Cannot access all ip's accross different subnets
-
Hi,
I have pfsense running as a VM on an unraid server
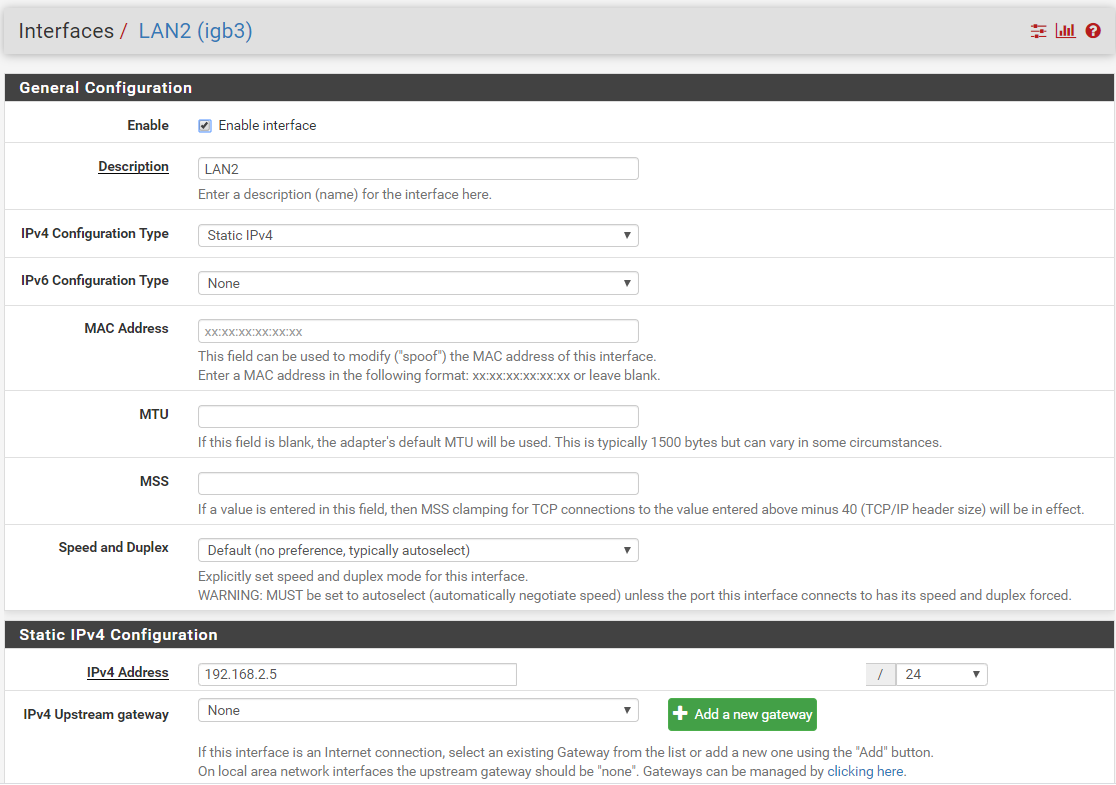
I have a 4 port nic with the following interfaces.
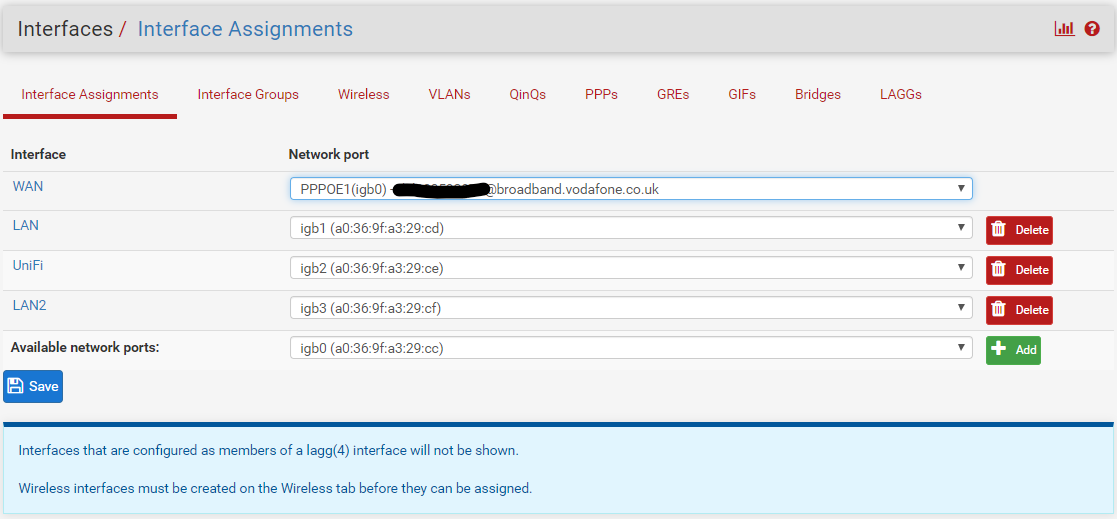
I can ping anything from LAN to UniFi and vica versa but am not able to access some addresses on LAN2For example if I ping 192.168.2.55 from a VM on LAN2 I get a response and can access the device but if I repeat from LAN or UniFi I cannot reach it.
But if I ping another device 192.168.2.57 from LAN or UniFi I can reach it without issue.
I have several devices I can reach and several I cannot
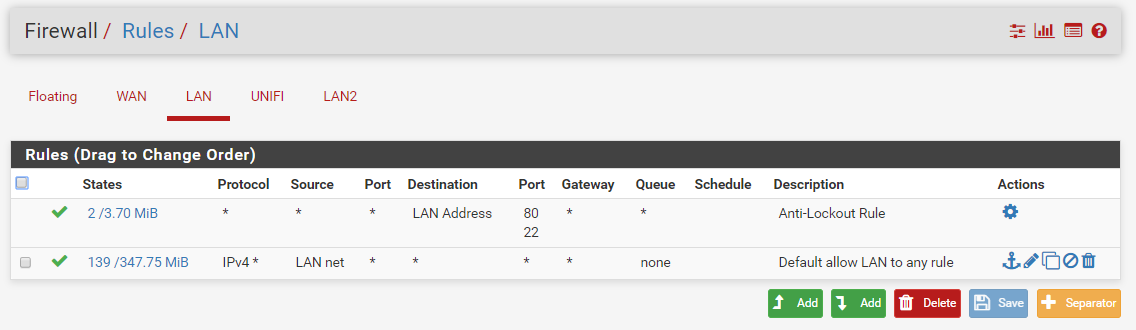
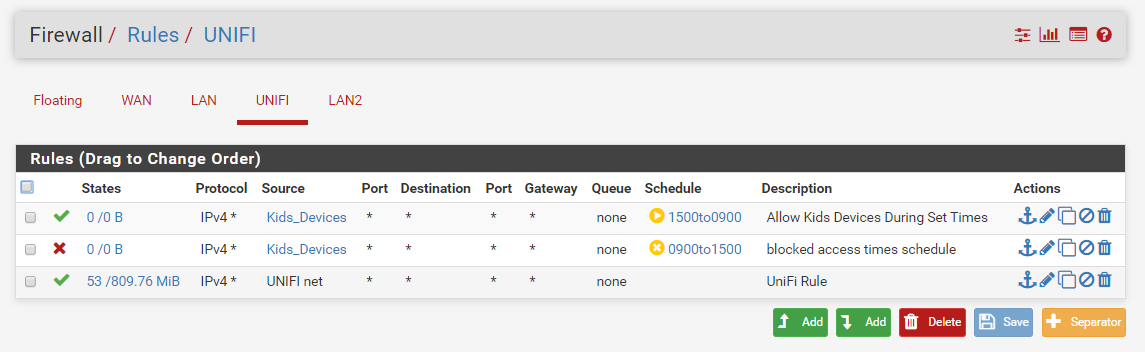
As far as I can tell my rules are correct so can anyone please help as to why this is happening?
Thank you


-
What device/OS is 192.168.2.55?
The Windows Firewall is blocking any incoming connection outside the local/known subnet.-Rico
-
Hi,
Many thanks for your reply, I should have mentioned I already disabled the windows firewall


-
Dude no shit you can ping from same network... This has nothing to do with pfsense, and most firewalls allow pinging from same network.
Here is the thing.. If you can ping some devices in this network, from lan.. Then its the device firewall or security software. or its using the wrong gateway, or has a bad mask?
So you want to ping device connected to different interface from lan... Ok sniff on pfsense interface in this other network, say your lan 2 interface while you ping from device in lan..
Do you see pfsense send the ping.. If so then NOT pfsense!!
-
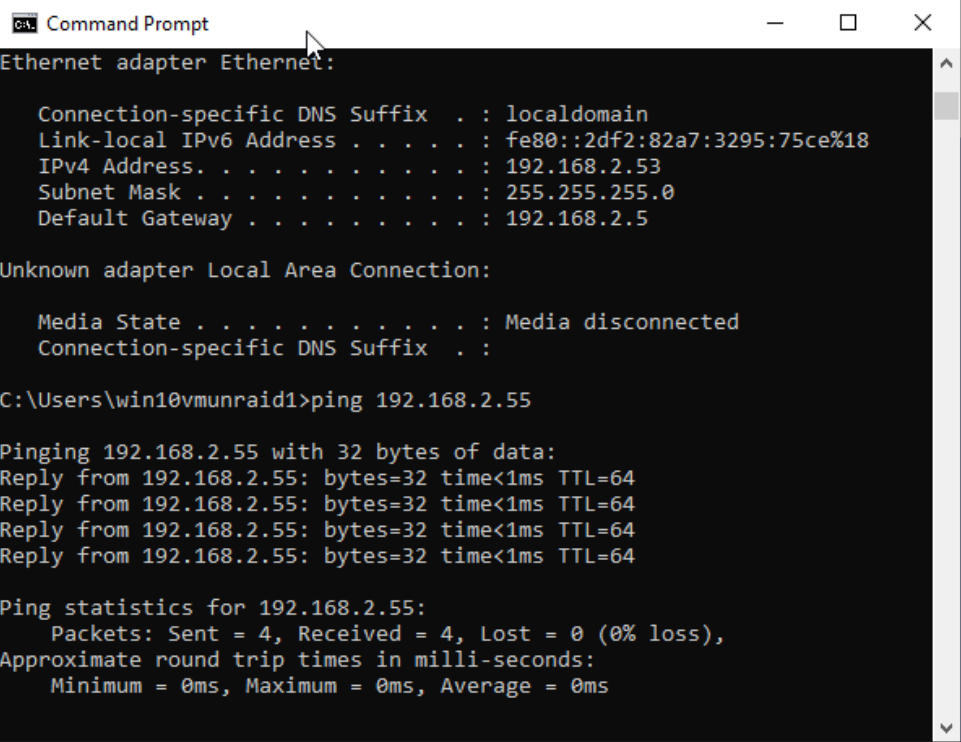
Obviously I can ping from the same network, this was just a screenshot to prove the device existed.
I started the packet capture on LAN2 interface (all protocols)
I then pinged 192.168.2.55 from 192.168.0.12 (Windows 10)
I tried to access 192.168.2.55 from 192.168.1.59 (Android Phone)
Here are the results with none of those IP's mentioned.
16:14:07.693246 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.693286 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.693612 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.693657 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.693696 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.693967 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1364
16:14:07.693979 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.693995 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.694016 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.694188 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.694228 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.694285 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.694463 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.694513 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.694533 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.694692 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1364
16:14:07.694732 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.694884 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.694895 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.694907 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.695178 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.695217 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.695289 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.695296 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.695305 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 824
16:14:07.695398 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.695463 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.701541 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 16
16:14:07.701551 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 1152
16:14:07.701572 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 296
16:14:07.701583 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 16
16:14:07.701593 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 156
16:14:07.701604 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 16
16:14:07.701614 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 252
16:14:07.702194 IP 192.168.2.53.59121 > 192.168.1.27.554: tcp 0
16:14:07.734057 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.734095 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.734168 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.734342 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.734534 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.734557 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1364
16:14:07.734650 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.734686 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.734731 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.734751 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.734932 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.734956 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.735104 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.735202 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.735291 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.735310 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.735489 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1364
16:14:07.735512 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.735674 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.735749 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.735872 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.735905 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.736063 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1108
16:14:07.736121 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.736157 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.775443 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 16
16:14:07.775468 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 256
16:14:07.776072 IP 192.168.2.53.59121 > 192.168.1.27.554: tcp 0
16:14:07.777087 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 16
16:14:07.777111 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 1152
16:14:07.777133 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 296
16:14:07.777154 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 16
16:14:07.777190 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 236
16:14:07.777227 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.777491 IP 192.168.2.53.59121 > 192.168.1.27.554: tcp 0
16:14:07.777527 IP 192.168.2.53.59121 > 192.168.1.27.554: tcp 0
16:14:07.813525 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 16
16:14:07.813550 IP 192.168.1.27.554 > 192.168.2.53.59121: tcp 248
16:14:07.814100 IP 192.168.2.53.59121 > 192.168.1.27.554: tcp 0
16:14:07.814906 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.814945 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.815146 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.815321 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.815350 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.815390 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.815607 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.815752 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1364
16:14:07.815790 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.815893 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.815994 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.816033 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.816117 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.816159 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.816459 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.816485 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.816530 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1364
16:14:07.816661 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.816731 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.816894 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.816931 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.817131 IP 192.168.2.53.59130 > 192.168.0.24.554: tcp 0
16:14:07.817251 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.817303 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1460
16:14:07.817420 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 1364
16:14:07.817478 IP 192.168.0.24.554 > 192.168.2.53.59130: tcp 396 -
Dude why would you do all when what your interested is in ping? And it defaults to only capturing 100 packets.. So no shit you prob finished your capture before you even ran your ping - so that is why don't see anything..
Look at your sniff, that is what 100 packets in less than 0.2 seconds.. Really dude come on!!!
Set the capture to be the dest IP your interested in, and just ICMP...
-
@johnpoz said in Cannot access all ip's accross different subnets:
Dude why would you do all when what your interested is in ping? And it defaults to only capturing 100 packets.. So no shit you prob finished your capture before you even ran your ping - so that is why don't see anything..
Look at your sniff, that is what 100 packets in less than 0.2 seconds.. Really dude come on!!!
Set the capture to be the dest IP your interested in, and just ICMP...Learning!

17:20:43.331497 IP 192.168.0.12 > 192.168.2.55: ICMP echo request, id 1, seq 3378, length 40
17:20:46.809362 IP 192.168.1.120 > 192.168.2.55: ICMP echo request, id 1, seq 22, length 40
so detected from both LAN & UniFi
Windows firewalls are off, Android does not have one, I know you said it is not pfsense so I have a challenge ahead!
Thanks for your help
-
@mbc0 said in Cannot access all ip's accross different subnets:
17:20:46.809362 IP 192.168.1.120 > 192.168.2.55: ICMP echo request, id 1, seq 22, length 40
So clearly pfsense sent this on to this 2.55 box!! So pfsense did everything it was told to do.. For some reason that did not come back..
Why are you seeing both 3 seconds apart? you did sniff on 2 different interfaces at the same time? You did 2 different sniffs which yeah that would make sense then. Or you don't actually have your interfaces isolated and your running multiple layer 3 on the same layer 2 network
-
I pinged from two addresses at the same time, that is why they are 3 seconds apart.
-
Ok - well clearly pfsense sent it on.. So as stated some time back its your machines firewall, or something between pfsense and this device. Or the device your pinging isn't using pfsense as gateway.
If you want to validate more, then sniff on the device.. To see if its seeing the ping.. If it is you know for fact its software on this machine preventing the ping from being seen/answered - ie firewall/security software.. Or your machine is sending its answer somewhere else, which you would see in the sniff.
Or it never gets there, so something between pfsense and the box is dropping pings?
Wireshark is free, and easy to use runs on pretty much any os...
-
I will download wireshark and see what I can find.
What I am really struggling to understand is from my main Windows Desktop PC (192.168.0.12) I cannot ping a Physical Machine 192.168.2.54 but can remote desktop in with no issues all? this makes zero sense to me.
the other devices are a mixture of dockers & vm's on my unraid server
some dockers I can ping and access, others I can not ping nor access. If I change them back to the 192.168.0 subnet they are all fine again. strange to me how I can access some but not others even though they are on the same subnet/network setting in unraid and are clearly visable from the physical machine on the same subnet
-
Well ping and rdp are different protocols - the host firewall could allow rdp and not allow ping (icmp). Or if a firewall rule with pfsense, you could be allowing just tcp or tcp/udp while ping icmp..