DNS doesn't work after switch layer 3 inter vlan routing upgrade
-
-
What does traceroute show? Also, why are you hiding the monitor IP? That shouldn't be your assigned address. It could be your ISPs gateway, DNS server or some other publicly reachable address.
-
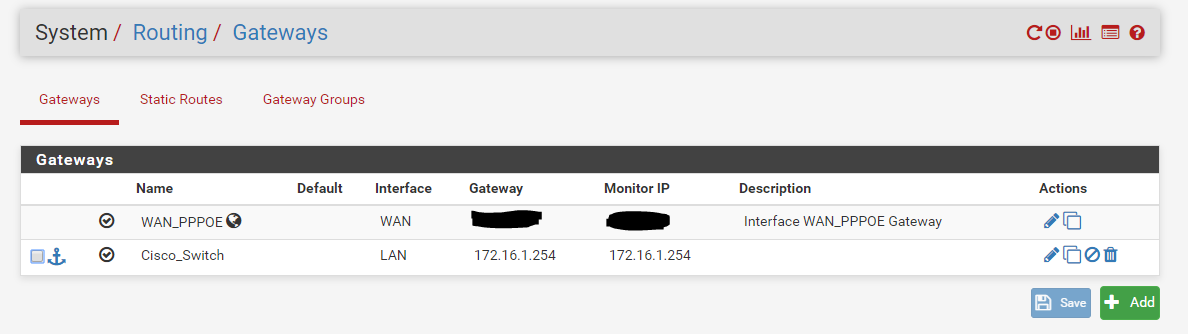
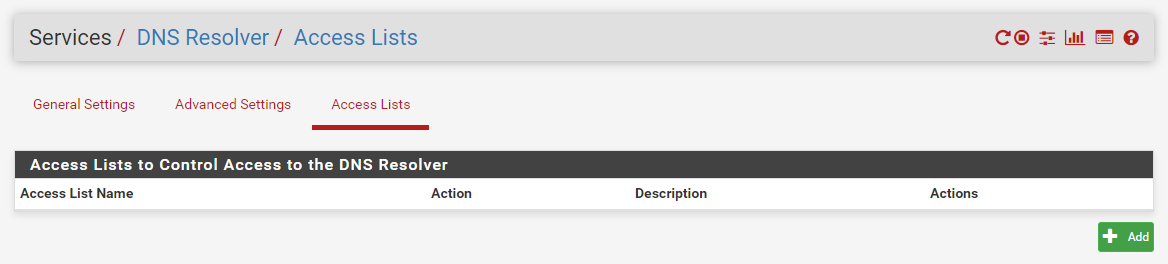
If your vlan 50 devices can not query your dns on 172.16.1.1 - most likely its the ACLs.. So ACLs for network directly connected to pfsense get auto created... But when your doing downstream networks, you would have to allow those queries via your ACLs setup in unbound.
Also I want to warn you up front about doing this - see this all the time... Do you plan on having devices on this 172.16.1 network? If so your most likely going to run into asymmetrical routing problems..
If you want to do downstream router - that is fine, but it needs to be a pure transit network that connects pfsense to your downstream router.. If your going to put hosts on this transit network, then you need to host route on those devices or you will end up with asymmetrical issues if these hosts are going to talk to downstream networks, or downstream networks are going to be talking to them.
-
Hi @JKnott and @johnpoz ,
Thanks for yours prompt reply.
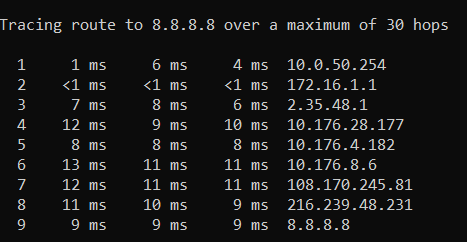
This is traceroute from vlan 50
Hiding it comes to me automatically :) this is lab enviroment and WAN IP is assigned by ISP dhcp, no reason at all for hiding. I fell sorry if you interpreted as a lack of trust.I assigned ACL on LAN interface for this subnet
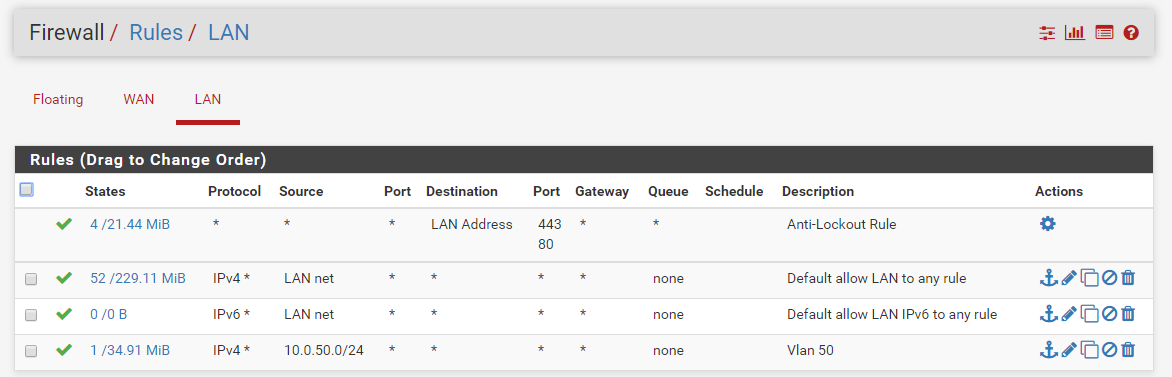
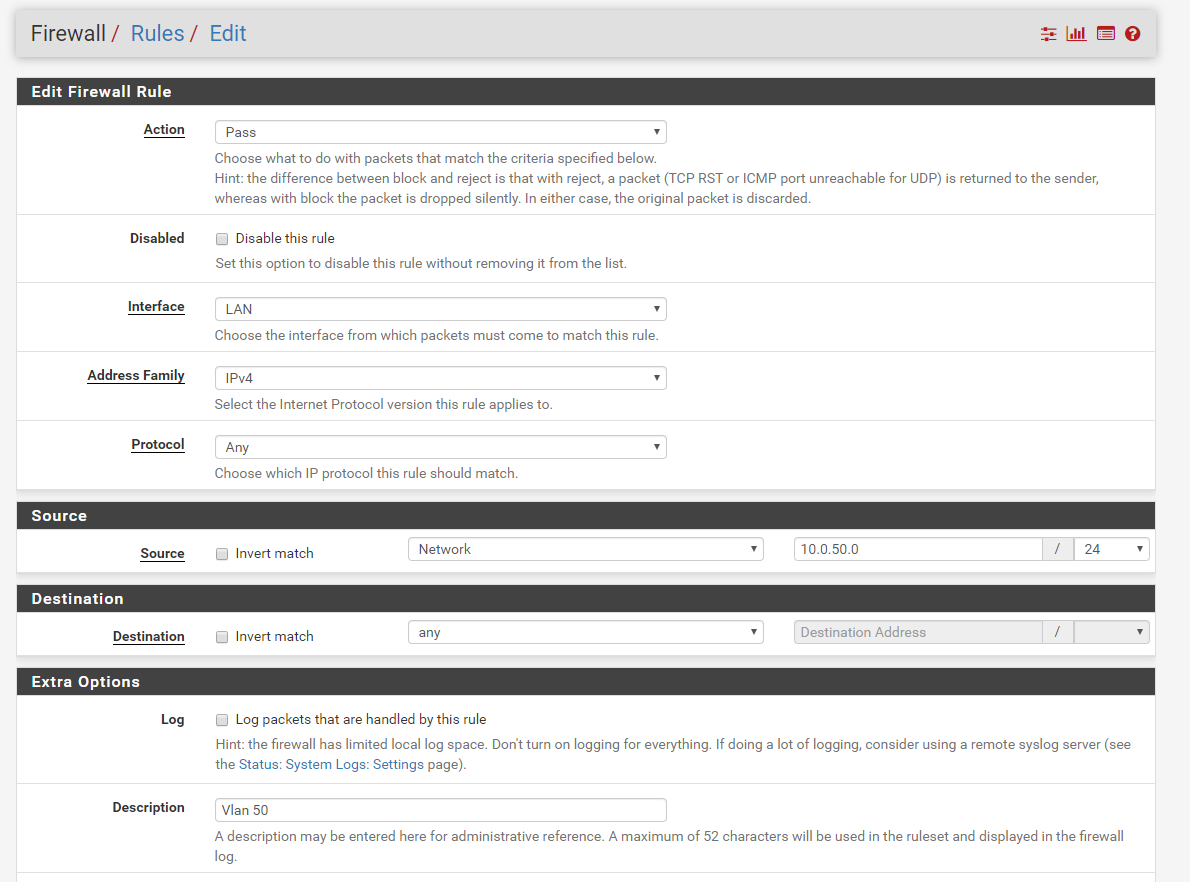
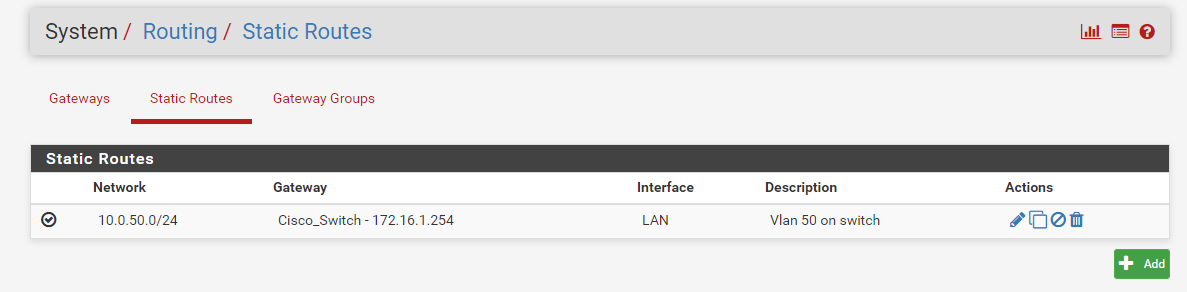
My goal is to use subnet 172.16.1.1 only as a transit network and shrink it from /24 to /30.
Anyway thanks for your advice to not use 172.16.1.1 as vlan for hosts.I appreciate your help
-
@chiprule said in DNS doesn't work after switch layer 3 inter vlan routing upgrade:
This is traceroute from vlan 50
I thought your problem was reaching VLAN 50. Why are you showing a traceroute from it to the Internet?
-
Not talking about you rules on your interface - talking about your unbound ACLs
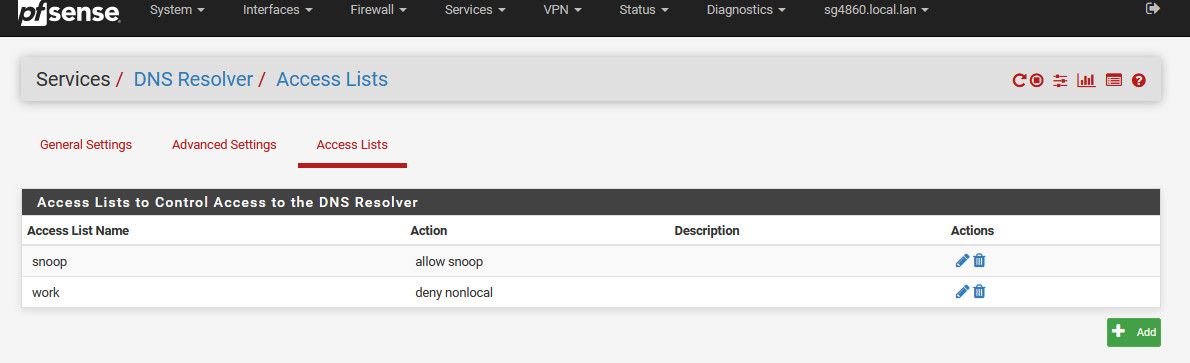
The auto rules create rules for the local attached networks, but will not work for downstream networks.. You would have to create acl to allow your 50 vlan to query dns..
Simple dig would show you not working or working..
-
Hi @JKnott
As I said in first post
"Now i can ping from vlan 1 to vlan 50 and viceversa.
I can ping PFsense LAN IP interfaces from both vlan.
I can ping 8.8.8.8 from both vlan.
I can go in internet with vlan 1 but not with vlan 50.""It seem to be a DNS problem. I can't figure out what is the missing or wrong config."
-
Exactly - so since this network is not directly attached - your auto rules will not allow you to query dns..
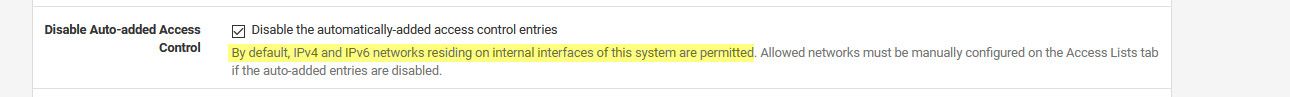
I turn off auto rules - because I hate auto rules ;) hehehe The lets me assign the acls I want specifically vs the auto... But out of the box it only creates acls that allow your locally attached networks to query unbound.. Which you downstream vlan 50 is NOT!!! Simple query would of showed you refused!
-
Hi @johnpoz
You solve my problem!!!
I'm new on PFsense and I'm learning. What do you mean of query? Query from host of vlan 50? You mean nslookup?Thanks
-
Yeah a dns query.. looking up something.domain.tld, ie www.google.com - this is a dns query..
Doing that with your fav dns tool, dig, host, sure even nslookup - which is pretty useless unless in full debug mode (set debug) would of shown you a refused response..
This isn't pfsense stuff - that is just basic dns stuff..
-
Hi @johnpoz
thanks for your help, I appreciate it!