IPSec (roadwarrior) + VLANs
-
I have a working IPSec configuration on my pfsense for several years now, and I can use it using my phone or laptop to connec to the home network from other places.
My internal LAN network is the 10.0.0.0/24 net, but recently, I've added 3 VLANs:
*** Welcome to pfSense 2.4.4-RELEASE-p3 (arm64) on aeon *** WAN (wan) -> mvneta0.4090 -> v4: 192.168.0.3/24 LAN (lan) -> mvneta0.4091 -> v4: 10.0.0.1/24 IOT (opt1) -> mvneta0.50 -> v4: 10.0.50.1/24 PRIV (opt2) -> mvneta0.60 -> v4: 10.0.60.1/24 GUEST (opt3) -> mvneta0.70 -> v4: 10.0.70.1/24Now, I can still connect to the IPSec VPN, however, it still lets me only access the LAN net, but none of the VLANs. I've tried googling for solutions, however I can't seem to find the obvious missing configuration which I have to add in order to make it work. When connected to the network directly w/o VPN (ethernet, wifi), I can access all of the VLANs without issues.
I tried adding another phase 2 entry wit the IOT net as local subnet, but it didn't help:

Also, there is no firewall rules on the IPSec interface which would prevent traffic to the IOT net:

What do I have to adjust in order to be able to access one of the VLANs from remote when using the IPSec VPN?
-
Hi soul710,
Did you manage to solve this? I'm trying to get an IPSec remote access VPN up that allows access to multiple VLANs as well.
I'm working from the following docs and forum howto:
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html
https://forum.netgate.com/topic/113227/ikev2-vpn-for-windows-10-and-osx-how-to
I've tried setting the local network to a specific VLAN and also to 0.0.0.0 for all traffic as a test (not what I want but tried it anyway).
The forum howto talks about setting routes on the client. I haven't done that yet as because a poster (@jimp ) said the instructions from the doc link were usually sufficient. That may be my missing link. I don't believe any traffic is actually going over my VPN even though the connection is showing as up.
If you got it working I'd greatly appreciate knowing how.
-
Unfortunately no, I have never managed to work this out. Let me know if you'll get any further :)
-
Try like this and manage access with rules on interface. It works for me.
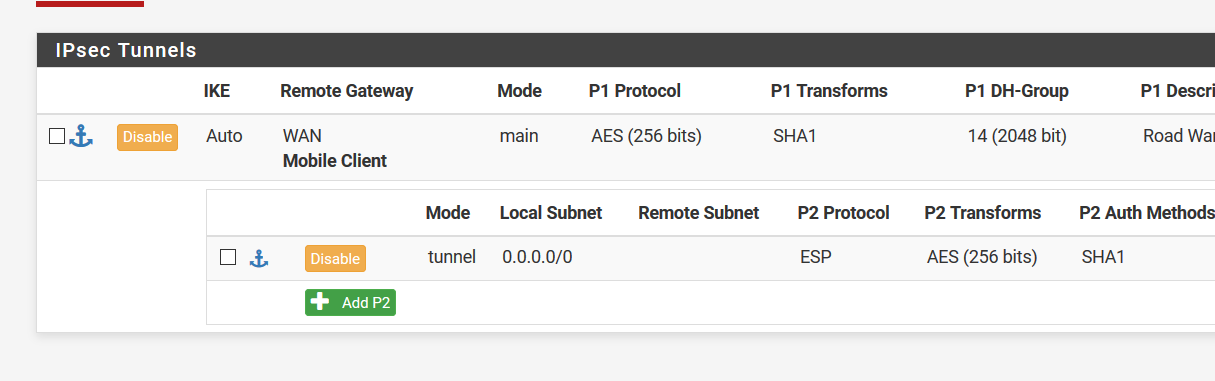
-
Thank you for your reply. I'm only just now having time to pick this back up.
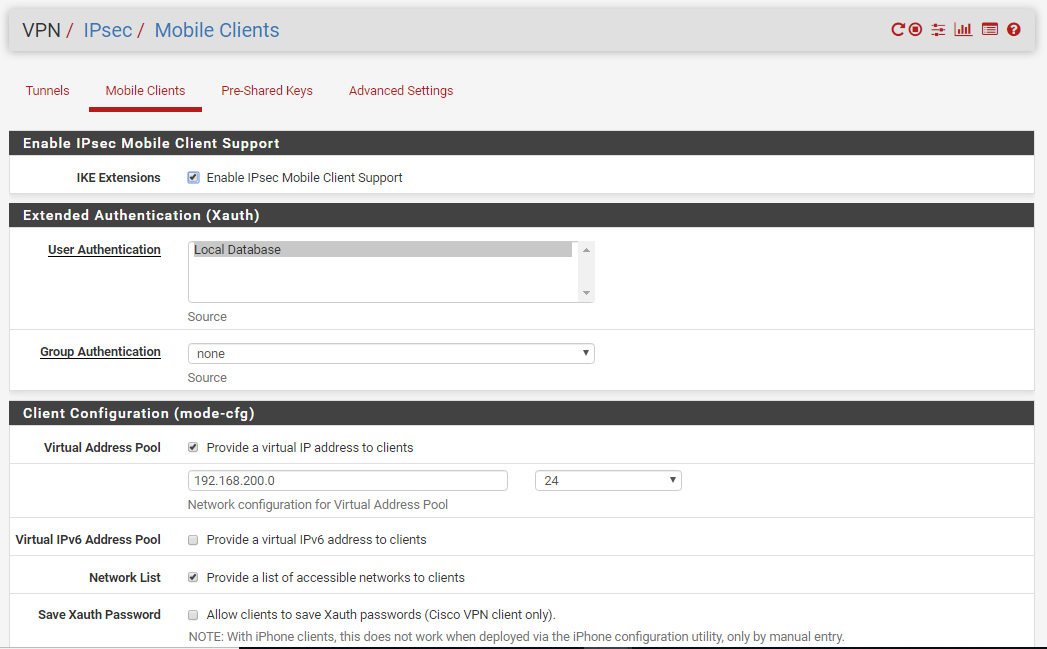
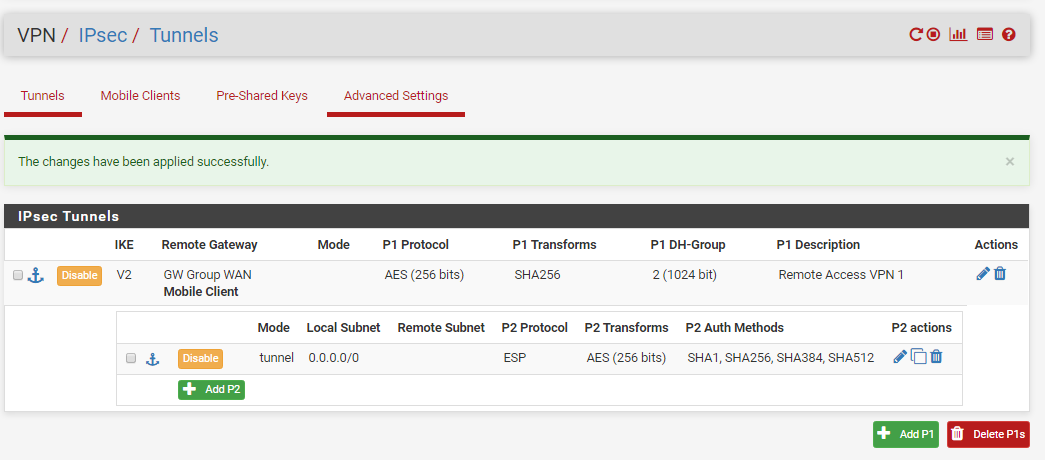
I adjusted the Phase 2 entries as suggested. I have not aligned all the other IpSec settings though as the VPN connects fine. If those other settings are a factor let me know and I'll change those too.
I have compared the output of the Windows command "route print" when connected to our existing VPN (Cisco VPN Client to Cisco ASA) to that I get when connected to our lab VPN (Windows Built-in VPN Client to Netgate XG7100).
Even with the suggested change no routes show up to any of the networks within the lab when connected to the lab VPN. See two attached files.
Am I still missing some basic piece of config that sets these routes? Or is my expectation that they should be there incorrect? My only VPN experience is with Cisco ASA and Cisco client. The routes are being sent to the client automatically in that case.
I don't even know where to start looking for issues. Is it my IpSec config that's wrong? Firewall rules? The IpSec set is set to allow any any. Do the rulesets for the VLANs also need checking? Its a lab so they're allow any any too at the moment.
Are there any logs that might help me figure this out? The IpSec logs show a successful connection, the states show a security association, etc, etc. I just cannot get anywhere with the routes.
Does it matter that that there is no LAN network itself (as nothing will ever be on it)? I've just set up VLANs as the intention is all devices will be in specific VLANs. The original poster had a network on LAN and VLANs on OPT1.
I'm just at a total loss here.
Any help from any quarter greatly appreciated.
Thanks.
Routes - Windows to Netgate Remote Access VPN.txt
Routes - Cisco VPN Client to Cisco ASA Remote Access VPN.txt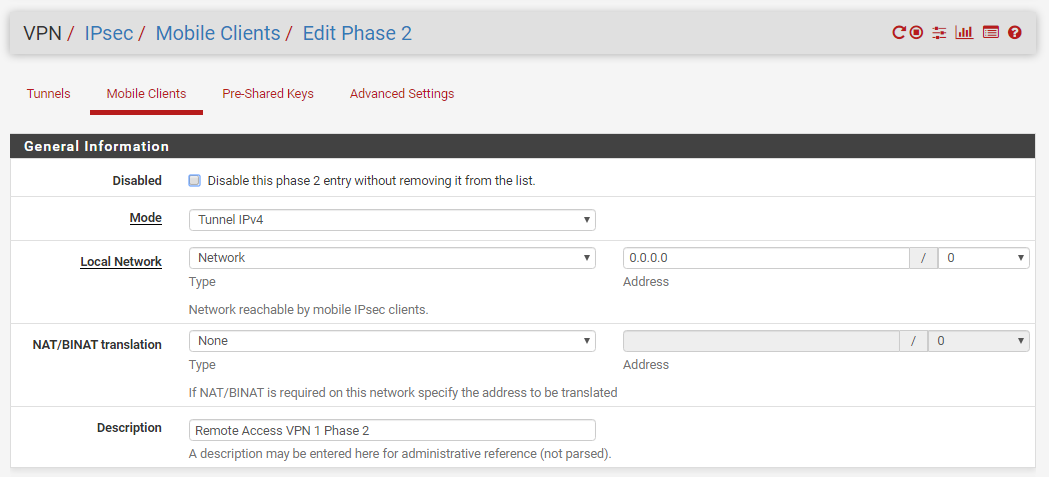
-
I'm just guessing here but, try with just one gateway instead of group.
-
Another thing... I use shrew soft VPN client on windows 7 to connect to this tunnel and I have to manually give it a route. It's by design. I've never tried a different approach
-
My issue was def that my expectation that routes be auto-populated is invalid. The Windows 10 client doesn't auto populate them.
Not sure if that was yours too...? Running "route print" from command prompt or powershell when connected showed no routes to any of my segments (not just the VLAN segments) which was why I couldn't get to anything.
I found another forum post that confirmed it here.
QUOTE
Windows 10 has split tunneling enabled by default, but with the same limitations seen since Windows 7, i.e. the virtual IP has to be
from the remote subnet, or routes have to be added manually, for instance, via Add-VpnConnectionRoute PowerShell command.UNQUOTE
I struggled to get my head around that at first because I've only ever worked with the old Cisco VPN client and the routes were sorted automatically. I hate that I have to manage these on clients as every time we change our segments I'm going to have push out updated group policy. But management don't want users having to use 3rd party clients so that's that.
It was the lack of static routes. It did say in the guide to do static routes. I was just slow on the uptake, didn't get that it was a requirement to get to any other segment and assumed I'd set it up wrong in pfsense.
Interesting that it's not just the Windows client that requires static routes. I've only ever worked with the old Cisco client which does not. It just seems mad to me.
Another piece of info the end user has to know about when all they want to do is connect. It's OK in our case as we can shove it out via group policy (I hope).Thanks given here because it was your thread and response that confirmed the situation with the Windows client.
POWERSHELL
Add-VpnConnection -Name "WindowsClientVpn_Test" -ServerAddress xxxxxx -TunnelType "Ikev2" -PassThru Set-VPNConnection -Name "WindowsClientVpn_Test" -SplitTunneling $True -AuthenticationMethod "Eap" -EncryptionLevel "Required" -PassThru Add-VpnConnectionRoute -ConnectionName "WindowsClientVpn_Test" -DestinationPrefix "192.168.30.0/24" -PassThru Add-VpnConnectionRoute -ConnectionName "WindowsClientVpn_Test" -DestinationPrefix "192.168.100.0/24" -PassThru Add-VpnConnectionRoute -ConnectionName "WindowsClientVpn_Test" -DestinationPrefix "192.168.110.0/24" -PassThru Add-VpnConnectionRoute -ConnectionName "WindowsClientVpn_Test" -DestinationPrefix "192.168.120.0/24" -PassThru ETC -
@jklmn12345 said in IPSec (roadwarrior) + VLANs:
My issue was def that my expectation that routes be auto-populated is invalid. The Windows 10 client doesn't auto populate them.
Not sure if that was yours too...? Running "route print" from command prompt or powershell when connected showed no routes to any of my segments (not just the VLAN segments) which was why I couldn't get to anything.
I found another forum post that confirmed it here.
Okay so I didn't try any other solutions until today when I wanted to try the proposed solution of setting 0.0.0.0/0 in the phase 2 entry. However I found that the VPN for whatever reason is not connecting anymore at all (without any changes from my side), so I would have to get that out of the way first, where I am currently lacking time to do so.
Also, I am not using windows. My client is my iPhone, and also a MacBook, however so far I've only tested with the iPhone. Once it works, the MacBook should work too.
-
I'm doing some more work on this today and was going through all the docs again.
I found this doc link that says Phase 2 is used to publish multiple segments. It seems to be talking about site-to-site VPNs (Site A, Site B).
So now I'm back to scratching my head over what is the correct way for a remote access VPN:
0.0.0.0/0 or multiple Phase 2?
Is the remote network information only used by clients for auto-route population (for clients that do auto-route population)?
Or is is used some other way as well?
Why would you choose one way over the other?
And how does the checkbox "Provide a list of available networks?" fit in with it all?
If I switch to multiple phase 2 entries and expose only a couple of segments, will that mean the others are unreachable even if I create a route on the client?
I'm going to do an experiment this morning to try and find out what happens but if anyone can explain a bit about how the Phase 2 remote network info is used it would be a great help.
-
How I've set mine up, I've got a single phase 2 setup with the local network of 10.0.0.0/16 as I have VLANs with IP ranges 10.0.100.0/24, 10.0.200/24, 10.0.201.0/24, 10.0.202.0/24. I haven't got the "provide list of accessible networks" checked. I have allow rules for it to access my LAN subnets in the IPSec firewall rules.
My client is windows and I can see that the 10.0.0.0/16 is showing up in my routing table as the second entry marked as on-link, all VLANs are accessible.
Without seeing the routing table from your computer it's a bit hard to tell what it is trying to do.