Segmenting local network clients - where to begin?
-
I would like to isolate one client on my local network from all of the other clients, but still allow them to all share the internet connection.
Currently I am running pfSense on a SuperMicro C2758, which has 4 ethernet ports.
One ethernet port is being used for WAN - connected to my cable modem.
Another ethernet port is connected to an unmanaged switch that connects my local devices.
The remaining two ethernet ports are currently unused.The one client I would like to isolate is a desktop PC.
What are the recommended/typical setup(s) to accomplish this?
-
If it’s only 1 computer, and you’ve got extra network ports on the pfsense box, and this computer doesn’t need to talk to the other machines on LAN, simply light up one of the extra NICs on the pfsense box and call it a day. You need to make a firewall rule on that particular network to only allow internet access. It’s pretty easy.
Jeff
-
@akuma1x Thank you for taking the time to read and reply! Would you kindly point me in the right direction for creating the rule?
When I turn on one of the additional ethernet ports pfSense automatically creates OPT2. How should 'OPT2' be configured in this case?
-
Perhaps you could create a Static Mapping on their Mac address and
create a firewall rule according to their IP address. This could filter their access rights within that interface -
@Gil said in Segmenting local network clients - where to begin?:
Perhaps you could create a Static Mapping on their Mac address and
create a firewall rule according to their IP address. This could filter their access rights within that interfaceWhen you activate a NIC as a useable interface, pfSense will baptise it OPTx. You can, if you which, rename it.
Let's assume that you have a LAN interface with the default setup : a static IP 192.168.1.1 mask /24. "IPv4 Upstream gateway" is (must be) set to "None". No other checks, no IPv6 stuff.
The the classic default settings.Visit Interfaces, and select OPtx, your new interface.
Check "Enable interface", Set "Static IPv4", don't bother with IPv6 related stuff (IPv6 Configuration Type set to None) and set "IPv4 Address" to 192.168.2.1 net mask to /24.
MTU / MSS = empty and Speed and Duplex to default.
IPv4 Upstream gateway to None.
Your done.
Hit Save and after that Apply.Now visit Services > DHCP Server. You will see that you have now two pages, a LAN and a OPTx.
Go to the OPTx page.
Only the "General Options" parts needs some setup.
Like this :
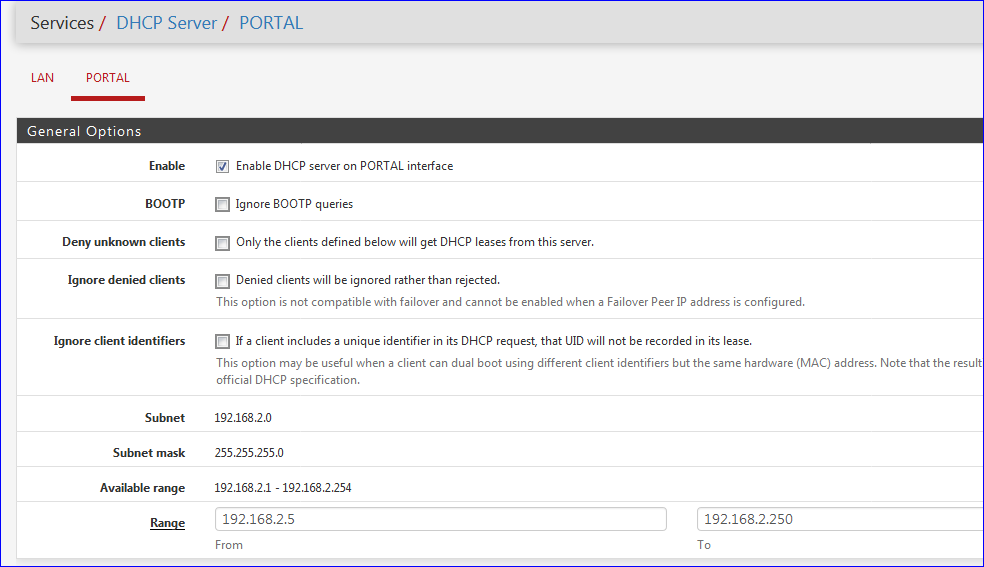
(note my OPTx interface is called PORTAL, I renamed it)
Hit Save at the bottom of the page after that Apply.
Now, you can hookup a PC to the OPTx NIC.
The PC (any device=) should obtain an 4 things at least : IP, the netmask - a gateway - a DNS.
Check these four !!!!!
It's a Windows device ? Ok, goto 'cmd' and typeipconfig /allThe IP should be somewhere in pool of the DHCP server range, thus between 192.168.2.5 and 192.168.2.54.
The DNS should be 192.168.2.1 - the gateway also, 192.168.2.1.On pfSense : Visit Status > DHCP Leases and find a line that has the IP of your device, hooked up to the OPTx interface. It will be a 192.168.2.x IP.
If so, DHCP is all ok.No Internet connection yet, because the firewall for the OPtx has to be set.
Visit Firewall > Rules and select the OPTx page, next to LAN.
You will notice that there are NO rules at all. That's normal.
Add one rule :
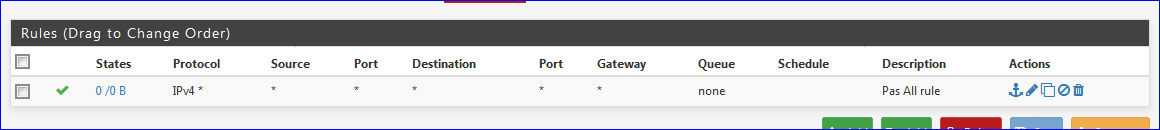
save and after that : Apply.
Get back to the PC, and you'll see you have Internet access.
Left to be done : use firewall rules to forbid access to
LAN
Probably pfSense (GUI, SSH etc) itself. -
@Gil said in Segmenting local network clients - where to begin?:
Perhaps you could create a Static Mapping on their Mac address and
create a firewall rule according to their IP address. This could filter their access rights within that interfaceThat wouldn't limit access on the LAN. They could still reach others. There is nothing that can be done on a firewall or router that would do that, short of giving it an address that's outside of the subnet and I don't know that pfSense can do that.
-
@cobrahead said in Segmenting local network clients - where to begin?:
How should 'OPT2' be configured in this case?
You would put an IP on it, with a mask for the size of network you want to create - /24 is quite common when using rfc1918 space since you have lots of IP ranges and space to work with... If your lan is say 192.168.1/24, then say use 192.168.2/24 on this opt network.
Turn on dhcp.. Then set your rules for what you want to allow or block... If you want to prevent this network from talking to your lan network, then put a rule there that blocks access to lan net above your allow any rule (internet)..
-
@JKnott said in Segmenting local network clients - where to begin?:
@Gil said in Segmenting local network clients - where to begin?:
Perhaps you could create a Static Mapping on their Mac address and
create a firewall rule according to their IP address. This could filter their access rights within that interfaceThat wouldn't limit access on the LAN. They could still reach others. There is nothing that can be done on a firewall or router that would do that, short of giving it an address that's outside of the subnet and I don't know that pfSense can do that.
The only thing that would fix the above is switch that supports Private VLAN Edge / Protected ports:-
Protected Ports provide Layer 2 isolation between interfaces (Ethernet ports and LAGs) that share the same VLAN.
Packets received from protected ports can be forwarded only to unprotected egress ports. Protected port filtering rules are also applied to packets that are forwarded by software, such as snooping applications.
Port protection is not subject to VLAN membership. Devices connected to protected ports are not allowed to communicate with each other, even if they are members of the same VLAN.
-
@Gertjan Wow, your instructions are very thorough! I did everything you laid out here with one exception. My LAN is setup on 172.16.0.1/24 so I am using 172.16.1.1/24 instead of 192.168.1.1/24, but otherwise everything is the same. The client machine is connected and has grabbed address 172.16.1.5, DNS and gateway both show 172.16.1.1, subnet shows 255.255.255.0 ... no internet access yet. Then I create the rule on OPT2 as you showed. Unfortunately there is still no internet access.
EDIT: Found my problem. I have some specific manual NAT rules setup for a VPN. When I switched from Manual to Hybrid rules it added two automatic rules to the bottom of the list, and that fixed the issue of not being able to reach the WAN from OPT2. Now I will study up on the rules to block traffic between 172.16.0.x and 172.16.1.x
-
@cobrahead said in Segmenting local network clients - where to begin?:
Now I will study up on the rules to block traffic between 172.16.0.x and 172.16.1.x
That's really easy. Add a new rule on the OPT2 interface, move it to the very top of the list, and make it read like this::
Action: Reject or Block (either one will work)
Interface: OPT2
Address Family: IPv4
Protocol: anySource: OPT2 Net
Destination: LAN Net
Description: lan blocker (or something similar)Click the SAVE button.
Jeff
-
@cobrahead Awesome! Got it, I added one more above that one to allow access from OPT2 to one address on the LAN, for the printer, and it works like a charm! I appreciate your help.
How much more involved are vlans to configure?