Filtering outgoing traffic
-
Hi All,
I found a lot of great help on this forum when I was setting up my pfSense installation. I've already set up all necessary things and came to the last one where I am a bit torn.
I was actually not really sure where to put this as it somehow mixes more questions together.My situation - pfSense is the only appliance doing all work - DHCP, DNS, VLANS, etc.
I have 3 VLANS - parent's, kids & guest lan. Guest LAN is set up directly to Cloudflare DNS servers, the other 2 are set up through the DNS resolver.
I've installed pfBlocker package doing ads, DNSBL & IP filtering.What would you recommend I could use best to filter the traffic for the kids LAN (I would love to do filtering based on categories)?
On one hand side, I want to keep the filtering for the ads, therefore wouldn't like to remove the 'parent's lan' from the pfBlocker. On the other hand if I do categories filtering via pfBlocker, as well the the parent's computers traffic will be filtered.
As well, I would like to at least have an general overview of what pages the kids are visiting.I was thinking to use proxy server, but .. on one hand side I am somehow unsuccessful to set that up, on the other hand ... if I get it right, if I would set up the squid, it'll bypass the pfBlocker/DNS resolver and it filters only what is set up in the proxy server, right? That would be a bit useless as I've already set the ads filtering in the pfBlocker.
Is there any other option I am missing?
If I would go with the pfBlocker (which is already set up and works well), is there a way how I could filter only one VLAN based on categories, without breaking the access of other VLAN?Any advices, insights are greatly appreciated.
Thanks a lot!
-
@MarianHlusek said in Filtering outgoing traffic:
it'll bypass the pfBlocker/DNS resolver
Says who? If your proxy uses pfsense as its dns, it would still be using pfblocker.
-
@johnpoz how can I check/assure that, please? If I use explicit proxy, I understood from few tutorials I have to have correctly filled the DN servers on the General Setup tab -> that's why I understood it will use these directly without going through the DNS resolver.
Seems my understanding was wrong. -
The only thing in general setup should be loopback 127.0.0.1.. Out of the box - this is how resolver works..
Are you letting dhcp set your dns? Uncheck that..
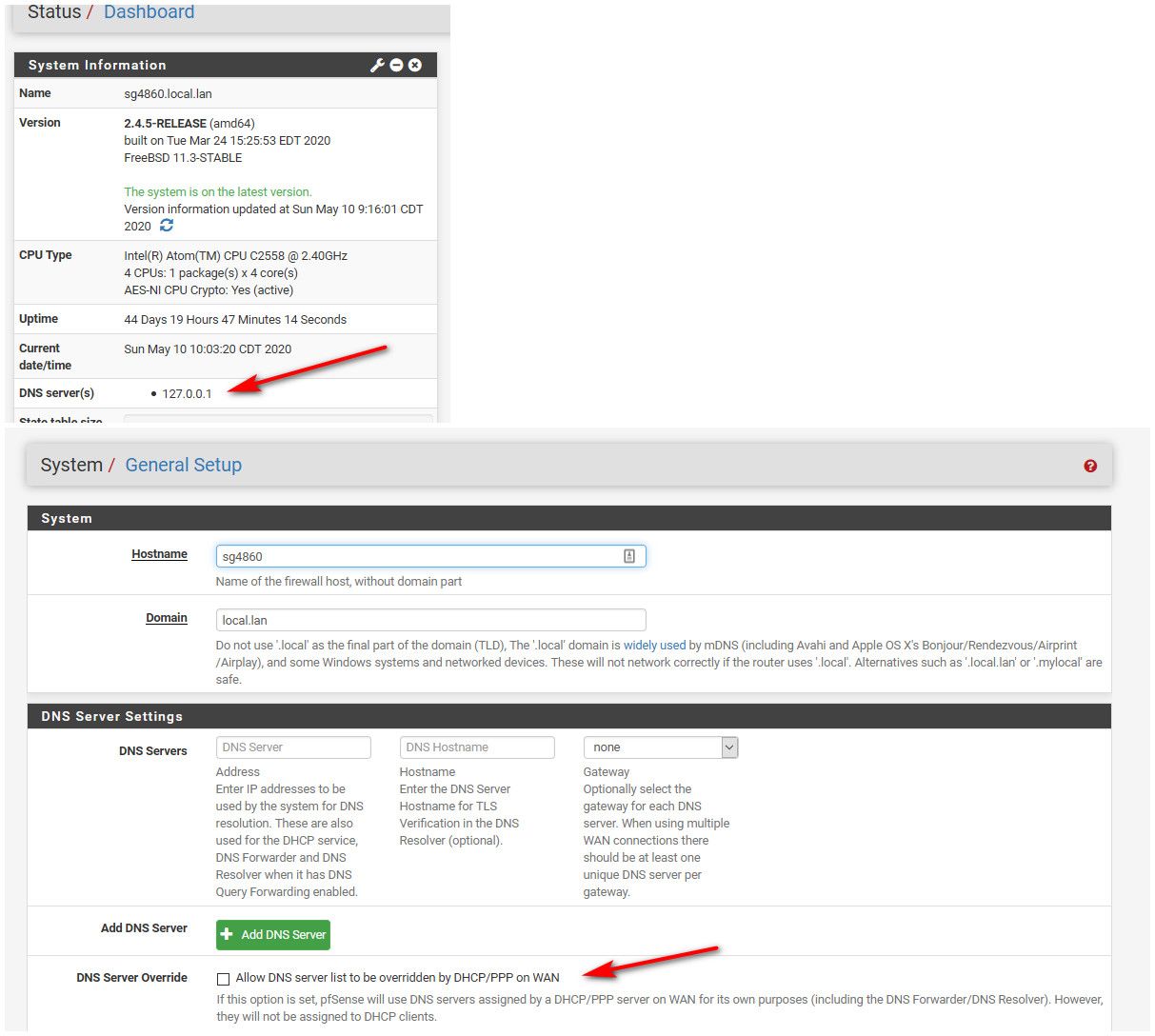
-
@johnpoz I just tried that, but that's probably not the right setup for me. Internet stops working.
Maybe because of NAT rules from each VLAN to 127.0.0.1 port 53?
-
No that would have nothing to do with it..
Are you actually resolving, or forwarding?
-
@johnpoz I am resolving. Forwarder is disabled.
-
Then this is only settings you need. As you saw from my system... That is how its setup..
Forwarding traffic to 127.0.0.1 would have zero to do with anything.
You didn't setup the resolver to forward? Did you you? Out of the box pfsense resolves.. Did you setup some forward to 1.1.1.1 with tls or something in the resolver?
There are 2 systems in pfsense, the resolver (unbound) which out of the box resolves, but can be setup to forward. Or the forwarder (dnsmasq)..
-
@johnpoz Yes, that was the catch ... I missed the tickbox forward in the resolver. Now it works just with the 127.0.0.1. Thanks.
Do you have any preference how to solve the above mentioned traffic filtering for the kid's LAN? -
Your proxy idea is the prob the best, because you can do categories..
I haven't filtered traffic for my kids for 20 some years ;) Back when they were teenage boys looking for p0rn ;) heheheh
I haven't looked into the pfblocker DNSBL lists you could use or setup.. But could be viable solution as well, might just be a bit more leg work.
-
@johnpoz Well, honestly ... I would love to use the pfBlocker, as this seems to me 'easier' solution as it is already implemented and working. The shallalist is available there as well ... the only thing I am not sure is how I split the filtering for:
parents -> DNSBL, Ads, IP
kids -> all the above + categories
But let's see, maybe someone else comes with some other views.
Thank you.