your input would be helpful. -
@Ashus I can't thank you enough. <3 its working now finally, and speeds already better than openvpn. Awesome & thanks again.
-
@Ashus
Dear Ashus,
Thank you so very much for your swift reply - and again - I hope that you are safe and well. A package for pfSense 2.5.0 amd64 architecture is just what I am looking for, so this is perfect for me. I want to thank you for taking your time and dedication in developing this package and project for us all. My reason for asking for this on pfSense 2.5.0 is because openssl 1.1 is available on this version ( FreeBsd 12 ) - and I run DNS OVER TLS with Stubby. With pfSense 2.5.0 I can run all upstream recursive servers using tls v1.3. So - once again - thank you so very much for your assistance. I will be more than happy to test the package once you complete it. Naturally, I will post my results to you as requested.
Peace -
@dubatech I am using 0.0.0.0/0 as allowed IPs. I use Rules in order to prevent unwanted traffic to the tunnel.
I am not having lower latency and allthough it looks stable, it isn't really the performance boost I was hoping for.
I don't need the extra speed or lower latency, but I just had to implement it because it could be done... -
@Ashus said in I made a WireGuard package for pfSense:
@ubernupe I will try to compile it for FreeBSD 12, so it's compatible with pfSense 2.5.0, but only for amd64 architecture. If you have another one, you will have to make it on your own, set up FreeBSD 12 in virtual machine and install and compile until you get a package. It's rather lengthy process.
Watch the assets in releases on github, i'll try to get it done today. Unfortunately I have no way of testing it easily, so your input would be helpful.I've just installed your pkg for FreeBSD 12 and finally also pfSense 2.5 works with WireGuard.
While trying to install it there is only an alert regarding mismatch between pkg and running kernel version but it works!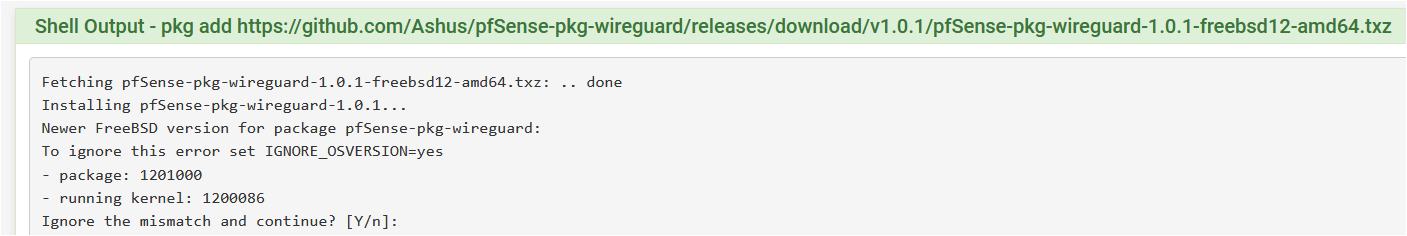
Thank you so much!
-
@Talisker said in I made a WireGuard package for pfSense:
@dubatech I am using 0.0.0.0/0 as allowed IPs. I use Rules in order to prevent unwanted traffic to the tunnel.
I am not having lower latency and allthough it looks stable, it isn't really the performance boost I was hoping for.

I don't need the extra speed or lower latency, but I just had to implement it because it could be done...As Ashus said, have you tried to set MTU and MSS on pfSense - Interfaces - tunwg0?
I've set the same MTU value under Package - VPN: WireGuard - Interface - Advanced Features - MTU and this fixed me some problems with some websites and also improve speed and low latency. -
@dubatech I have tried different things now and I seems to fail with most.
I first tried with adding a second interface, but I can't get my head around it. I am not that familiar with PFSense xml, but I think I would manage to configure the secondary wireguard interface. However, I don't understand how to do that and get it to show up as a tunwg1.I also tried changing TCP MSS and MTU, but when I do that I get the following error:
The following input errors were detected:
Cannot add IPv4 Gateway Address because no IPv4 address could be found on the interface.I can revert to an old configuration and get the wireguard up and running, but when I make changes the firewall doesn't accept saving because I set gateway address manually. If I have the gateway as dynamic I wont get the tunnel running.