haproxy and wildcard lets encrypt only for internal servers
-
do i have to copy these to somewhere else ?
maybe to /var/etc/haproxy/ ???-----END CERTIFICATE-----
[Tue Apr 14 20:47:33 CEST 2020] Your cert is in /tmp/acme/certName.xyz//.certName.xyz/.certName.xyz.cer
[Tue Apr 14 20:47:33 CEST 2020] Your cert key is in /tmp/acme/certName.xyz//.certName.xyz/.certName.xyz.key
[Tue Apr 14 20:47:33 CEST 2020] The intermediate CA cert is in /tmp/acme/certName.xyz//.certName.xyz/ca.cer
[Tue Apr 14 20:47:33 CEST 2020] And the full chain certs is there: /tmp/acme/certName.xyz//.certName.xyz/fullchain.cer
[Tue Apr 14 20:47:33 CEST 2020] Run reload cmd: /tmp/acme/certName.xyz/reloadcmd.shIMPORT CERT certName.xyz, /tmp/acme/certName.xyz/.certName.xyz/.certName.xyz.key, /tmp/acme/certName.xyz/.certName.xyz/.certName.xyz.cer
update cert![Tue Apr 14 20:47:34 CEST 2020] Reload success -
@noplan
If you open the 'name.pem' file, does it contain 'BEGIN CERTIFICATE' twice?
If you look in the pfSense certificate manager, on the certificates tab, is the 'Issuer' column filled? If not try adding the intermediate cert from LE at the CAs tab, it should then automatically fill the Issuer on the certs tab as well when iirc..That would only be separate 'parts' of the fullchain.cer ..
(afaik the LE cert that signs public certs itself is not trusted root.., seems not with my one anyhow.. but i set it up a few years ago.. maybe things changed..)
-
name.pem (goes like this)
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE----------BEGIN RSA PRIVATE KEY-----
-----END RSA PRIVATE KEY----------BEGIN CERTIFICATE-----
-----END CERTIFICATE-----certificate manager, on the certificates tab
yes filled with
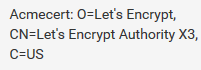
-
@noplan hmm.. seems it all sounds good..
sure the browser doesn't use a proxy.? or a local dns direct record? -
firefox / not usin a proxy
pfsense is the DNS
hmm /me a little in the woods now :) *ffffff
-
@noplan
Send you a PM/chat, perhaps i can take a look at your setup.?. -
-
The only progress I was able to make with this is to remove the "Register DHCP static mappings in the DNS Resolver" .... save ... apply.
Close the browser, run ipconfig /flushdns, reopen the browser and it works.
As a consequence, I loose access to anything that I had as a static DHCP lease and didn't set an override for...but also if I want to ssh into one of the machines that I have an override for...I will get my PFsense box.
For more details, I posted my findings here: Override Hosts not working with DNS Resolver
If you leave the tick in, "Register DHCP static mappings in the DNS Resolver" ... then the resolver servers two IPs... the 1st is the actual IP of your server, the 2nd is the override.
Looks like the browser uses the 1st IP and goes directly to your machine, bypassing haproxy, and getting the self signed cert... NOT the wildcard cert from LE.
I don't know what the solution to this is... maybe someone with more experience can chime in?
-
yes i fixed it
plain and simple the only thing i had to change in


domain = your domain
IP = ip your HaProxy is runnin on in this case the LAN IP of the firewalland it is workin
let me know if u succeeded
brNP -
@noplan Thanks for the reply.
Naw... I've tried that. It doesn't work for my setup. Pfsense returns two IPs for that hostname...but the 1st IP is the real server IP...the 2nd IP is the 'override' ... besides I can't ssh into the server if the override IP is the only one that resolves for that hostname...
Just starting to accept the fact that this solution won't work for my setup.