AWS VPN NO_PROPOSAL_CHOSEN
-
Hello,
I'm trying to create a VPN on AWS. I created the tunnels with AWS VPC VPN Wizard but the tunnels aren't going up.
I received a NO_PROPOSAL_CHOSEN.Here is log:
Apr 5 17:28:07 charon 05[IKE] <con2000|25> activating ISAKMP_VENDOR task Apr 5 17:28:07 charon 05[IKE] activating ISAKMP_CERT_PRE task Apr 5 17:28:07 charon 05[IKE] <con2000|25> activating ISAKMP_CERT_PRE task Apr 5 17:28:07 charon 05[IKE] activating MAIN_MODE task Apr 5 17:28:07 charon 05[IKE] <con2000|25> activating MAIN_MODE task Apr 5 17:28:07 charon 05[IKE] activating ISAKMP_CERT_POST task Apr 5 17:28:07 charon 05[IKE] <con2000|25> activating ISAKMP_CERT_POST task Apr 5 17:28:07 charon 05[IKE] activating ISAKMP_NATD task Apr 5 17:28:07 charon 05[IKE] <con2000|25> activating ISAKMP_NATD task Apr 5 17:28:07 charon 05[IKE] sending XAuth vendor ID Apr 5 17:28:07 charon 05[IKE] <con2000|25> sending XAuth vendor ID Apr 5 17:28:07 charon 05[IKE] sending DPD vendor ID Apr 5 17:28:07 charon 05[IKE] <con2000|25> sending DPD vendor ID Apr 5 17:28:07 charon 05[IKE] sending FRAGMENTATION vendor ID Apr 5 17:28:07 charon 05[IKE] <con2000|25> sending FRAGMENTATION vendor ID Apr 5 17:28:07 charon 05[IKE] sending NAT-T (RFC 3947) vendor ID Apr 5 17:28:07 charon 05[IKE] <con2000|25> sending NAT-T (RFC 3947) vendor ID Apr 5 17:28:07 charon 05[IKE] sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID Apr 5 17:28:07 charon 05[IKE] <con2000|25> sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID Apr 5 17:28:07 charon 05[IKE] initiating Main Mode IKE_SA con2000[25] to 35.180.xxx Apr 5 17:28:07 charon 05[IKE] <con2000|25> initiating Main Mode IKE_SA con2000[25] to 35.180.xxx Apr 5 17:28:07 charon 05[IKE] IKE_SA con2000[25] state change: CREATED => CONNECTING Apr 5 17:28:07 charon 05[IKE] <con2000|25> IKE_SA con2000[25] state change: CREATED => CONNECTING Apr 5 17:28:07 charon 05[CFG] <con2000|25> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048 Apr 5 17:28:07 charon 05[ENC] <con2000|25> generating ID_PROT request 0 [ SA V V V V V ] Apr 5 17:28:07 charon 05[NET] <con2000|25> sending packet: from 192.168.1.49[500] to 35.180.xxxx Apr 5 17:28:07 charon 05[NET] <con2000|25> received packet: from 35.180.xxx [500] to 192.168.1.49[500] (40 bytes) Apr 5 17:28:07 charon 05[ENC] <con2000|25> parsed INFORMATIONAL_V1 request 0 [ N(NO_PROP) ] Apr 5 17:28:07 charon 05[IKE] received NO_PROPOSAL_CHOSEN error notify Apr 5 17:28:07 charon 05[IKE] <con2000|25> received NO_PROPOSAL_CHOSEN error notify Apr 5 17:28:07 charon 05[IKE] IKE_SA con2000[25] state change: CONNECTING => DESTROYING Apr 5 17:28:07 charon 05[IKE] <con2000|25> IKE_SA con2000[25] state change: CONNECTING => DESTROYINGThe encryption algorithm is fine: AES 128bit SHA1 DH2.
Could somebody help please?
Regards,
Cosmin -
@tupanu Hi
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ipsec-troubleshooting.html
key for finding the source of a possible problem "NO_PROPOSAL_CHOSEN"
-
Hello,
Thank you for the link.
When I've created the tunnels with AWS pfsense wizard, theauthentication methodwasMutual PSKbut on aws side I used certificates.
Anyway, I've imported the certificates from AWS, changed the authentication method and now I've run into another problem:Apr 6 06:05:58 charon 11[ENC] <con3000|887> generating ID_PROT request 0 [ SA V V V V V ] Apr 6 06:05:58 charon 11[NET] <con3000|887> sending packet: from 192.168.1.49[500] to 52.47.XXX.XXX[500] (180 bytes) Apr 6 06:05:58 charon 11[NET] <con3000|887> received packet: from 52.47.XXX.XXX[500] to 192.168.1.49[500] (124 bytes) Apr 6 06:05:58 charon 11[ENC] <con3000|887> parsed ID_PROT response 0 [ SA V V ] Apr 6 06:05:58 charon 11[IKE] <con3000|887> received DPD vendor ID Apr 6 06:05:58 charon 11[IKE] <con3000|887> received NAT-T (RFC 3947) vendor ID Apr 6 06:05:58 charon 11[CFG] <con3000|887> selecting proposal: Apr 6 06:05:58 charon 11[CFG] <con3000|887> proposal matches Apr 6 06:05:58 charon 11[CFG] <con3000|887> received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Apr 6 06:05:58 charon 11[CFG] <con3000|887> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Apr 6 06:05:58 charon 11[CFG] <con3000|887> selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Apr 6 06:05:58 charon 11[IKE] <con3000|887> reinitiating already active tasks Apr 6 06:05:58 charon 11[IKE] <con3000|887> ISAKMP_VENDOR task Apr 6 06:05:58 charon 11[IKE] <con3000|887> ISAKMP_CERT_PRE task Apr 6 06:05:58 charon 11[IKE] <con3000|887> MAIN_MODE task Apr 6 06:05:58 charon 11[LIB] <con3000|887> size of DH secret exponent: 1023 bits Apr 6 06:05:58 charon 11[ENC] <con3000|887> generating ID_PROT request 0 [ KE No NAT-D NAT-D ] Apr 6 06:05:58 charon 11[NET] <con3000|887> sending packet: from 192.168.1.49[500] to 52.47.XXX.XXX[500] (244 bytes) Apr 6 06:05:58 charon 11[NET] <con3000|887> received packet: from 52.47.XXX.XXX[500] to 192.168.1.49[500] (356 bytes) Apr 6 06:05:58 charon 11[ENC] <con3000|887> parsed ID_PROT response 0 [ KE No CERTREQ NAT-D NAT-D ] Apr 6 06:05:58 charon 11[IKE] <con3000|887> received cert request for 'C=FR, O=xx, OU=xx, ST=xx xx, CN=xx, L=xx' Apr 6 06:05:58 charon 11[IKE] <con3000|887> local host is behind NAT, sending keep alives Apr 6 06:05:58 charon 11[IKE] <con3000|887> remote host is behind NAT Apr 6 06:05:58 charon 11[IKE] <con3000|887> reinitiating already active tasks Apr 6 06:05:58 charon 11[IKE] <con3000|887> ISAKMP_VENDOR task Apr 6 06:05:58 charon 11[IKE] <con3000|887> ISAKMP_CERT_PRE task Apr 6 06:05:58 charon 11[IKE] <con3000|887> MAIN_MODE task Apr 6 06:05:58 charon 11[IKE] <con3000|887> sending cert request for 'C=FR, O=xx, OU=xx, ST=xx xx, CN=xx, L=xx' Apr 6 06:05:58 charon 11[IKE] <con3000|887> authentication of 'CN=vpn-07633023bf21e2c62.endpoint-1' (myself) successful Apr 6 06:05:58 charon 11[IKE] <con3000|887> sending end entity cert "CN=vpn-07633023bf21e2c62.endpoint-1" Apr 6 06:05:58 charon 11[ENC] <con3000|887> generating ID_PROT request 0 [ ID CERT SIG CERTREQ N(INITIAL_CONTACT) ] Apr 6 06:05:58 charon 11[NET] <con3000|887> sending packet: from 192.168.1.49[4500] to 52.47.xx.xx4500] (1500 bytes) Apr 6 06:05:58 charon 11[NET] <con3000|887> received packet: from 52.47.xxx.xxx[4500] to 192.168.1.49[4500] (1356 bytes) Apr 6 06:05:58 charon 11[ENC] <con3000|887> parsed ID_PROT response 0 [ ID CERT SIG V ] Apr 6 06:05:58 charon 11[ENC] <con3000|887> received unknown vendor ID: 49:4b:45:76:32 Apr 6 06:05:58 charon 11[IKE] <con3000|887> received end entity cert "CN=vpn-07633023bf21e2c62.endpoint-1" Apr 6 06:05:58 charon 11[IKE] <con3000|887> IDir 'CN=vpn-07633023bf21e2c62.endpoint-1' does not match to '52.47.xx.xx' Apr 6 06:05:58 charon 11[IKE] <con3000|887> queueing ISAKMP_DELETE task Apr 6 06:05:58 charon 11[IKE] <con3000|887> activating new tasks Apr 6 06:05:58 charon 11[IKE] <con3000|887> activating ISAKMP_DELETE task Apr 6 06:05:58 charon 11[IKE] <con3000|887> deleting IKE_SA con3000[887] between 192.168.1.49[CN=vpn-07633023bf21e2c62.endpoint-1]...52.47.xx.xx[%any] Apr 6 06:05:58 charon 11[IKE] <con3000|887> sending DELETE for IKE_SA con3000[887]What is means
Apr 6 06:05:58 charon 11[IKE] <con3000|887> IDir 'CN=vpn-07633023bf21e2c62.endpoint-1' does not match to '52.47.xx.xx'?
Does this means that the certificated from pfsense don't match the one from aws?
How can I fix this?Thanks a lot
-
-
Please excuse my ignorance but I can't make it work.
From the log the CN of the certificate is :
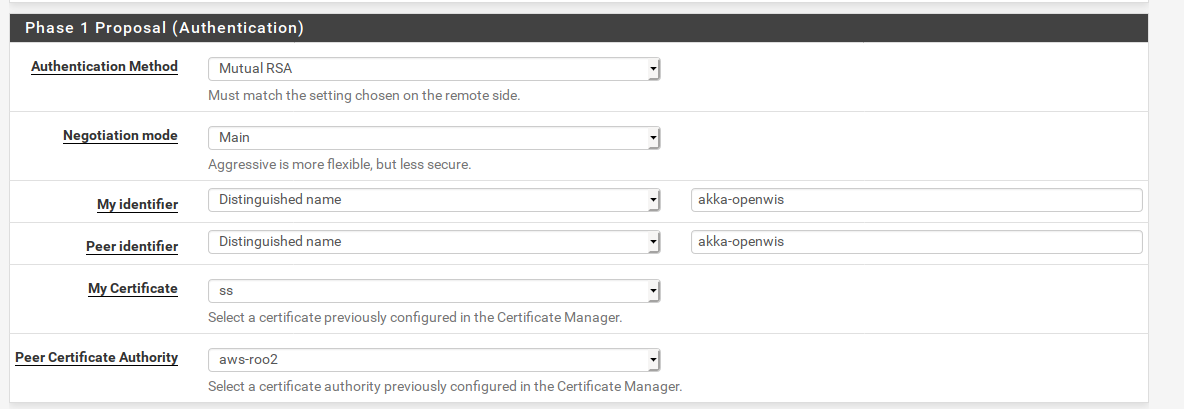
received cert request for 'C=FR, O=XXX, OU=ASW, ST=Haute Garonne, CN=akka-openwis, L=ToulouseHere are my settings:
But I still get:
Apr 6 07:34:00 charon 14[IKE] <con2000|1071> IDir 'CN=vpn-07633023bf21e2c62.endpoint-0' does not match to 'akka-openwis'I've tried with
keyID = vpn-07633023bf21e2c62.endpoint-0but no luck. -
I ran into this and had created my own post https://forum.netgate.com/topic/157561/aws-vpn-to-pfsense-w-cert-based-auth-how-to-configure-peer-identifier-for-cn/2 but I found the answer through testing and think it would work for you too.
On the pfSense side, for the Phase 1 peer identifier set the type to ASN.1 distinguished Name and the value to CN=vpn-07633023bf21e2c62.endpoint-1 (just using the example in your post, I assume in reality you haven't left a broken VPN running in AWS all this time and now you would have a different endpoint name) and try connecting the tunnel.