Tip - I solved my WiFi Calling issues
-
I finally remembered that I meant to share this months ago when I discovered it, so here I am ...
I'll be succinct:
- I have all iPhones in the house, and WiFi calling was sporadic on all of them. It might work for a while, or only a few minutes, or never manage to negotiate the Wi-Fi calling connection at all
- Two iPhones could never be on WiFi Calling at the same time
- Providers are Rogers (x2) and Fido (x1)
- pfSense 2.4 series, bone stock rules
The problem was the auto-generated ISAKMP rules. I turned them off:
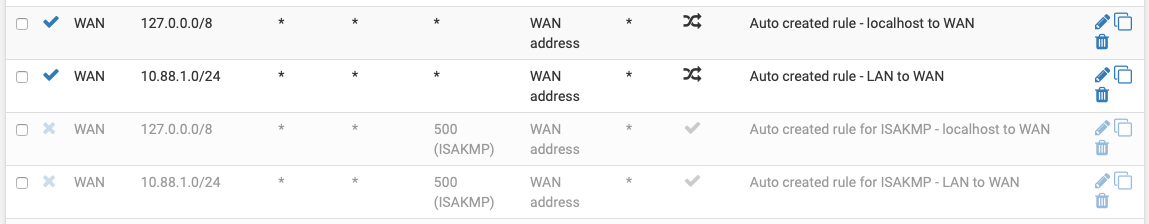
Now WiFi Calling is perfect on any iOS device on my home network.
However, from the docs (https://docs.netgate.com/pfsense/en/latest/nat/static-port.html) ...
Automatic Outbound NAT rules on the pfSense firewall will retain the source port for UDP 500 (ISAKMP for IPsec VPN traffic) by default because this traffic will almost always be broken by rewriting the source port.So, your mileage may differ if you use IPsec for other than WiFi Calling. Behaviour may differ between providers, too.
Cheers!
-
@tomk said in Tip - I solved my WiFi Calling issues:
I have all iPhones in the house
That's the problem.

-
I just started having wifi calling issues after upgrading to 2.4.5. I deleted the default isakmp rules a long time ago so I appear to be having a different issue. Are there any good resources on wifi calling that you know of to help me troubleshoot this issue?
-
@nicheath
WiFi calling is VoIP encapsulated in IPSec, encapulated in UDP. So, your issues will be with passing IPSec/UDP.
-
[Spam was here]
-
FWIW, I am also on Rogers and haven't noticed any problems. However, I have only one Android phone.
-
This post is deleted! -
This post is deleted! -
A little bit of thread necromancy here.
I have had the same issue -- intermittent problems with my Verizon Wi-Fi calling behind PfSense. I had the default auto generated rules active.
When I disable the ISAKMP rule, the problem resolves. I can consistently repro this. Rebooting my iPhone is the most reliable way to see whether it's currently working, as it will attempt to setup the tunnel as soon as you unlock the phone and it jumps on WiFi.
This doesn't make a lot of sense to me. The ISAKMP rule is static mapping the port, and if it's disabled, that port is then being rewritten/randomized. Why is this making a difference? Why does this work? I'm on 2.4.5-RELEASE-p1.
Edit: I also just tested setting a catch-all static NAT rule at the top of the list. Simply using static NAT does not break Wi-Fi calling. In fact it is still broken merely by toggling on the ISAKMP rule which is several rules beneath it in the list. Really weird.
I cannot quite put my finger on when Wifi calling broke for me but it does seem to align with upgrading to 2.4.5 for me.
Ultimately I don't think my network really needs PF to rewrite my source ports, and I already have had to write outbound NAT rules to deal with various video games (old and new) that use UDP hole punching methods. My fix for now is just going full manual and using static port.
-
Thought I would share a few of my own thoughts and experiences enabling WiFi calling behind pfSense based primarily on using Verizon as the cellular provider:
-
Apple devices (e.g. iPhones) have worked well for me without any modification need to pfSense settings. What I have noticed, however, is that iPhones may switch back to the cellular network if the signal improves even through WiFi calling is enabled. One way around this (and to essentially force WiFi calling) is to put the phone in airplane mode, effectively disabling the cellular component. Calls & text messages still work just fine. On a related note, this behavior doesn't appear to be unique to Verizon. I have also seen this on a device that was using AT&T as the cellular provider. Again, enabling airplane mode helped to persist WiFi calling.
-
For Android devices with WiFi calling enabled I received word from a family member that calls were not connecting and there were also problems with texting. The solution for me was to change "Firewall Optimization Options" to "Conservative" under System > Advanced > Firewall & NAT. There have been no more issues since making this adjustment to the settings. More details here in this thread: https://forum.netgate.com/topic/155113/wifi-calling-issue/
Hope this helps.
-
-
This post is deleted! -
Locking this, it's just attracting spam at this point.
-
S SteveITS referenced this topic on
-
J JT40 referenced this topic on
-
J JT40 referenced this topic on