Slicing my pfSense in a router for WANs connections and a firewall for LANs networks.
-
Hi.
Iam having a problem with my current pfSense configuration. I haven't got free network ports to use (Iam alredy using VLANs on almost all of current configuration available ports)
Of course I can create new VLANs for new WAN access or LAN Networks, but I would like another solution. Iam planning to slice in 2 my pfsense: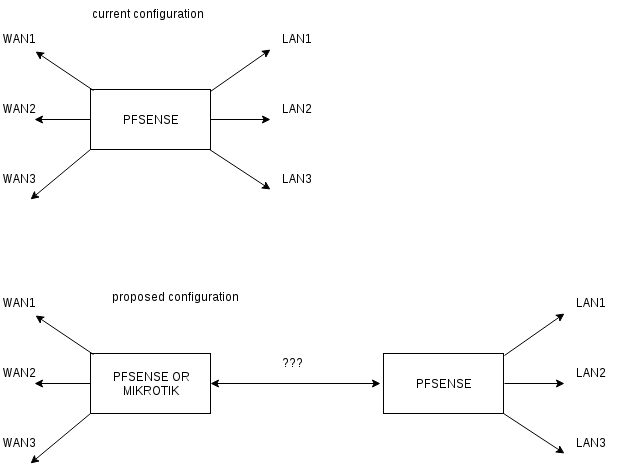
My current pfSense will be used as internal firewall & router for my internal LANs and Iam thinking in use a second pfSense (perhaps a Mikrotik) to manage all my WAN connections.
My questions are:
Is this configuration a valid configuration?
How the communication between this two routers is accomplished?
If port 8080 in WAN A.A.A.A was pointed to port 8080 on server B.B.B.B inside LAN1 in current configuration, how do I do that in proposed configuration?Thanks for your comments.
-
What kind of bandwidth are we talking about on your WAN sides? How much for each WAN connection?
If you bought, or even put together a DIY box, a pfsense machine with enough ports, you could easily accomplish this task. A solution that comes immediately to mind is the Netgate XG-7100 appliance. With the 10 built-in ports, it's got you easily covered. The rack-mount option also let's you add an expansion card, for a total of 14 built-in ports.
https://www.netgate.com/solutions/pfsense/xg-7100.html
Or, if you want to build one, size one up accordingly, with enough ports for your situation. You could deck out a nice PC box with multiple NIC cards, and accomplish what you want. SuperMicro makes some good server boxes for this kind of thing.
Do you want to spend any additional money on this? If so, do you have a budget?
Really, what would make me move on a project like this is, like I asked first off, is what bandwidth do you have on your WAN side, and what do you need to supply to your clients on the LAN side?
Jeff
-
Thanks for your comments Jeff. I was thinking in 7100 as one of my possible solutions.
WAN bandwidth is low, 5 different access with (aprox.) 15MB each. They all together doesn't reach 80MB.6 months ago we have a problem with one of ours ISP providers, they provide us 3 of these 5 access.
When I tried to put 2 of them at the same port (but in different VLANs) we started with problems (One of these just doesn't traffic any packet). Finally we decided to put an intermediate router between their fiber router and pfSense just as a temporary solution.Now I need a new WAN access and I want to finally get rid of these kind or problems splitting my pfSense in two. The questions I need to answer are what happend with the traffic between this 2 routers? What happend with OpenVPN connections?
Thanks for your comments, they shows me that I was thinking in the right direction.
-
I'm curious into your reasoning why you want to go down this route rather than leverage a switch to provide additional ports? Whats the benefit? Just so its clear, I'm genuinely interested if theres a reason for this approach vs what I understand to be more conventional.
-
@q54e3w On the LAN side, sure, switches make sense. I would get managed switches to connect to the LAN1, LAN2, and LAN3 ports out of the pfsense box.
On the WAN side, I don't know about that. If it were me, I would want them directly connected to the pfsense firewall. One less point of failure on the WAN side.
What @Daniel1972 needs to find out is why the WAN connections he's getting from the ISP are not behaving. That would be my first project.
Jeff
-
Yes. we have managed switchs in every LAN Port.
On the WAN side, as akuma1x said, I don't know how to accomplish that with switchs. The only solution I can imagine is with a swtich with routing capabilities. But that's the same a than just a router.
Jeff. What you said about trying to figure it out what is happend with this ISP connections, it's true. Iam agree with that.Iam just facing a problem with 2 or 3 remarkable points that make think about another solution than troubleshooting that problem.
1.- Iam just run out of NIC interfaces at pfSense. Any new network or Internet access need to be done using VLANS. Nothing bad about that, but I want a DMZ, and I want a NIC interface just for that network. (I think is a good practice, but maybe Iam wrong)
2.- The switch were all these VLANS are configured also is running out of ports. Any new WAN/LAN represent a new port on this switch.
3.- If I can centralize all the internet traffic in just one patchcord connecting both routers/firewalls I could introduce a new IDS (beside the one in pfSense) sniffing all my internet traffic going in and out.
Thanks for your comments.
-
@Daniel1972 I am trying to implement the same configuration, not because I'm running out of ports but because I'd like to have separate machines handling the WAN and internal LANs as well as having an internal LAN for monitoring. I just set up a(nother) 192.168.x.x/24 LAN between the boxes and used RIP to share the routes. Unfortunately, I'm running into an issue with routing to the Internet:
https://forum.netgate.com/topic/153989/1-pfsense-router-works-2-pfsense-doesn-t