Initial site to site IPSEC not working ...
-
I'll start by saying I'm new to ipsec and certainly don't have a depth of knowledge with VPN etc.
I've used the SG3100 to setup remote users and that has worked fine.
So, now I need to setup some site to site tunnels using ipsec from the SG3100 to 3rd party LTE routers. I am trying to keep things simple to simply fault finding before trying to harden firewalls etc. I have a test router going that is connected and has a dyndns address. I have it configured and can connect (but only from the SG3100 which is odd) but when connected nothing passes when though I have an any/any rule as per the pfsense book ...If anyone has any links to any docs that don't assume pfsense both ends that I can reference it would be appreciated.
-
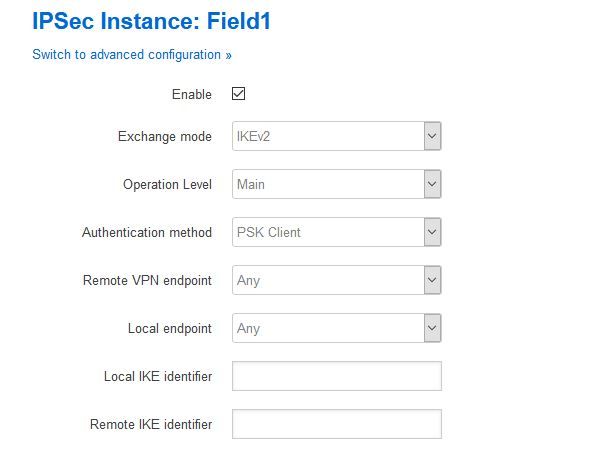
Also if anyone has any idea why I have to leave the endpoints (local and remote) as any any to get any (ha ha) kind of connection to begin to form I'd be keen to know ..
-
Ok. so some small steps forward. The tunnel is up and will establish from the client end which is what I need.
but
No, and I mean no traffic is passed, or even appears to be hitting the firewall.
Thoughts ?
-
Did you add a rule to the ipsec tab on the firewall rules to allow traffic?
-
The rules were automatic, the issue was the remote and local identifiers needed to be present. Any / Any did'nt cut it. All sorted although I did'nt find that answered anywhere here.