Setting up a DMZ with a backdoor
-
I'm trying to figure out how to add to a second router (also PFSense) SOLELY for sshing (ok, maybe RDP & VNC too) into the DMZ. The figure below shows the current semi-functional network setup. The design here is that the main router is to be as simple as possible (goal is "just work" for the LAN) and have the DMZ router is the one I'm fussing with. However, I want to be able to ssh into any misbehaving machines on the DMZ...hence the problem!
Disclaimer: While this does have the potential for a loop, the DMZ should NEVER send traffic over the LAN and the LAN should only send SSH (and maybe VNC/RDP if I'm feeling lazy) directly to the DMZ router. So the loop should not be a concern, in theory. This also lets me access the config over the DMZ Router's LAN (which feels better than accessing it over the WAN).
I've tried to find solutions on the forum, but I have not been able to. I believe my firewall rules are correct, but I'm not ruling such config issues out and would be happy to share if requested. I'm not sure if this falls under "multi-wan" as it's two separate routers, but the DMZ is not assigning DHCP nor providing and internet/network access (beyond ssh for it's own 10.1.x.x/16) to the LAN
Thanks for the help in advance :)
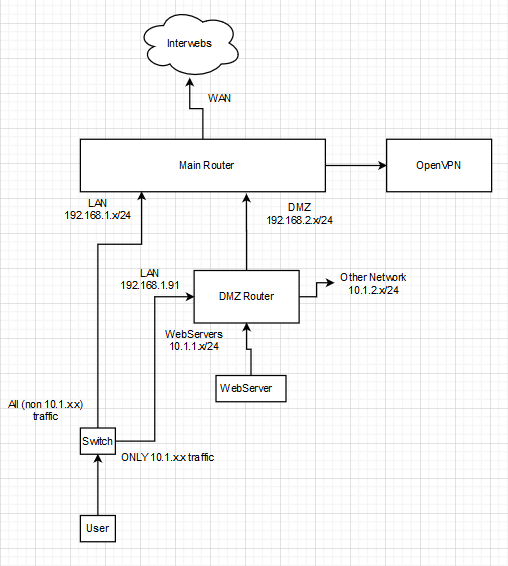
Note: Currently the LAN can access the internet & DMZ can be accessed from the internet. However LAN can neither access DMZ over SSH (through the back path, so to speak) or access DMZ over http(s) over the main router.
Edit #1: Updated picture per comment.
-
Things are not clear. It looks like you must have a switch in there somewhere?
The box labelled user, is that host with dual NICs? Dual IP addresses? (two subnets i one segment?
The DMZ router has 4 interfaces? Two appear to be in the same subnet if it's 10.1.0.0/16.
How exactly are you trying to test from the LAN host? What IP are you trying to access in the DMZ?
The problem here is almost certainly an asymmetric routing issue:
https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-due-to-asymmetric-routing.htmlDo you see blocked traffic in the firewall on either device when trying to connect?
Steve
-
Thanks for the reply Steve :)
Good catch! I left off a switch sitting between the user and the Main router. I will update drawing shortly. User is single port device, both routers are multiport devices.
From LAN, I am trying to ssh to an IP in the 10.1 space (say 10.1.1.10) by using the 10.1 address. I do not see any blocked data regarding 10.1.1.10 on either firewall log (just searching for that IP in the log).
From the link you posted it seems that asymetrical is defined as "traffic going from A-> Z taking a different route then traffic going from Z -> A" My thought is that 10.1 traffic would go through the 192.168.1.99 port on the DMZ router, not going to the main router at all. This would be the same route that I would expect the traffic to take back. So I'm missing why it would be asymmetrical >_<
Edit: Picture is updated.
-
This post is deleted!