2 LB WANs and 2 LANs. Hosts on LAN1 can ping hosts on LAN2, but not vice versa
-
Hey guys, I've been trying to figure out why I'm unable to pings hosts between both LANs given the simple rules I have setup.
First, here's a simple diagram of my network:
The seedbox can ping the 10.0.1.1 gateway on the main LAN just fine, as well as any hosts on it.
Hosts on the main LAN can ping the 10.0.3.1 gateway the seedbox in on, but they can't ping the seedbox itself.
Here are all my interfaces:
My 2 WAN gateways:
And my gateway group containing my two WANs:
My LAN rules:
And my seedbox network rules:
Note that in both cases, the Gateway is my MultiWAN group. Could that be the issue?
Both LANs are allowing all traffic from that source to go anywhere, so I'm not seeing what is blocking pings from the main LAN from reaching the /30 subnet with the seedbox on it.
The seedbox is a Windows machine and yes, I did change the firewall config to allow it to respond to pings from any ip address, not just ones in it's own subnet.
Any ideas?
-
@pclausen What happens when you remove the MultiWAN gateway from all of the firewall rules? You should not need to explicitly define that unless you are doing policy based routing.
-
^ Exactly, And if you do want to allow network/vlan X to get to network/vlan Y - then you need to allow that before you shove traffic out a gateway.
There is no reason to shove traffic out a specific gateway like that - unless you have need to policy route it out a specific gateway..
-
Appreciate the feedback. Removing the MultiWan gateway from all my firewall rules does indeed resolve the issue. I can now ping it from any host in my main LAN, and I can establish a RDP session to the server.
However, it also means that I loose my WAN load balancing. When I run speed test now, I'm only getting half the speed I was before since all traffic goes through WAN1. If I run 2 speed tests concurrently to different servers, they both still only use WAN1.
Prior to removing the MultiWan as the gateway on my firewall rules, running just a single instance of speed test would perfectly balance the load across both WAN1 and WAN2 and max out the available bandwidth of both.
So I changed back to setting the MultiWan as the gateway on my LAN interfaces, but added a new up at the top of the list to allow traffic between LANs using the default gateway as follows:
And:
Now both WANs are being fully utilized during speed test (and of course other activities), AND I can get to hosts on my various local sub-nets.
Is there's a simpler way to achieve WAN load-balancing without changing away from the default gateway, I'd be interested in knowing, but adding the direct LAN to LAN rules at the top of each interface does the trick.
-
@pclausen A simpler approach would be to create an Alias group (Firewalls -> Aliases) that includes all of the subnets for your local networks. Then in the rule where you're specifying the MultiWan, set the destination to "Invert Match" and use "Single host or alias" as the destination and in the field beside that enter the name of the alias group you created for your internal networks.
-
@Cmdrd I must not be quite following. So I created this Alias group:
And I changed these two rules containing the MultiWan gateway as follows:
And:
I then disabled the rule at the top of each list that I created last night to allow allow traffic between LANs using the default gateway.
But now I'm no longer able to ping the seedbox from the LAN subnet.
I should note that I had a RDP session going to my seedbox while doing this that remained working, but I guess perhaps since that was an active session already, changing rules "on the fly" does not result in such sessions being dropped?
-
@pclausen said in 2 LB WANs and 2 LANs. Hosts on LAN1 can ping hosts on LAN2, but not vice versa:
rules "on the fly" does not result in such sessions being dropped?
Active states are not killed on firewall rule changes no.. You would have to kill any active states, or they would have to time out on their own for the new rules to be evaluated for the new sessions.
But you should not have to force traffic out a gateway for load balancing to work.. What do you have setup in you gateways for default?
https://docs.netgate.com/pfsense/en/latest/book/multiwan/load-balancing-and-failover.html
Post your gateway listing under routing. You prob single gateway being used for default
-
@johnpoz Thanks for confirming active states are not killed on firewall rule changes. Makes sense.
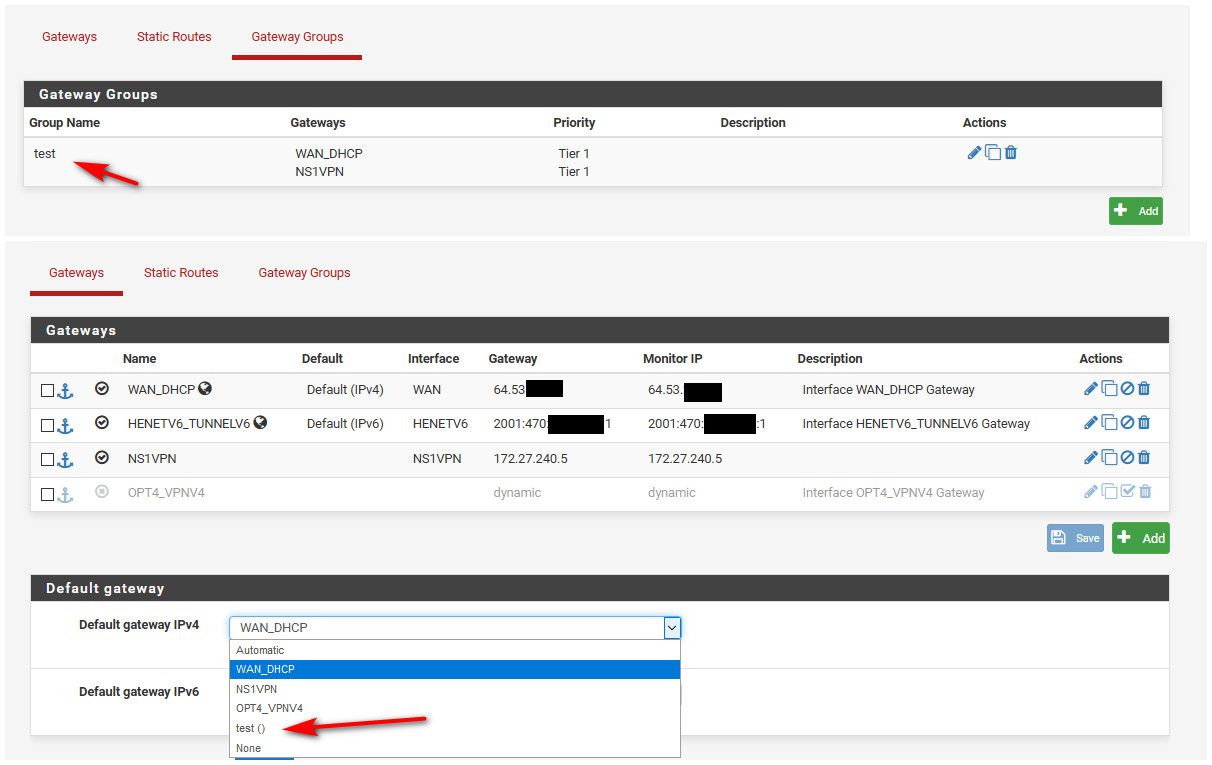
So here are my current gateway group and gateway settings:
And the LAN firewall rule (circled in red) that makes load-balancing work:
Thanks for the link to the official documentation on WAN load balancing. I noticed that they state the following at the start:
"The group itself does not cause any action to be taken, but when the group is used later, such as in policy routing firewall rules, it defines how the items utilizing the group will behave."
Does that not imply that the gateway group needs to be used in firewall rules (like I am) to become effective?
I also noticed they recommend setting up 3 groups as follows in a dual WAN load-balance scenario:
I have found that with just one group defined as shown above, I can disconnect either WAN interface and all traffic automatically starts routing through the remaining active WAN interface, so I'm not sure what the advantage would be to have 3 gateway groups?
Could it be that the reason my traffic is routed out the active WAN is the LAN firewall rule that includes the MultiWAN gateway?
-
@pclausen said in 2 LB WANs and 2 LANs. Hosts on LAN1 can ping hosts on LAN2, but not vice versa:
so I'm not sure what the advantage would be to have 3 gateway groups?
For policy routing..
If your group is set as the default in the gateway section, you should not have to policy route it by placing gateway on the rule. But you could then policy route other traffic you wanted to use a specific gateway and not load balance, etc.