Suricata inline mode IPS and VLANS
-
@bmeeks It's more than ok, thanks
-
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks It's more than ok, thanks
Reading quickly through a few issues on that link I sent you indicates that in general, when you have VLANs with
netmap, you should runnetmapon the parent interface only. So translating that to pfSense would mean running Suricata on the parent interface and not each VLAN. However, that method might not fit into the scenario where you want different rules in place for each VLAN.VLANs can be good I guess, but the better solution is usually to have actual independent physical interfaces for each subnet. This would especially be true when you want to utilize an IPS with different rules for the different protected subnets.
-
@bmeeks said in Suricata inline mode IPS and VLANS:
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks It's more than ok, thanks
Reading quickly through a few issues on that link I sent you indicates that in general, when you have VLANs with
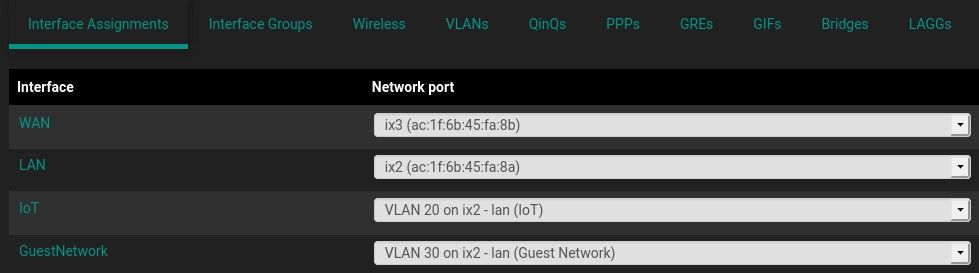
netmap, you should runnetmapon the parent interface only. So translating that to pfSense would mean running Suricata on the parent interface and not each VLAN. However, that method might not fit into the scenario where you want different rules in place for each VLAN.I only run Netmap on the parent interface, in my picture the parent interface is ix2 - LAN, which is not tagged. On VLANS I'm not running Netmap, VLANs where created for the IOT devices, and Guests devices.
I also did some reading and found this:
"if you are receiving VLAN-tagged packets, netmap applications (with patched drivers) may not see the VLAN tag because receive VLAN offloading is enabled (and so VLAN tags are stripped by the NIC). To disable it use
ethtool -K eth0 rxvlan off"
taken from here:
https://github.com/luigirizzo/netmap/blob/38cbc64d005029324cd63896fe9ad644d7d9d2bd/LINUX/README.mdbut I don't think it's that easy, and there is no ethtool on pfSense
-
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks said in Suricata inline mode IPS and VLANS:
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks It's more than ok, thanks
Reading quickly through a few issues on that link I sent you indicates that in general, when you have VLANs with
netmap, you should runnetmapon the parent interface only. So translating that to pfSense would mean running Suricata on the parent interface and not each VLAN. However, that method might not fit into the scenario where you want different rules in place for each VLAN.I only run Netmap on the parent interface, in my picture the parent interface is ix2 - LAN, which is not tagged. On VLANS I'm not running Netmap, VLANs where created for the IOT devices, and Guests devices.
I also did some reading and found this:
"if you are receiving VLAN-tagged packets, netmap applications (with patched drivers) may not see the VLAN tag because receive VLAN offloading is enabled (and so VLAN tags are stripped by the NIC). To disable it use
ethtool -K eth0 rxvlan off"
taken from here:
https://github.com/luigirizzo/netmap/blob/38cbc64d005029324cd63896fe9ad644d7d9d2bd/LINUX/README.mdbut I don't think it's that easy, and there is no ethtool on pfSense
I think I've also read that some NIC drivers won't honor that command because the feature is "enabled" inside firmware on the card and cannot be changed without reflashing the firmware.
-
@bmeeks said in Suricata inline mode IPS and VLANS:
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks said in Suricata inline mode IPS and VLANS:
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks It's more than ok, thanks
Reading quickly through a few issues on that link I sent you indicates that in general, when you have VLANs with
netmap, you should runnetmapon the parent interface only. So translating that to pfSense would mean running Suricata on the parent interface and not each VLAN. However, that method might not fit into the scenario where you want different rules in place for each VLAN.I only run Netmap on the parent interface, in my picture the parent interface is ix2 - LAN, which is not tagged. On VLANS I'm not running Netmap, VLANs where created for the IOT devices, and Guests devices.
I also did some reading and found this:
"if you are receiving VLAN-tagged packets, netmap applications (with patched drivers) may not see the VLAN tag because receive VLAN offloading is enabled (and so VLAN tags are stripped by the NIC). To disable it use
ethtool -K eth0 rxvlan off"
taken from here:
https://github.com/luigirizzo/netmap/blob/38cbc64d005029324cd63896fe9ad644d7d9d2bd/LINUX/README.mdbut I don't think it's that easy, and there is no ethtool on pfSense
I think I've also read that some NIC drivers won't honor that command because the feature is "enabled" inside firmware on the card and cannot be changed without reflashing the firmware.
How can I try to set that on pfSense, should I set something in bootloader.conf or it's another tool, to try it out ?
-
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks said in Suricata inline mode IPS and VLANS:
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks said in Suricata inline mode IPS and VLANS:
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks It's more than ok, thanks
Reading quickly through a few issues on that link I sent you indicates that in general, when you have VLANs with
netmap, you should runnetmapon the parent interface only. So translating that to pfSense would mean running Suricata on the parent interface and not each VLAN. However, that method might not fit into the scenario where you want different rules in place for each VLAN.I only run Netmap on the parent interface, in my picture the parent interface is ix2 - LAN, which is not tagged. On VLANS I'm not running Netmap, VLANs where created for the IOT devices, and Guests devices.
I also did some reading and found this:
"if you are receiving VLAN-tagged packets, netmap applications (with patched drivers) may not see the VLAN tag because receive VLAN offloading is enabled (and so VLAN tags are stripped by the NIC). To disable it use
ethtool -K eth0 rxvlan off"
taken from here:
https://github.com/luigirizzo/netmap/blob/38cbc64d005029324cd63896fe9ad644d7d9d2bd/LINUX/README.mdbut I don't think it's that easy, and there is no ethtool on pfSense
I think I've also read that some NIC drivers won't honor that command because the feature is "enabled" inside firmware on the card and cannot be changed without reflashing the firmware.
How can I try to set that on pfSense, should I set something in bootloader.conf or it's another tool, to try it out ?
Go have a look at this Sticky Post at the top of this forum: https://forum.netgate.com/topic/138613/configuring-pfsense-netmap-for-suricata-inline-ips-mode-on-em-igb-interfaces. You can do this on FreeBSD using the
ifconfigcommand in many cases. -
@bmeeks Thanks, I read that in the past, and I applied that info.
I only have the following:
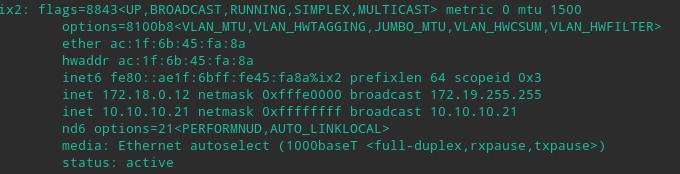
I don't know which should I disable further, if "rx_vlan" is off or not, from what I see
-
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks Thanks, I read that in the past, and I applied that info.
I only have the following:

I don't know which if "rx_vlan" is off or not, from what I see
I would lean towards VLAN_HWFILTER being a potential problem. But turning that off might break all of your VLAN routing.
You may have to think about abandoning Inline Mode if you have to use the VLANs. There are just too many issues with the
netmapdevice itself and VLANs. These issues are totally outside the realm of Suricata. All Suricata does is call an API function to open anetmapdevice tunnel on an interface.Oh, and that link I gave you to the Sticky Post was not about VLANs. It was just to illustrate use of the
ifconfigcommand. That user was working on some different issues and tuning around those problems. -
@bmeeks I will try to compose a mail to Luigi, before doing something to my pfSense. Maybe I get lucky and he will respond. VLANS I can't abandon, I need them, for the moment I disabled Suricata on LAN, and run it only on WAN, I don't have any other choice for now
Thanks again :) -
@bmeeks said in Suricata inline mode IPS and VLANS:
@NRgia said in Suricata inline mode IPS and VLANS:
@bmeeks Thanks, I read that in the past, and I applied that info.
I only have the following:

I don't know which if "rx_vlan" is off or not, from what I see
I would lean towards VLAN_HWFILTER being a potential problem. But turning that off might break all of your VLAN routing.
You may have to think about abandoning Inline Mode if you have to use the VLANs. There are just too many issues with the
netmapdevice itself and VLANs. These issues are totally outside the realm of Suricata. All Suricata does is call an API function to open anetmapdevice tunnel on an interface.Oh, and that link I gave you to the Sticky Post was not about VLANs. It was just to illustrate use of the
ifconfigcommand. That user was working on some different issues and tuning around those problems.Hello Bill,
I know it's an old post, but I wanted to tell you that you were partially right about my issue, which seems that hunts many people.
I found this bug:
https://github.com/luigirizzo/netmap/issues/703I did not understand if it's fixed or not, but I looked to this PR afterwards:
https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=236584
After I disabled the following:
ifconfig ix2 -vlanhwtso -vlanhwfilter -vlanhwtag -vlanhwcsumI can start Suricata in inline mode, on parent interface that have other VLANs.
I though it was ok to share, if this is not known already.
Tested on pfsense 2.5.0, but I don't think it matters. -
@NRgia said in Suricata inline mode IPS and VLANS:
https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=236584
After I disabled the following:
ifconfig ix2 -vlanhwtso -vlanhwfilter -vlanhwtag -vlanhwcsumI can start Suricata in inline mode, on parent interface that have other VLANs.
I though it was ok to share, if this is not known already.
Tested on pfsense 2.5.0, but I don't think it matters.I think this is a driver-specific issue. The em series driver appears to be the one not honoring the disable option. Other drivers do (like your ix series).
There are other features of FreeBSD networking that do not play well with the netmap device either. One of them is limiters (packet shaping). Several folks have reported that when that is enabled in pfSense (FreeBSD, actually), network traffic stops on the interface. Also have reports of the traffic graph function not working when netmap is running on an interface.