Can I intercept DNS?
-
This post is deleted! -
solved how ?
-
I setup an outbound NAT rule to intercept any calls to Google's DNS and route them instead to my intranet DNS server.
-
Intercept what DNS ?
The classic '53' could be intercepted and routed else where. See pfSense manual, it's explained how to do so.If clients - or the browser used by the clients, decide to use DNS over TLS, port 853, you can't. You could block destination port 853 and hope the client falls back to classic '53' usage.
If the "client" detects this, he'll fire up a VPN ;) -
if u wanna play u can do something like that in
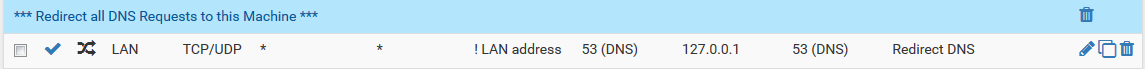
and a fw rule like that

this should do the trick :)
or am 1 missin something @Gertjan -
@noplan said in Can I intercept DNS? (solved):
1 missin something
DNS request are not only UDP. That was valid in the eighties, the other century.
Check this out DNS over TLS.
Typical application : Google Public DNS : DNS-over-TLSAlso, look in the forum you posted ! - take the very first pinned post : Home pfSense
 Software DHCP and DNS HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox.
Software DHCP and DNS HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox.All this boils down to : you, as an router firewall admin can advise your clients what DNS to use. Your clients can take that advise, or stuff it. Next solution : have a talk with your clients - or pull the switch.
-
@Gertjan
rigth about the other century .... i m always tryin to ignore that (not remindin me how old i am)ok another small project (thanks for the riminder with the link) to anoy my it guys gggggg
we boiled it down not to use DNSoTLS so far workin but for how long ?
i liked the approach to redirect all DNS related traffic back to the firewall (where the magic happens eg pfBlocker)
you dont ?brNp (from that other century) ;)
-
-
Interesting. When I setup the rule, I didn't specify DNS 53 exactly. I just set the rule so any traffic of any protocol/port going to 8.8.8.8 gets routed to 10.0.0.3.
It seemed to work; when I used nslookup before the rule and did server 8.8.8.8 it reported dns.google. After the rule, it reported my own internal DNS hostname. I grabbed my Fire tablet and went to one of my sites and it worked so I assumed I'm good. But then I went to another of my sites and it timed out. Unsure why it works on one but not another; they're both on the same server, same setup. (shrug) I can't figure out how to flush DNS on the tablet but maybe once the cache duration expires it'll start working.
-
@Strahan said in Can I intercept DNS? (solved):
figure out how to flush DNS on the tablet
Switching off the IP stack = shutting down the wifi, should do it.
If not, rebooting.
If not, remove battery ?@Strahan said in Can I intercept DNS? (solved):
the rule so any traffic of any protocol/port going to 8.8.8.8 gets routed to 10.0.0.3.
I propose :
the rule so any traffic of any protocol/port53 going to any gets routed to 10.0.0.3.pfSense is 10.0.0.3 ?
Then who is 10.0.0.1 ???? -
@Gertjan 10.0.0.3 is my Active Directory domain controller (and infrastructure box). pfSense is 10.0.0.1.
Also I thought I had it licked, but now none of my domains work. They all resolve to the external IP, as though I resolved it from an internet DNS not intranet. AUGH. Weird, because some worked fine the other day.
I think I just give up at this point, going to return this !@##$%^ Fire HD and get a Galaxy Tab A. The price I realized is only like $40 less for the Fire, that is NOT worth the headache lol
-
Why not hand out the address of the internal dns server via dhcp. Then block any dns requests port 853 53 and otherwise not destined for the internal dns server.
-
^exactly - much better way to do it in my personal and professional opinion.. Interception of traffic is not a good thing, be it your doing it or your isp is doing it... What do you feel about your ISP doing it - then why and the F would you do it on your own network ;)
If you don't want clients using outside dns, then don't let them - why intercept it and let them think they are using X?
The problem with clients trying to use their own dns problem currently is them using doh to circumvent a networks wishes.. Atleast with dot or normal dns easy to block with port block.. doh is whole new ball game, that is not in anyone best interest.. Sure is not a security thing handing all your dns to provider X..
-
The only thing to do so (redirect all dns traffic to your own box in you Lan)
Is the use of content filter and not willing to use a full man in the middle attackAm I looking wrong at this
BrNP
-
@tman904 said in Can I intercept DNS? (solved):
Why not hand out the address of the internal dns server via dhcp. Then block any dns requests port 853 53 and otherwise not destined for the internal dns server.
I am. Problem is, Amazon automatically adds 8.8.8.8. I assumed the Google DNS would be a secondary, only used if the internal is not reachable but that is not the case. It is checking there first which is what hoses me up.
@johnpoz said in Can I intercept DNS? (solved):
^exactly - much better way to do it in my personal and professional opinion.. Interception of traffic is not a good thing, be it your doing it or your isp is doing it... What do you feel about your ISP doing it - then why and the F would you do it on your own network ;)
If you don't want clients using outside dns, then don't let them - why intercept it and let them think they are using X?
The problem with clients trying to use their own dns problem currently is them using doh to circumvent a networks wishes.. Atleast with dot or normal dns easy to block with port block.. doh is whole new ball game, that is not in anyone best interest.. Sure is not a security thing handing all your dns to provider X..
I was afraid blocking it would cause latency in DNS lookups while the tablet was trying to reach 8.8.8.8. I assume it'd have to time out before it goes to the internal one. The fact that it is my own network is why I'm cool with interception. If I cannot trust myself, who can I trust? ;)
Edit: I just tested blocking 8.8.8.8 and now I have no name resolution at all. It's like the tablet only wants that DNS and is ignoring my internal one. (sigh)
-
@Strahan said in Can I intercept DNS?:
I just tested blocking 8.8.8.8 and now I have no name resolution at all.
And what tablet is that? I multiple alexa, dots and shows. And my grand kids have amazon tablets.. Have always blocked google dns.. Never any issues.
Why don't you sniff and validate exactly what is happening.. While a device might try and use say google dns... If you hand it local dns - it should use that, period! Or it wouldn't be able to resolve anything locally.. etc..
-
@johnpoz It's a Fire HD 10. I agree, I don't see why it isn't using the DHCP provided DNS primarily. It's quite frustrating. For example, I have kana.domain.com on my 10.0.0.3 DNS server. It's a CNAME to web.domain.com which is an A record with a value of 10.0.0.100. Externally, kana.domain.com is CNAME'd to web.domain.com which is an A record with a value of 50.77.x.x.
On my Fire HD, I go to load that website and it times out. Opened a ping tool, and kana.domain.com resolves to 50.77.x.x. I'm not a network guy, I have no idea how to validate what its doing. I know I can run Wireshark on my PC, but they don't have that for the Fire HD and not being a network guy I haven't a clue how to have pfSense report the activity unfortunately.
-
sniff on pfsense, its packet capture under diag menu..
t's a CNAME to web.domain.com which is an A record with a value of 10.0.0.100
If you have public anything resolving to a 10.x address - its going to fail locally, since that would be a rebind. If you have rfc1918 address space in a public domain - that should fail everywhere - such a setup is pretty borked. If you want something.domain.tld to resolve locally to a rfc1918 address, then setup your local dns to resolve that - say a host override in unbound.
If you do for some reason need/want to resolve a public available record to a rfc1918 address, then you need to turn off rebind protection or set that as a private domain in unbound.. The one example of this that comes to mind is with how plex works out its ability to do ssl with its wildcard certs.. It resolves your uniqueID.plex.direct to your local rfc1918 address, which means you have to tell unbound in pfsense to be able to resolve that with a
private-domain: plex.direct
Setting in unbound.
How did you setup a cname locally? unbound does not make that easy in the gui, and your client would have to specifically look for a cname.. Or you would have to have a resolver looking that up when you ask for the A record, etc. etc..
PM what this fqdn your trying to resolve exactly? And I will take a look see on what is up with it. What do you want this fqdn (something.whatever.tld) to resolve to?
-
Nothing public resolves to a 10 address. My domain exists on both the internal DNS server and the public DNS server. The internal forwards requests it doesn't have local to my ISP DNS. So for computers with 10.0.0.3 DNS, a request for www.google.com hits 10.0.0.3 then gets forwarded to 75.75.75.75 since that isn't authoritative for that domain. A request for www.mydomain.com though gets served from 10.0.0.3 since mydomain.com is local to that server thus it gives 10.0.0.100. A person outside my LAN requests www.mydomain.com and gets my record from ClouDNS where I have my public records hosted and that resolves to a 50.77 address.
It's worked fine for years this way, and it's the same way our DNS is setup at work (a major municipal government entity). It's only a problem because this blasted Fire HD tablet is apparently asking 8.8.8.8 first. I tried blocking 8.8.8.8 all together and then name resolution totally fails on the tablet, which is why I think it's ignoring the 10.0.0.3 DNS server DHCP is giving out.
