Quad9 and DNS Resolver
-
Ok so I have been using Pfsense for a bit now and am adding things one by one. So right now I am trying to get quad9 setup with DNS resolver. I came across this article https://linuxincluded.com/configuring-quad9-on-pfsense/ but not sure how accurate it is because I have come across similiar articles with somewhat different settings.
So current settings:
System --> General Setup
DNS Servers: 9.9.9.9 and 149.112.112.112DNS Server Override: unchecked
Disable DNS Forwarder: uncheckedServices --> DNS Resolver --> General Settings
Enable DNS Resolver: Checked
Next few items default
DNSSEC: Checked
Pyhton Module: Unchecked
DNS Query Forwarding: Checked
Use SSL/TLS: Checked
DHCP Registration: Unchecked
Static DHCP: unchecked
OpenVPN Clients: uncheckedIf I look at System information:
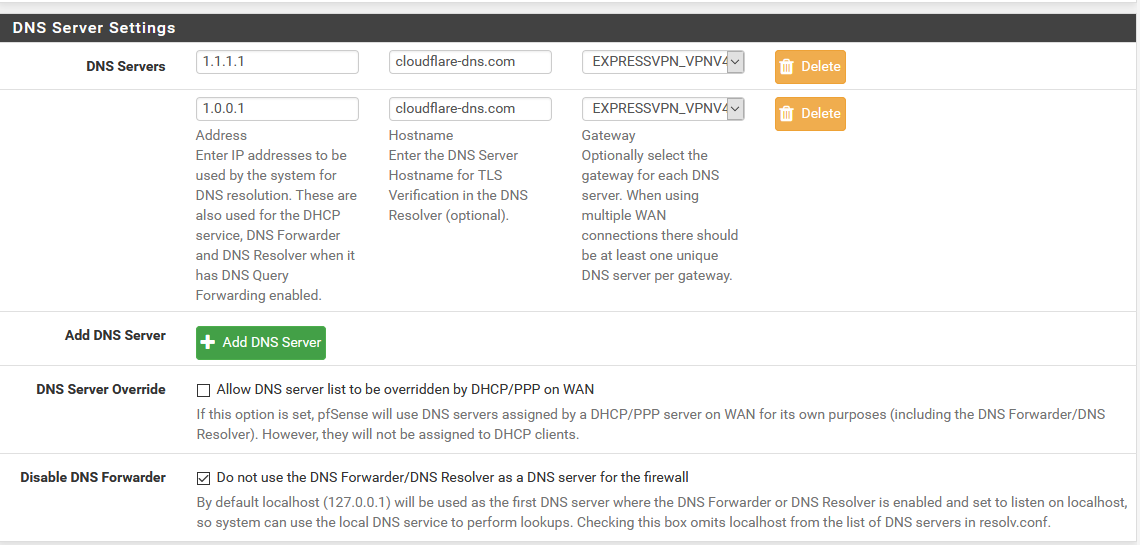
DNS server(s)127.0.0.1 9.9.9.9 149.112.112.112Why is 127.0.0.1 in that list?
If I run this per that article - nslookup isitblocked.org
Results:Server: Name of box
Address: IP address of my pfsense box*** Name of box can't find isitblocked.org: Server failed
Also if I go to Diagnostics -> DNS Lookup
I get the followingName server Query time
127.0.0.1 30 msec
9.9.9.9 7 msec
149.112.112.112 2 msecAgain why 127.0.0.1 ?
Any help would be great on if the above settings are correct?
Then I can move onto some more testing to verify it is working correctly.
-
Again why 127.0.0.1
Do not use the forwarder.I hope this helps, br Krisz
-
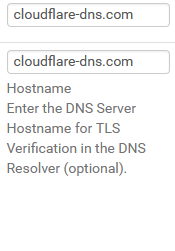
You even wrote this: Use SSL/TLS: Checked
Does Quad9 support DNS over TLS? YES
We do support DNS over TLS on port 853 (the standard) using an auth name of dns.quad9.net.therefore, it is necessary to specify this field: dns.quad9.net
Like:
-
Of course, this is an example from my system, you use your own 9.9.9.9 setting. :-)
-
Ok that fixed that part. Makes sense too after reading on it more.
-
Also if I do an Ipconfig /all on my devices should it be using my pfsense box or the above DNS settings?
-
@cburbs said in Quad9 and DNS Resolver:
Also if I do an Ipconfig /all on my devices should it be using my pfsense box or the above DNS settings?
In your place, situation with this setting, I would only give pfSense to the DNS server, so that your DNS could not leak. (https://www.dnsleaktest.com/)
Or with DHCP, but still only the pfSense box should be the server.Be careful with DHCP server + pfblockerng, create static entries for DHCP
it’s an old story, so you can avoid the unbond of restarting multiple times -
@cburbs said in Quad9 and DNS Resolver:
Static DHCP: unchecked
What I forgot: :-)
if you decide to... and use DHCP on your network, check this as well: Static DHCP: to checked (this is in view of my previous remark) -
So DNS should be pointing to my pfsense box?
When I go to dnsleaktest I Get the following -
207.162.219.52 None Lightpoint Colocation & Hosting LLC Beaverton, United States
66.96.115.176 res100.pdx.rrdns.pch.net. WoodyNet United States
66.96.115.177 res200.pdx.rrdns.pch.net. WoodyNet United States
66.96.115.178 res300.pdx.rrdns.pch.net. WoodyNet United StatesThe last 3 I believe show quad9 is working correctly just not sure why I am getting the top IP which is a Colocation/Hosting place in my area? Why would this one show up?
-
@cburbs said in Quad9 and DNS Resolver:
@DaddyGo
So DNS should be pointing to my pfsense box?
When I go to dnsleaktest I Get the following -
207.162.219.52 None Lightpoint Colocation & Hosting LLC Beaverton, United States
66.96.115.176 res100.pdx.rrdns.pch.net. WoodyNet United States
66.96.115.177 res200.pdx.rrdns.pch.net. WoodyNet United States
66.96.115.178 res300.pdx.rrdns.pch.net. WoodyNet United States
The last 3 I believe show quad9 is working correctly just not sure why I am getting the top IP which is a Colocation/Hosting place in my area? Why would this one show up?You will never see pure 9.9.9.9 DNS resolution, quad9 doesn't have its own network, therefore using CDN, as you can see WoodyNet, so I don't use it for 9.9.9.9 never, hmmmmm (https://www.snbforums.com/threads/cloud9-dns.56918/)
-
So it does seem to be working on that part then.
Do you also use this in your setup?
https://docs.netgate.com/pfsense/en/latest/dns/blocking-dns-queries-to-external-resolvers.html
-
@cburbs said in Quad9 and DNS Resolver:
So it does seem to be working on that part then.
Do you also use this in your setup?There can be many approaches to this theme:
Use what I have already described above for 853 DNSoverTLS + DNSSEC (https://dnssec.vs.uni-due.de/) and then you can also block port 53 on the firewall as a rule.
Don't forget the firewall is blocking all unsolicited traffic by default, this is the rule on pfSense.
Another solution is to use Suricata and/or Snort with ET DNS rules, for example -
Addition: the pfSense is blocked from the WAN side, so if you think about the LAN side you can disable the external DNS query for the clients or as I mentioned ET DNS rules set will be the solution (IPS on LAN)
-
@cburbs said in Quad9 and DNS Resolver:
207.162.219.52
Your first DNS point is suspicious: https://www.reddit.com/r/pihole/comments/efi7u8/google_cloud_openvpnpihole_instance_leads_to_an/
-
Yep but I can't figure out why it is showing up.
-
@cburbs said in Quad9 and DNS Resolver:
Yep but I can't figure out why it is showing up.
This is a typical DNA leak from your OS, I think.
Even if the NIC settings only point to the router in terms of DNS.I had a similar experience with a module of Avast antivirus software that was "trusted sites", if it is enabled then Avast will also connect to its own DNS server to check the sites you visit and of course log your browsings :-).
Do you have similar software on your system? -
No and i get the same results off of my phone.
Also if I switch to cloudfare and run dnsleaktest
IP Hostname ISP Country
172.68.173.29 None Cloudflare Portland, United StatesAlso Do you have any rules under firewal/rules/wan?
-
@cburbs said in Quad9 and DNS Resolver:
172.68.173.29
Try looking in the state table for what is associated with this IP address. (Diagnostics / States / States)
I will be more and more curious....With the settings discussed, the dnsleak test should show something like this....
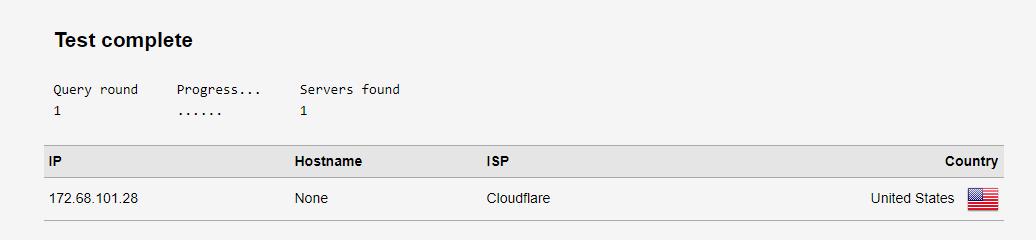
The only difference between the DNS settings of our systems is that I perform DNS queries through a VPN tunnel. (ExpressVPN)
since the datacenter is two blocks away from me and both the Cloudflare and VPN provider ping times are 2 to 4 ms (therefore, DNS over VPN also provides very good speed)BTW, Do you have a VPN?
-
No VPN here just trying to tweak my Pfsense box as a starting point. Lock things down better.
-
@cburbs said in Quad9 and DNS Resolver:
Also Do you have any rules under firewal/rules/wan?
Yeeeepppp is actually the box for that.
to your previous question: Also Do you have any rules under firewal/rules/wan?
- I don't like to load the WAN side with rules, it's like drilling a hole in a sieve, pfSense block all unsolicited traffic on the WAN, so I have more floating rules