LAN and DMZ Interface
-
Hi, I am not really sure if it's the right practice to make DHCP Server enabled on both LAN and DMZ?
Scenario: My problem is, when I try to enable both dhcp server.. for example in my windows 10 machine it keeps grabbing IP from the DMZ. Even if I already blocked the MAC address and enabled "Deny unknown clients" in my DMZ Options.
Sometimes when I try to restart my Windows 10 machine or Restart the dhcp server of my pfsense it worked. But when I try to do an ipconfig /release and /renew commands in cmd, I always get the scenario I mentioned above.
-
Your different networks lan and dmz should be isolated layer 2 networks... I would not be possible for device on one network to get an IP from dhcp server on other network.
I am guessing you 2 different lan and dmz are plugged into some dumb switch? That is borked. if you want to run more than 1 network you either need to use different physical switches, or a vlan capable switch.
-
The machine for pfsense we use has 6 LAN ports, I have setup LAN and DMZ on different LAN Interface. This seems to be the setup I see most in tutorials online. GOAL: I want to have LAN access to DMZ, and then DMZ blocked access to LAN.
If I will be using a separate separate switch/VLAN switch, I wont achieved my goal right?
-
If you use different switches that are not connected together other than connection to interfaces on pfsense then you will be fine.
When you say 6 lan ports, this is discrete interfaces, and not some switch ports? They show up like igb0, igb1, igb2, etc..
-
@johnpoz Thank you for you response. Yes both LAN and DMZ cables are connected in one main switch only, a daisy chain network setup
-
@johnpoz yes they show up like igb0, igb1, igb2, igb3, igb4, igb5
-
@kirbyL said in LAN and DMZ Interface:
Yes both LAN and DMZ cables are connected in one main switch only
That doesn't work!!! You have connected your different layer 2 networks together...
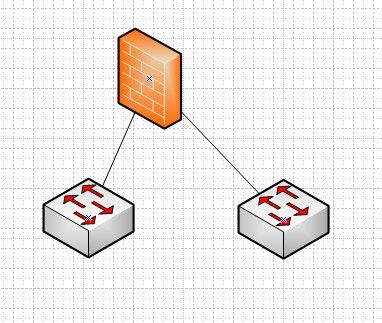
You need to do like above - or you need vlan capable switches
To do something like this
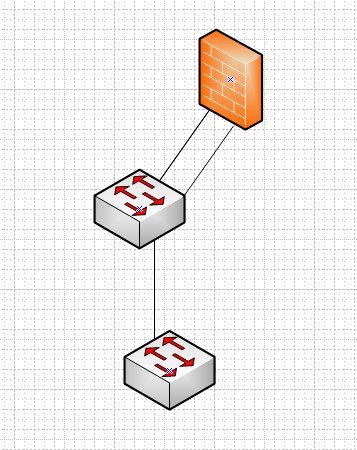
At min that switch connected to pfsense needs to understand vlans. And be configured to isolate the connections into different vlans.
What is the switch model(s) you are working with?
-
@johnpoz model is s1700-24gr
-
What is the model number?
BTW - have moved this into vlan section.
-
@kirbyL said in LAN and DMZ Interface:
s1700-24gr
Yeah that is just dumb switch, can not do vlans... You can not isolate network with those - they are only 1 network switches. If you want to do more than 1 network you need to connect them like my first pic
-
@johnpoz i have a VLAN switch model s5700s-28p-li-ac which is vlan capable. So if i connect my pfsense machine's LAN and DMZ on separate VLANs. It will look like this? (sorry for my drawing)
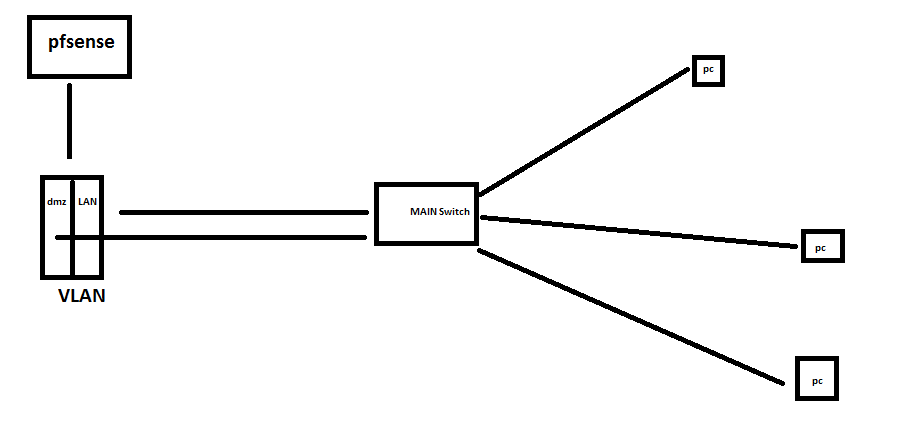
-
Your main switch needs to support vlans - if you want those pcs to be in different vlans.
That is great that the switch you connect to pfsense supports vlans.. But you can not connect both of those to a dumb switch and maintain isolation.
If you have a vlan capable switch, you can put dumb switch downstream of it, but each switch has to be its own vlan/network..
Once you have a dumb switch, its 1 network.. You can not run multiple networks on that switch with any isolation.. So you can do this..
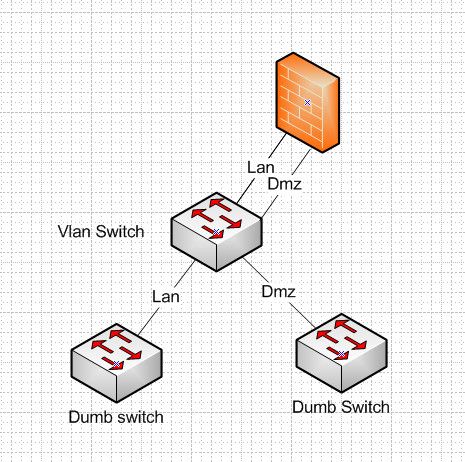
-
copy that.. thank you much for the insights.. for now I guess, I will have to disable DMZ dhcp server
-
See my edit posted above with a picture
btw - be clear just because you disable dmz dhcp server doesn't mean you can just run multiple L3 networks over the same L2 and expect any security or isolation. Just because you setup the IPs on the device static.. There is no security there if your switches are not actually isolating the L2 networks.
-
@johnpoz thank you so much for the layout, so if LAN needs to talk to DMZ, it will be configured in FW rules?
-
Yes once you have your networks properly isolated, then yes the only way for network X to talk to network Y would have to be allowed by firewall rules.
-
@johnpoz noted.. thank you so much..