two firewalls - external, and internal
-
Hello Everyone,
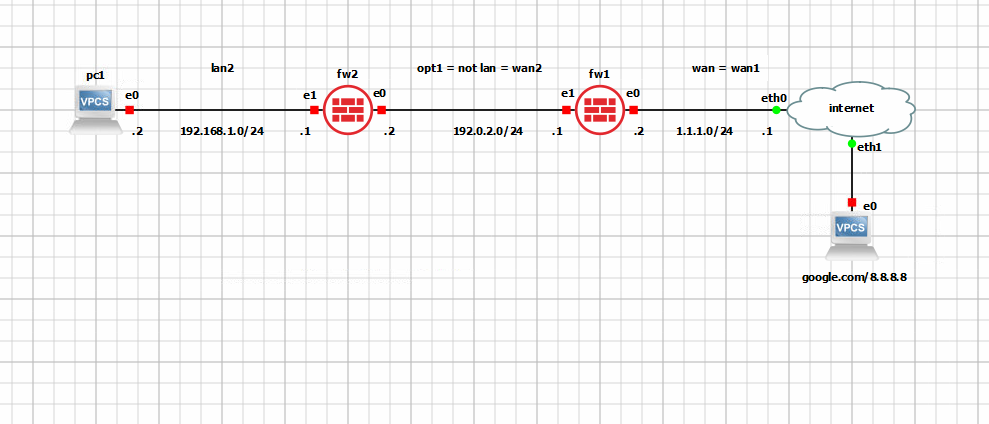
I hope All is doing well !Please, see the attached image at the bottom for a small home infrastructure with two firewalls.
There is an "external" firewall - fw1, and "internal" one - fw2.On fw1's e1- interface is configured as opt1, and e0, as wan. There is also a lan- interface on fw1 (lan1) but for simplicity it is not shown on the diagram.
The wan1 ip- address on fw1's e0 is not the real one, and just implies that it is connected to the public net.
A range of 192.0.2.0/30 (/24 on the schema is wrong) is used between fw1, and fw2.
On fw1's e1- interface icmp, dns (tcp, and udp), http, and https rules are configured, and a static route to 192.168.1.0/24 thru 192.0.2.2 is done too.On fw2's e0- interface is configured as wan, and e1 is configured as lan.
On fw2/e0 a static route to 1.1.1.0/24 thru 192.168.1.1 is configured too.From "Diagnostic"-"Ping" of fw2's wan (e0) I am able to ping google.com (the reply is ok from 8.8.8.8).
From "Diagnostic"-"Ping" of fw2's lan (e1) I am able to ping google.com, and 8.8.8.8 (the reply is OK from 127.0.0.1).From pc1, when I try to ping google.com, or 8.8.8.8 there is no reply (very strange because the dig google.com from the same pc1 is working perfectly !) - Could you give a hand with this, please ? The OS is Pop!_OS, and ufw is stopped, and disabled. No firewalld, and iptables presented, and I just ask the Pop!_OS community and they have confirmed that nothing else should block the ping by default ...
Also, for the static route on fw2 - how in pfSense the Default Route might be configured - Does 0.0.0.0/0 as destination network, instead of 1.1.1.0/24 will work ?Thanks, and Regards,
rick
-
Have you allowed ICMP on LAN2?
-
Thank you for your prompt reply JohnKap,
For FW2, I am using the default WAN-LAN- infrastructure, and I taught I do not need to do anything extra.
Do you think I need to allow the ICMP, DNS, and HTTP(S) here too ?Best,
rick
-
@rickeyw I don't recall what the default allow rule on the LAN includes.
The fact that dig works, indicates that TCP is enabled, which does not necessary mean that ICMP is enabled.
As a simple test, can you ping the firewall (192.168.1.1). If that fails, then most likely ICMP isn't allowed. What rules do you have on the LAN interface? -
thank you @JohnKap :
from the pc1:
192.168.1.1 - pingable
192.0.2.2 - pingable
192.0.2.1 - pingable
172.x.y.z - pingable (the LAN- interface of the fw1)From the web interface of fw2:
wan - traceroute google.com - success
lan - traceroute google.com - failurecan you suggest how the lan's icmp- rule supposed to look like ?
best,
rick
-
@rickeyw said in two firewalls - external, and internal:
thank you @JohnKap :
from the pc1:
192.168.1.1 - pingable
192.0.2.2 - pingable
192.0.2.1 - pingable
172.x.y.z - pingable (the LAN- interface of the fw1)That proves that ICMP is enabled on LAN2 so no need to investigate that further.
From the web interface of fw2:
wan - traceroute google.com - success
lan - traceroute google.com - failureCan you copy / paste the output of lan - tracert google.com
-
@JohnKap sorry for the late reply !
Please see the embedded link :
https://1drv.ms/u/s!Aol6-DSakWI0pxrL52AEsf94IsUl?e=NfmhCJ
best,
rick -
@rickeyw said in two firewalls - external, and internal:
@JohnKap sorry for the late reply !
Please see the embedded link :
https://1drv.ms/u/s!Aol6-DSakWI0pxrL52AEsf94IsUl?e=NfmhCJ
best,
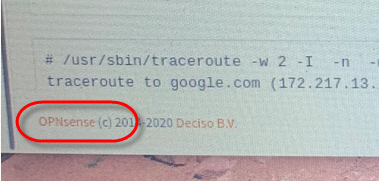
rickDo you realize you're on the wrong forum.
pfSense and OPNsense are different products!
-
@JohnKap my "front"- one is pfSense.
Best,
rick -
I'm guessing some kind of routing issue.
The tracert from both the LAN & WAN interface should be identical as they will be both routing via the same gateway - at least that what's I got when tested on my firewall.
Have a look at the routing table of FW1. It's LAN interface (which is the WAN/FW2) may require a static route telling it that 192.168.1.0/24 should be routed via its 192.168.2.1 interface. This would explain why WAN/FW2 works & LAN/FW2 doesn't as WAN/FW2 is sitting on the same subnet as LAN/FW1.