Routing over IPSec is not working fine.
-
Hello,
I have an issue with routing OpenVPN Client's over Site A through a IPSec tunnel to Site B.I already posted this issue on the facebook group and also check that with multiple pfsense admins - without success. Maybe I can find some help here.
My Network Subnets:
OpenVPN: 172.16.0.0/24
Site A: 10.0.0.0/16
Site B: 10.3.0.0/16
Office: 10.100.0.0/16In the first step we can ignore the issues with office. As a workakround, I added a second tunnel to Site B from office. The most important issue is the OpenVPN. I just make some input for office issue too, maybe it helps with debugging.
My Network:
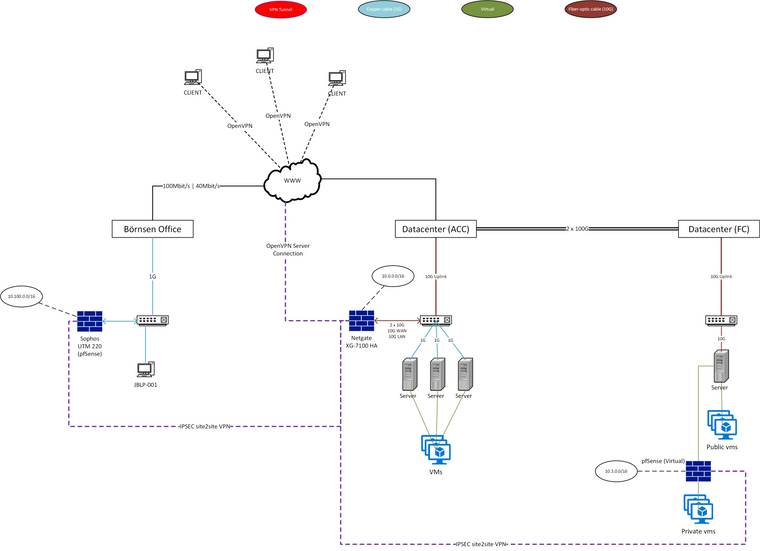
All internal Traffic should be sendet over the Site A - it's like the HQ.
My diagnostics:
 Site A can PING to Site B (IPSec)
Site A can PING to Site B (IPSec) Site B can PING to Site A (IPSec)
Site B can PING to Site A (IPSec) OpenVPN Clients can PING to Site A (OpenVPN)
OpenVPN Clients can PING to Site A (OpenVPN) Office can PING to Site A (IPSec)
Office can PING to Site A (IPSec) OpenVPN Clients can PING to Site B over IPSec from Site A (OpenVPN => IPSec)
OpenVPN Clients can PING to Site B over IPSec from Site A (OpenVPN => IPSec) Office can PING to Site B over IPSec from Site A (IPSec=> IPSec)
Office can PING to Site B over IPSec from Site A (IPSec=> IPSec)What I did:
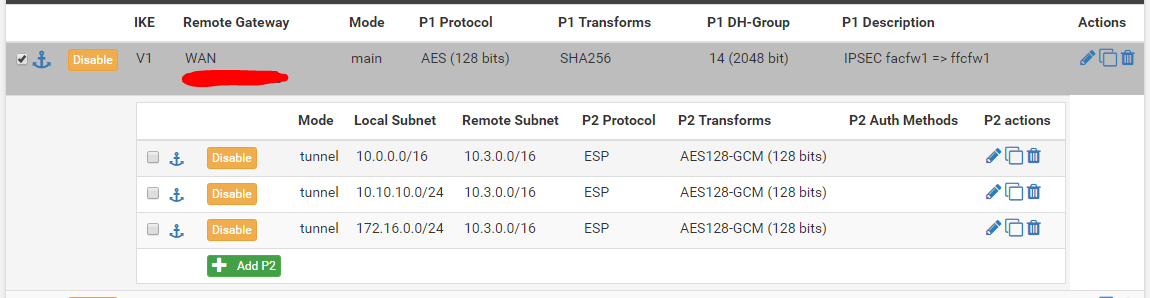
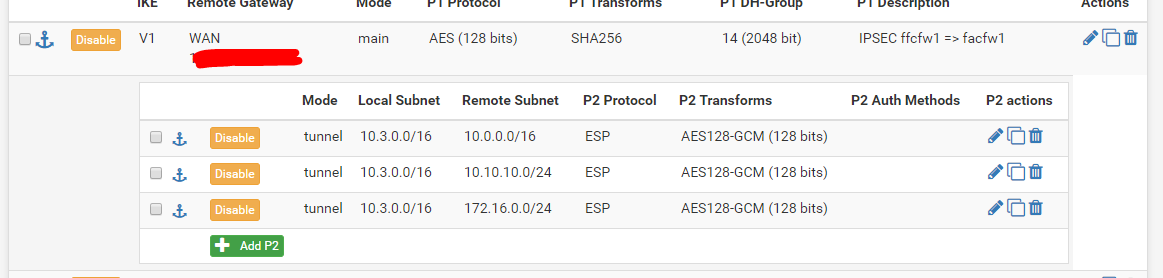
 I added a Phase 2 for 172.16.0.0/24 (local) to 10.3.0.0/16 (remote) on both sides. On Site B i changed the local and remote subnets.
I added a Phase 2 for 172.16.0.0/24 (local) to 10.3.0.0/16 (remote) on both sides. On Site B i changed the local and remote subnets.
 Also added a Phase 2 for 10.100.0.0/24 (local) to 10.3.0.0/16 (remote) on both sides. On Site B i changed the local and remote subnets.
Also added a Phase 2 for 10.100.0.0/24 (local) to 10.3.0.0/16 (remote) on both sides. On Site B i changed the local and remote subnets.
 I added the push route setting to OpenVPN Config: push "route 10.3.0.0 255.255.0.0";
I added the push route setting to OpenVPN Config: push "route 10.3.0.0 255.255.0.0";
 I added allow all on all sites for testing reason.
I added allow all on all sites for testing reason. Now I start ping from Client 172.16.0.10 to Site B pfSense: 10.3.0.1.
Now I start ping from Client 172.16.0.10 to Site B pfSense: 10.3.0.1.Failed.
On Site A I can see the "success-rule" in firewall logs.
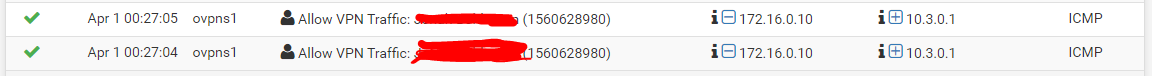
Also on Site A I also see the ICMP Packets with "Packet Capture" (Interface = OpenVPN):
00:28:35.565868 IP 172.16.0.10 > 10.3.0.1: ICMP echo request, id 10429, seq 1, length 64 00:28:36.575877 IP 172.16.0.10 > 10.3.0.1: ICMP echo request, id 10430, seq 1, length 64 00:28:37.565659 IP 172.16.0.10 > 10.3.0.1: ICMP echo request, id 10431, seq 1, length 64 On Site B I can't see any traffic. No Package Capture and no blocked rules. There is NOTHING.
On Site B I can't see any traffic. No Package Capture and no blocked rules. There is NOTHING. Based on my tests, I think that the traffic on Site A is not forwarded to IPSec Tunnel for Site B. Same with the second IPSec Tunnel from Office to Site A to route traffic to Site B.
Based on my tests, I think that the traffic on Site A is not forwarded to IPSec Tunnel for Site B. Same with the second IPSec Tunnel from Office to Site A to route traffic to Site B.Tracerote also ends on Site A.
On the IPSec Status I can see that the "172.16.0.0" Tunnel is not active.
IPSec Configuration
IPSec Config Site A:
IPSec Config Site B:
Any ideas how to Debug? What can be the issue? Any NAT fail? How can I check what happed to the accepted traffic from the openVPN clients?
Thanks!
