Quad9 and DNS Resolver
-
@cburbs said in Quad9 and DNS Resolver:
207.162.219.52
Your first DNS point is suspicious: https://www.reddit.com/r/pihole/comments/efi7u8/google_cloud_openvpnpihole_instance_leads_to_an/
-
Yep but I can't figure out why it is showing up.
-
@cburbs said in Quad9 and DNS Resolver:
Yep but I can't figure out why it is showing up.
This is a typical DNA leak from your OS, I think.
Even if the NIC settings only point to the router in terms of DNS.I had a similar experience with a module of Avast antivirus software that was "trusted sites", if it is enabled then Avast will also connect to its own DNS server to check the sites you visit and of course log your browsings :-).
Do you have similar software on your system? -
No and i get the same results off of my phone.
Also if I switch to cloudfare and run dnsleaktest
IP Hostname ISP Country
172.68.173.29 None Cloudflare Portland, United StatesAlso Do you have any rules under firewal/rules/wan?
-
@cburbs said in Quad9 and DNS Resolver:
172.68.173.29
Try looking in the state table for what is associated with this IP address. (Diagnostics / States / States)
I will be more and more curious....With the settings discussed, the dnsleak test should show something like this....
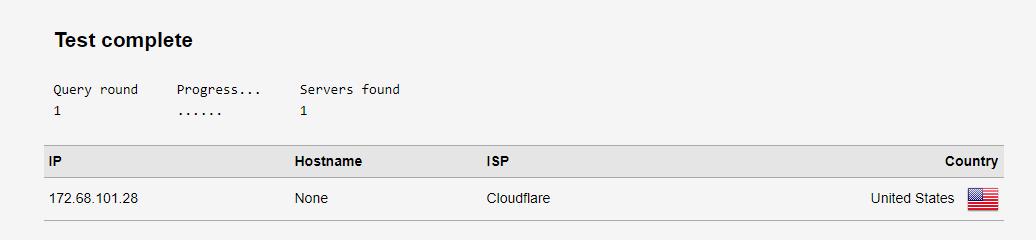
The only difference between the DNS settings of our systems is that I perform DNS queries through a VPN tunnel. (ExpressVPN)
since the datacenter is two blocks away from me and both the Cloudflare and VPN provider ping times are 2 to 4 ms (therefore, DNS over VPN also provides very good speed)BTW, Do you have a VPN?
-
No VPN here just trying to tweak my Pfsense box as a starting point. Lock things down better.
-
@cburbs said in Quad9 and DNS Resolver:
Also Do you have any rules under firewal/rules/wan?
Yeeeepppp is actually the box for that.
to your previous question: Also Do you have any rules under firewal/rules/wan?
- I don't like to load the WAN side with rules, it's like drilling a hole in a sieve, pfSense block all unsolicited traffic on the WAN, so I have more floating rules
-
I have a WAN rule called - Easy Rule: Passed from Firewall log view - says it was created by Easy Rule .
Trying to figure out what it is -
Protocol: IPv4 TCP
Source: ISP IP addres
Destination: 104.25.242.31
Port: 80(HTTP)Destination IP is Carrier: cloudflare
Confused?
-
@cburbs said in Quad9 and DNS Resolver:
Easy Rule
Yes it is, :-).
did you add it this? with this? (https://docs.netgate.com/pfsense/en/latest/firewall/adding-rules-with-easyrule.html) -
It has a date from almost a year ago. Could have as I think that is when I was looking at snort but was having all sorts of issues so I disabled it all.
So I probably don't need that rule - I won't do anything with it now but remove it later today.
-
Do you use squidguard on your system? That was the next thing I was going to implement.
-
@cburbs said in Quad9 and DNS Resolver:
squidguard
I use HA proxy I think for my purposes more appropriate, Squid is problematic among MITM, so SquidGuard doesn't work for me either
But I strongly recommend installing Suricata/Snort and pfblockerNG-devel -
Delete the rule for said http 80 port because it is unnecessary!
I didn’t investigate all the way through, but it points to a Cloudflare CDN -
Yeah snort and pfblocker are on my list. I played with these a while back but it broke many things and haven't got back to them.
-
@cburbs said in Quad9 and DNS Resolver:
Yeah snort and pfblocker are on my list. I played with these a while back but it broke many things and haven't got back to them.
Before you jumping into these IPS / IDS, DNSBL, etc. things, I highly recommend Bill Meeks (alias: bmeeks) posts Snort / ÍSuricata and BBcan177 on the topic of pfblockerng