IPsec Mobile Clients don't receive traffic seen on IPsec interface
-
First time trying to get a working IKEv2 EAP-TLS configuration for macOS and iOS mobile clients. I had a tested working configuration, then came back the next morning and successfully connected but no traffic would pass. I am nearly certain that I didn't change anything right before I left. I see traffic in both directions on the IPsec
enc0interface, but the clients behave as if they do not receive any replies.All configuration attached. Any insights?
Summary
- Server: pfSense 2.4.5 on Netgate XG-7100
- Clients: macOS 10.14.6 & iOS 13.3.1
PKI
- Internal Root CA
- Intermediate L2 CA
- VPN Server Certificate
- Intermediate L3 CA
- VPN Client Certificates
- Intermediate L2 CA
Configuration Details
pfSense Configuration Pages
Mobile Clients
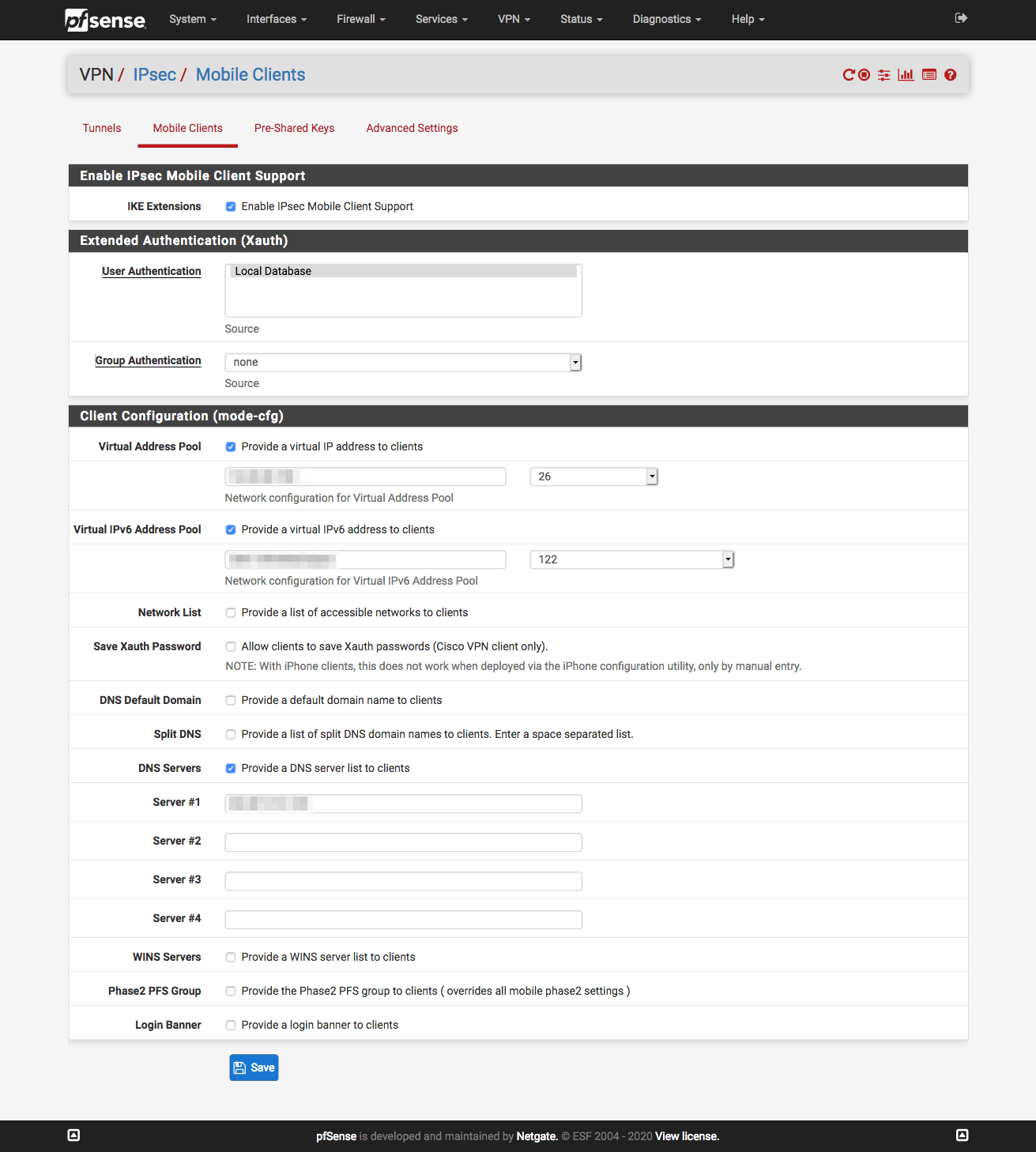
Phase 1
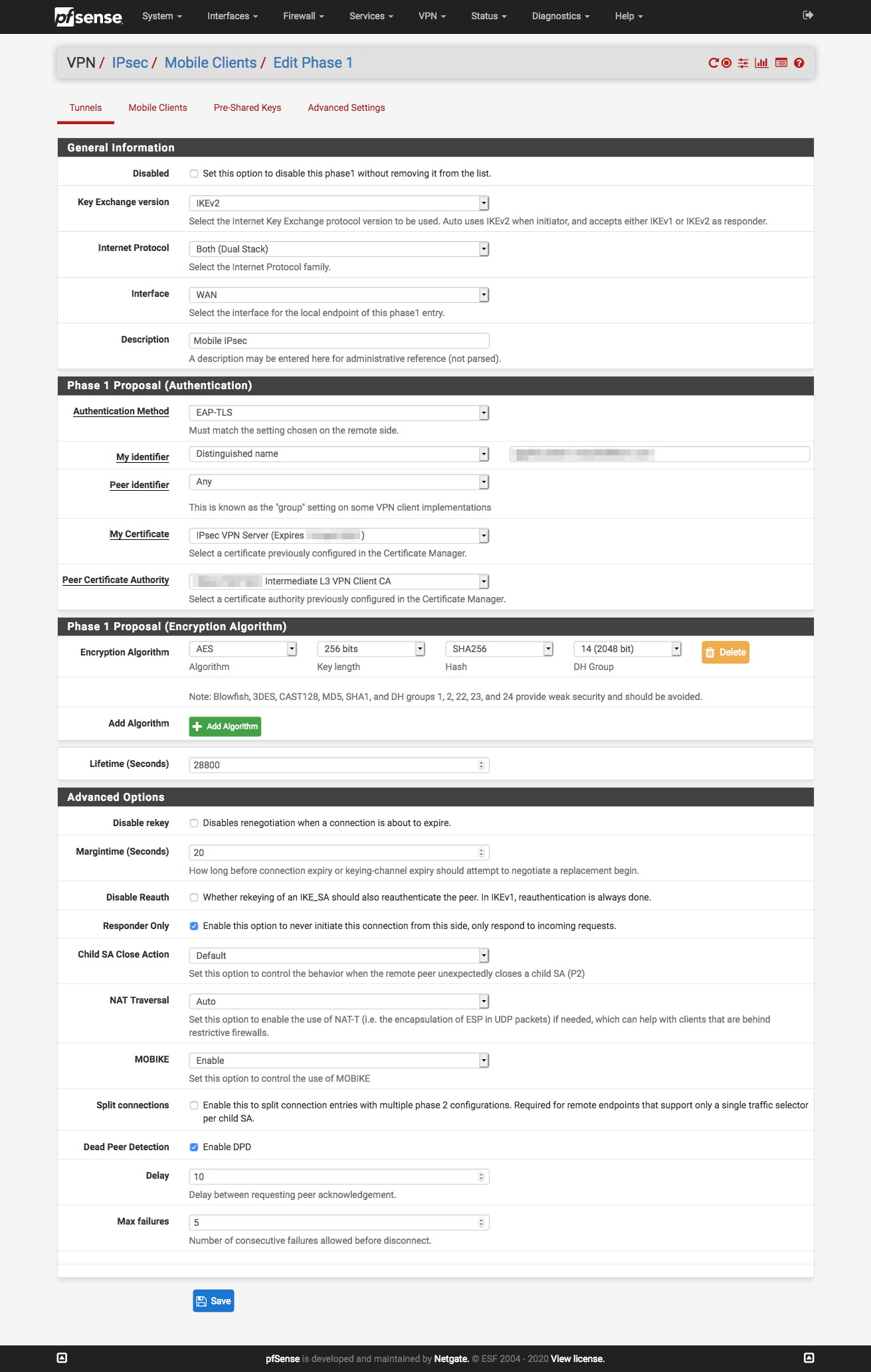
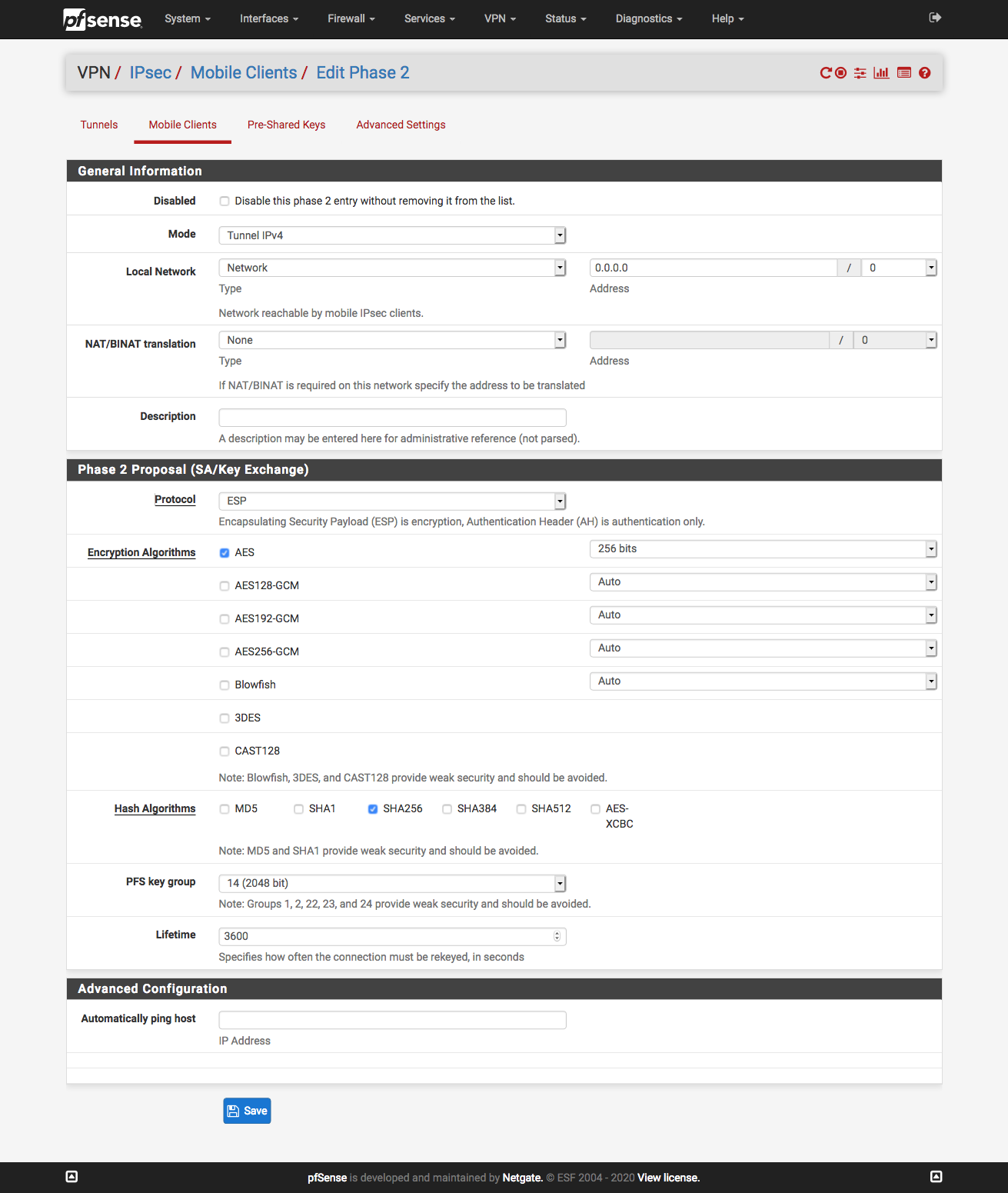
Phase 2 - IPv4
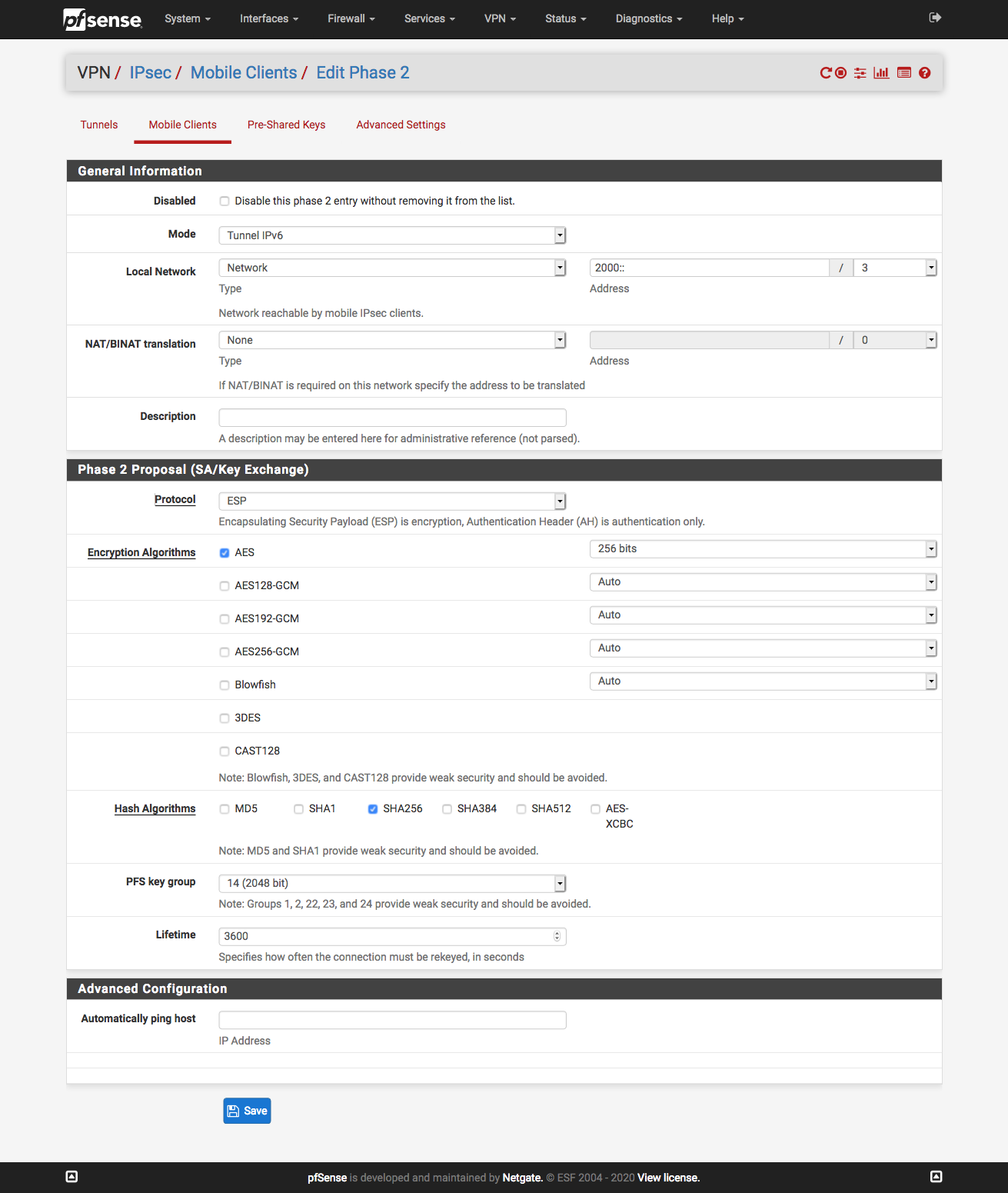
Phase 2 - IPv6
ipsec.conf# This file is automatically generated. Do not edit config setup uniqueids = yes conn con-mobile fragmentation = yes keyexchange = ikev2 reauth = yes forceencaps = no mobike = yes rekey = yes margintime = 20s installpolicy = yes type = tunnel dpdaction = clear dpddelay = 10s dpdtimeout = 60s auto = add left = <<WAN IPv4>>,<<WAN IPv6>> right = %any leftid = fqdn:<<WAN DNS name with A and AAAA records>> ikelifetime = 28800s lifetime = 3600s rightsourceip = 10.xxx.xxx.xxx/26,<<Globally routable IPv6 prefix>>/122 rightdns = <<IPv4 address of firewall LAN interface>> ike = aes256-sha256-modp2048! esp = aes256-sha256-modp2048! eap_identity=%identity leftauth=pubkey rightauth=eap-tls leftcert=/var/etc/ipsec/ipsec.d/certs/cert-1.crt leftsendcert=always rightca="<<DN of internal intermediate CA that issues all client certificates>>" leftsubnet = 0.0.0.0/0,2000::/3strongswan.conf# Automatically generated config file - DO NOT MODIFY. Changes will be overwritten. starter { load_warning = no config_file = /var/etc/ipsec/ipsec.conf } charon { # number of worker threads in charon threads = 16 ikesa_table_size = 32 ikesa_table_segments = 4 init_limit_half_open = 1000 install_routes = no load_modular = yes ignore_acquire_ts = yes cisco_unity = no syslog { identifier = charon # log everything under daemon since it ends up in the same place regardless with our syslog.conf daemon { ike_name = yes dmn = 1 mgr = 1 ike = 1 chd = 1 job = 1 cfg = 1 knl = 1 net = 1 asn = 1 enc = 1 imc = 1 imv = 1 pts = 1 tls = 1 esp = 1 lib = 1 } # disable logging under auth so logs aren't duplicated auth { default = -1 } } plugins { # Load defaults include /var/etc/ipsec/strongswan.d/charon/*.conf stroke { secrets_file = /var/etc/ipsec/ipsec.secrets } unity { load = no } curve25519 { load = yes } attr { } xauth-generic { script = /etc/inc/ipsec.auth-user.php authcfg = Local Database } } }
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.