Is this possible? 1 Internet connection, 2 networks, 2 gateways (default and VPN)
-
To be clear, I've been reading a LOT of posts that I thought would have the answer, but somewhere along the line, it's never quite what I need, so I'll explain as best as I can.
I have 1 internet connection, we will call WAN. This is the default gateway called GW1.
I have 1 network we will call LAN (10.0.0.0/24)
I have 1 network we will call SEC (192.168.0.0/24)
And the twist, I have 1 VPN Client acting as a gateway called GW2.The goals, however simple in my mind, is to have:
1: LAN use GW1 for all things internet.
2: SEC use GW2 for all things internet.
3: allow LAN and SEC to communicate with eachother.For whatever reason, I have not been able to get this to work. I've completely blown my Pfsense to bits three times forcing me to completely rebuild it once before I wised up and saved a known good backup with just goal 1 in place, however I had both 1 and 3 working at some point, I have not gotten back to there yet.
Any help anyone can lend on getting all three would be greatly appreciated.
-
Hi
this is what I'm using at home (in fact, points 1. + 2. and only point 3. partially, I want network connections to be initiated by my "trusted" LAN only). I'll post screenshots later today.
-
You say 2 gateways. What are they connected to? If the ISP, you'll need one that provides 2 addresses (mine does). As for connecting from one LAN to the other, that should be doable, as it's just plain routing over the Internet. In fact, I do that here when I use the 2nd IP for testing. In this case the 2 gateways are no different than 2 customers.
-
To me it sounds rather simple with IPv4, it is just a normal setup with a VPN-Client on pfSense and some easy policy routing.
Just "copy" the Default allow LAN to any rule to "SEC" if it not already exist there and then change the gateway under advanced to the VPN-Client, done.
-
@Bob-Dig
Then again, if he has 2 pfSense systems, then just run an Ethernet connection between the 2. If it's on it's own interface, then you can use the firewall rules to control what's allowed.
A little more info on what he needs would be useful.
-
This post is deleted! -
@JKnott said in Is this possible? 1 Internet connection, 2 networks, 2 gateways (default and VPN):
@Bob-Dig
Then again, if he has 2 pfSense systems,
I don't think he has. He just has WAN and the "virtual" gateway which is the VPN-CLient.
-
@Bob-Dig
I don't see he mentioned virtual machines. As I said, we need more info. Otherwise we're just guessing and my crystal ball is busted.
-
@JKnott said in Is this possible? 1 Internet connection, 2 networks, 2 gateways (default and VPN):
@Bob-Dig
I don't see he mentioned virtual machines.
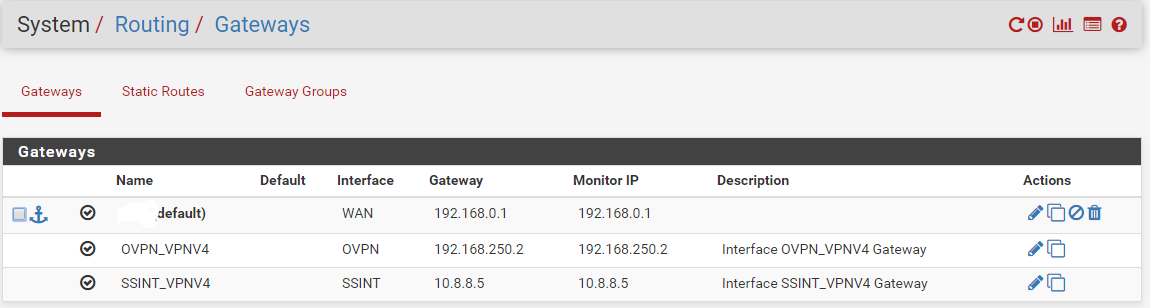
I didn't. I bet he just meant Gateways in the Sense what is showing under: System Routing Gateways
One box, WAN and the VPN Client as the two gateways (exits). -
@Bob-Dig
I prefer not to assume. In that case, he'll need a virtual Ethernet cable.

-
Thank you all for your responses!
Let see if i can get to them all...
@JKnott , @Bob-Dig is correct. Only one Ethernet cable to the internet modem. The second "gateway" is a virtual gateway created by the VPNClient.
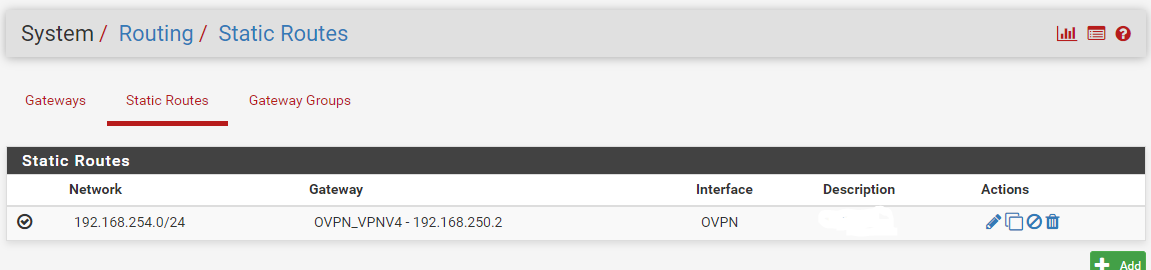
I have tried to setup firewall rules in the SEC interface with source SEC/any destination any/any use VPN gateway (GW2) but alas, this seems to fail the test when i connect to that network and tracert, I see my traffic goes over the default GW1 instead.
As for "machines" on that network, most are VMs and or Dockers. Only one physical device that I have connected becides the PFsense machine.
Long and short of it, I want my VMs and Dockers on the SEC network to route all traffic to the VPN tunnel. The main network uses manages inbound SSL traffic as well as other internal outbound traffic.
-
@Bob-Dig said in Is this possible? 1 Internet connection, 2 networks, 2 gateways (default and VPN):
Just "copy" the Default allow LAN to any rule to "SEC" if it not already exist there and then change the gateway under advanced to the VPN-Client, done.
This is everything you need to do, if the vpn-Client was setup correctly in the first place.
If it was not or is not connected, then traffic would go automatically out to WAN. For this to stop you have to tag that traffic and then block it with a special floating-rule.
-
@Bob-Dig said in Is this possible? 1 Internet connection, 2 networks, 2 gateways (default and VPN):
If it was not or is not connected, then traffic would go automatically out to WAN. For this to stop you have to tag that traffic and then block it with a special floating-rule.
Sorry, if im kinda newbish, but how would i go about this?
-
@rottonpeech said in Is this possible? 1 Internet connection, 2 networks, 2 gateways (default and VPN):
Sorry, if im kinda newbish, but how would i go about this?
You won't. You would first setup a working VPN-Client.
-
yes. i figured out what you meant, and i also found a few other things that did some magic (like not making a change, but re-saving and committing all my interfaces)
Now I see that all the interfaces are up, and the Client is up... but still cannot route across the VPN client.
Here is a pic if it helps at all
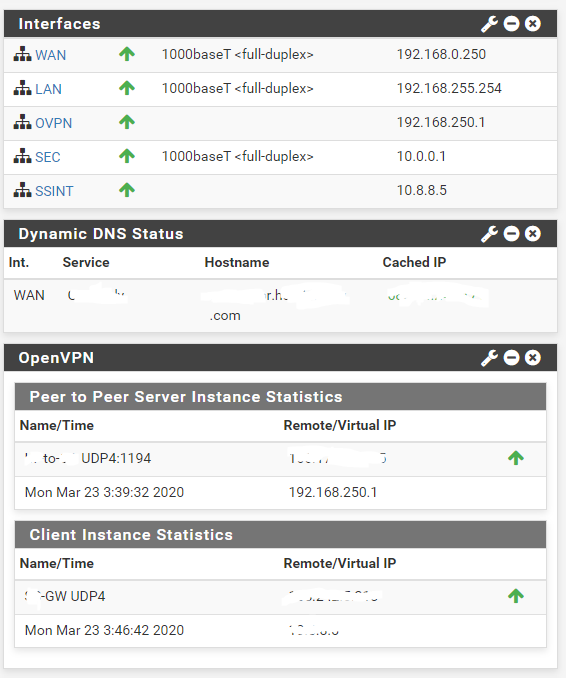
P.S. i also have a open VPN site-to-site that is working, where i am hosting the server side. 
-
Please show what you got under
FirewallNATOutboundMaybe you should do a much simpler setup in the beginning for testing with WAN, LAN, VPN-Client only.
-
here are a few other screens
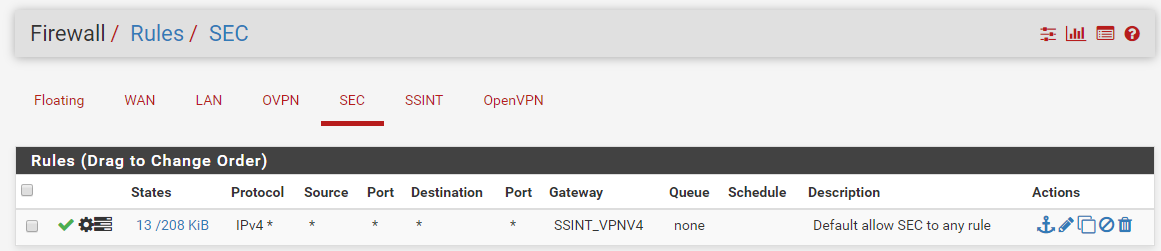
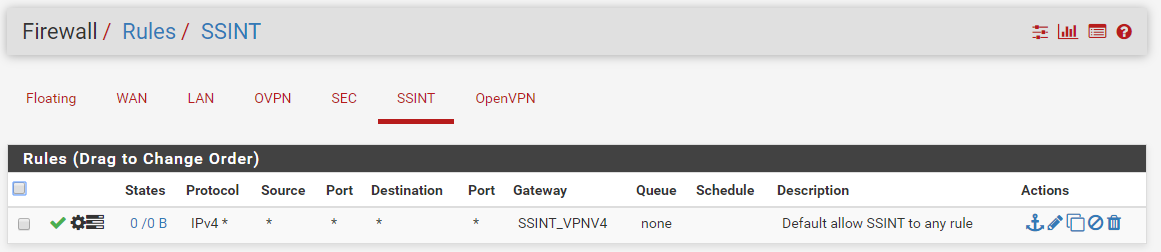
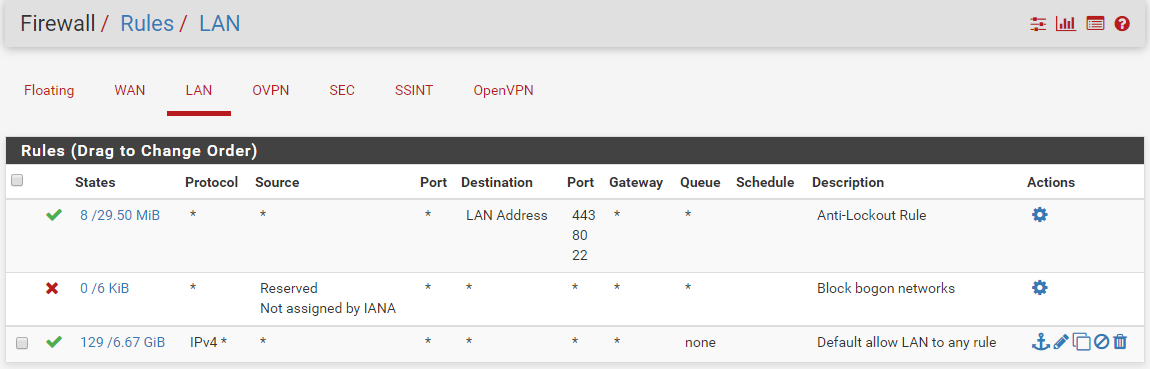
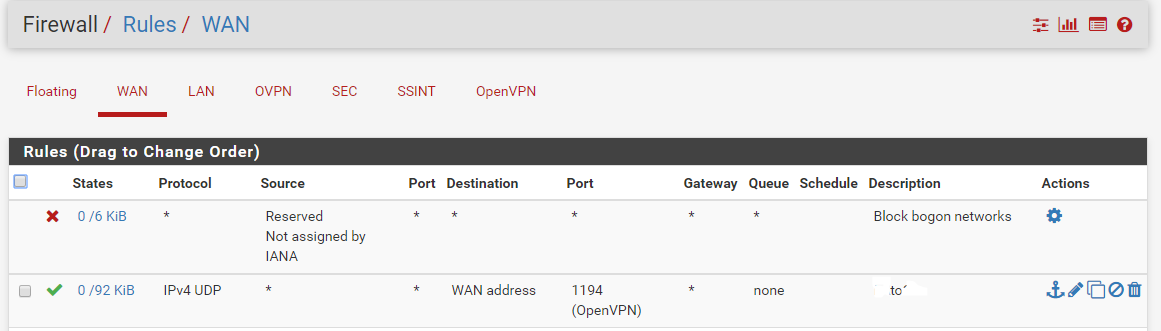
-
@rottonpeech Firewall NATO utbound still missing.
-
missed a few
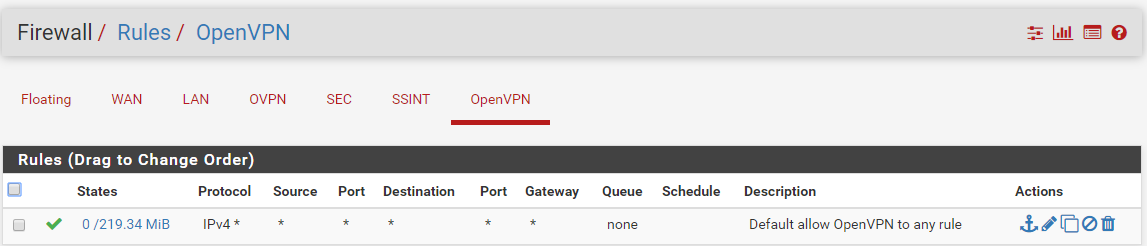
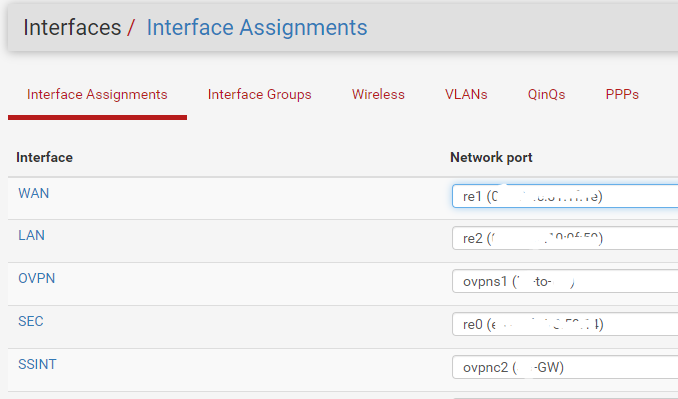
ok, i think thats about all of them
-
@Bob-Dig - Sorry, here it is