Why cant i reach the other network while i have added the routes and firewall rules to allow traffic? (Pfsense/USG200)
-
See my Stackexchange post for all details as askimet sees my config and diagram(s) as spam: https://networkengineering.stackexchange.com/questions/67889/why-cant-i-reach-the-other-network-while-i-have-added-the-routes-and-firewall-ru
I have 2 networks, the current one and the new one. The current one is not configured by me and one big mess and contains heavily out dated hardware (especially servers). I want to be able to access the complete current network from the new one so i can migrate server for server and device for device.
Some network details:
- Current network:
- IP: 192.168.1.1
- IP range: 192.168.104.0/24
- Router/firewall: Zyxel USG200
- Contain all currently connected devices
- Gives DHCP address to Pfsense (192.168.104.4/24)
- New network:
- IP: 10.128.10.1
- IP range: 10.128.10.0/24.
- Router/firewall: Pfsense
- Currently it contains only 1 device, my desktop but this network will replace the current one in future
- All devices will be "moved" from the old to the new network by time (one for one)
- Connected with old network by port with alias "WAN 2"
I added a route in each firewall to the other network.
- Zyxel: 10.128.10.0/24 via 192.168.104.4
- Pfsense: 192.168.104.0/24 via "WAN2"
I also added a firewall rule to each firewall to allow all traffic from all sources to all destinations (for testing)
When i ping 192.168.104.1 with pfsense diagnostics, i got a response. I cannot find a way to do a ping from the Zyxel to Pfsense but as the route bellow is in the routing table i assume the (at least) routing configuration must be okay.
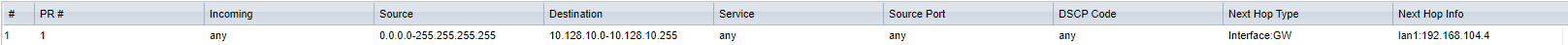
When i try to ping 192.168.104.1 (or any other device in the 104.x network) from my desktop in the 10.128.10.x network, i got a "request timed out" response. I also cannot SSH or browse to any IP in the 104.x network. When i connect my desktop to the 104.x network and try to ping 10.128.10.1 or try to visit that IP in my browser (Pfsense web interface) i also got "request timed out"
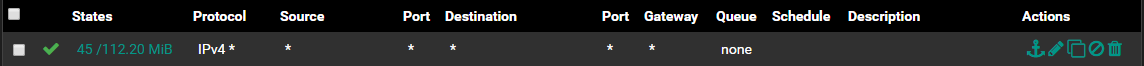
A print screen of my firewall rule on Pfsense (on the desktop interface): enter image description here
And one from my firewall rule in the Zyxel: enter image description here
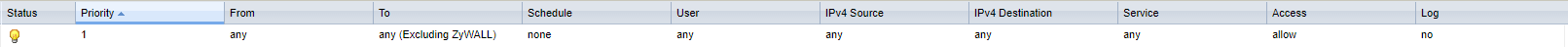
Probably i miss some configuration/settings but i have no idea what. Would be great when someone can help me out with this as i'm already struggling almost 2 days with this. When extra details are required, let me know and i will update my question.
- Current network:
-
Do you have outbound NAT in auto mode? Is pfSense NATing from WAN2?
If it is you should be able to reach devices in the pfSense WAN subnet (192.168.104.0/24).
If it is not you will have an asymmetric route as hosts in the WAN subnet try to reply via 192.168.104.1.
https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-due-to-asymmetric-routing.htmlSteve
-
@stephenw10 First of all, thanks for your answer.
I tried with
Outbound NATin automatic mode and in manual mode with the rules:
WAN1 10.128.10.0/24 * * * WAN1 address *this is not a rule to theWAN 2where the192.168.104.0network exists.
Should i make aNATrule toWAN2?
Something like:
WAN2 192.168.104.0/24 * * * WAN2 address *?I also tried to enable the
Bypass firewall rules for traffic on the same interfacesetting. Unfortunately i still not able to reach the192.168.104.0network from the10.128.10.0or visa versa.I thought adding a static route on each firewall and add the correct firewall rule (to allow traffic from the other network on the concerning interface) should do the trick? but how i understand from you i miss something (NAT?) ?
Note that i can ping the
Zyxel USG200interface and devices of the 192.168.104.0 network from thePfsense diagnosticsping tool but not from my computer.