Help with my pfsense + unifi AP setup
-
I'm trying to setup a new home network using pfsense and a unifi AP nanoHD access point and I think I'm missing some important or obvious steps to get my access point going... here's what I'm working with:
Fitlet2 mini-pc with 4 NIC ports:
-"Eth1" port = wan = igb2 = disconnected (haven't connected to modem yet)
-"Eth2" port = opt1 = igb1 = disconnected
-Facet 2 added LAN "left" port = opt1 = LAN = igb0 = connected to LAN port of desktop PC
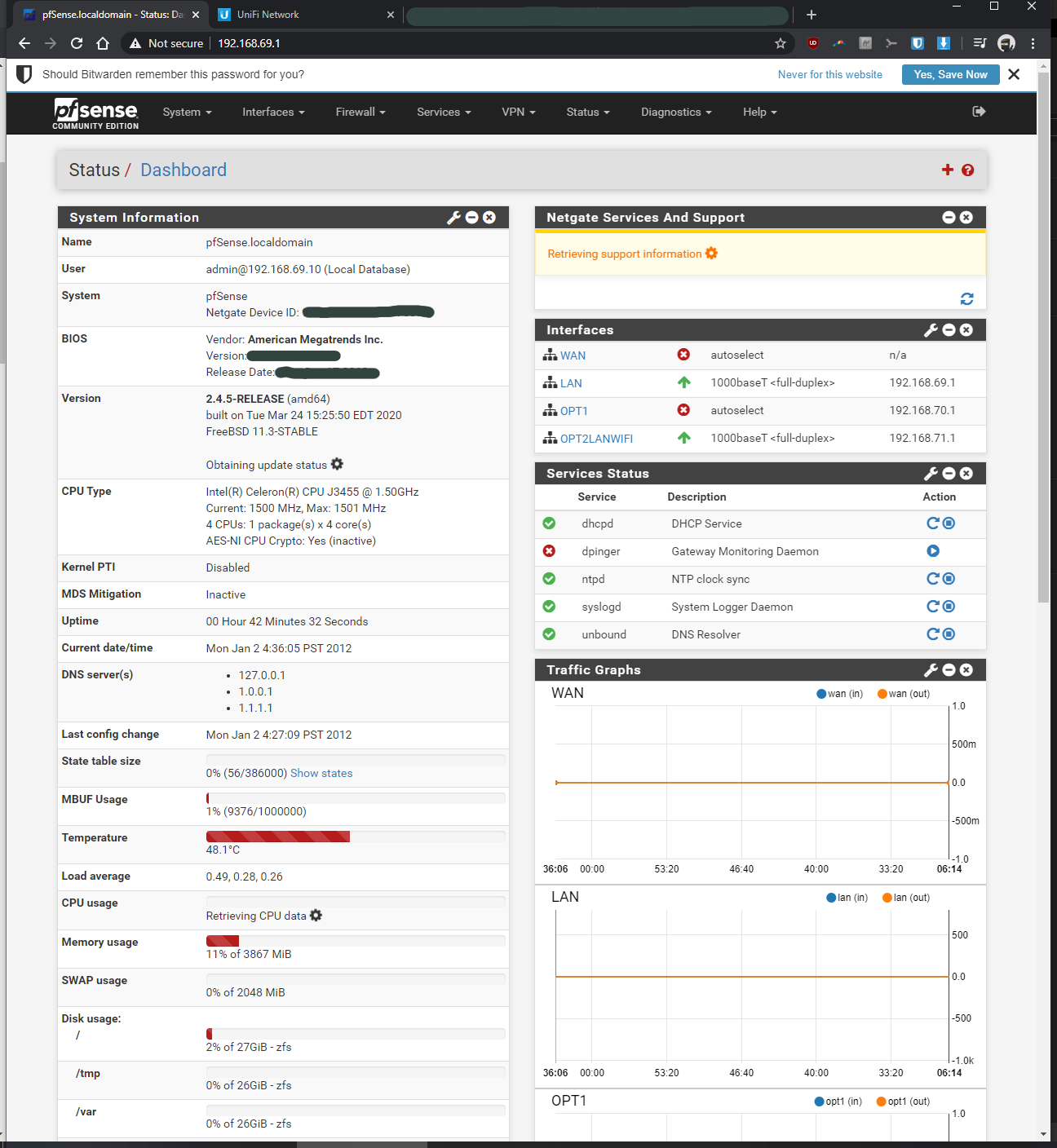
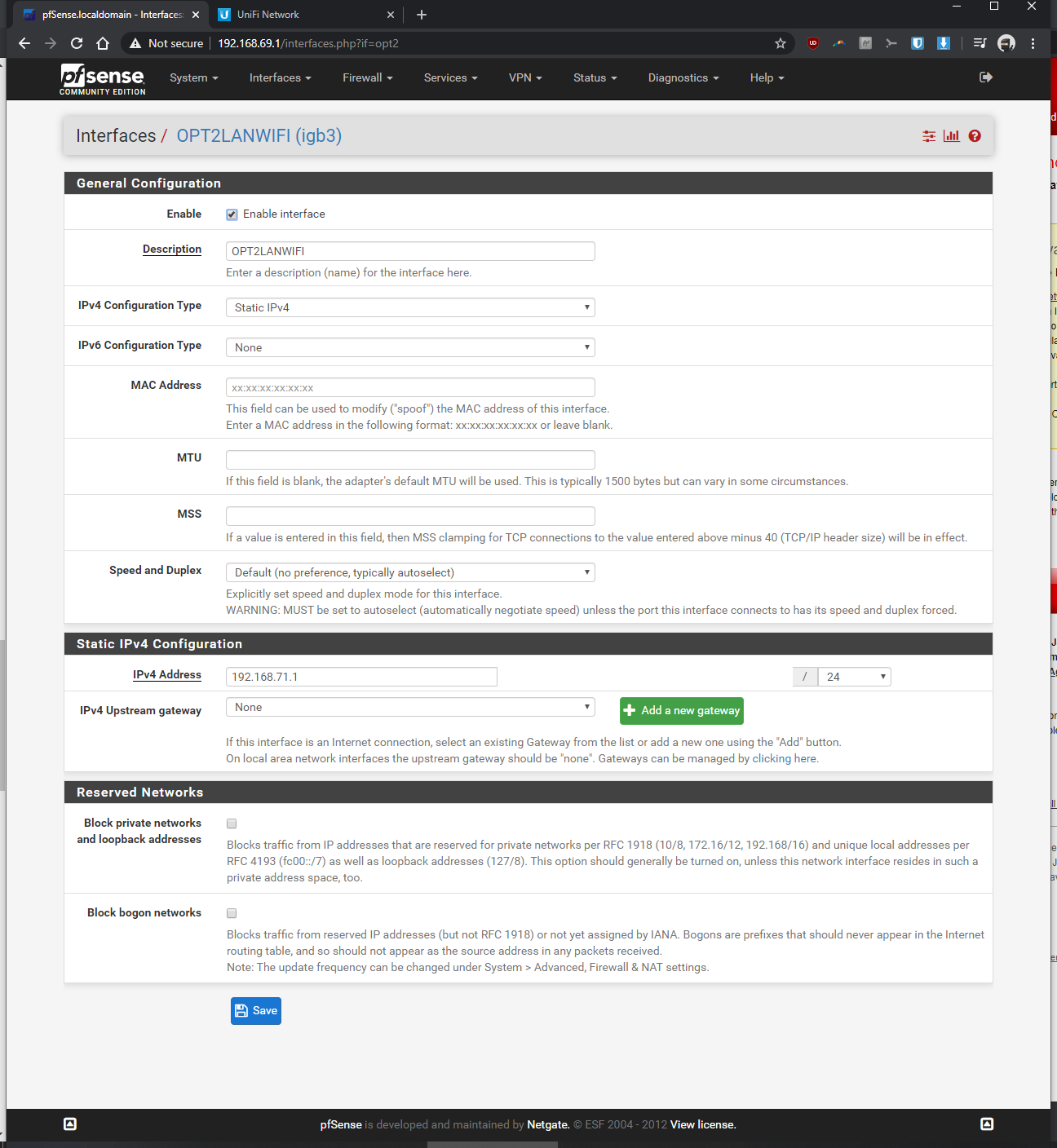
-Facet 2 added LAN "right" port = opt2= LAN = igb3 = connected to Unifi AP nanoHDI've installed pfsense on the fitlet2 PC (with the 3 bios settings disabled as required for this mini pc) and can login into the pfsense accnt thru the desktop PC (LAN igb0) and static IP address of the fitlet2 PC.
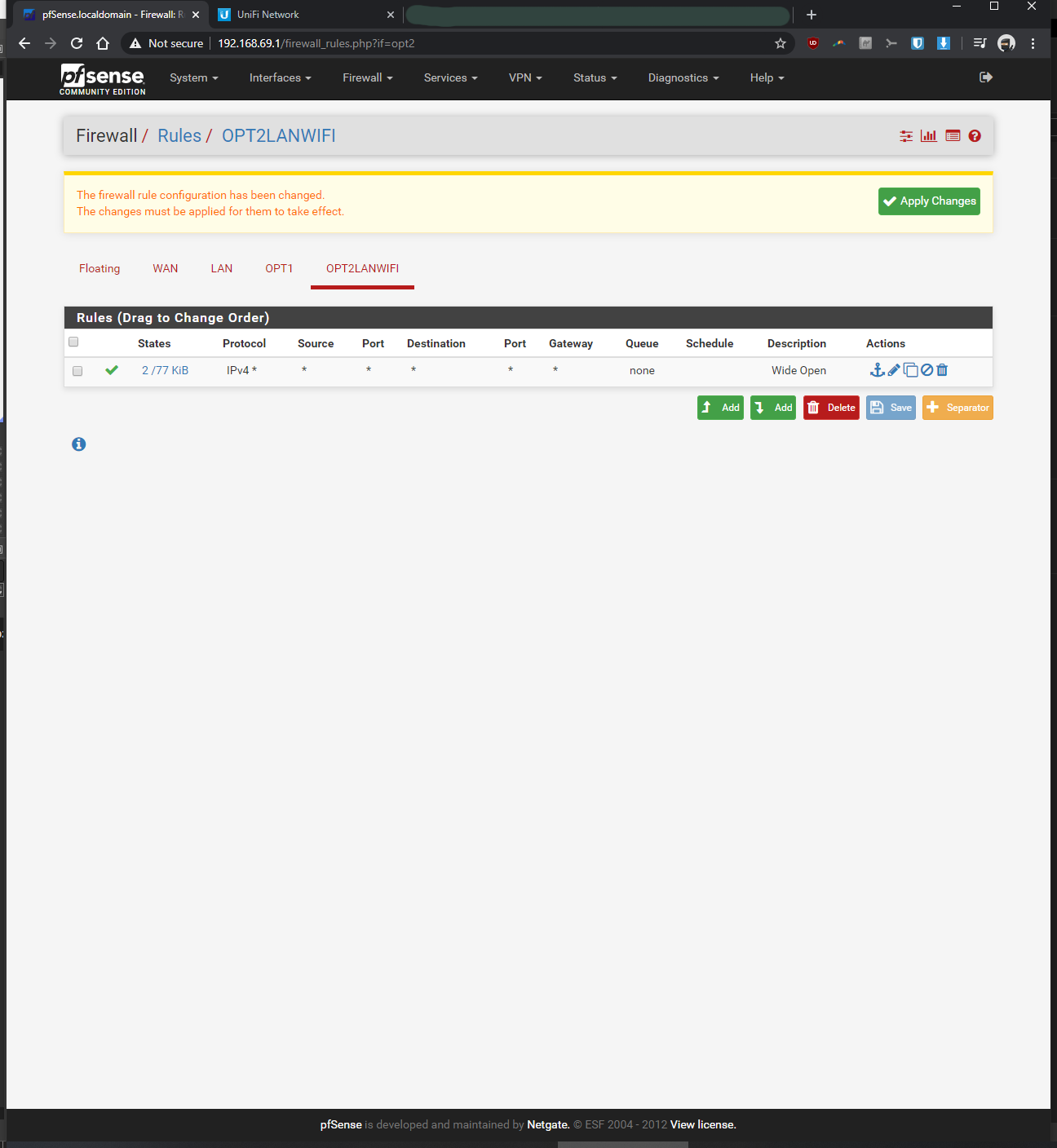
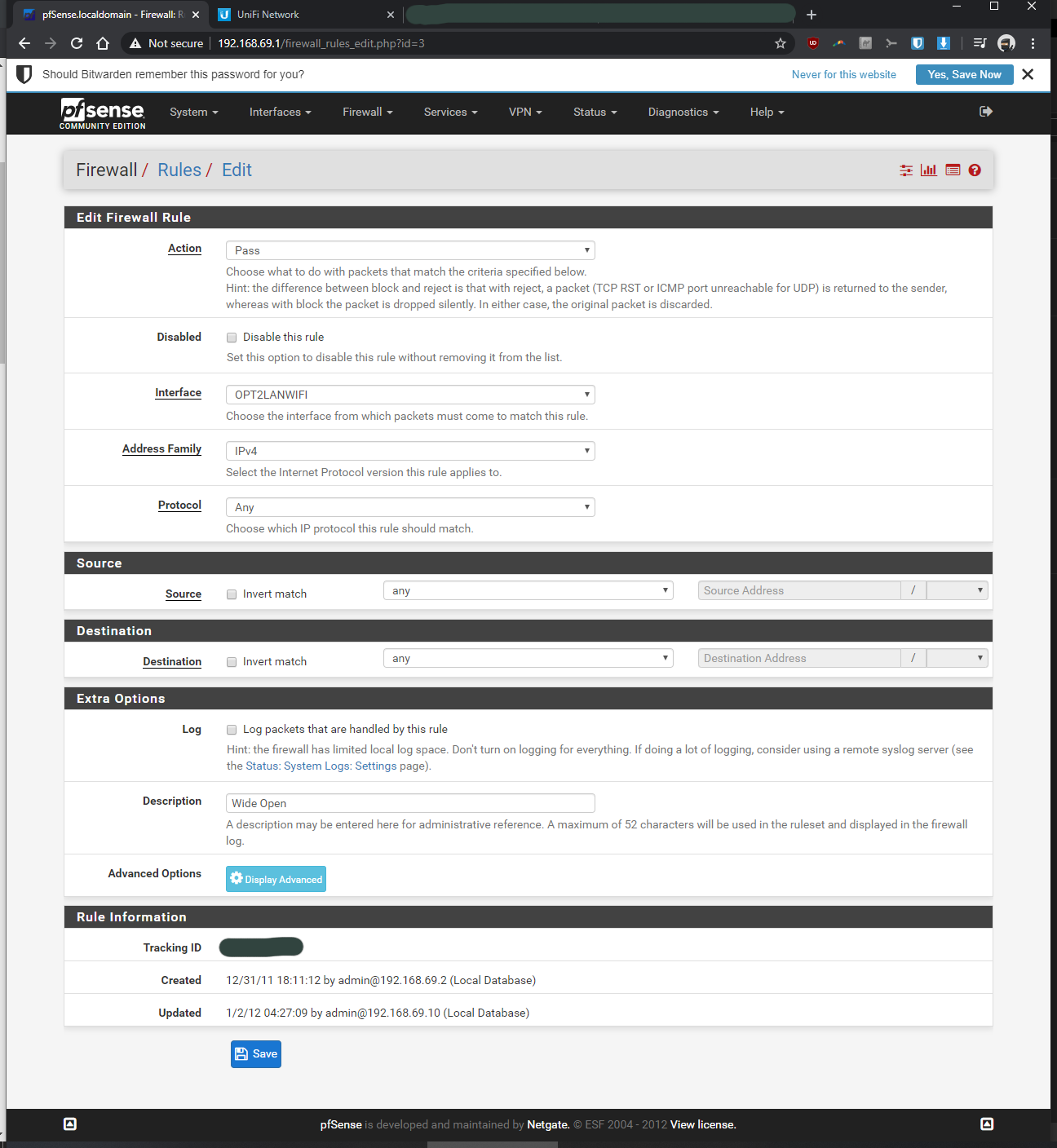
I've physically/directly connected the nanoHD to opt2 and setup a firewall rule to pass all (action "pass" and protocol "any" for OPT2 in Firewall > Rules > OPT2)
I've got the Unifi controller software installed on my desktop PC (connected via ethernet on igb0), but when i go to "devices" within the Unifi controller, I don't see the access point. I've also tried the android mobile app on my phone to setup the nanoHD (underneath standalone devices where it appears), but when I click on it while its physically connected to the pfsense mini pc, I get an error (couldn't connect to the device, retry error)). I know the access point works fine because it works as it should when I connect it to my pre-existing home network/router that I'm trying to replace. I'm not totally clear on the purpose of the Unifi Network controller honestly and why I can't seem to just setup the access point thru the android mobile app as a standalone device, like I've done successfully with an Access Point Pro that's currently on my existing/current running home network.
I'm wondering if the pfense mini PC is really assigning an IP address to the nanoHD.
I've been watching hours of youtube videos and I'm stuck. I've tried reinstalling pfsense completely on the mini PC once as well. I've tried the reset button on the nanoHD a couple times. Thanks for your help in advance.
My goals are to:
- Get the access point working first of all...
- Setting up internal LAN wifi thru this access point
- Setting a guest wifi with limited access to internal LAN wifi thru this access point
- Setup PIA VPN (with all connections going thru VPN as default, killswitch if VPN is off, and select devices that don't go thru VPN)
-
I setup a 2nd computer (Dell Optiplex 9010 w/ intel gig 4 port nic) to try instead the Fitlet2 and running into the same problem. What am I missing here?
-
Check Status > DHCP leases to make sure the AP is pulling an IP address from pfSense.
The issue here is that by default the AP tries to find the controller in the same subnet but because you have put it on a different interface you need to tell it the IP address if the controller.
Two ways I'm aware of to do this:
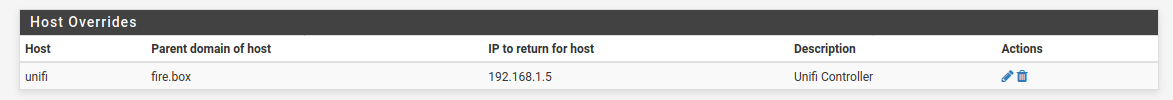
You can SSH to the AP and edit the config file there to include a line for the unifi controller.You can add a host override for
unifiin the pfSense DNS resolver and set that for the address of the controller. The AP will try to resolve it and then find the controller as long as you have firewall rules to allow it. Which you do as long as you apply those changes.Steve
-
Thank you for the reply.
It sounds more complicated than I thought.
Would using a Unifi Switch 8 fix my issue? Would I just connect this switch to one of the pfsense computer's LAN ports, then connect the AP & the desktop PC to the that switch?
If that's the case, I guess I didn't need to buy the Facet add-on card for the Fitlet2 to add 2additional ports (4 total) to the Fitlet2 & could have just the 2 ports it came with (1 Wan, 1 LAN).
-
@rogerkamp8817
Extra ports on the PFSense box provides you different networks, so if your goal is to have the wireless on a different network from the desktops, that it will do. But the controller software and access points need to be on the same network by default. Otherwise, as stephenw10 said, you would need a host override in PFSense DNS to 'direct' the AP to the controller computer. I just setup my new AC PRO yesterday and yep, my controller computer is on a different vlan from the AP. I use Microsoft DNS servers and setup their version of a host override on DNS and it worked great. In your case, it sounds like a switch might be the way to go.
I just took a look at the PFSense host override setting and it looks like you need to set a static IP on the computer, then set the host override on the DNS Resolver/General Settings page. Fill in the computer name, domain name ("local" if not on a domain) and IP, then below the additional name of 'unifi'. That should work. You might want to give it a try. But if having different networks is not the goal here, getting a switch is probably a better way to go overall. It does not need to be a Ubiquity switch BTW. I use Netgear switches and have been very happy with them. -
As others have mentioned there are many ways to get the L3 adoption to work.. When your going to put the controller on different L2 than the AP... You have to use L3 adoption.
https://help.ui.com/hc/en-us/articles/204909754-UniFi-Device-Adoption-Methods-for-Remote-UniFi-Controllers
But its much easier to put the controller on the same L2.. If you need a switch to do that, they are cheap.. It does not have to be unifi.. Any smart switch will work, if your going to run AP that can do vlans, its just stupid to not get a switch that can also do them... A smart 8 port gig switch can be hand for like $40.. just stay away from tplink.. They should have it fixed by now, but their low end didn't actually do vlans.. they wouldn't let you remove vlan 1 from ports..
-
Thanks guys, this is a great community. I'm learning as I go and the explanations are very helpful.
I have a "Ubiquiti UniFi Switch 8 US-8-60W 8-Port Gigabit Ethernet Managed Switch" on the way. I plan to do vlans.
-
I'm playing with what I've got for now as I wait for the new switch. I'm having some issues connecting to my pfsense gateway thru my existing router. Here's how I've got it connected:
-modem to WAN port of pfsense machine (pulling public IP fine & internet working on my devices)
-LAN port (192.168.69.1, see earlier post screenshot #1) of the pfsense PC is connected to WAN port of Asus router (current router)
-Asus router has wifi enabled, with a gateway IP address of 192.168.50.1 and seems to be an IP of 192.168.69.12 from the pfsense machine (wifi works fine and devices connected to this wifi can connect to the internet)
-Unifi AC pro connected to a LAN port off the Asus router (this wifi connects fine to Asus gateway 192.168.50.1 and internet)After I got all this connected, I was intermittently able to connect to the pfsense gateway (192.168.69.1) thru my wifi devices (connected to Asus or Unifi AC Pro wifi). Now, it doesn't seem like I can connect to the pfsense gateway (192.168.69.1) at all thru my wifi devices. Any advice on how I can access the pfsense gateway?
Thanks in advance!
-
You will want to use your Asus router in access point mode if it has that. Alternatively do this:
https://docs.netgate.com/pfsense/en/latest/wireless/use-an-existing-wireless-router-with-pfsense.htmlAdding a host override to use the Unifi controller is pretty easy. Go to Services > DNS Resolver. Add a new override something like:
You probably want the UAP connected directly to pfSense to make sure it's not using the Asus for DNS which may or may not pass that request to pfSense.
Steve
-
I switched my Asus router to access point, but now i can't seem to access its gateway (192.168.50.1) and my IP addresses for my clients are coming from the pfsense. I'd like to maintain access to the Asus gateway and use other features of the Asus router for now (VPN, etc.) and I'm sure i can undo this change (connecting LAN cable to a computer to, going back to the Asus gateway and changing it back to router mode).
If i did the 2nd option, what would I enter for:
Parent domain to host?
IP to return to house (IP address of the Asus router or IP address of the LAN port the Asus router is connected to on the pfsense box?)? -
If the router is in trues Access Point mode it will no longer have a second subnet. It will only have an IP in the subnet it's connecting to, 192.168.69.0/24 in this case.
If you leave the Asus in router mode and have the UAP behind it the UAP will probably be using the Asus for DNS. The Asus may forward requests to pfSense or not. To be sure you would want to put the host override in the Asus config.
The domain used in the host override is usually the default domain pfSense is using. That domain is passed to dhcp clients to use for lookup so the UAP tries to resolve unifi.localdomain or whatever domain is passed to it.Steve
-
I was able to change my Asus router from AP mode back to router mode. I will keep the Unifi AP unplugged for now to remove that from the equation and just use the wifi from my Asus router.
How can I access my pfsense gateway (192.168.69.1) thru a client (192.168.50.X) connected to the Asus router/wifi (192.168.50.1)?
I've tried:
Services > DNS Resolver > added Host override using:
Host: pfSense (same as System> general setup > host)
Domain: localdomain (from System > general setup > domain)
IP to return for host: 192.168.69.1 (is this correct?)When I punch in 192.168.69.1 on a client (connected thru the Asus router as 192.168.50.X), I can't get to the pfsense gateway (192.168.69.1). I can get to the Asus router gateway just fine (192.168.50.1).
Thanks for the patience. I'm sure I'm over complicating this with 2 routers running together. I dont want the pfense to assign IP's yet because various clients have been assigned static IP's my Asus router and I don't want to mess this setup up for now (i.e., wifi printers that were a pain for me to configure).
-
If the Asus is in router mode it should be connected to pfSense via it's WAN port. In that setup you should be able to access the pfSense webgui at it's LAN IP, 192.168.69.1, without making any changes in pfSense.
Is the Asus pulling an IP from pfSense on it's WAN via DHCP? Or is it set statically in that subnet correctly?
Steve
-
Connecting to the pfsense gateway thru a device connected to the Asus would work on some device but not others. Weird... The Asus seems to have better speed and range on the 2.4Ghz band than both the nanoHD and the Pro AP's.
I received the Unifi Switch 8 and have the nanoHD connected to it now. Currently experimenting on this separate network w/ a few devices then will transitioning most if not all devices onto it.
-
I'm having some issues getting my WLAN clients to ping to my wireless VLAN clients network... I suspect it has something to do with how the vlan and the unifi switch 8 is talking to each other (conflicting firewall rules or how vlan is being separated from main WLAN?). Here's what I'm doing:
-Using pfsense (192.168.69.1, igb0, default "LAN"port), connected to Unifi switch 8 (port 1), connected to Unifi nanoHD access point (POE port 5)
-Regular WLAN and VLAN both being broadcasted by the same nanoHD
-Raspberry pi 4b as a Unifi controller is connected to Unifiswitch port 8 as 192.168.69.2
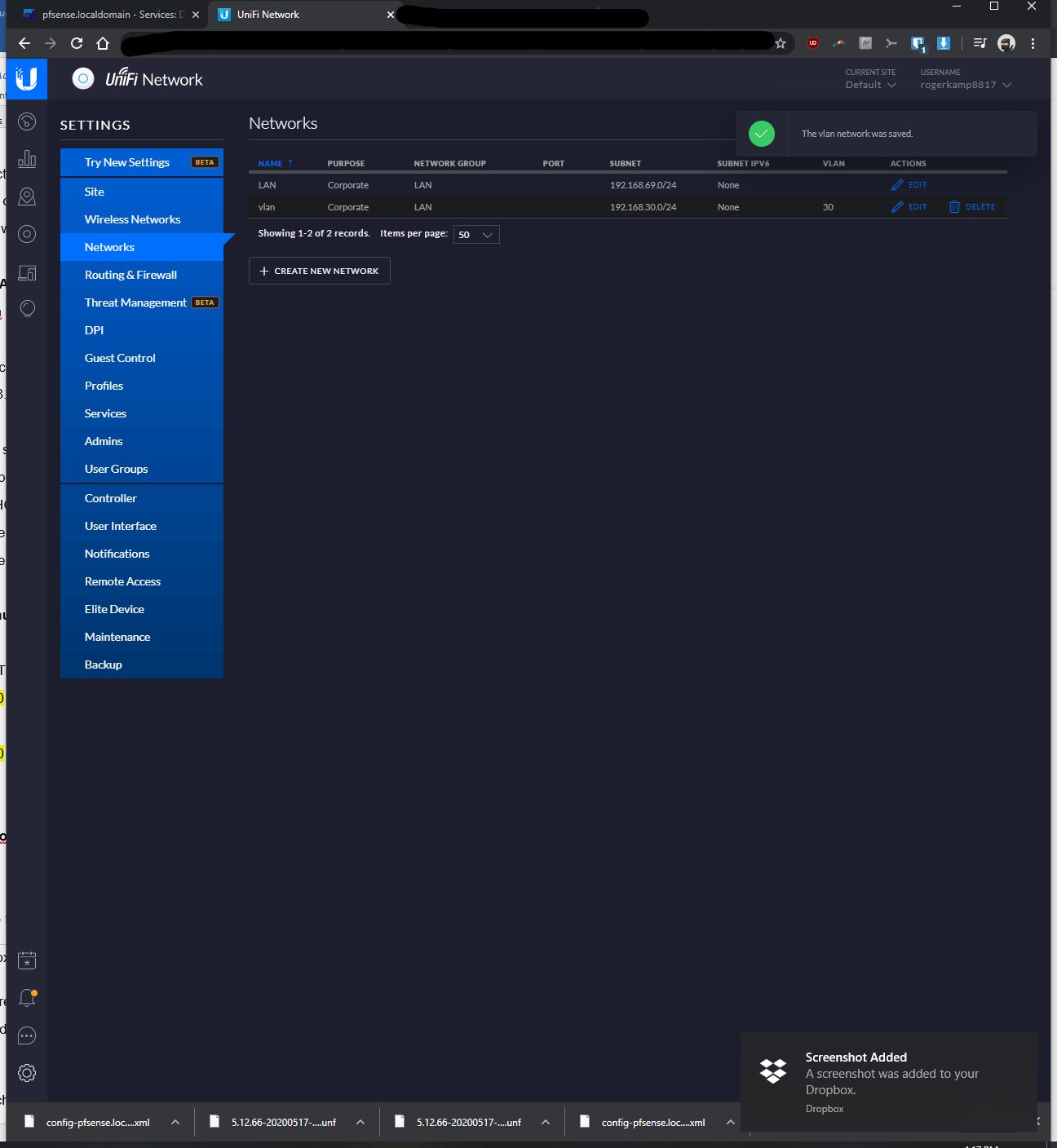
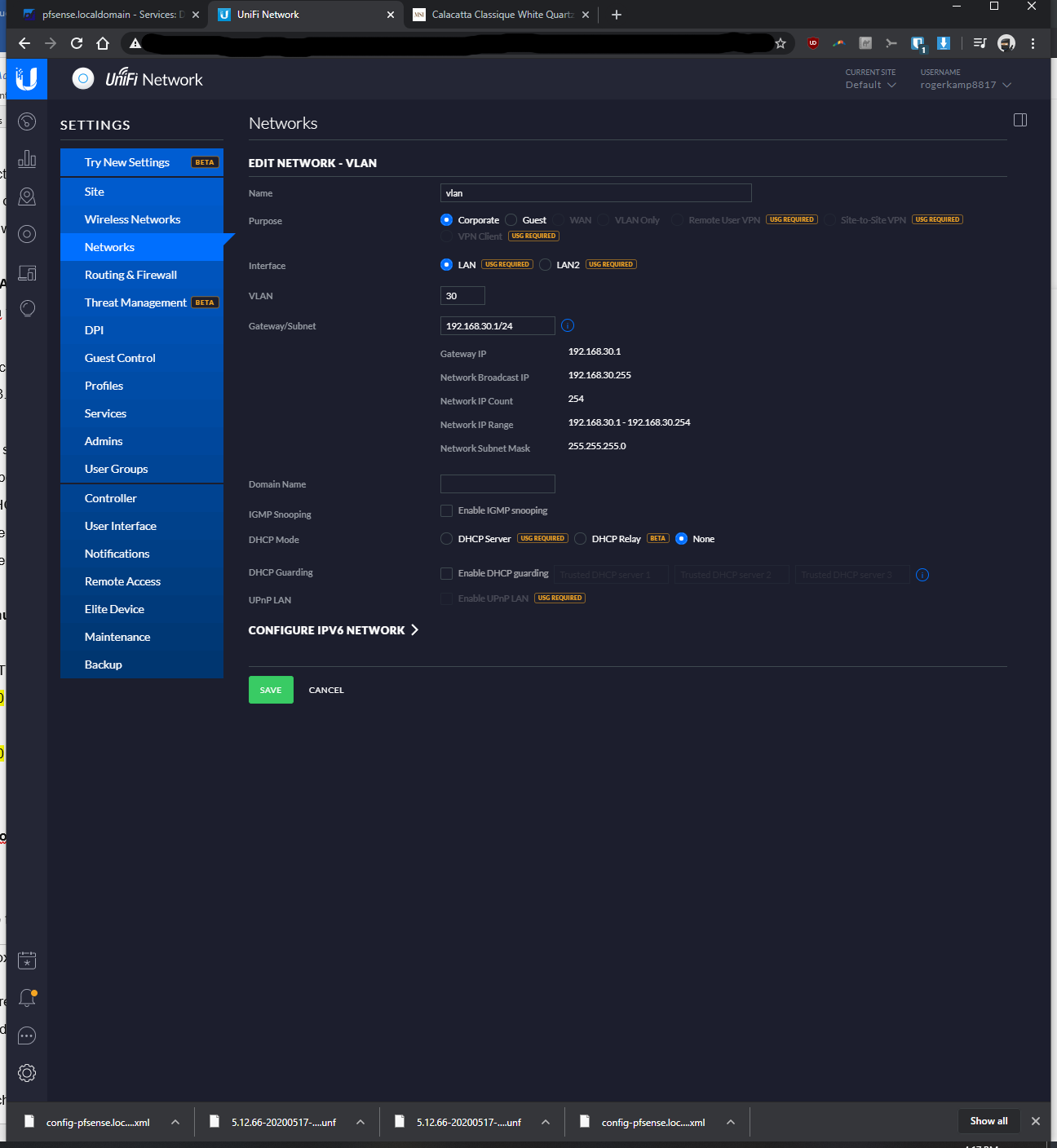
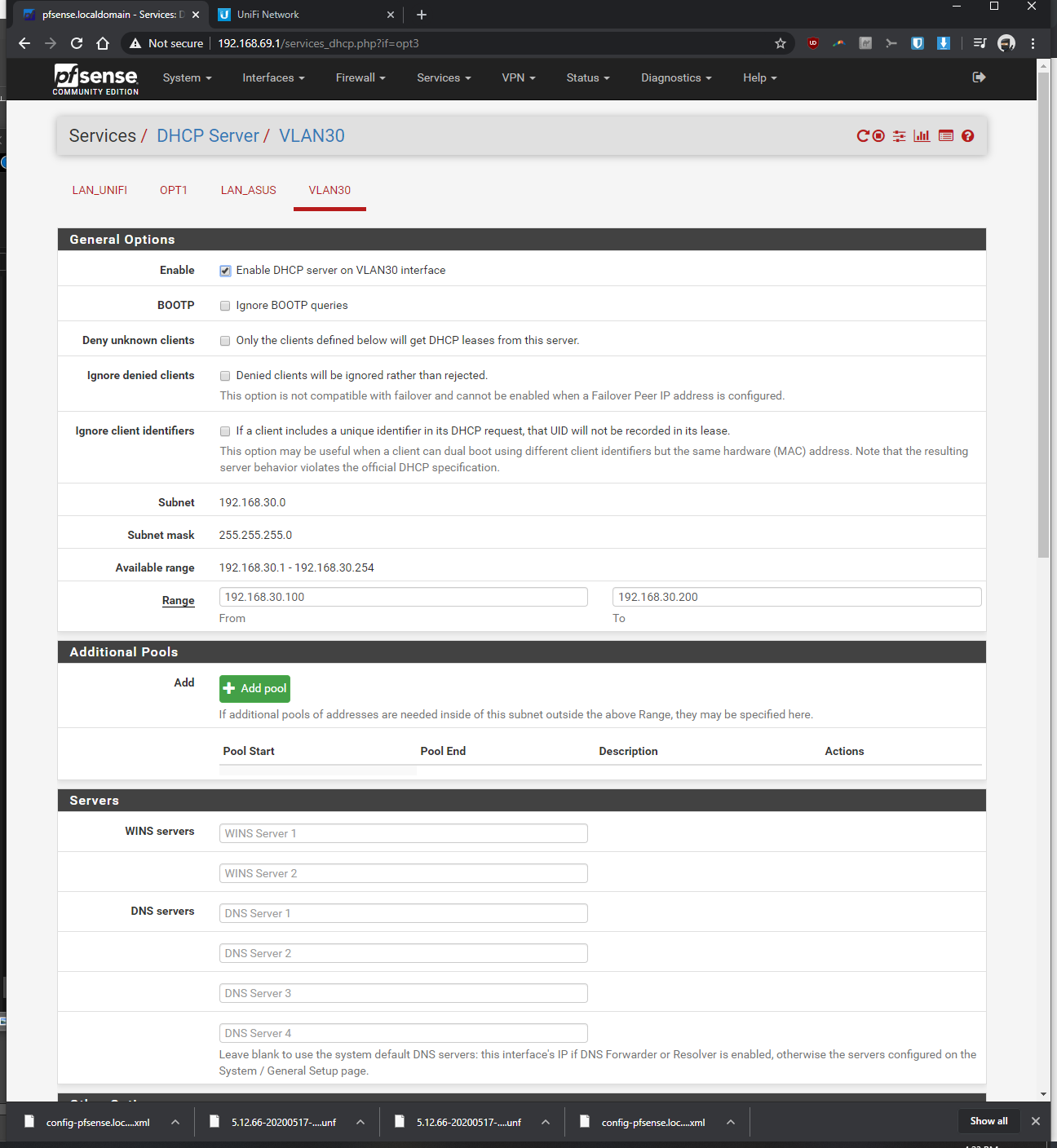
-I'd like the pfsense to assign IP's and not the Unifi switch 8In pfsense, I've setup a vlan as follows:
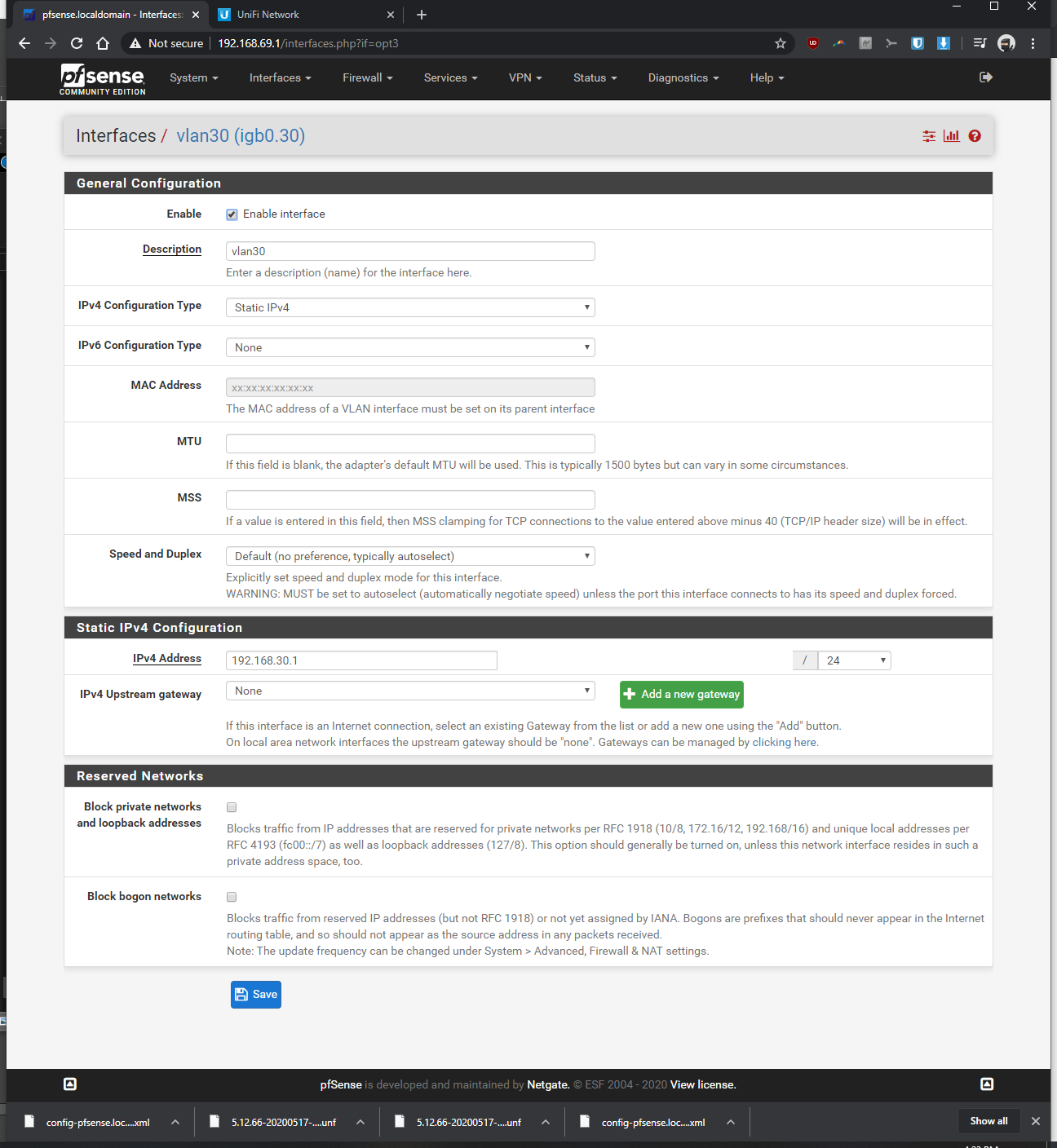
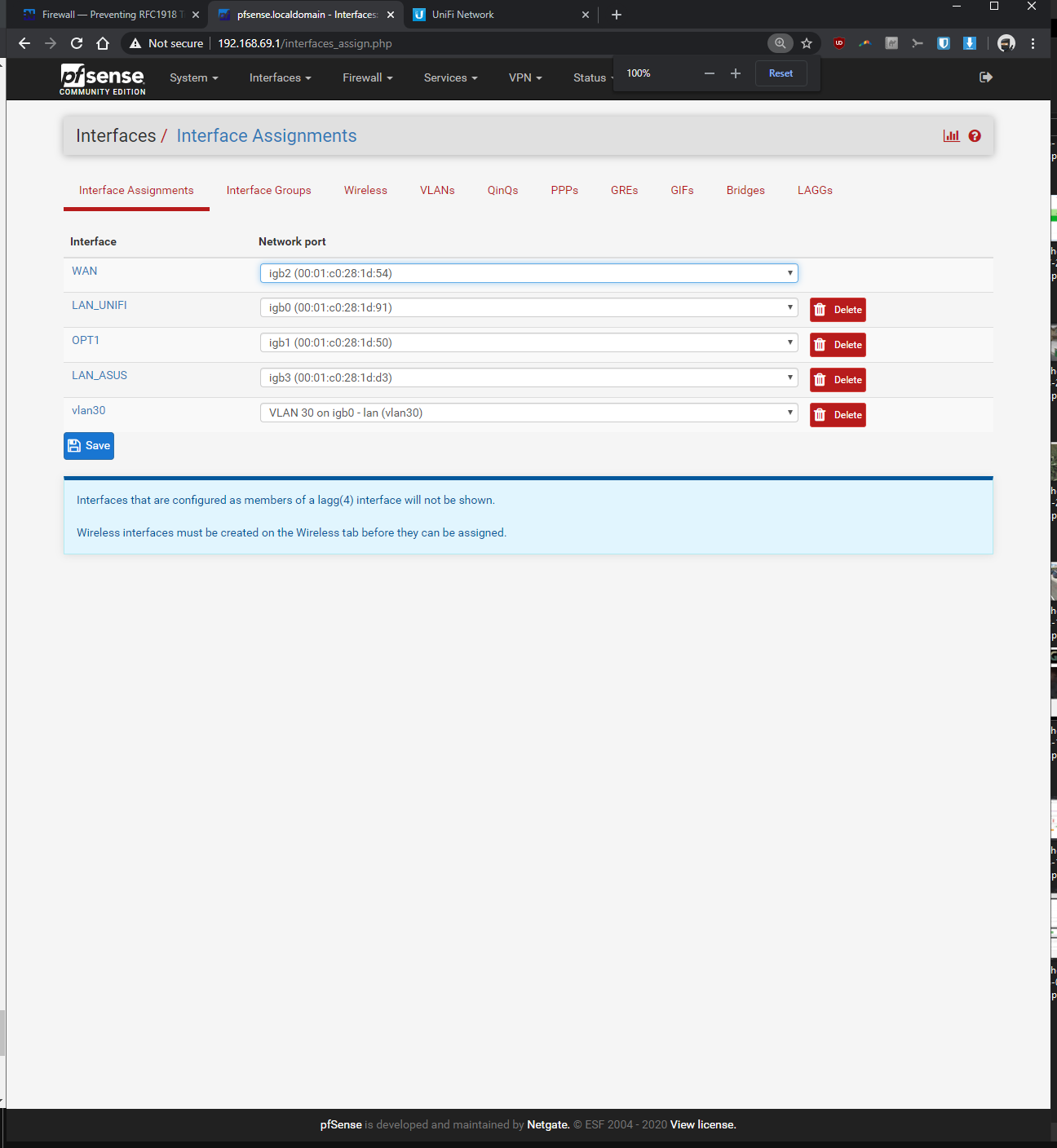
-Interfaces > interface assignments > vlans > vlan config: parent interface igb0 (same port unifi switch is plugged into), vlan tag: 30, vlan priority 0 (default), description: vlan30 > saved
-Interfaces > assignments > assigned VLAN30 to new OPT and renamed it, enabled it, static ipv4 of 192.168.30.1 / 24, saved
-Services > DHCP server > VLAN30 > enabled yes > range from 192.168.30.100 to 192.168.30.200, saved
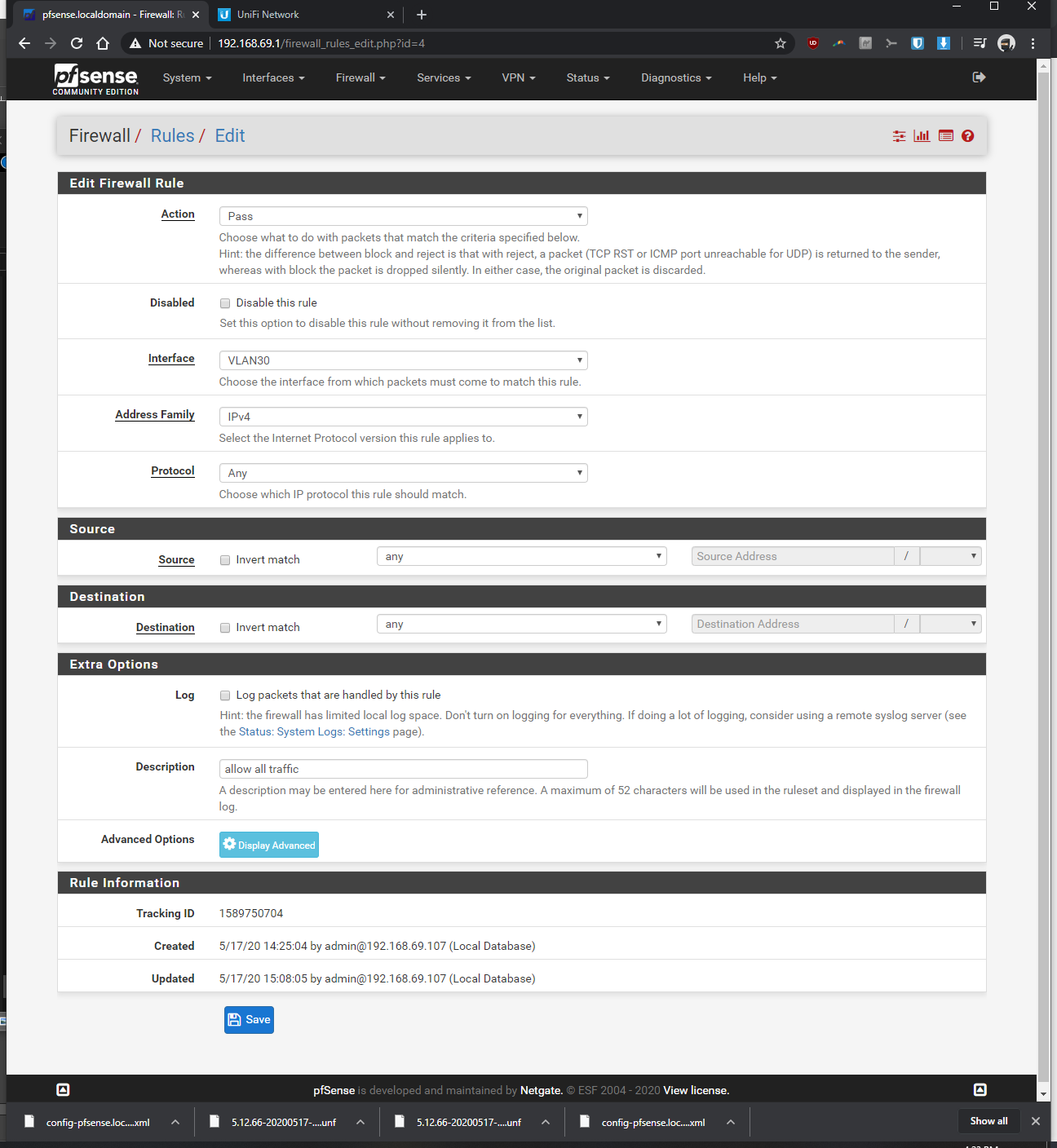
-Firewall > Rules > VLAN30> pass, interface vlan30, any, any, anyIn the Rpi4b Unifi Controller (192.168.69.2 static)
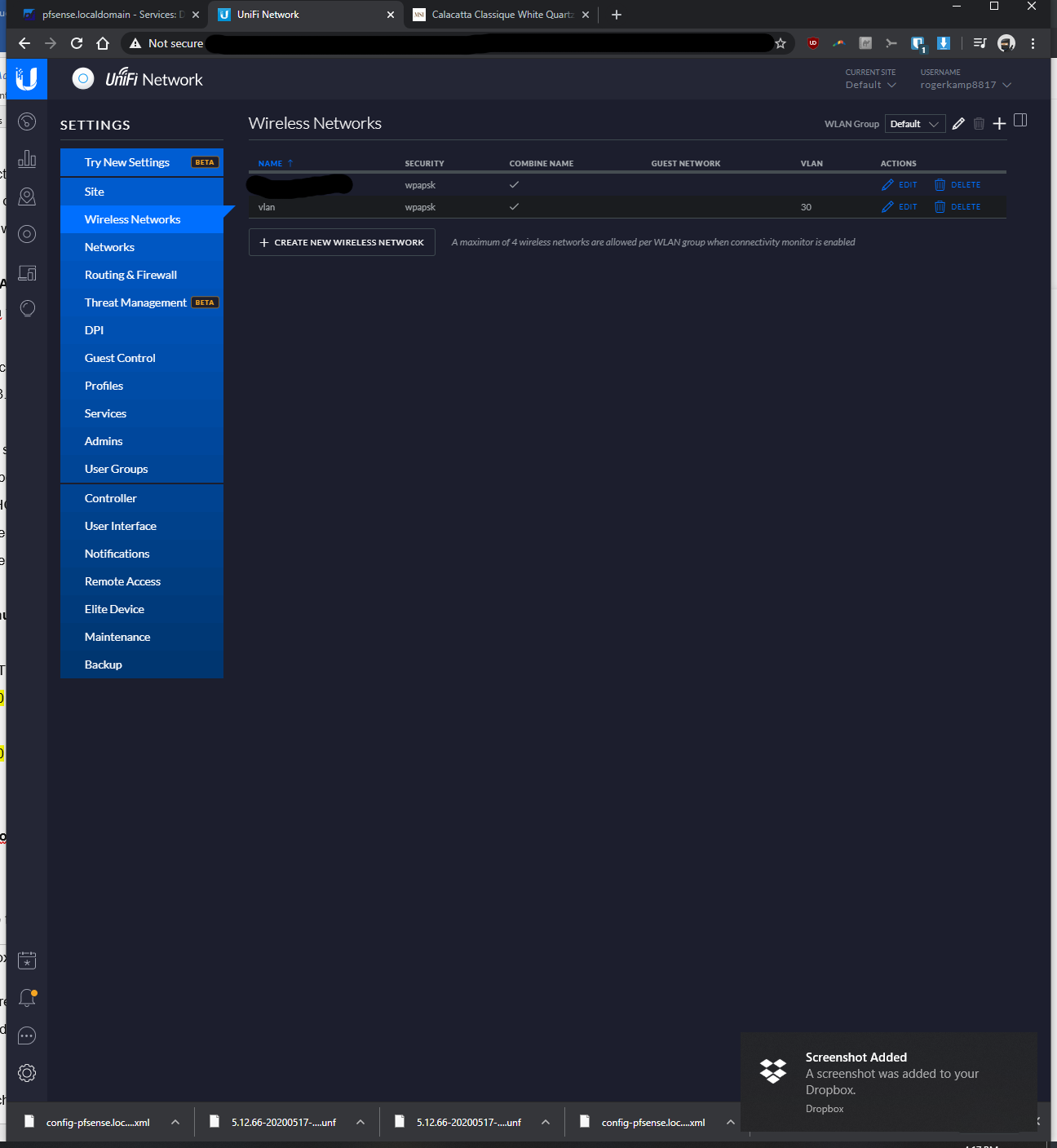
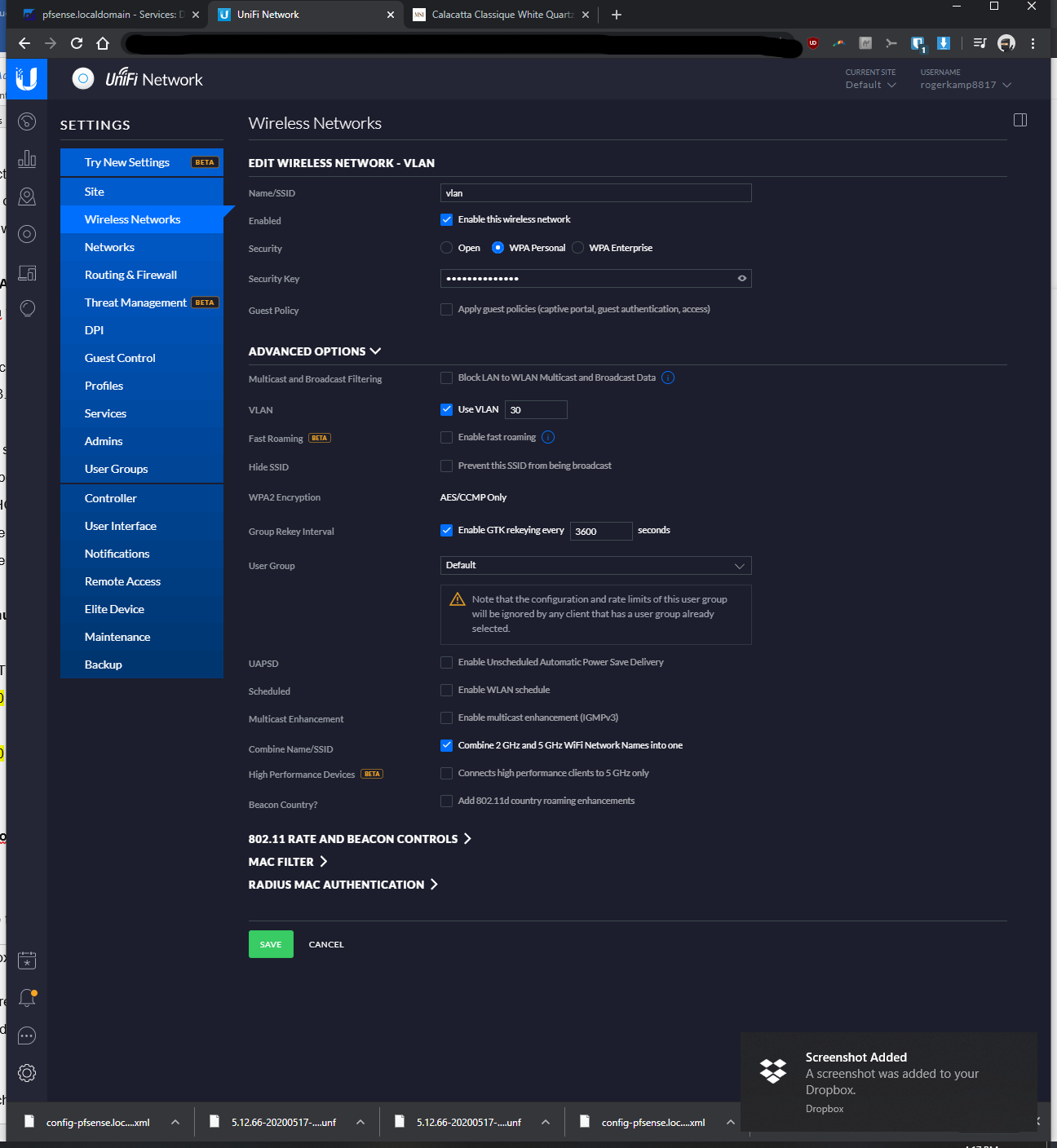
-At first, I initially only went to Settings > Wifi Networks > Create New Wireless Network >Named the SSD, entered password, and assigned vlan 30; however wifi devices connected to vlan 30 wasn't getting assigned a proper IP. From the tutorials I was watching, I think this should have worked, but it didn't seem to.
-In addition to doing the above bullet, I went to Settings > Wifi Networks > Networks > Named it vlan 30, kept corporate bubble filled, entered vlan ID of 30... After taking this additional step, then it started to assign proper IP's to the vlan connected device.When I ping from the RPi Unifi controller to my WLAN clients (not VLAN clients), it'd ping fine.
When I ping from the RPi Unifi controller or ping from other WLAN clients to VLAN clients, there is no connection
I would like to see that the VLAN network pings (transfers data) with other networks, before I setup additional firewall rules to prevent transfer (i.e., IoT devices).
-
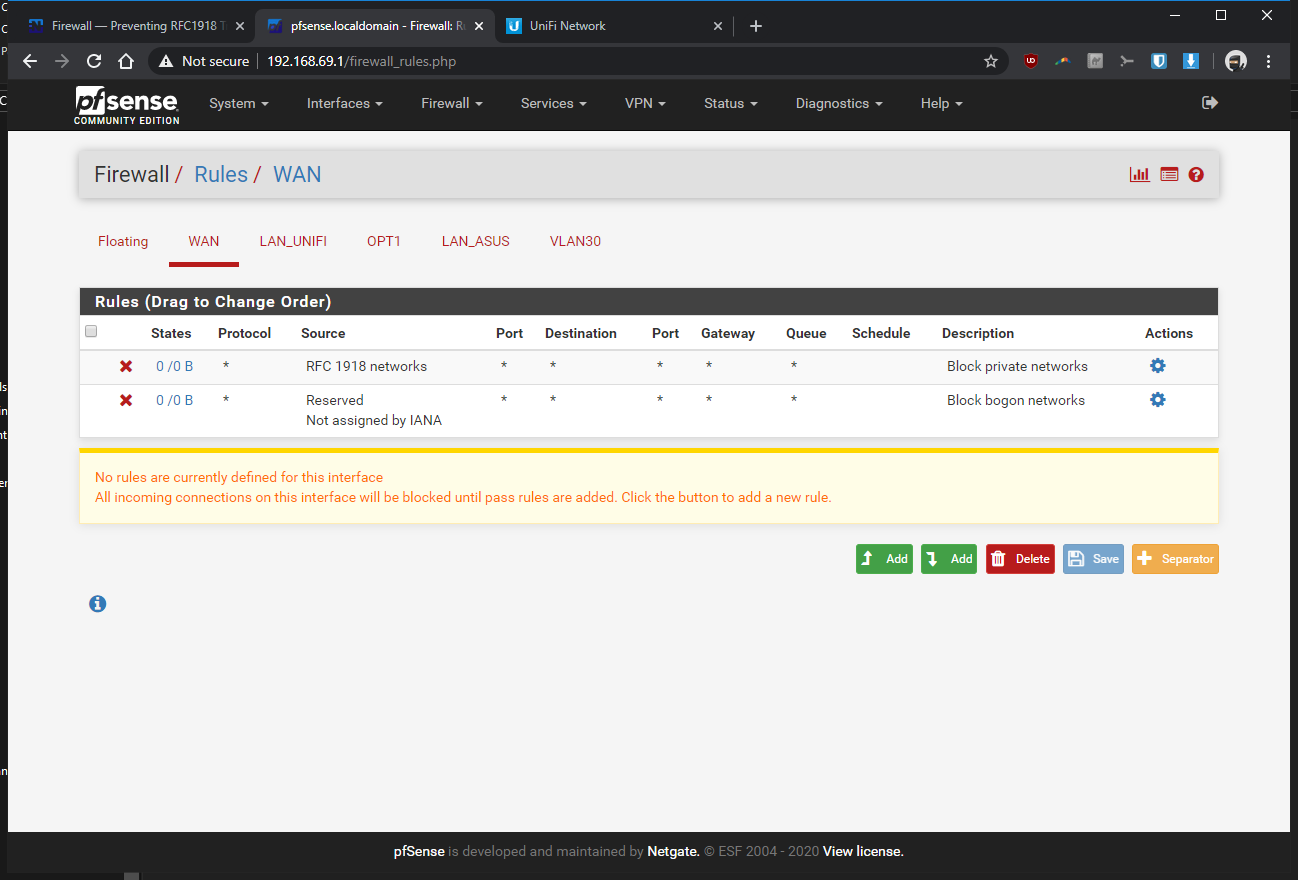
What rules do you have on the interfaces... Showing us the specific 1 rule doesn't help... For all we know you have block rfc1918 enabled on that interface..
Keep in mind local devices firewalls as well... Just because pfsense allows traffic from 1 vlan to the other, doesn't mean the other devices firewall allows you to ping from that remote network.
-
Thanks for chiming in.
The tutorials I was following, it didn't mention anything about RFC 1918 (I left it as default/untouched). As you eluded to, it might be doing something that's preventing my vlan from communicating to non-vlan devices? What should I be changing with my settings to make the vlan devices ping with the non-vlan devices, without opening up my network to the entire internet by mistake? Should I be unchecking one or both of the resrved network check boxes within my WAN?
If you need to see any other screenshots, please let me know.
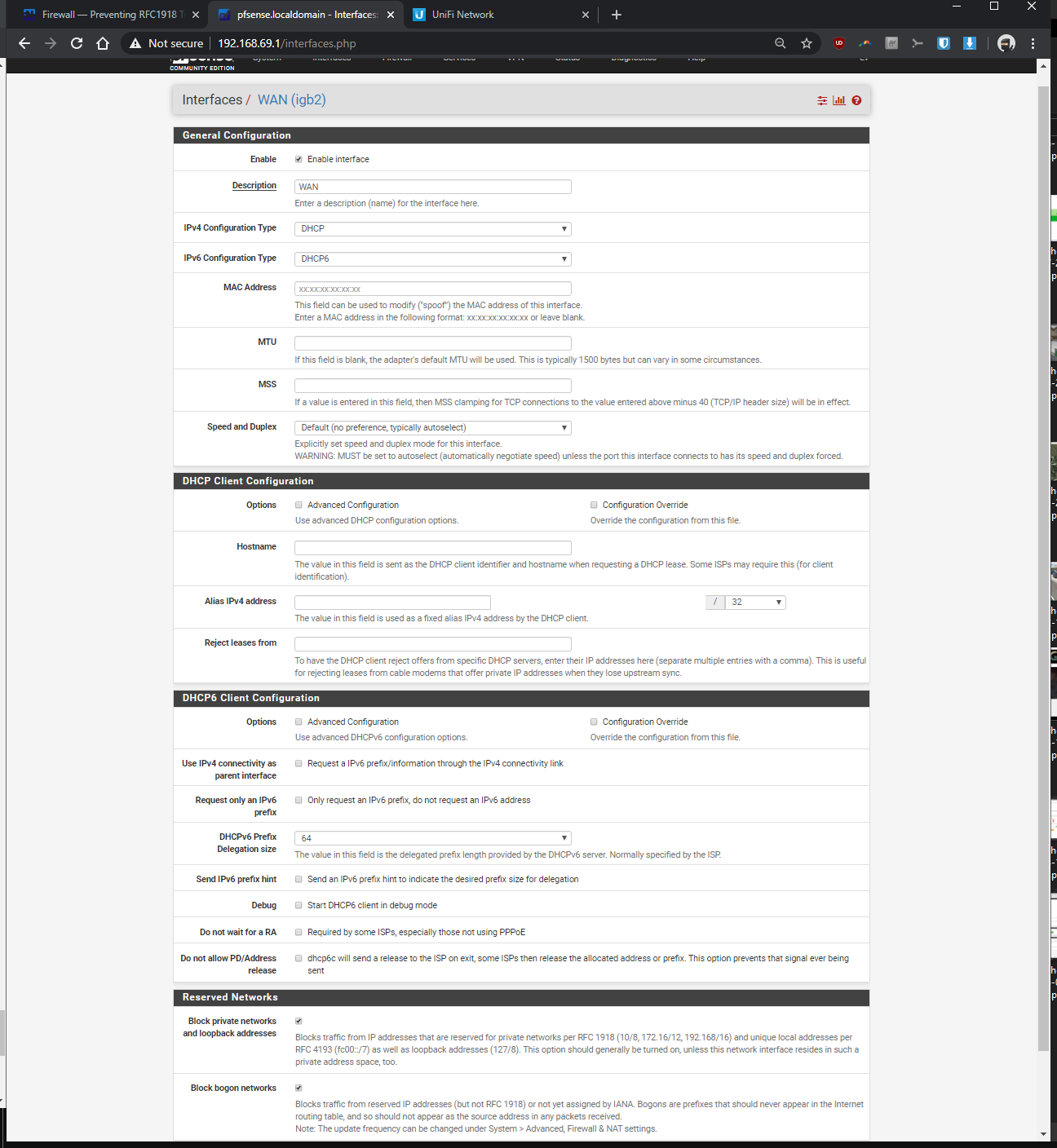
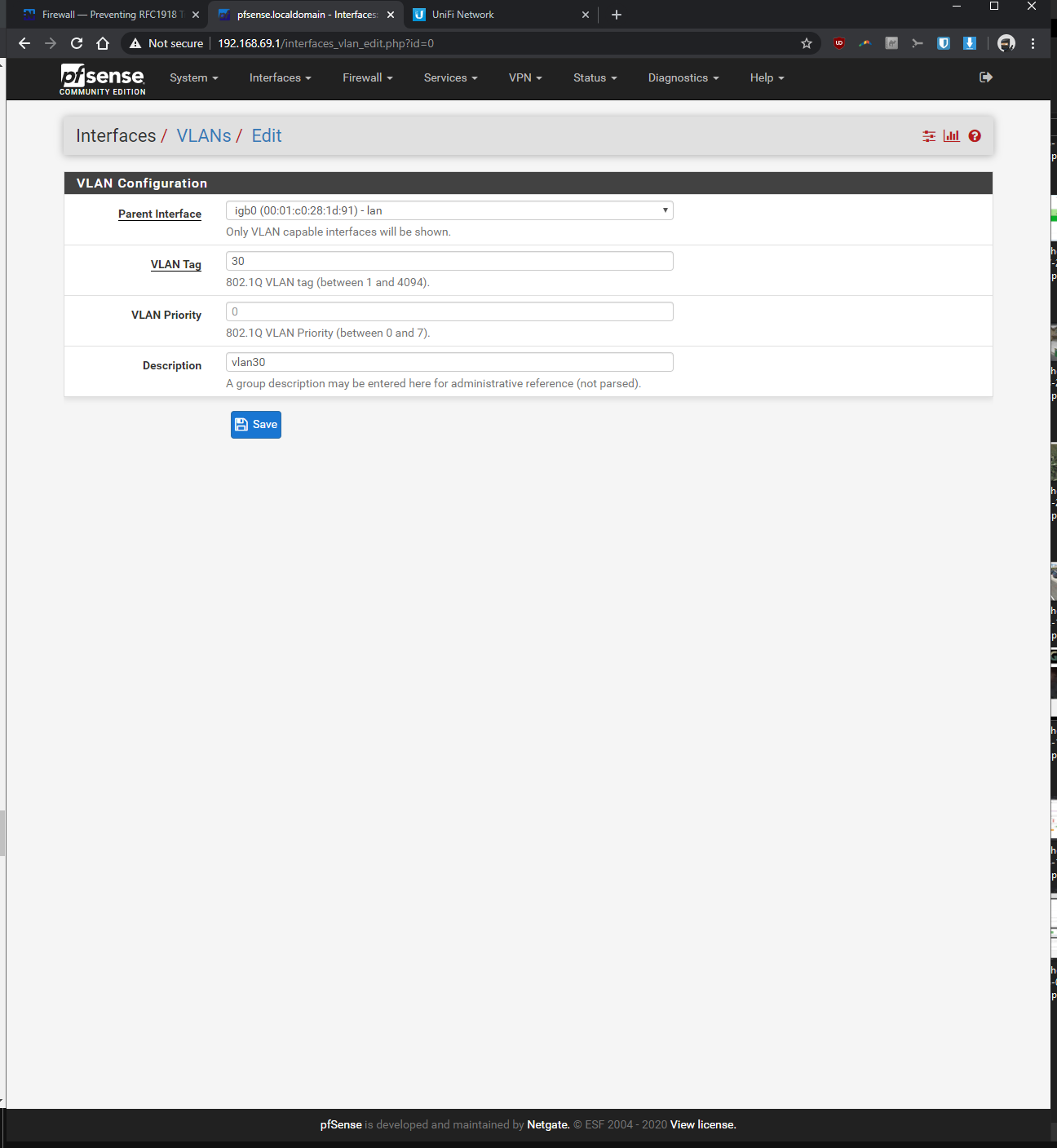
-
@rogerkamp8817 said in Help with my pfsense + unifi AP setup:
If you need to see any other screenshots, please let me know.
How about the firewall rules on the interfaces.. You know the ones I specifically asked for ;)
What rules do you have on the interfaces.
-
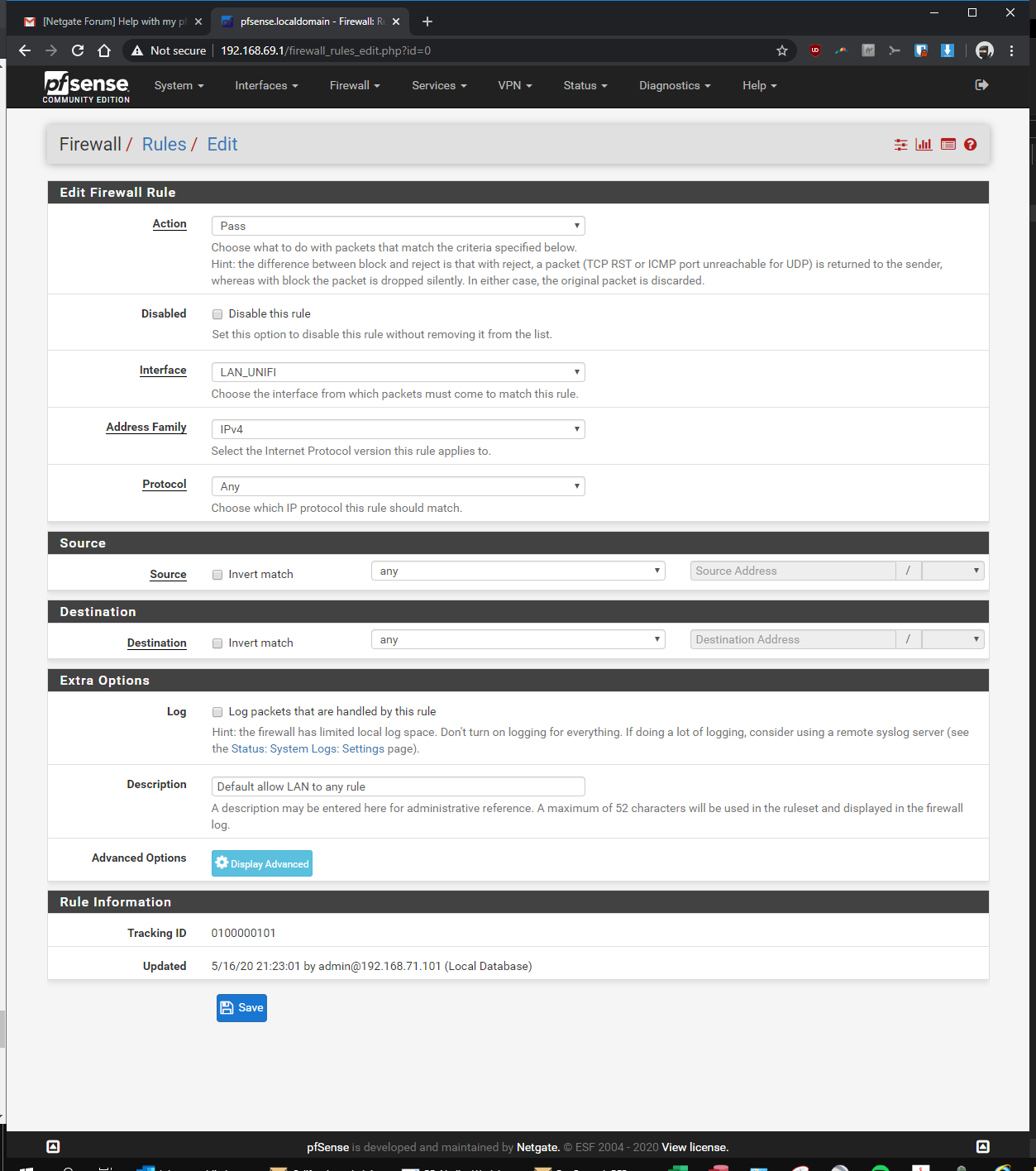
here you go! let me know if i'm still missing something...
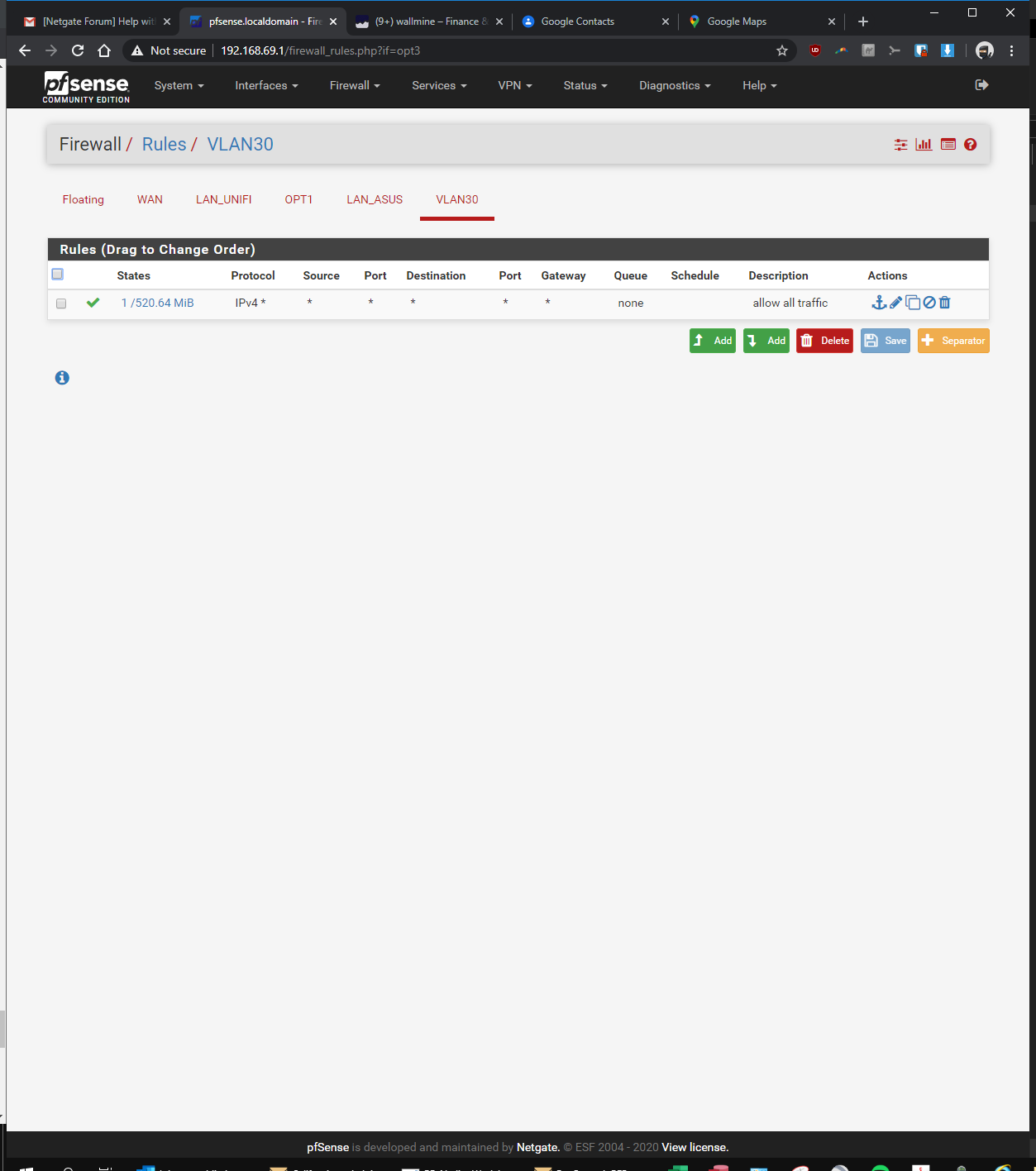
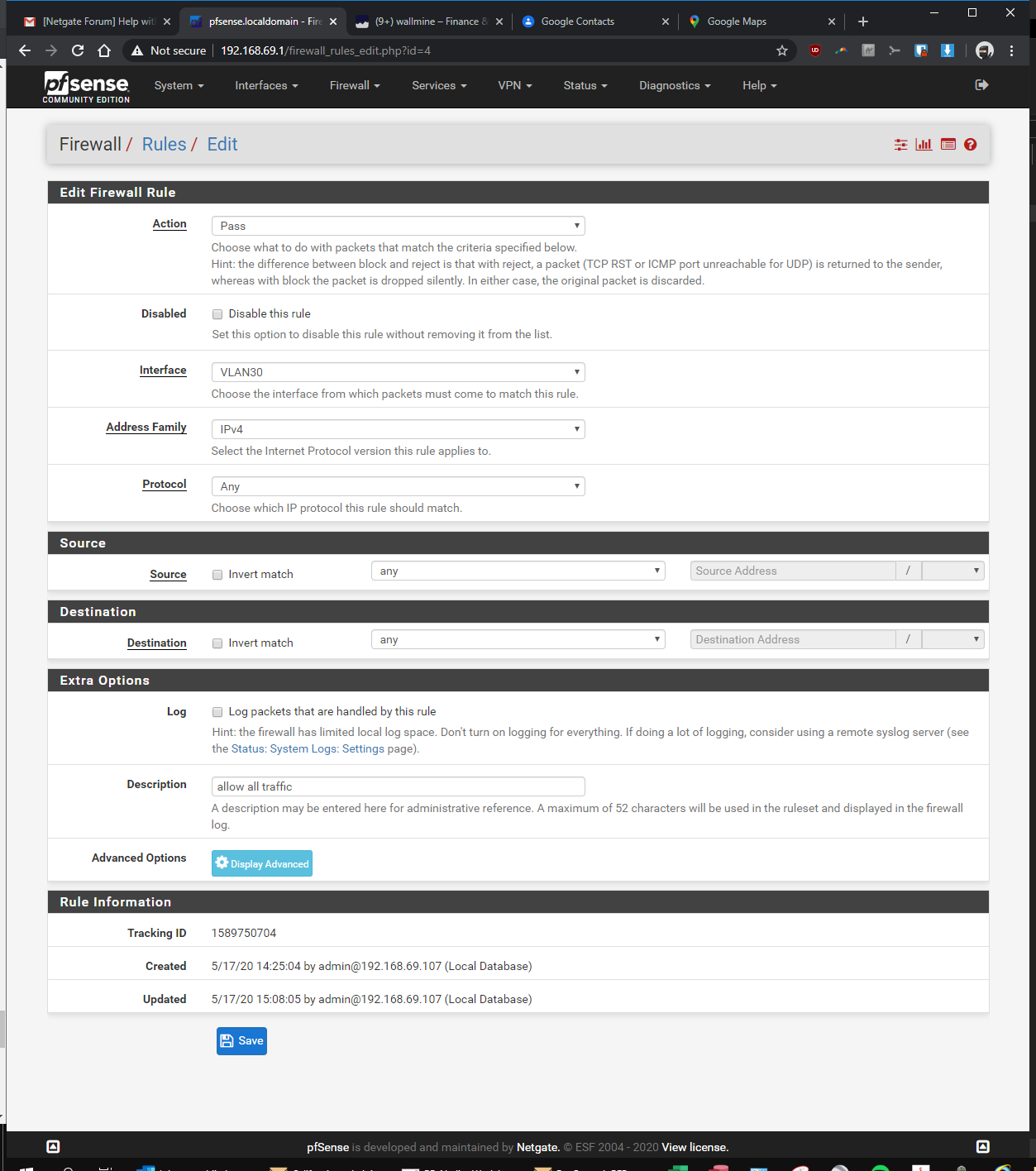
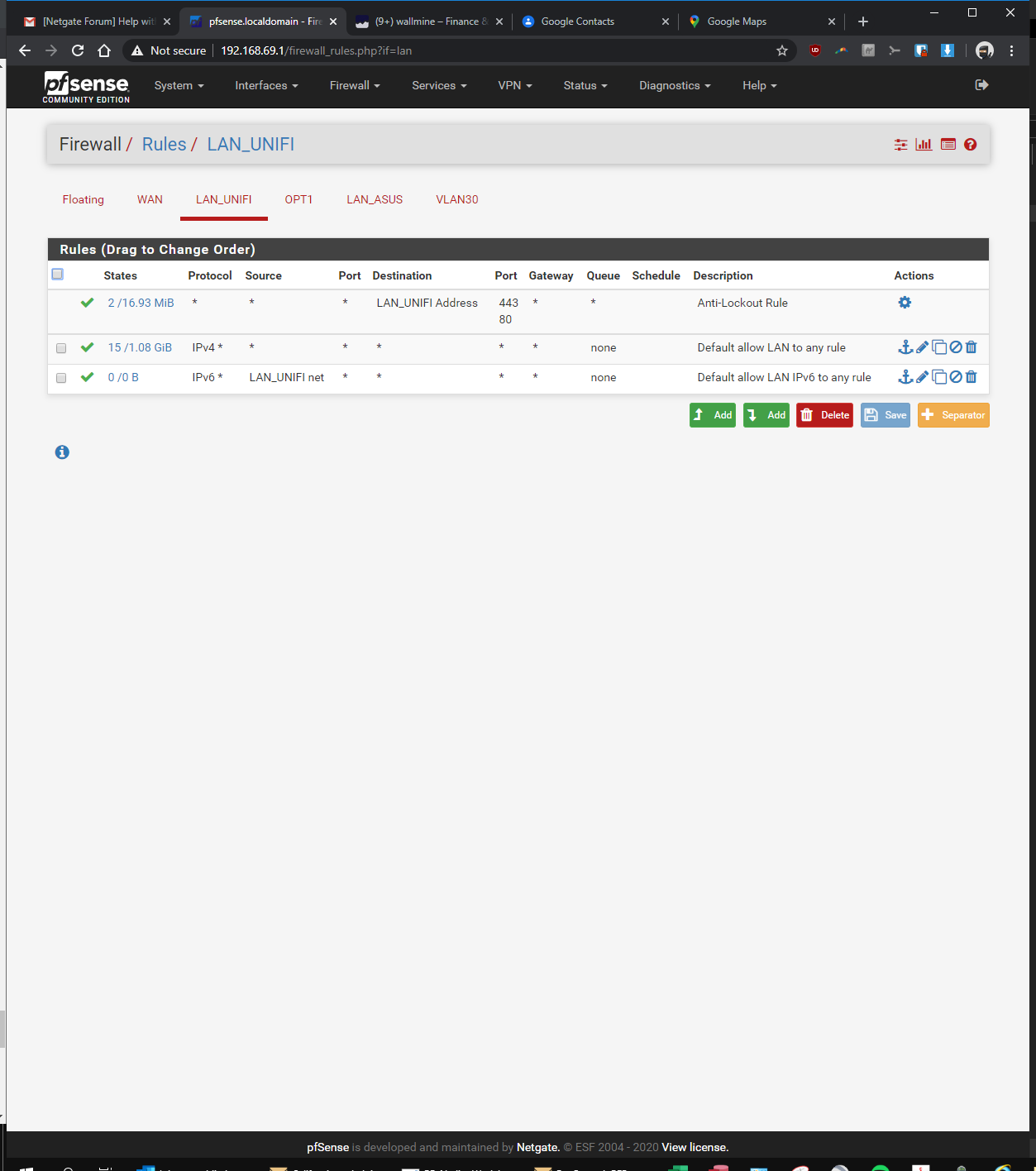
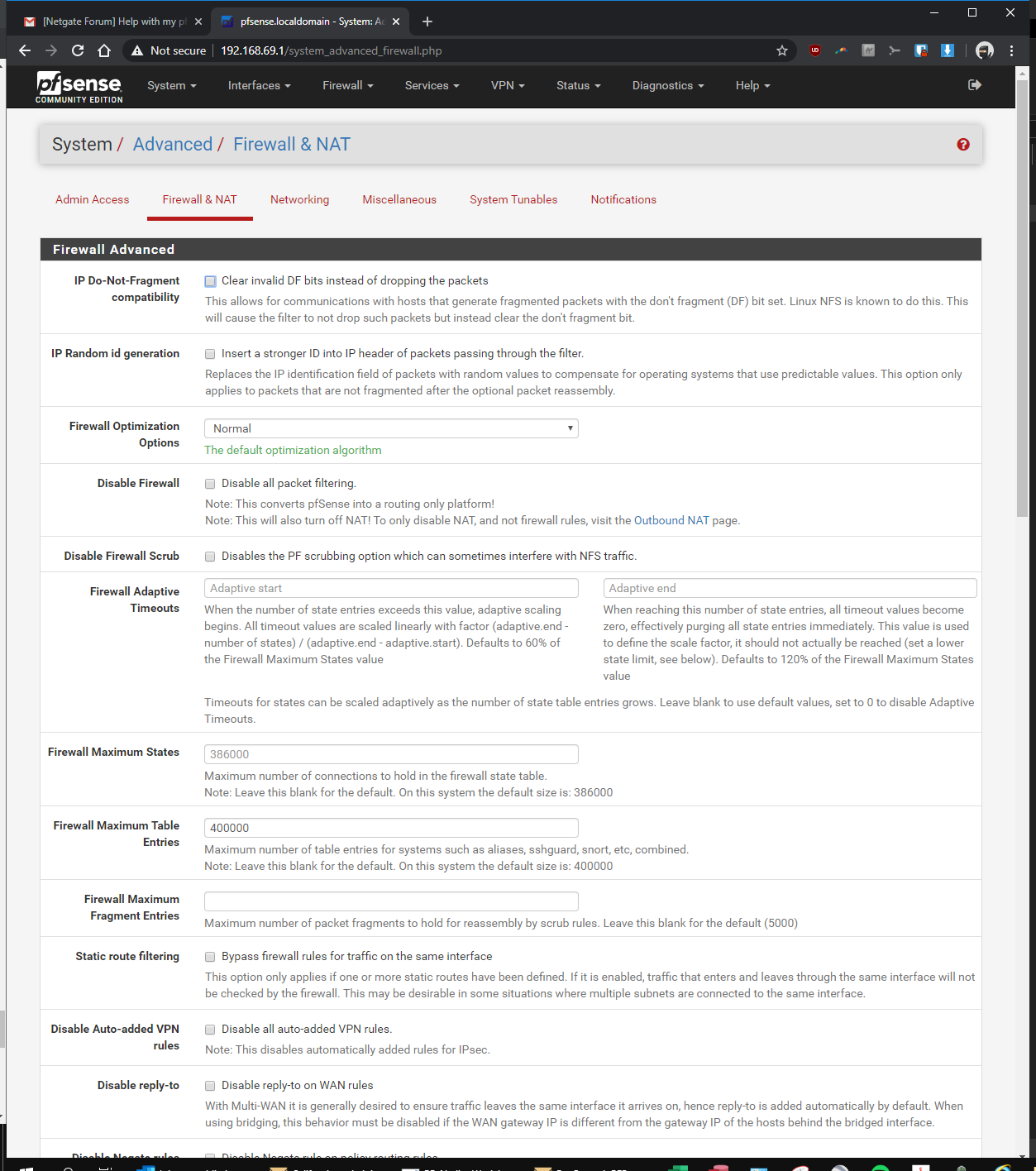

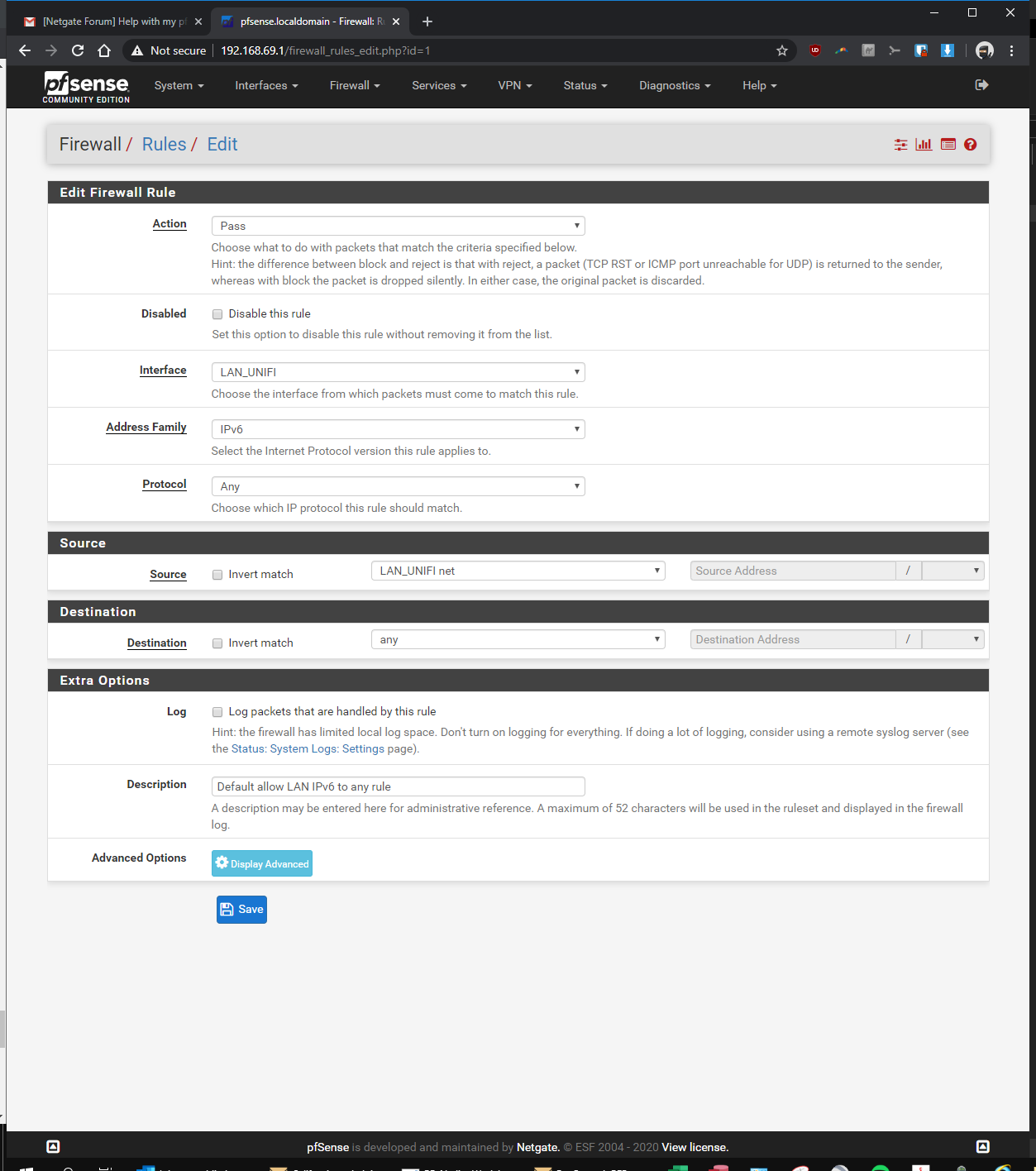
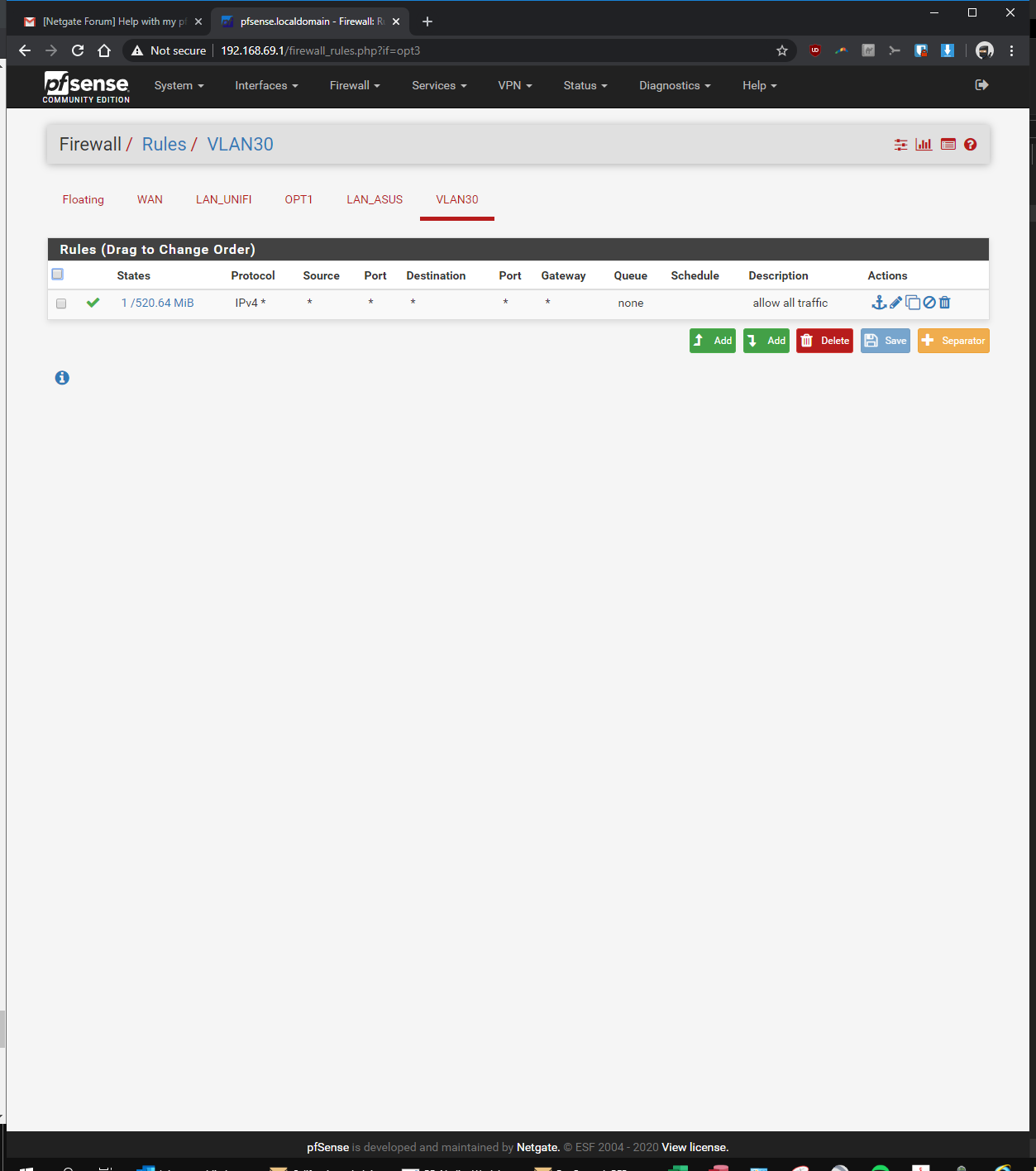
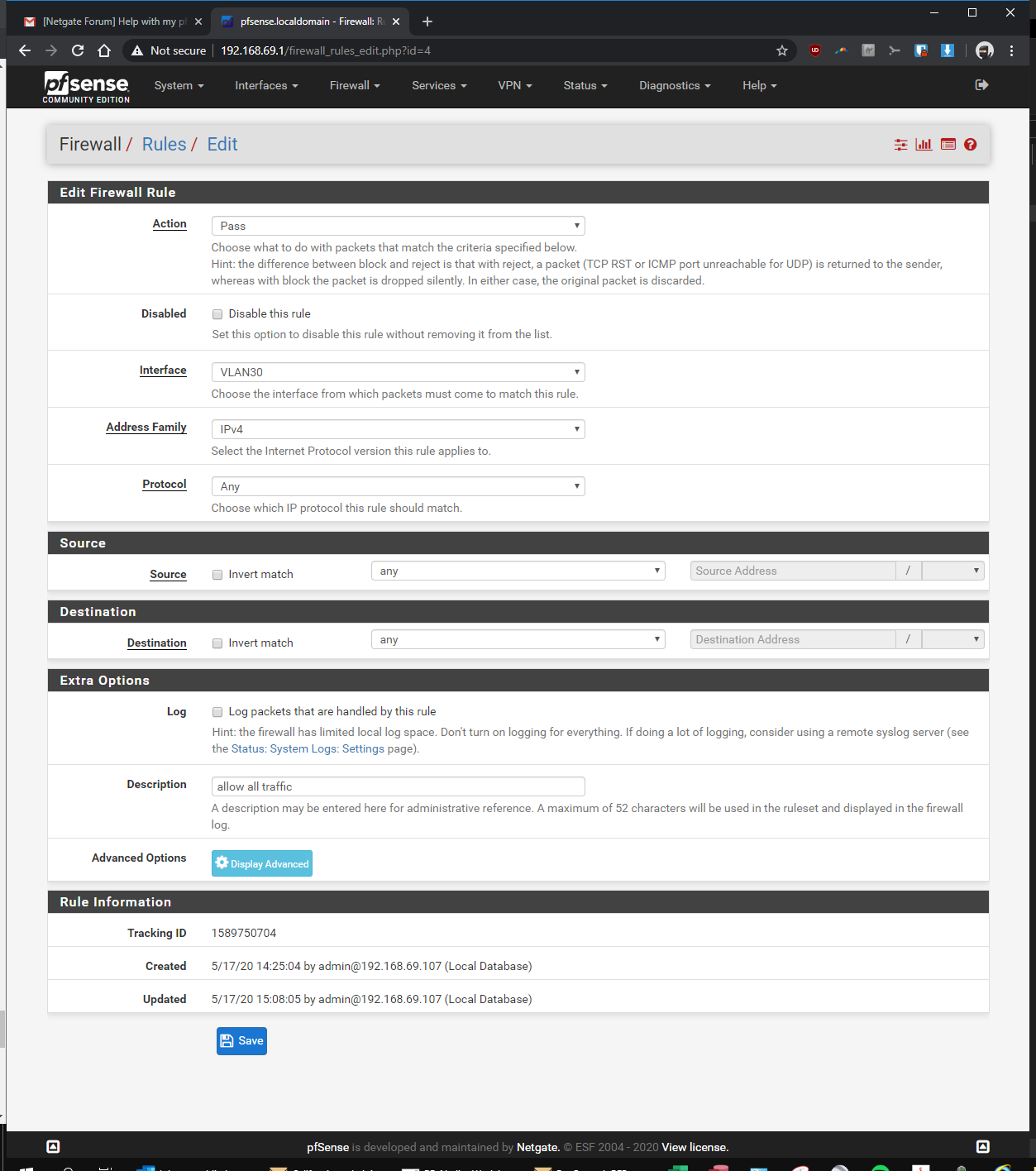
-
OMG!!! dude post up the rules so we can see their order
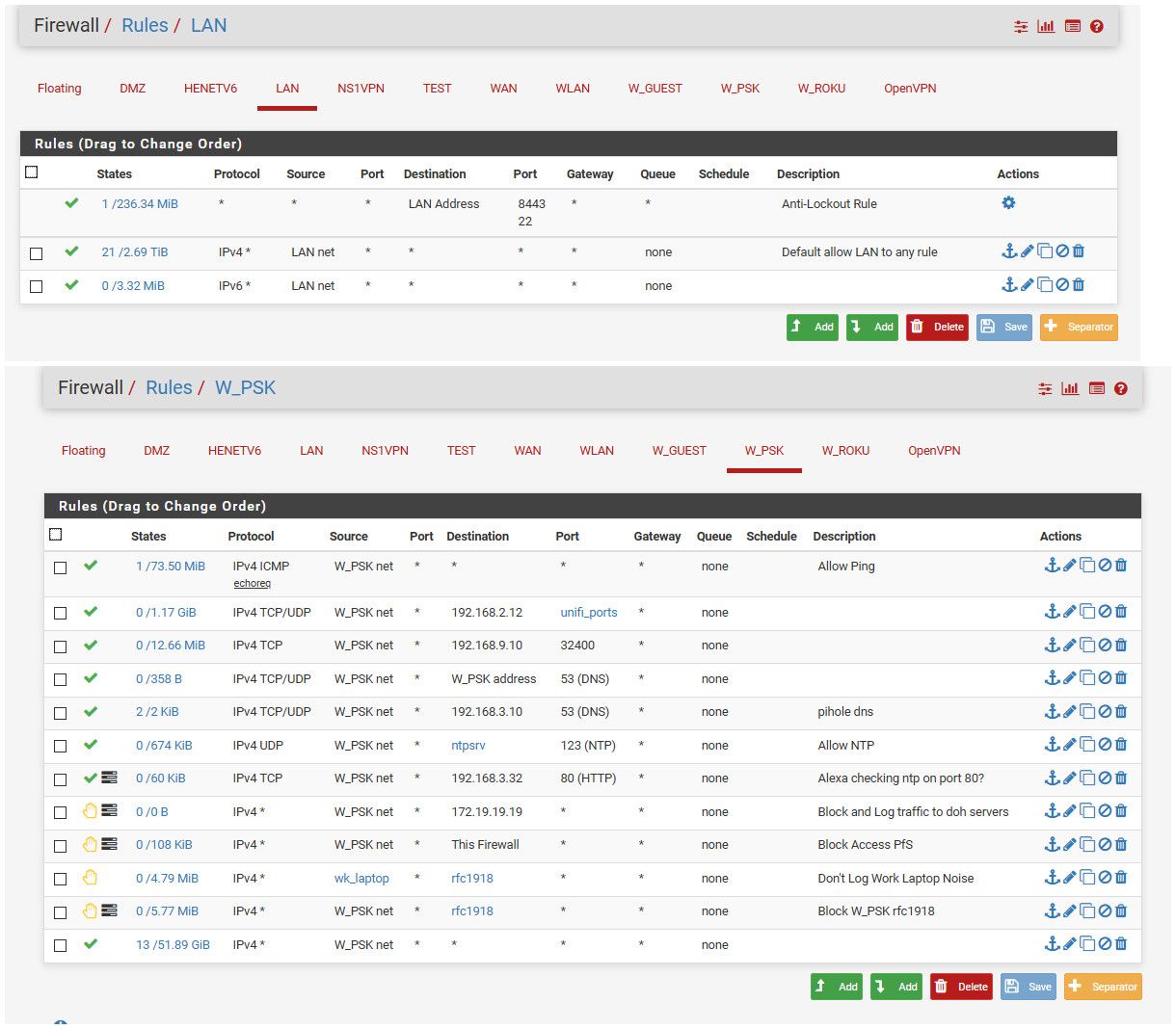
I shouldn't have to scroll through a hundred pages to see the info needed ;)
So your vlan rule is any any.. So if you can not ping some device in your lan - it would SCREAM that devices firewall.. Can you ping the pfsense lan IP from your vlan?
Simple test sniff on your lan interface while you say try and ping something in the lan from you vlan.. Do you see the traffic go out to the device from pfsense.. If so - if there is no answer, then its firewall on the device your trying to talk too.